The Year in Review 2024: Today’s Insights, Tomorrow’s Outlook

For 10 years, Akamai has published State of the Internet (SOTI) reports — in-depth analyses of the latest cybersecurity research and trends. These reports provide valuable insights into the evolving threat landscape and cybersecurity challenges faced by organizations worldwide.
In our early years, these reports focused largely on broadband adoption and connection speeds, but over time they’ve shifted to cybersecurity — and each of them has been built on a collection of robust data that we’ve cultivated by protecting tens of thousands of customers in over 130 countries for more than a quarter of a century.
In 2024 alone, Akamai researchers and threat intelligence officers published 6 SOTI research reports that covered both industry trends and threat methodologies. More than 100 researchers and 65 data scientists support our publications, and they represent a brain trust of cyber intellect that crosses cultural, geographic, and thought diversity boundaries.
Reflections and expectations
In this blog post, I’ve asked six Akamai cyber experts to reflect on the notable trends and events of the past year and give their informed perspective on what we might expect in 2025 and beyond. They also share their thoughts on how organizations can prepare for the future, with practical ideas on minimizing vulnerabilities and reducing their threat footprint.
|
Roger Barranco Vice President of Global Security Operations |
Supply chain and nation-states Lisa Beegle Senior Director of Information Security |
EMEA, hacktivism, and compliance Richard Meeus Senior Director of Security Technology, EMEA region |
|
Ruben Koh Director of Security Technology, APJ region |
Steve Winterfeld Advisory CISO |
Threat actor and tech skill evolution Tricia Howard Scrybe of Cybersecurity Magicks |

Roger Barranco, Vice President of Global Security Operations
What stood out for you in 2024?
As I look back at 2024, several key trends stand out. One surprising phenomenon was the continued high frequency and effectiveness of DNS attacks. Akamai researchers recently observed that DNS was a component in 60% of Layers 3 and 4 distributed denial-of-service (DDoS) attack events in an 18-month period. Yet, there are solutions that can eliminate many of those attacks. Many of these attacks are reflector-based, with threat actors taking advantage of improperly configured servers. Simple DNS changes can prevent this and ensure that organizations don't inadvertently become part of the problem.
We saw a resurgence of the Mirai botnet, which has been responsible for some of the world's largest and most complicated attacks. It's one of the most interesting attack tools; it’s highly intelligent in how it takes over endpoints and locks out other actors. Mirai was quite prominent five years ago, then it disappeared — but now it's back with a vengeance.
This development underscores the need for organizations to focus not just on the size of attacks but also on their level of sophistication. Attack campaigns are becoming much more complex. Many security vendors are building in more intelligent automation to speed up response times, which is an appropriate move given the landscape.
Additionally, I firmly believe that access to security experts remains crucial. Sooner or later, every medium or large enterprise will face a cyber event and resolving it will require human expertise.
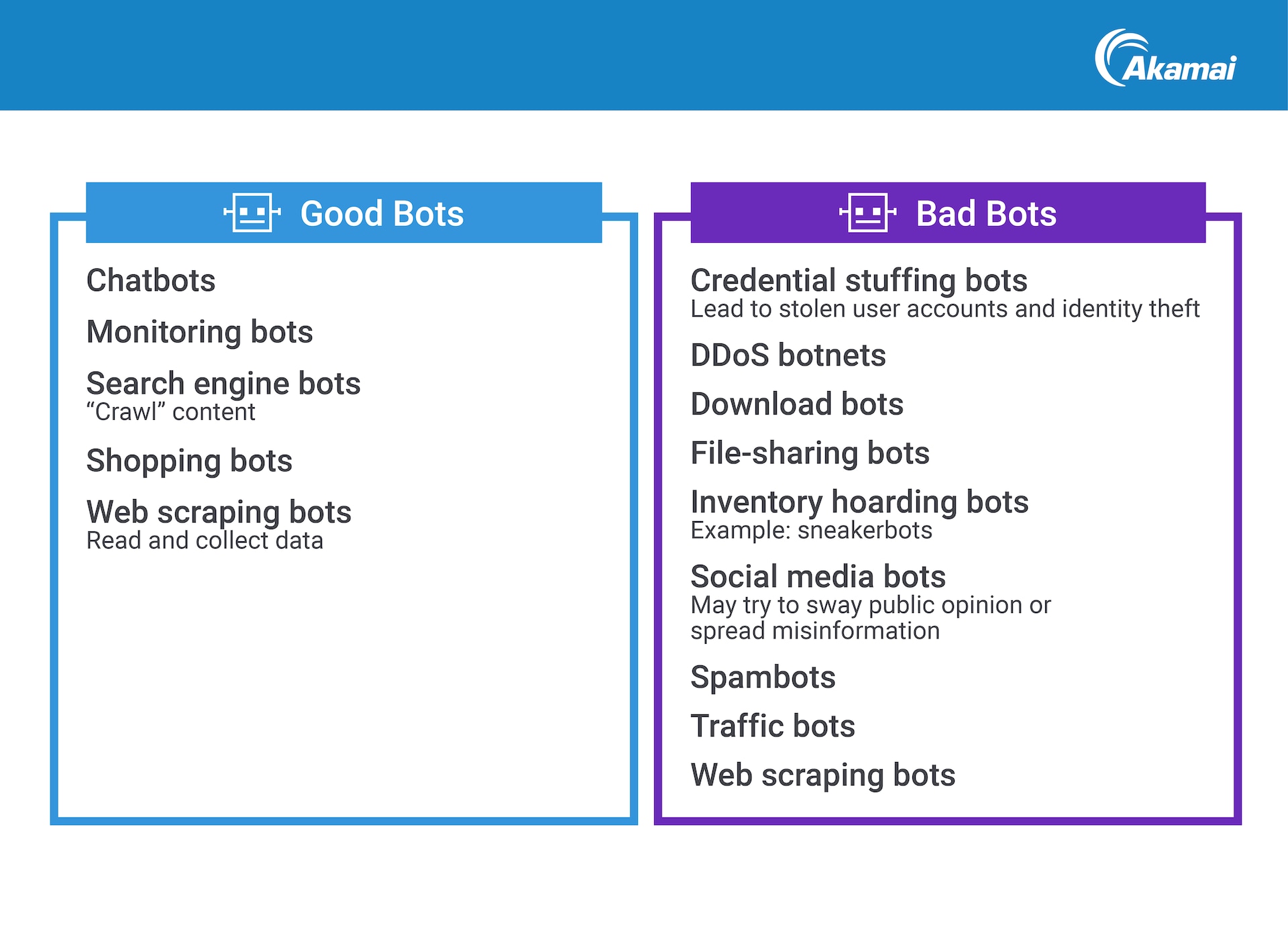
On the applications side, bot credential abuse continued to emerge as a major threat. These attacks, many committed by nation-state actors, are extremely challenging to mitigate. Determining whether an attacker is a bot or a human, or distinguishing between "good" and "bad" bots (Figure 1), requires experienced human experts to understand the unique customer environment and implement the appropriate protection measures.
What notable issues do you foresee in 2025?
Organizations should strengthen their defensive posture when the network is not under active attack.
— Roger Barranco, Vice President of Global Security Operations
The Mirai botnet will likely continue to be a significant factor, becoming even more sophisticated as threat actors continue to evolve the code to create more variants. This evolution will pose ongoing challenges for cybersecurity professionals, who will need to contend with attack campaigns that hit simultaneously at multiple layers across their entire network and application space.
We can expect nation-state activity to expand further through proxies. These attacks will frequently be motivated not by financial gain, but purely by a desire to cause damage.
Organizations will face a continuing need to get a handle on their API endpoints to mitigate vulnerabilities. Proper API identification, management, and security will become even more critical components of a robust cybersecurity strategy, as will microsegmentation.
In the year ahead, I strongly encourage everyone to dedicate time to hardening their environment. Organizations should strengthen their defensive posture when the network is not under active attack. The return on investment for refining the environment before an attack will remain substantial.
As we move further into the future, we’ll need to focus on the impact of quantum computing. This technology will potentially accelerate attacks in dramatic ways the industry is not yet prepared for. Organizations should start planning for a total hardware refresh to keep pace with the advancing capabilities of cyber threat actors. Although the full impact of these plans may not be immediate, initiating discussions and preparations now will be crucial for a smooth transition when quantum computing becomes more prevalent in cybersecurity.

Lisa Beegle, Senior Director of Information Security
What stood out for you in 2024?
State-sponsored cyber operations have seen a significant uptick, driven by heightened geopolitical tensions.
— Lisa Beegle, Senior Director of Information Security
Several key trends emerged in 2024 that demand our attention today. The evolution of threat actors has been particularly striking. Their communication and coordination have become highly organized, making these threat actors far more efficient in exploiting vulnerabilities. This includes hacktivists who offer attack services, such as DDoS-for-hire, to other threat actors.
Recently, the Akamai Security Intelligence Response Team (SIRT) teamed with law enforcement to help take down a significant hacktivist group called Anonymous Sudan (Figure 2).
 Fig. 2: Imagery of a flag of Sudan behind a masked hacker representing the hacktivist group Anonymous Sudan
Fig. 2: Imagery of a flag of Sudan behind a masked hacker representing the hacktivist group Anonymous Sudan
Attackers are now sharing intelligence about successful breaches, repeatedly targeting organizations in which they've found weaknesses, and probing for additional exposures. This sophistication has caught many organizations off guard, as they fail to recognize that the apparent victim of an attack may not be the attackers' true target.
State-sponsored cyber operations have seen a significant uptick, driven by heightened geopolitical tensions. These nation-state attacks have increasingly targeted critical infrastructure, which underscores the urgent need for organizations to adopt proactive threat intelligence and monitoring strategies.
Supply chain breaches emerged as a critical concern in 2024, with attackers exploiting third-party providers to infiltrate organizations, including some high-profile targets. This trend has exposed gaps in security practices and highlighted the necessity for continuous monitoring and vetting of supply chain partners. It's clear that organizations across the supply chain must foster a culture of security to mitigate these risks.
Perhaps most alarmingly, cybercriminals are now using artificial intelligence (AI) to create more sophisticated attack vectors. AI-powered tools have enabled the crafting of highly convincing phishing campaigns, deepfakes, and other novel tactics. This AI adoption has led to a marked increase in successful attacks. To combat this threat, organizations must cultivate a culture of skepticism and education at all levels, coupled with robust verification processes for sensitive requests.
What notable issues do you foresee in 2025?
I anticipate that cybercriminals will continue to use AI to automate and personalize phishing attacks, which will make detection more challenging. This will likely drive organizations to invest in AI-based security solutions for real-time threat detection.
I also foresee continued ransomware attacks that build on their success in 2024. Tactics have advanced from double extortion to triple extortion (often with DDoS attacks) to even quadruple extortion (i.e., attackers directly contact the victim’s customers, employees, and other connected entities to inform them that their sensitive information has been compromised). Organizations that pay ransoms are likely to be targeted again. To protect themselves, businesses need to enhance their backup solutions and intensify employee training to mitigate these risks.
I expect an increase in attacks on Internet of Things (IoT) devices, which often lack robust security. There are numerous devices attackers can exploit, and these attacks tend to occur quickly after vulnerabilities are identified. This highlights the need for stronger security measures and standardized protocols at both the consumer and organizational levels. It is crucial to keep patches and protections up-to-date and to understand your IoT footprint.
Given the ongoing geopolitical tensions, I anticipate a continuation of cyber warfare strategically aimed at targets linked to specific countries. I foresee an increase in cyber events that are strategically coordinated with physical actions, such as the simultaneous disruption of critical alert systems and launch of military attacks. This trend suggests a continued focus on cyber warfare aimed at specific national interests. In light of this, it will be essential to adopt a multilayered security approach and foster collaboration with governmental agencies to enhance resilience against these evolving threats.

Richard Meeus, Senior Director of Security Technology, EMEA Region
What stood out for you in 2024?
The main trend in 2024 was the increase in hacktivism and DDoS attacks in the Europe, Middle East, and Africa (EMEA) region. In Q3, we saw a massive ramp-up of attacks that targeted Europe and the Middle East. This is clearly associated with the two regional wars that are driving much of this activity, and there is no sign that these attacks will let up.
Another notable development was the implementation of the NIS2 Directive, which is focused on operational resilience. It was designed to be written into legislation by each European Union (EU) member state. The EU member states had until October 17, 2024, to transpose NIS2 into national law. Organizations in Europe need to ensure that their security infrastructures comply with these new and updated requirements that center on mitigating risk and improving resilience in the event of attack.
A particularly interesting event was the XZ Utils backdoor (CVE-2024-3094) that exploited a vulnerability in this widely used open source library. This attacker played the long game by contributing to the XZ project over the course of nearly two years to build credibility until they were able to embed malware into the open source environment. This long play had echoes of the Volt Typhoon campaign, which infiltrated DSL routers in the United States with the goal of disrupting communications.
Perhaps the most interesting development in DDoS attacks was a vulnerability that the Akamai SIRT discovered in the Common UNIX Printing System (CUPS), an open source printing platform. This was yet another vector that attackers could add to their arsenal to strike Europe. The capability to hit once but then create an endless stream of traffic was particularly interesting, especially given that there are thousands of vulnerable devices on the internet that use CUPS.
What notable issues do you foresee in 2025?
In 2025, I think we will see more focus on being cryptographically agile.
— Richard Meeus, Senior Director of Security Technology, EMEA Region
With two regional wars still raging, I don’t believe the hacktivism threat will diminish any time soon. Indeed, Akamai continues to work with the government of Ukraine to protect their key online assets. I think this threat activity will continue until these geopolitical situations are resolved, since hacktivists are driven by conflict or by what they perceive as injustice. They are trying to create a lack of trust in institutions and put pressure on governments to stop their support of specific regimes.
I think we will see a shift in attack vectors to focus more on APIs. As organizations deploy more application programming interfaces, it will only increase their exposure to threats and put them at more risk of abuse. Akamai has been focused on API vulnerabilities for quite some time, driven by the ever-expanding threat landscape and emphasizing the need for organizations to implement a robust API security strategy.
In 2025, I think we will see more focus on being cryptographically agile. Organizations are starting to get their heads around what they need to be “quantum safe.” In a few years, if not sooner, they will need to update some of their certificates and algorithms. This raises a number of questions about what encryption standards to use and when and how to shift to quantum-safe encryption. That’s not going to happen tomorrow, but I think people will need to start thinking about the risk and how to address it. It’s a generational shift.

Ruben Koh, Director of Security Technology, APJ Region
What stood out for you in 2024?
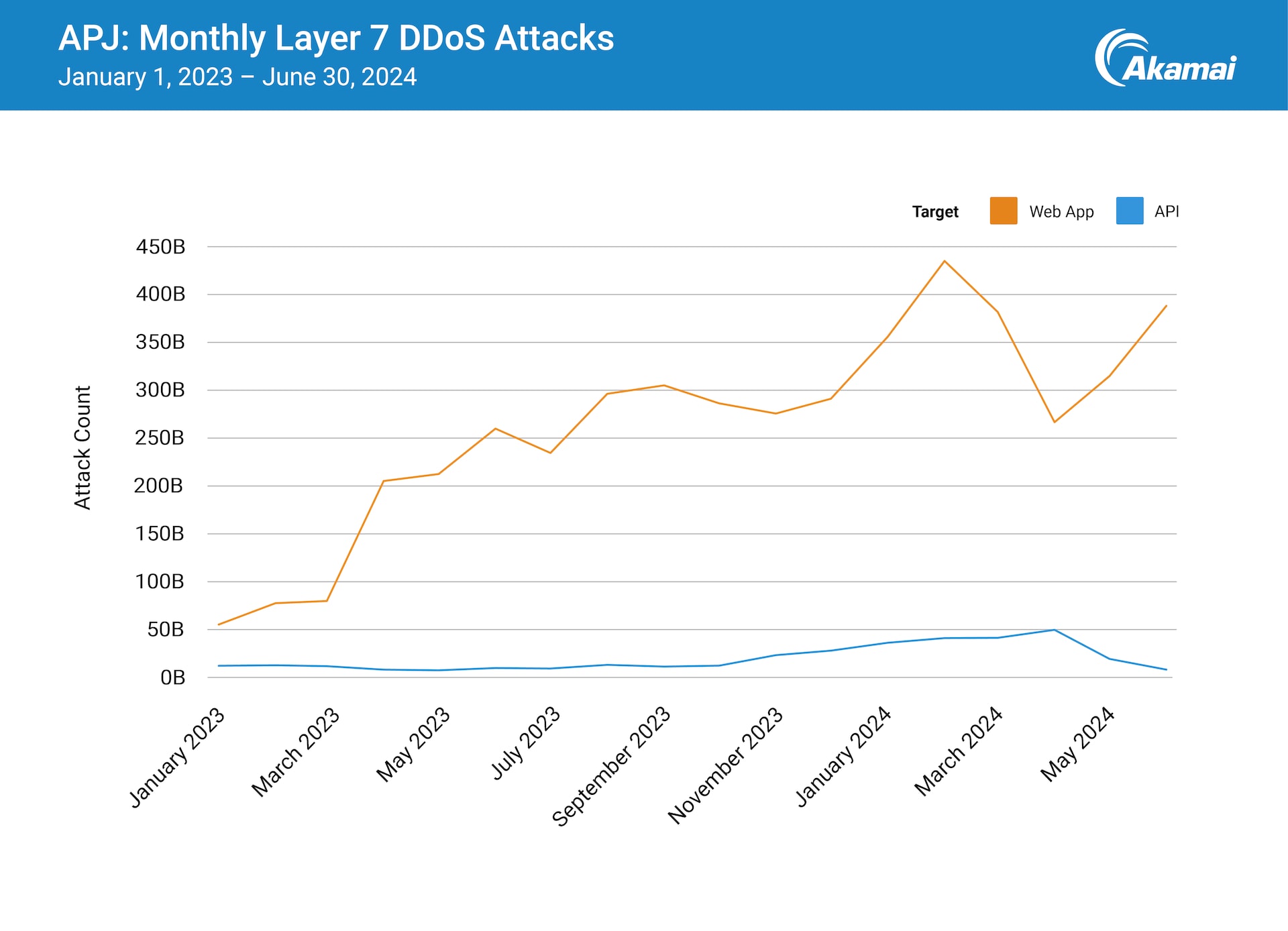
A particularly significant trend in 2024 was the tremendous increase in Layer 7 DDoS attacks that targeted the Asia-Pacific and Japan (APJ) region. This was covered in detail in our State of the Internet (SOTI) report Digital Fortresses Under Siege, which was focused on threats to applications. Akamai researchers found that the number of Layer 7 DDoS attacks in APJ grew fivefold from January 2023 to June 2024 (Figure 3). The growth trajectory of this type of high-impact attack is very concerning.
Also notable was the fact that the spikes in DDoS attacks aligned with the timing of significant geopolitical events. In 2024, there were major elections in three countries within the APJ region — India, Indonesia, and Taiwan — and we saw a rise in DDoS attacks around the times of those events.
I believe the rise in these attacks may be attributed to an increase in hacktivism aimed at countries or industry sectors that the hacktivists believe conflict with their ideology and beliefs. This observation highlights the need for organizations to not only defend against cybercriminals who are looking to make a profit but also to defend against hacktivists who are driven by political agendas and can strike at any time.
DDoS attacks are clearly a major problem, but I think many organizations in APJ are still not adequately prepared for them. They are real threats that must be taken seriously. DDoS attacks are not only going after commercial enterprises but are also targeting critical infrastructures, from banking systems to transportation to public utilities. If DDoS attacks are successful, their impact will likely be felt in our everyday lives.
What notable issues do you foresee in 2025?
As AI becomes more deeply embedded in business operations, efforts to secure AI will need to be at the forefront of organizations’ strategies.
— Ruben Koh, Director of Security Technology, APJ Region
As in other global regions, organizations in APJ will be adopting AI to benefit their businesses and profitability at a much more frantic pace across every industry in 2025. However, in their rush to embrace AI, it’s important that they not lose sight of essential security safeguards. We saw a similar situation more than a decade ago, during the rush to adopt cloud computing and cybersecurity. Security was often overshadowed by speed to adoption, which inevitably led to several high profile data breaches.
Currently, I think we are just scratching at the surface of what is possible with AI, and organizations may not fully understand the underlying potential security implications. As AI becomes more deeply embedded in business operations, efforts to secure AI will need to be at the forefront of organizations’ strategies. Unfortunately, if past activity is any indication, the likelihood of this happening is relatively low — until there is a major data breach that suddenly jolts organizations and regulators into focusing on related security frameworks and regulations.
Starting in 2025, I think we will see an increasing focus on two aspects of AI security: protecting AI systems and defending against AI-driven attacks. After all, cybercriminals are learning how to leverage AI to make their attacks more evasive, more efficient, and more effective. AI will lower the barriers to entry for attackers, accelerating their ability to identify and exploit vulnerabilities. At Akamai, we are already a few steps ahead by building our own AI models, exploring how to attack them, and determining what protections are needed to enhance our security solutions — which may include various implementations of AI-augmented capabilities, as well. This is an area in which we will continue to advance our capabilities in 2025 and beyond.
Finally, while people are distracted by the latest shiny new thing that is AI, it is important not to lose sight of having solid security fundamentals. Attackers will still come after API endpoints, and they will still conduct phishing attacks in 2025. We still need to ensure that patches are deployed in a timely manner, our safeguards are always on, and that people are continuously trained to identify and mitigate malicious activity. Because with or without AI, those threats are not going away.

Steve Winterfeld, Advisory CISO
What stood out for you in 2024?
These new regulations are having cross-regional impacts, necessitating a global perspective on compliance.
— Steve Winterfeld, Advisory CISO
The regulatory landscape for cybersecurity continued to evolve globally. In 2023, Anu Bradford outlined three distinct emerging approaches: market-driven, state-driven, and rights-driven models. This framework provided a useful lens for understanding the new regulations in 2024, including the U.S. Securities and Exchange Commission's introduction of cyber materiality reporting requirements, the EU’s DORA, and China's Data Security Law. These new regulations are having cross-regional impacts, necessitating a global perspective on compliance. Emerging areas of regulatory focus include APIs, generative AI, and ransomware payment policies, which warrant close monitoring.
Concurrently, DDoS attacks evolved from primarily criminal enterprises to geopolitical tools employed by nation-states and hacktivists. We witnessed record-breaking DNS NXDOMAIN attacks, also known as pseudo-random subdomain (PRSD) attacks, and increased Layer 3 and 4 (infrastructure) DDoS attacks targeting financial institutions in conflict zones, alongside a growing prevalence of Layer 7 (application-layer) DDoS attacks against both applications and APIs. These trends were observed across industries and regions, underscoring the need for robust, adaptive cybersecurity measures.
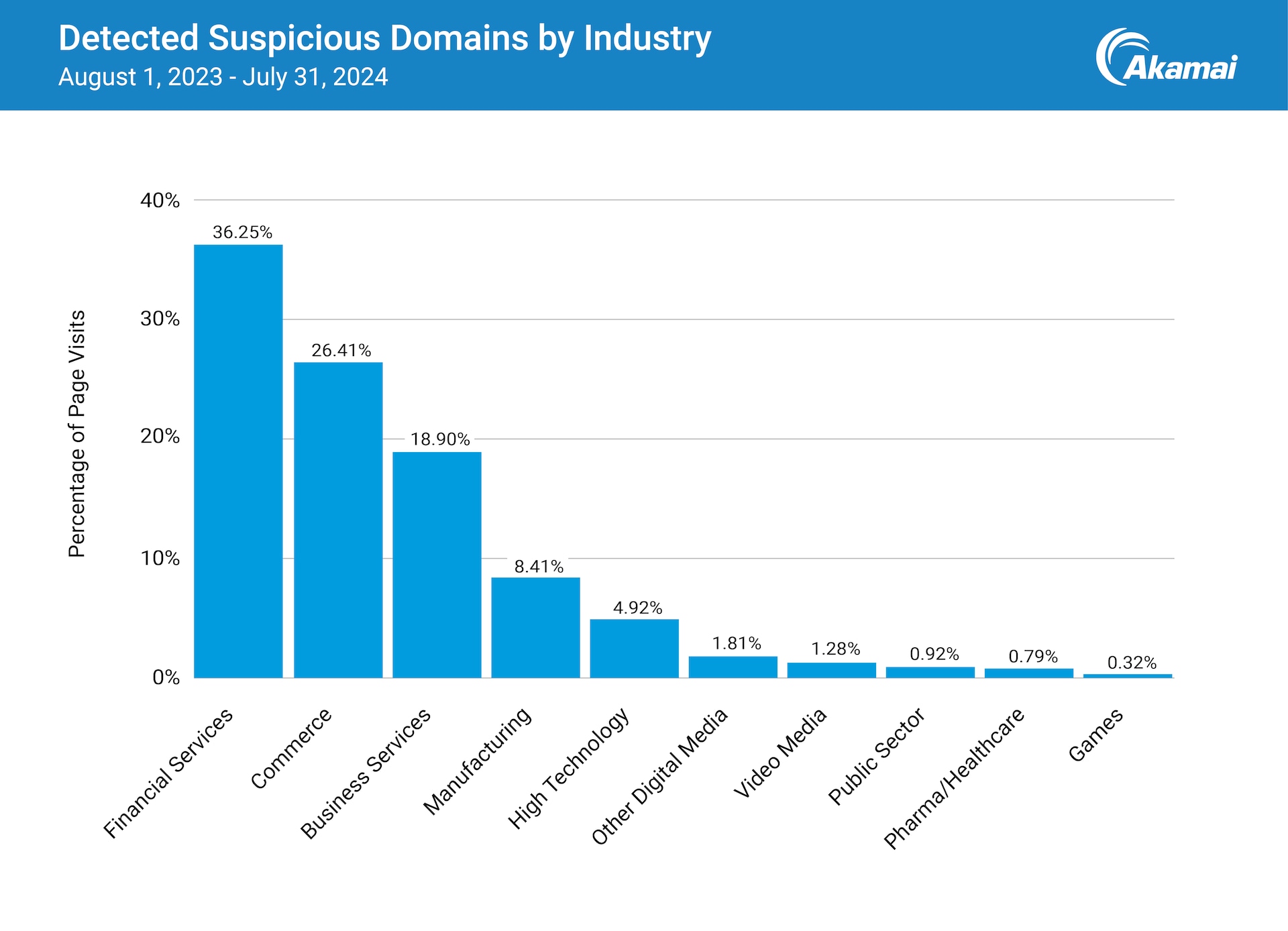
The cybersecurity landscape continued to evolve, with fraud becoming an increasingly significant concern for security teams. Akamai's recent report on web scraping, driven by customer demand for protection, reveals that the financial services sector was the most heavily impacted. Our data shows that 36% of detected suspicious domains targeted financial institutions (Figure 4). Notably, 68% of these spoofed financial services sites employed phishing tactics to acquire personal identifiable information, including credentials, facilitating account takeover and identity theft. Mitigating these growing scams has necessitated cross-organizational collaboration.
What notable issues do you foresee in 2025?
Although generative AI is still in its nascent stages, the Open Worldwide Application Security Project (OWASP) has already published a top 10 security risk list for large language models (LLMs). These risks will require defenses against threats such as DDoS attacks, sensitive information disclosure, and runtime security issues. Additionally, cybersecurity teams must develop skills to effectively leverage and safeguard these models.
API risk will continue to be a critical concern with rapid scalability. The OWASP Top 10 API Security Risks list highlights the need for skills and security controls to address business logic attacks. While APIs remain vulnerable to traditional threats like local file inclusion, these new prevalent attack vectors demand enhanced capabilities for visibility and swift response. In 2025, it will be even more crucial to identify rogue or forgotten systems that become unmanaged "zombies," train developers on common vulnerabilities, and validate runtime of secure code deployment. The increasing number of major breaches stemming from public API abuse underscores the importance of the ongoing monitoring and mitigating of such activities before they escalate to material impacts.

Tricia Howard, Scrybe of Cybersecurity Magicks
What stood out for you in 2024?
Defenders are getting bombarded, and every year it seems to get worse.
What stood out to me this year was how much the attack surface has grown — not only from implementing new technology but also because the technology itself creates new threat actors. I’m not talking about ChatGPT writing malware, that’s a whole OTHER issue. The technical barrier to entry for attackers has been lowered significantly, making the gap between defenders and attackers even more disproportionate as a result — and with generative AI and LLMs becoming the norm, that gap could effectively become a big hole.
Technology is advancing at speeds that were previously unthinkable: We’re not just fighting the nation-state level of sophistication, we’re also fighting any skiddie with an ax to grind. The attacker’s time to market has shrunk to mere hours after disclosure, some of whom have multiple exploit options. Defenders are getting bombarded, and every year it seems to get worse.
New technology has also offered new attack paths out of old threats. Threats that you previously mitigated can now have an entirely new entry point, or a vector could do more damage post-exploit. A significant amount of the malware we saw this year took advantage of old vulnerabilities like Log4Shell, some more than a decade old, and even some without proper CVE assignment. A seasoned botnet author can expand their toolkit to include Golang-based malware as it’s harder to obfuscate, and any person with access to a credit card can run a full-scale ransomware or DDoS attack as easily as buying a pair of shoes online.
What notable issues do you foresee in 2025?
As this ever-changing digital forest we call the internet becomes increasingly interconnected, even more places will emerge for attackers to strike. Next year, organizations should go back to basics by reexamining and refreshing their patch management and incident response strategy, even for previously unassuming vulnerabilities. Considering that attackers can scan for vulnerabilities and spread malware at warp speed — and an input mismatch can affect the globe — assuming a breach will be the way to go in 2025.
Conclusion
Forewarned is forearmed, and Akamai is committed to keeping clients, colleagues, and the public informed of the threats that are impacting organizations now, as well as those that are lurking around the corner.
In addition to practical solutions for today’s threats, we are hyper-focused on the transformative changes AI is bringing to both attack strategies and defenses. Akamai researchers are also directing our attention to the next generation of technology — including quantum computing — and working with our clients to help them prepare for the future.
Learn more
We look forward to sharing more insights with you in 2025. Visit us to see our SOTI report and research library — and if you have questions, please reach out to us.
Happy 2025 and stay safe!