9 Malware Types Enterprise Professionals Need to Know
Executive summary
Malware can damage or disrupt an IT system, or give hackers access to an organization’s IT environment.
In today’s digital era, malware can violate data security for everyone — but attacks are especially devastating for enterprise organizations.
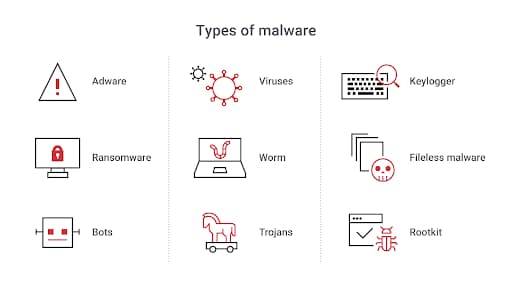
Common types of malware include adware, ransomware, bots, computer viruses, worms, Trojans, keyloggers, fileless malware, and rootkits.
Data security is everything for enterprise organizations. Read on to learn about malware and nine common types of malware so you can be more proactive in bolstering your business’s cybersecurity by protecting it from cybercriminals.
What is malware?
Malicious software, or malware, is a software program or file designed to damage or disrupt an IT system, or to give hackers access to an organization’s IT environment. Attackers use a variety of techniques to install and launch malware on infected computer systems, including writing malicious code into websites, inserting malicious links, weaponizing email attachments, uploading malicious files, or loading an executable file onto a USB drive instead of just a hard drive.
Cybercrime will cost organizations US$10.5 trillion annually by 2025.
In 2022, global organizations suffered 5.5 billion malware attacks.
Ransomware is expected to cost global organizations US$20 billion by 2025 and US$80 billion by 2030.
In today’s complex digital era, malware threatens to violate the security of sensitive information and other data for consumers and companies alike — and attacks can be especially devastating for enterprise organizations. When a cyberattacker infects your personal device with this harmful (and often invisible) software, they can access your personal data while you scramble to remove all traces of the offending malware.
But when your company’s data, apps, and cybersecurity become compromised, you also face halts to business and you risk violating data privacy rules and regulations. Worst of all, you lose your most valuable resource: the consumer and partner trust you’ve spent years building.
9 common types of malware
The first step in protecting your data from malware infections is to understand the different types of malware that are out there. The nine most common types of malware you should know about include:
Adware
Ransomware
Bots
Computer viruses
Worms
Trojans
Keyloggers
Fileless malware
Rootkits
 Learn more about nine malware types so that you can protect your business and your customers from cyberattackers
Learn more about nine malware types so that you can protect your business and your customers from cyberattackers
1. Adware
Adware is a type of malware that inundates users with advertisements by collecting their personal information, as well as their browser, download, and even keystroke history. These ads may take the form of pop-up windows or additions to a browser or operating system’s toolbar tray. Some adware will sell a user’s browsing history to third-party organizations, and those recipients will tailor their own ads to that user — thus creating a vicious cycle of unwanted ads for the user.
Adware can infect a user’s device both passively (through seemingly safe program downloads) and actively (through browser vulnerability exploitation). As such, everyone — even particularly savvy internet users — risks falling victim to adware.
Spyware is a type of adware that differs in one key area: It secretly gathers a user’s personal and browsing data and transmits it to a cyberattacker. Both adware and spyware are distinct from malvertising, a recent cyberattack technique in which malicious code is injected into an enterprise system through seemingly innocuous ads.
2. Ransomware
Ransomware is malware that accesses and encrypts an organization’s files, documents, apps, and images once deployed. The cyberattacker then demands a ransom from the victim — typically in a specified cryptocurrency — in exchange for restored access to the uncorrupted data. Ransomware typically infects a network’s device via phishing emails containing a malware download or attachments containing a built-in downloader.
Many ransomware programs have a built-in timer — and once the time expires, the program will delete the compromised data or distribute it online. Ransomware victims are typically large enterprises, federal governments, and global infrastructure and healthcare organizations. These victims often feel a great degree of pressure to comply with the attacker’s ransom demands since the compromised data contains both proprietary and customer information.
This has made ransomware a particularly pervasive malware type; it’s projected that the costs of worldwide ransomware attacks will exceed US$265 billion by 2031.
3. Bots
Bots — sometimes known as spiders or crawlers — are an increasingly pervasive type of malware. After infecting a victim’s device, they connect back to a server that centralizes all compromised devices, including mobile devices, into a command center operated by the attacker (also known as a botnet). This malware gets downloaded onto a device via harmful websites and email attachments, or via scare tactics that tell users their computer will contract a virus if they don’t click a link.
Bots self-propagate, meaning they can scan for and attack other vulnerable servers from that central server. They often go unnoticed for long periods because they use common file and process names. Like other types of malware, bots can obtain sensitive data like credentials and financial information, but also relay spam, capture and analyze packet data, launch distributed denial-of-service (DDoS) attacks, and exploit backdoors opened by other viruses and worms — or open new ones.
4. Viruses
Viruses are dangerous software or code samples attached to a document or file. By misrepresenting the details of the virus-carrying file, cybercriminals trick victims into unintentionally deploying the virus’s code.
Once downloaded and deployed by a user, viruses attack the infected device’s systems through a process known as self-propagation in which the virus makes copies of itself. In doing so, viruses can seize control of device applications, steal and transmit private and proprietary data back to the attacker, initiate DDoS attacks, increase their attack surface by distributing infected files to contacts available on the victim’s device, and more.
5. Worms
Like viruses, worms are self-replicating malware that attempt to infect all of a network’s devices. Although viruses require a user to unintentionally deploy them, worms can deploy automatically. They’re also not dependent on a software host, and can be installed onto a device by a number of means, including via email and direct message attachments, malicious websites, or existing software vulnerabilities.
Worms can impact a victim’s device in many ways, including:
File modification and deletion
Theft of personal and proprietary data
Backdoor installation
DDoS and ransomware attacks
Botnet generation
6. Trojans
Trojans enable backdoor and remote access capability on victims’ devices. The name of this malware invokes the Greek myth of the Trojan horse, in which Greek soldiers were hiding inside the giant wooden horse that they gifted to the Trojans. Trojan malware similarly appears to be a legitimate software program, but it executes hidden malicious code once installed. As with other types of malware, users may download a Trojan from anywhere — from legitimate-seeming websites and emails to online games and instant messaging applications.
Once their device becomes infected, users continue to use it unaware that the Trojan is siphoning their data back to the cyberattacker, all the while infecting other exposed devices on the user’s network.
7. Keyloggers
Keyloggers remotely track, record, and transmit everything users do on their devices, including keystrokes entered, web pages opened, emails sent, and more. While some keyloggers aren’t used for malicious or illegal purposes — such as when a parent monitors a child’s screen time or a company tracks an employee’s productivity — cyberattackers use keyloggers to obtain credentials for any number of services used by their victims (like email clients or bank accounts).
One common approach to infecting a user’s device with a keylogger is to target unsecured wireless computer networks to which many users connect — like those found in hotels, restaurants, or other public places. Cyberattackers then train their keylogger on those connected devices and record the desired results. After executing and recording a certain number of user interactions, some keyloggers delete themselves to hide from users and malware detection tools.
8. Fileless malware
Many different types of malware impact a victim’s device by infecting their hard drive’s files. Fileless malware, however, directly infects a device’s memory rather than its files. Fileless malware will then search through and steal an organization’s data (user credentials and personal, bank, and credit card information, for example) from the device’s available memory.
Like other types of malware, fileless malware can reach a device through various methods, like a user downloading a file from an email or a deceptive webpage. Fileless malware’s key difference is that the core file itself is safe and will function as expected, but it contains an added malicious code sample that is injected into and executed from the target device’s memory, not the file itself.
This makes it difficult for malware detection tools and experts alike to determine where the malicious code originated. Fileless malware can also impact Windows devices in a specific way through registry manipulation, in which a threat actor takes advantage of a trusted Windows process. For example, when a user clicks on a malicious link, the Windows process will then write and execute code in the operating system’s registry.
9. Rootkits
The final malware type we’ll address in this blog post is rootkits. They enable access and control of a device or its software that the cyberattackers otherwise wouldn’t have proper authorization and authentication data to access. With full control over the target device, attackers can disrupt any antivirus software or security software and have complete agency to infect the system with other malware types like Trojans and worms.
As with many other malware types, attackers infect a victim’s device with rootkits through social engineering attacks such as fake websites and deceptive emails.
Protect your enterprise malware with Akamai
Now that you’re armed with important information about nine prevalent malware types, you can more proactively defend your organization against current and emerging cyberthreats.
Akamai App & API Protector includes our state-of-the-art malware protection service that rapidly scans file uploads at the edge to automatically detect and isolate any malware type before it reaches its victim. Adopting this anti-malware solution requires no changes to existing applications, which enables you to quickly scale this robust security solution across your entire organization while saving personnel time and energy that is better invested in your key value drivers.
In the event that your enterprise organization is impacted by a cyberattack, Akamai Guardicore Segmentation lets you isolate the injected malware to prevent it from propagating to devices across your network. This network segmentation solution helps you enforce Zero Trust principles across your data centers, multicloud environments, and endpoints with precise segmentation policies, real-time activity diagnostics on your IT environment, and informative network security alerts.
Talk to one of our experts to learn more about how anti-malware protection and network segmentation from our massively distributed edge and cloud platform can protect your business against threats.
Summary
In this blog post, we’ve examined nine key malware types — such as adware, keyloggers, and botnets — to prepare you and your security team to navigate current and emerging malware threats. We’ve also taken a close look at how each of these malware types targets and impacts enterprise organizations. Finally, we’ve spotlighted two Akamai solutions for combating malware threats: one that dynamically protects enterprise companies and their data from malware and another that segments your network to give you an extra layer of protection in case of a cyberattack.


![[Once] you’re armed with important information about nine prevalent malware types, you can more proactively defend your organization against current and emerging cyberthreats.](/site/zh/images/blog/2024/thumbnails/edge-1080x608-1.png)
