Ransomware is a type of malicious software, or malware. After being downloaded to a server or a user’s computer, ransomware encrypts files on the device, blocking access and rendering files unusable until a ransom is paid. Versions like REvil and WannaCry ransomware are responsible for some of the largest and most devastating cyberattacks. Ransomware may be spread through Trojan files in an email that appears to be legitimate, but actually contains malware. Botnets like the massive Meris botnet may also be used to propagate ransomware or find vulnerabilities that can be exploited by ransomware gangs.
Stop ransomware with Zero Trust principles
Improve breach protection by securing every endpoint with granular access controls, from servers to user devices.
Customer stories
Harden your security posture with our complementary Zero Trust solutions
Frequently Asked Questions
Malware is a broad term for any software designed to harm or exploit a computer or network, while ransomware is a specific type of malware that encrypts a victim’s data and demands a ransom payment to restore access. In essence, ransomware is a type of malicious software, but not all malware is ransomware.
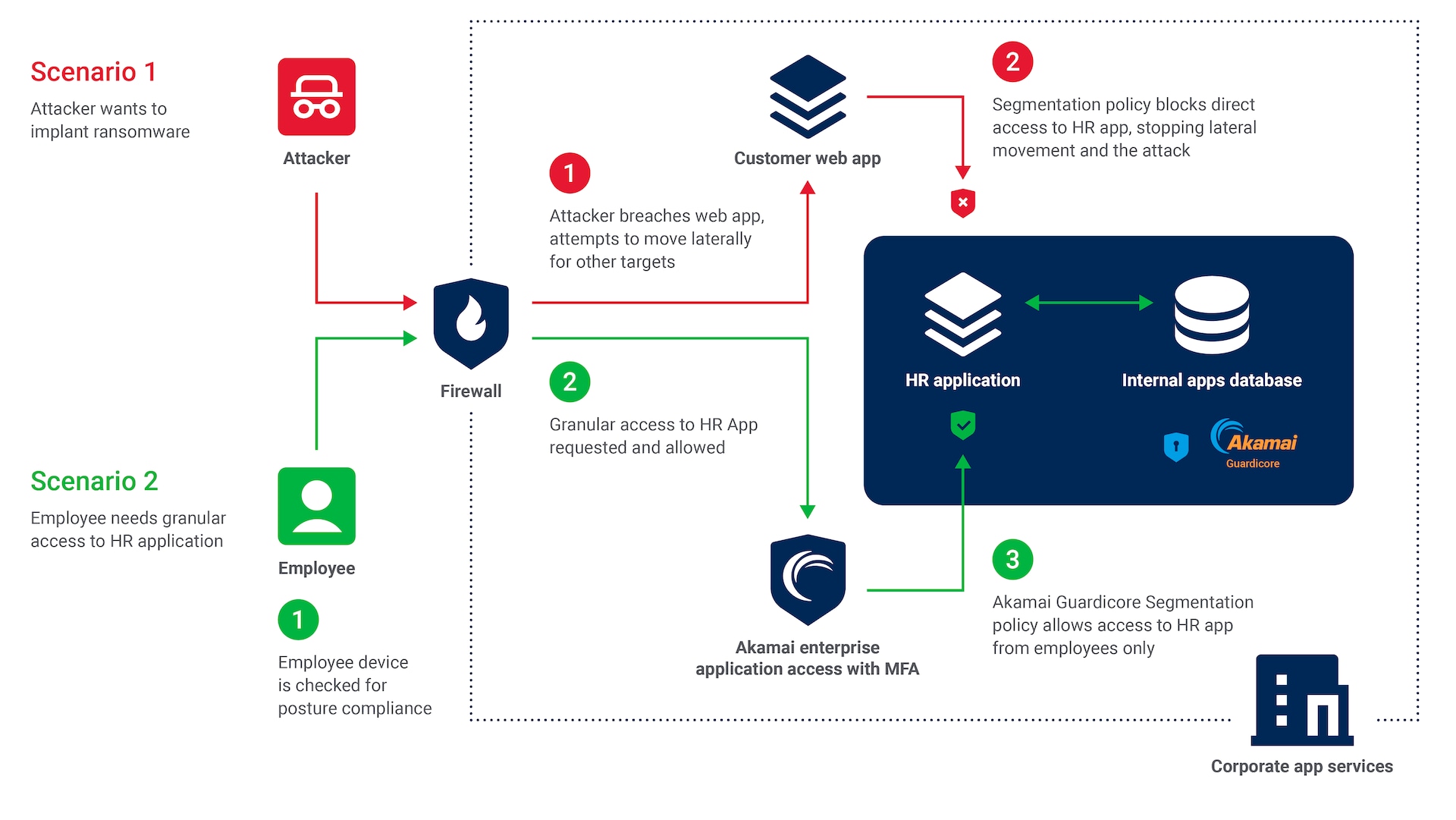
Most ransomware attacks use social engineering techniques such as phishing attacks: emails or fake websites to dupe users into revealing credentials that allow attackers to gain access to an IT environment.
Then the malware uses lateral movement to find and infect high-value assets. Some ransomware spreads like a worm throughout the network, and some are botnets that infect thousands or millions of machines with malware that gives attackers the ability to control the devices.
Having a strong incident response plan is key to responding to ransomware, as well as making sure you have the right security solutions that can stop it.
Akamai’s security solutions enable you to protect against ransomware by reducing the chance of initial infection as well as allowing you to stop lateral movement in real time, containing the breach and making recovery easier.
With a combination of Akamai’s Zero Trust Network Access, MFA, and threat detection, you can reduce your business’s attack surface to minimize vulnerabilities.
Of course, awareness training of employees about the risks of ransomware should be at the foundation of any cybersecurity best practice.
The most effective protection against ransomware involves a multilayered approach, including robust backups, strong authentication with multi-factor authentication, regular system updates, and the use of comprehensive security software.
Data backups help to ensure sensitive data can be restored after an attack, and strong authentication prevents unauthorized access.
Keeping all device operating systems and apps connected to the network up to date helps mitigate vulnerabilities that ransomware exploits. Security software helps detect and block malicious activity.
Akamai’s solutions cater to both cloud-based and on-premises environments, ensuring versatile protection from ransomware across your infrastructure.
Ransomware protection resources

Request your personalized demo
Let us show you how to stop lateral movement with granular controls.
- Instant visibility — Immediately visualize all of your assets and their communications to investigate the breach and validate containment.
- Fast time to policy — Enforce policy in just a few clicks to contain the spread of ransomware infection and limit the scale of the breach.
- Prevent lateral movement during recovery — Easily block all incoming connections during recovery to prevent reinfection.
Thank you for your request.
An Akamai expert will reach out soon.