Five Ways to Prevent and Protect Against Ransomware Attacks
Ransomware is a pervasive type of malware that encrypts and restricts access to an enterprise’s data, including files, documents, and images. Cybercriminals then demand a ransom payment — often in a cryptocurrency like bitcoin — in exchange for restoring the data. If the ransom isn’t fulfilled within the specified period, the attacker either destroys or publicly releases that data to the internet, often via sites on the dark web.
Ransomware incidents pose a significant threat, especially for enterprises with large volumes of proprietary and customer data. Not only is there the upfront cost of paying off a ransom, but ransomware cyberattacks can also damage brand reputation and put organizations at risk of violating data privacy laws and regulations.
Proactive, holistic ransomware protection and prevention measures are crucial to your enterprise’s continued success — especially considering the following statistics:
The share of global organizations affected by ransomware attacks increased from 55.1% in 2018 to 72.7% in 2023.
The estimated cost of cybercrime attacks is projected to increase to US$13.82 trillion by 2028.
Network downtime, critical data loss, and brand/reputation damage are three of the biggest issues for organizations after a ransomware attack.
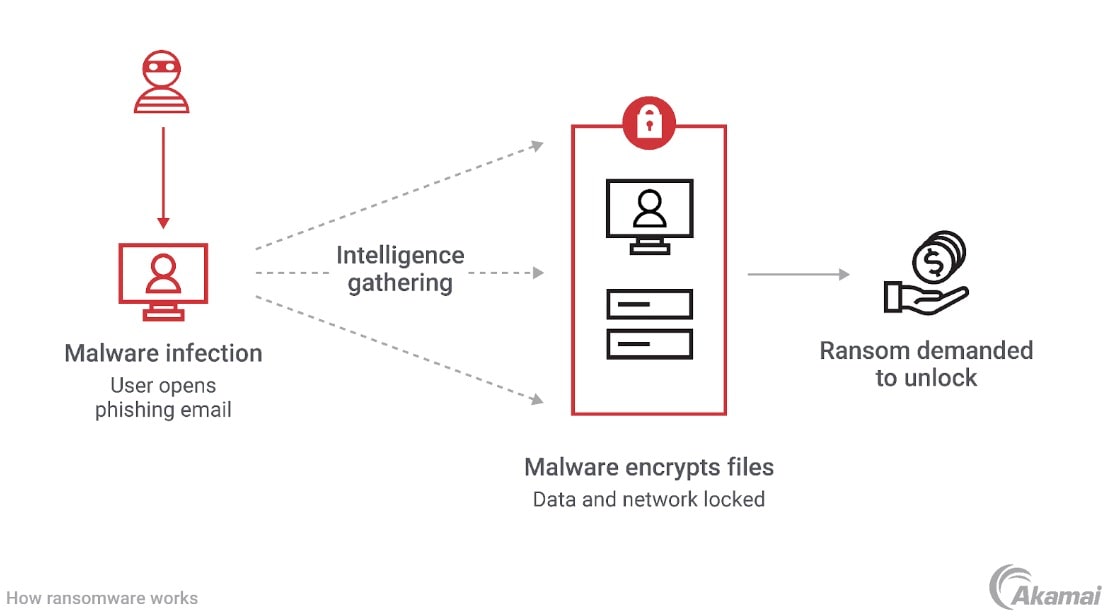
Read on to learn how ransomware infects target devices and the five steps you can take to protect your digital systems from cybercriminals.
How is ransomware delivered?
Ransomware is often delivered through compromised websites or phishing emails that appear to have been sent from a legitimate, trusted source. These emails entice users to click malicious links or open attachments that automatically download the ransomware to the user’s device without their consent — and often without their knowledge.
The ransomware may also run after download and without any interaction. Once executed, the ransomware may encrypt the data on that device, but it’s more likely that the attacker will use the compromised device as the means to move throughout the network to discover high-value targets, such as customer lists or company confidential data.
How to prevent ransomware attacks
Now that you understand how ransomware infections occur, you can apply the security measures needed to protect your organization from these devastating attacks. The following five ways can help you prevent these attacks:
1. Assess your ransomware risk
Before putting ransomware prevention and protection measures into place, try to analyze the specific ways that your organization may be at risk — evaluate potential vulnerabilities, system misconfigurations, attack vectors, and potentially malicious network activity. Document this information in a ransomware risk report, so your team can choose the most appropriate ransomware prevention and attack mitigation measures for your organization.
Wondering where to start? The Center for Internet Security’s Ransomware Business Impact Analysis Tool can help you quantify the likelihood and potential impacts of a ransomware attack on your enterprise so you can craft a sound incident response plan against hackers.
2. Update your organization’s endpoint devices
Software and operating system vendors frequently release new security and antivirus updates — called patches — for their products. These updates are often designed to address newly discovered security vulnerabilities and emerging malware types — including new ransomware variants. By frequently auditing organization-wide devices, your IT team can discover and address outdated operating systems and applications.
Contemporary operating systems, such as Microsoft Windows, macOS, iOS, Android, and others, offer frequent, proactive patches designed to help bolster endpoint security and protect your devices against ransomware. Applications may automatically update when new updates get released, or they may require a manual update via a web page.
However, in some cases, when a vulnerability is discovered and reported, it may take time for the source code creators to develop and distribute a patch — leaving devices at risk. In these cases, you can apply microsegmentation along with monitoring solutions like Akamai Hunt to protect the vulnerable asset until a patch has been created, filling the critical time gap between when a vulnerability is detected and a patch is issued.
3. Create frequent and thorough offline data backups
At the outset of a successful ransomware attack, the attacker encrypts an organization’s proprietary and customer data and makes it inaccessible to the organization. If the organization neglects to pay the attacker’s ransom demands, their compromised data may be affected in the way specified by the attacker. In some cases, this can mean that sensitive data will be publicly released via sites on the dark web. In other cases, the data will be outright destroyed.
In the latter scenario, having up-to-date backup files for all your organization’s data can help you recover your data. Of course, if your backups are part of the impacted dataset, they’ll be inaccessible. It is best practice to store backup files on devices that are strictly segmented away from the main network or the internet so they can’t be remotely targeted by attackers.
Cloud services that retain previous file versions allow you to roll your compromised data back to an unencrypted version to alleviate the effects of a ransomware attack. Be sure to verify that your backups weren’t infected because of an unknown internet or intranet connection before rolling back so you don’t risk further compromising your data and devices.
Alternatively, you can externally offload your organization’s data to the cloud. Look for cloud storage solutions that offer dependable, easily accessible storage and management functionality you can use to automatically create daily, weekly, or biweekly data backups for your entire organization.
4. Educate employees to recognize potential ransomware attacks
Firewalls can only do so much to protect your organization from external cyberthreats. Malicious software can make its way to unsuspecting organization members in the form of suspicious emails. So the onus is on everyone within your organization, not just those on security teams, to practice strong email security and help stop ransomware attacks from occurring. It’s good practice to mandate ransomware awareness training and education that focuses on:
- Email senders
- Links
- Email attachments
- Remote desktop protocol and credential abuse
Email senders
When employees receive an email from an unfamiliar sender, or if the content of the email seems suspicious, they should forward that email to your organization’s IT department or help desk. Experts can assess the sender’s legitimacy by inspecting the domain name — for example, official email correspondence from Akamai always contains “@akamai.com” in the sender address — or by referring to a list of approved addresses.
Links
It’s essential that employees exercise caution when faced with a link to an unknown page, since sending malicious links is a primary ransomware distribution strategy. Educate employees to first inspect a link to verify its validity before clicking on it.
For example, if a link reads “akamai.net,” they can type “Akamai” into a search engine to discover that Akamai’s official website is “akamai.com” — thereby discovering that the link may be malicious in nature. In cases like these, employees should forward the correspondence containing the potentially malicious link to your organization's IT department or help desk to determine its safety and legitimacy.
Email attachments
Teach your employees to exercise caution when presented with an email that contains an attachment, even when it’s sent by a verified sender. Ransomware executables may be directly embedded in malicious emails, but are often disguised as other files — particularly compressed files with .zip or .rar extensions — which, once opened, will automatically begin encrypting the infected device’s data. No matter the situation, your employees should always alert your organization’s IT department or help desk to confirm an email attachment’s safety before opening it.
Remote desktop protocol and credential abuse
Remote desktop protocol (RDP) is a secure, interoperable protocol that establishes secure connections among clients, servers, and virtual machines, enabling users to remotely access servers and desktops. RDP can be abused, however. With credentials purchased off the dark web, cyberattackers can use brute-force or credential stuffing attacks to remotely log in to organizational systems while posing as a legitimate user — then infect the network with malware.
This approach works in tandem with other ransomware attack approaches like malicious email and link attacks because those tactics are used to procure user credential information that gets sold and used in RDP attacks. Always ensure that your employees understand the risks that can come with opening a link or email from an unknown user.
Of course, educating your organization’s employees to recognize potential ransomware attacks is only possible when your organization’s leaders are educated themselves. The Akamai Ransomware Threat Report by Akamai’s anti-malware security experts contains information on new and emerging ransomware toolkits as well as trends and mitigation techniques you can refer to in the event of a ransomware attack.
5. Reduce the attack surface by minimizing the use of VPNs
Attackers are continuously looking for ways to gain an initial foothold into an organization. One very common approach is to exploit any security vulnerabilities or misconfigurations in virtual private networks (VPNs), which are used to provide employees with remote access to resources such as business applications. Since a VPN provides network-level access, once an attacker has gained VPN access then they are free to move laterally to find high-value targets.
Zero Trust Network Access (ZTNA) solutions, such as Akamai Enterprise Application Access, are alternatives to VPNs. Based on Zero Trust principles, access is only provided once a user is authenticated and authorized to access specific resources based on the user’s security policy. In addition, access can be allowed or denied based on the context of the request; for example, Where is the user connecting from? What is the security posture of their device?; Does the device have the latest security patches applied?
Most important, network-level access is eliminated and users only have access to the resources that they need. In addition, inbound firewall ports can be closed because all application connections are made outbound through the firewall, which makes the applications undiscoverable by attackers. The elimination of network-level access, closing inbound firewall access, and hiding resources from the public internet can significantly reduce an organization's attack surface.
To ensure strong authentication for users, deploying a phish-proof multi-factor authentication (MFA) service such as Akamai MFA, in conjunction with ZTNA, eliminates the use of stolen or compromised employee login credentials to take over employee accounts.
Prevent enterprise ransomware attacks and strengthen cybersecurity with Akamai solutions
By partnering with an experienced cloud security provider, your enterprise can prevent ransomware from infecting your network and impacting your reputation.
If you’re struck by a ransomware attack, it’s crucial to minimize the attack surface by preventing lateral movement of the ransomware across your organization’s devices. Akamai Guardicore Segmentation offers granular controls that make it fast, easy, and intuitive to protect your organization and critical assets from lateral movement in on-premises and multi-cloud environments during a ransomware attack.
This solution enables process-level visibility of your organization’s asset communications and dependencies, as well as robust threat detection capabilities — all so you can more proactively assess risk, prevent ransomware attacks, and protect your organization while receiving real-time notifications on your organization’s security posture.