How Does Ransomware Actually Spread?

Ransomware can be a lucrative business, with payoffs ranging from thousands to millions of dollars. While phishing emails remain a popular tactic to introduce ransomware into target organizations, it’s not the only vehicle that bad actors leverage. Since paid ransoms can mean big money, attackers are willing to use any technique at their disposal to breach perimeter defenses and maximize damage in environments.
Unfortunately, despite the best perimeter defenses, breaches are now a matter of when and not just if these days. This is why organizations need a defense strategy that minimizes an attack’s effectiveness and stops malware propagation within your network once an attacker is inside. Unless an organization has made an effort to strengthen its defenses beyond the perimeter, the malware will likely move laterally quickly, capturing whatever assets it can reach. Often by the time IT security receives a ransom note, it’s too late.
How can ransomware reach your system?
Today, through a mix of outdated technology, “good enough” defense strategies focused solely on perimeters and endpoints, lack of training (and poor security etiquette) and no known “silver bullet” solution — organizations of all sizes are at risk of a hard-hitting ransomware attack. Some common techniques for introducing and spreading malware include:
Emails: Despite security teams’ best efforts and training attempts, bad actors know that a naive end user can be relied on to open and interact with a convincing enough phishing email somewhere. These emails can be general or involve spear phishing tactics that tailor the contents to a specific organization or person, hoping that it will prompt an interaction, such as opening an attachment or clicking a link, and give the bad actors a vehicle to deliver malware.
Malicious URLs: Malicious URLs appear commonly in phishing campaigns, but they can also be embedded in a website, or anywhere a user may click. In the case of ransomware, after the target interacts with the URL, the malware will often attempt to auto-install itself onto the victim’s machine, where it can begin to propagate and spread to multiple assets.
Remote Desktop Protocol: The use of virtual desktop infrastructure (VDI) has continued to increase steadily, especially with employees transitioning to a work-from-home model in 2020. Unfortunately, it’s also become a rapidly growing attack surface. One significant VDI risk includes the fact all infrastructure and applications are often on the same server. If an attacker can successfully introduce malware, it can be challenging to detect until it’s too late. Additionally, without granular policies that can control east-west traffic within a network segment, an attacker has the opportunity to maximize damage by encrypting anything they can reach. Since desktops are likely to be shared among a large number of users, this means bad actors may only be a step away from moving laterally to other critical assets, applications, and data.
The lateral spread of ransomware
So, how does a typical ransomware attack unfold?
Postmortem analyses on successful ransomware attacks have revealed that poor segmentation practices often top the security gap list that prevented an organization from stopping or containing the attack.
Once an organization is infected with ransomware, restoring an environment can be a challenge. In many cases, backups are quickly located and encrypted, cutting off the easiest path to recovery. Attackers can achieve this, and maximize the assets they encrypt, by moving laterally from the point of entry to other areas where they can harvest credentials with administrator privileges. This might mean a domain controller, an IT person’s laptop, or any number of other systems that privileged users access regularly. Finally, when a bad actor is ready to issue their ransom note, the attack is usually escalated to other critical systems in a rapid motion that can take as little as one day.
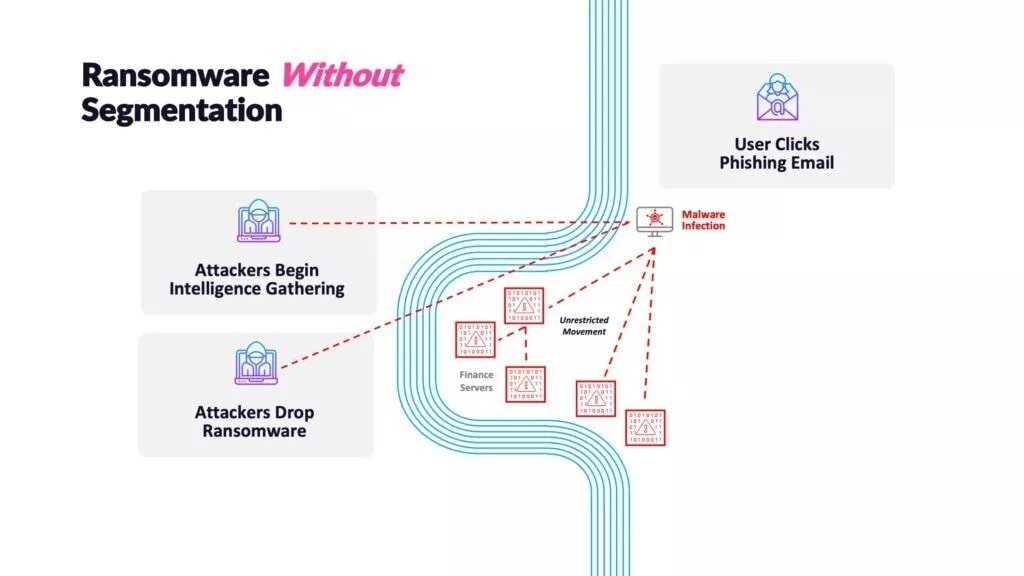
Let’s step through a simple example where a user infects their local machine by clicking on a piece of malware. The malware gives the attacker a jumping-off point for lateral movement towards more sensitive systems. Then, with nothing holding them back, they can drop ransomware without restriction across the environment.
In contrast, with good segmentation boundaries in place, there may still be a point of compromise. Still, an attacker’s ability to move laterally is blocked, preventing them from advancing the attack.
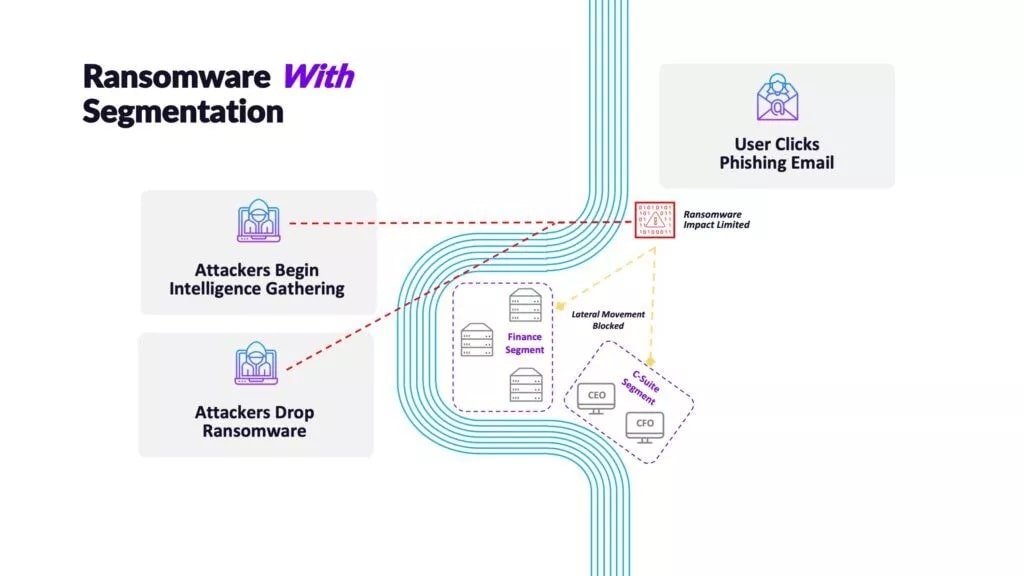
At the end of the day, one of the best defenses against ransomware is preventing lateral movement within your perimeter. However, this can be difficult to realize for east-west traffic with traditional firewalls. In addition, while you can achieve some segmentation using VLANs, it’s often broad, and it’s not exactly the most agile approach when you need to isolate assets on the fly, such as in the event of a successful breach.
If you can stop malware from spreading from beyond its initial landing point, you greatly reduce the impact of a breach enabling you to avoid the massive clean-up efforts and business downtime that can result from a successful ransomware attack.



