How Ransomware Is Delivered and How to Prevent Attacks
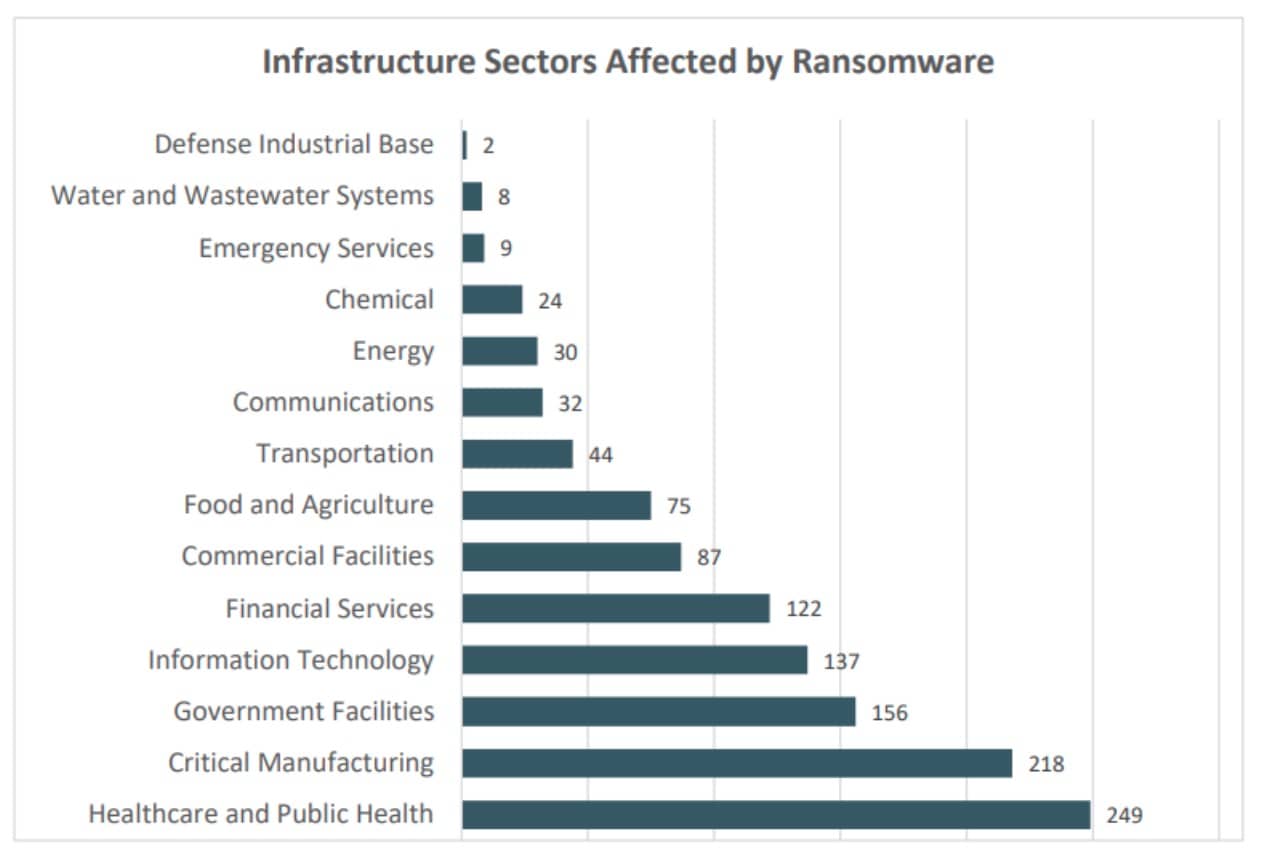
No individual or enterprise is exempt from the threat of ransomware attacks. In recent years, cyberattacks by ransomware have grown — both in number and sophistication. Unfortunately, this has shown that anyone can be a potential target (Figure 1).
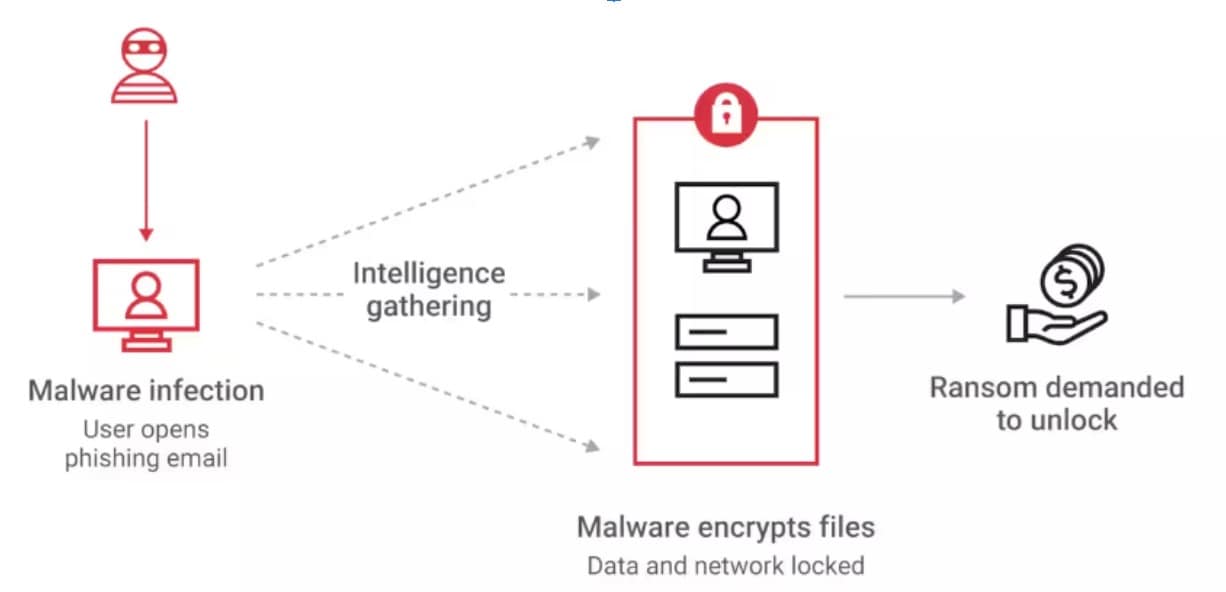
What is a ransomware attack? Let’s start with a basic definition. In short, ransomware is a form of cybercrime involving a type of malware that locks victims out of their own systems or data, using extortion with a hefty ransom to regain access (Figure 2).
Ransomware attacks can be crippling. Enterprises lose revenue. Their operations suffer heavy disruption. Their business reputation is damaged.
Understanding ransomware delivery and prevention methods
Attackers may be individual hackers, or they may be ransomware groups such as REvil, which operated a ransomware as a service operation. These attackers have several different methods for delivering ransomware. Common to all of them is the aim of exploiting either a human error or a technical vulnerability. Delivery channels include phishing emails or unpatched vulnerabilities in software.
Strong cybersecurity practices — such as regular system updates, employee training, and implementing continuous monitoring tools — can help you deal with these risks. Ultimately, the first step in effectively protecting your systems against these attacks is gaining a clear understanding of how ransomware is being delivered.
In this blog post, we’ll explore the most common methods for spreading ransomware, and provide you with actionable steps to prevent these attacks.
Primary ransomware delivery channels
How do ransomware threats make their way into your network? Knowing where your security gaps are will help as you develop defenses to stop attacks before they cause damage. Let’s look at three primary channels through which ransomware is commonly delivered.
#1: Email phishing: The gateway to ransomware infection
You’ve read the news and heard the stories. A ransomware attack takes down a company’s operations by locking down their network drive and holding the sensitive data hostage. What was the root cause? An employee accidentally clicked on a link in a phishing email scam or downloaded a malicious attachment.
Email phishing attempts are an incredibly common — and all too effective — channel for delivering ransomware. These emails are crafted to appear as if they’re from legitimate sources, such as a financial institution, healthcare provider, or social media site. By appearing authentic and genuine, these emails trick users into clicking malicious links or opening infected attachments. In many cases, these emails evade basic filters and land directly in users’ inboxes.
Social engineering plays an important role in convincing users to download ransomware via phishing emails. Emails are carefully crafted, creating a sense of urgency or mimicking a trusted source, such as a colleague or a well-known institution. Links in phishing emails may redirect users to compromised websites or apps that silently download ransomware in the background.
Alternatively, attachments may contain executable files or documents programmed with dangerous macros. On the surface, these documents may look like legitimate invoices or reports, making the underlying malware difficult to spot.
Unsuspecting recipients fall victim to the scheme by clicking to download and opening the attachment. Then, the ransomware installs itself on the user’s device. The system breach goes unnoticed, and the malicious software begins encrypting files, rendering them inaccessible without the decryption key.
#2: Exploiting vulnerabilities: Drive-by downloads and exploit kits
Hackers may also take advantage of vulnerabilities in outdated or unpatched software. These kinds of vulnerabilities are found in web browsers or old plug-ins like Flash, Java, or PDF viewers. This is the starting point for cybercriminals to use drive-by downloads or exploit kits to silently deliver ransomware to their victims’ machines.
A malicious web page or pop-up notification may have embedded scripts or hidden code meant to exploit weaknesses in insecure browsers or plug-ins. This code initiates a drive-by download, which is the automatic downloading of a file in the background without any user interaction. The key vulnerability here is within the browser or plug-in, which is why keeping them updated is essential.
The downloaded ransomware file will continue the attack, exploiting other weaknesses in the victim's system to gain control and execute malicious code. Exploit kits automate the process of scanning systems for these vulnerabilities, whether in the browser or other outdated software. After detecting a vulnerability, the exploit kit injects the ransomware payload, often with no visible sign until files are encrypted.
To prevent these attacks, it’s critical to regularly update your browsers, plug-ins, and operating systems.
#3: Remote Desktop Protocol and remote connections
As recent years have brought about the rise of remote work, the use of Remote Desktop Protocol (RDP) has increased significantly. RDP allows users to remotely access and control systems. Although it’s meant for convenience and access, the use of RDP without proper security measures can open the door for attackers.
Attackers begin by scanning targeted machines for exposed RDP ports. They couple this with a brute-force attack to guess valid login credentials. After gaining access to a vulnerable machine, the attackers can disable security features or alter system settings. From there, they can manually deploy their ransomware.
The attack vectors for exploiting these remote connections depend on:
Weak passwords
Default (and insecure) configurations
Unpatched RDP software
Once attackers have made their way inside a machine and network, they can move laterally and spread ransomware. They will then disable security software and delete backups, making recovery difficult.
To prevent RDP-based attacks, organizations must enforce strong passwords, use multi-factor authentication (MFA), and monitor remote access logs for suspicious activity.
How to prevent ransomware from infiltrating your information
There is no single solution that you can implement to guarantee comprehensive protection against ransomware attacks. Instead, you’ll need a proactive and layered approach that combines advanced security measures with strong cybersecurity practices. Let’s walk through several key strategies that can help you protect your systems.
Implementing advanced security measures
Start with a solid foundation of tools to implement advanced security measures that will stop ransomware before it infects your system. This first line of defense includes:
Antivirus and anti-malware software: Detects and blocks various forms of malware, including ransomware, before they can be executed on your machine
Behavioral analysis and real-time monitoring: Identifies and alerts you to suspicious activity in your network, preventing the installation of ransomware on targeted machines
Firewalls: Monitors network traffic and restricts access, reducing the likelihood of ransomware entering your network through open ports of vulnerabilities
Endpoint security: Ensures that individual devices are continuously monitored and protected, preventing ransomware from spreading across your organization
Zero Trust security: Enforces strict identity verification for every user or device trying to access resources, and enables granular segmentation of critical applications, minimizing the risk of ransomware spreading by assuming no one is trusted by default
Keeping these solutions up-to-date is crucial to staying protected against new variants of ransomware that continue to emerge.
Adopting cybersecurity best practices
Even if you have advanced security tools in place, poor cybersecurity practices will undermine your defenses. Security tools must work hand-in-hand with best practices. Let’s highlight some basic security best practices that any organization should put in place.
Regular software updates
Patching your software is critical for closing the security gaps that attackers often exploit. One of the most common entry points for ransomware is outdated software. When a security vulnerability is discovered in a piece of software, the software manufacturer should release an update to patch the security issue.
Yet all too often, software users put off applying the fix — and sometimes there is no fix to apply. This is what attackers are counting on when they attempt to exploit the known vulnerability.
WannaCry was a highly publicized ransomware attack in 2017, and it exploited the server message block (SMB) of unpatched machines running Microsoft Windows. In total, more than 300,000 computers across 100,000 businesses in 150 countries were infected with the ransomware.
By patching vulnerabilities whenever possible and updating your systems regularly, you shrink the window of exploitability, minimizing the risk that attackers will prey on known weaknesses to deliver ransomware.
User education
Since phishing remains a top delivery method for ransomware, educating employees on how to recognize suspicious emails, links, and attachments can prevent them from inadvertently downloading ransomware. Ongoing training helps users stay vigilant against evolving cyberthreats.
Multi-factor authentication
Add an extra layer of security by requiring users to authenticate with more than just a password. In the case of ransomware delivery methods, protecting RDP connections with FIDO2-based MFA is especially important. FIDO2 MFA is phish-proof by design, making it significantly harder for attackers to gain unauthorized access and deploy ransomware within your system.
Akamai Guardicore Segmentation
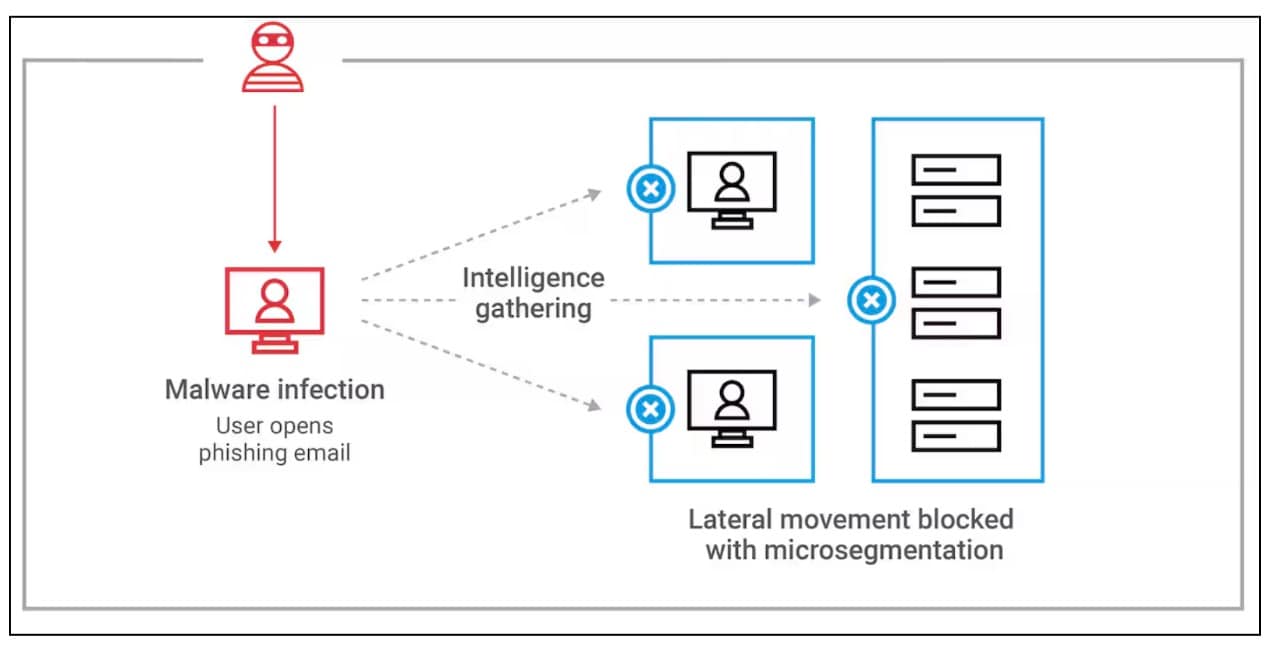
In addition to traditional security tools and best practices, microsegmentation is one of the most effective strategies to limit the spread of ransomware once it has entered your network. Akamai Guardicore Segmentation enables your organization to isolate critical systems and workloads. This isolation helps to prevent ransomware from moving laterally across your network and wreaking havoc.
Microsegmentation works by creating virtual boundaries around different parts of your network. These boundaries restrict communication flows among applications, users, and devices. In the case that ransomware breaches one area of your network, it cannot easily spread to other parts of the network. Microsegmentation essentially minimizes the “blast radius” of a ransomware attack (Figure 3).
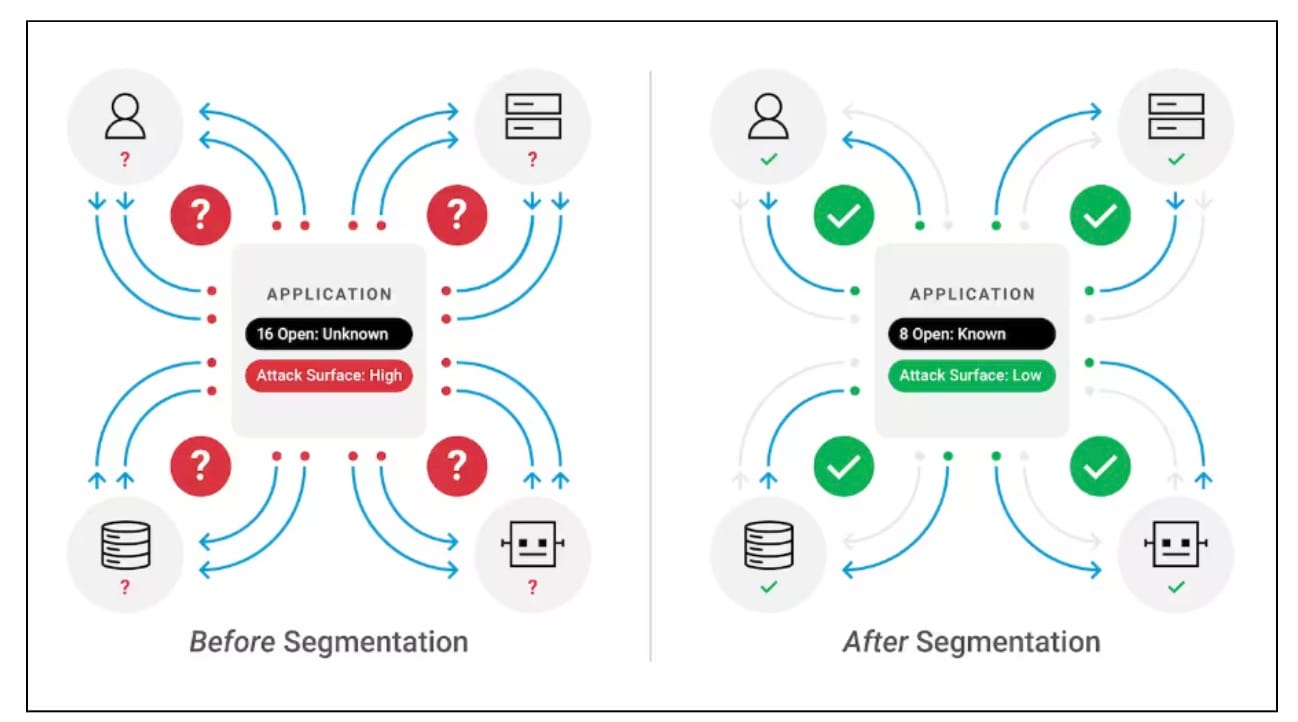
Akamai Guardicore Segmentation gives you centralized visibility and control across environments and infrastructures. Your security team can enforce policies and monitor network traffic in real time- on-premises, in the cloud, and across devices. With this level of visibility, your team will be more effective at detecting and blocking unauthorized activity, ensuring that ransomware cannot spread unchecked (Figure 4).
Strengthening defenses against ransomware delivery
Ransomware attacks are constantly evolving and growing increasingly sophisticated. However, organizations are certainly not defenseless. Protection begins with a strong understanding of the most common delivery methods:
Phishing emails
Exploiting vulnerabilities in unpatched software
RDP and remote connections
With this foundational understanding in place, organizations can protect themselves with a layered defense strategy, including:
Traditional security tools, such as anti-malware applications and firewalls
Security best practices, such as regularly updating software and enforcing MFA
Advanced microsegmentation solutions, like Akamai Guardicore Segmentation, to minimize the blast radius of an attack
By combining reliable tools, robust practices, and advanced network protection, you can significantly improve your risk mitigation and reduce the impact of ransomware attacks.