Zero Trust Network Access or ZTNA is controlled by security policies that determine which IT assets, users, and systems can safely communicate with each other. When policies are defined too narrowly, it can slow down critical processes and create bottlenecks. When policies are too broad, it creates an attack surface that is too difficult to protect.
Traditional network security models, such as perimeter-based security, rely on the assumption that everything inside a network can be trusted. However, this approach is no longer sufficient to protect today’s dynamic and distributed IT ecosystems, where private applications can be hosted anywhere, and employees require secure application access from everywhere, using managed and unmanaged devices.
Zero Trust Network Access (ZTNA) is an approach to providing secure access to resources (such as private applications) that focuses on strict access controls and security measures. ZTNA operates under the principle of “never trust, always verify,” which means that no user or device, whether inside or outside the network perimeter, should be automatically trusted. Instead, ZTNA verifies and authenticates every user and device before granting access to applications or resources, regardless of their location.
Background
In the past, organizations have relied on technology such as firewalls that built strong walls around its network. Access management that allows employees to use private applications is largely based on where an employee is located. If they are in the office and connected to the corporate network, then they are “trusted” and given access to applications and resources. Remote workforce employees who need secure remote access to the same applications and workloads will typically use a virtual private network (VPN) service to connect to these.
Businesses will likely apply different access permissions and access policies based on where the employee is located. If they are on-premises, they may have access to more resources. If they are remote, they may only have access to specific applications.
However, with the move to multicloud and work-from-anywhere models, enterprises have now realized that this method of managing access needs a new approach.
The Zero Trust security model
The concept of Zero Trust security offers far greater protection for enterprises than traditional perimeter defenses. Zero Trust security assumes that every user identity, device, system, and application is already compromised. ZTNA is a critical solution for any enterprise that wants to transition to a Zero Trust security model.
How ZTNA works
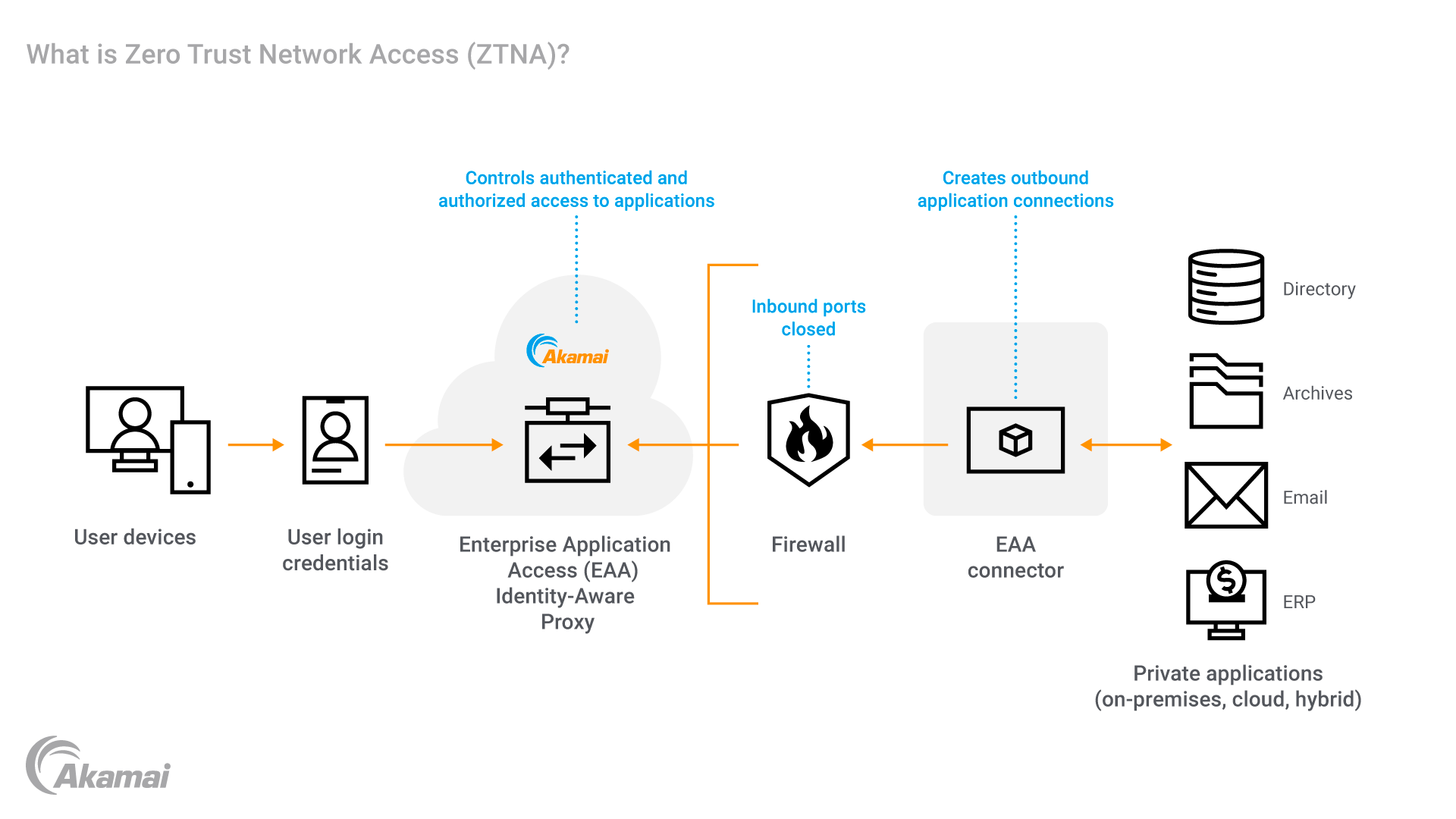
ZTNA is an architecture that grants secure access to applications and resources based on strong authentication, authorization, and context.
A ZTNA architecture provides access only to the applications and workloads that employees need to do their jobs, and not the entire network. Where an application is hosted is irrelevant — on-premises, public, or private cloud — authenticated users only get access to applications that they have been authorized to use. And with a ZTNA architecture, the employee’s location is irrelevant — the same access policies are applied when they are working from the office on the corporate network, at home, or at their favorite coffee shop.
A typical ZTNA solution uses a cloud-hosted Identity-Aware Proxy (IAP) that provides granular application access based on real-time signals such as user identity information and device posture signals. The second component is an access connector, most typically a virtual machine, which is deployed where private applications are deployed — on-premises or in cloud environments. The access connector links to the private application and makes an outbound connection to the IAP. When a user wants to access an application, the IAP authenticates the user, validates the device, and authorizes access to the application. The user is only granted access to applications that they need to do their job role and furthermore, that access is continuously assessed. If the device posture changes, then access can be revoked in near-real time.
How does ZTNA increase security posture?
Firstly, because the apps are hidden and not exposed to the public internet, cybercriminals cannot discover these applications. Secondly, because the access connector makes an outbound connection, all inbound access ports on the firewall can be closed. Thirdly, reducing the usage of VPNs in an enterprise helps to reduce the attack surface. Finally, enforcing the principles of the Zero Trust security model, and providing least-privilege access control, significantly reduces the ability for lateral movement.
What is Akamai’s Zero Trust Network Access solution?
Enterprise Application Access Give your workforce fast, secure remote access with Zero Trust Network Access from endpoint devices — with no more slow, clunky VPNs.
Secure Internet Access Explore Secure Internet Access, a cloud-based secure web gateway.
Akamai MFA (Multi-Factor Authentication) Prevent employee account takeover and data breaches with phish-proof MFA.
Frequently Asked Questions (FAQ)
The concept of Zero Trust Network Access offers far greater protection for enterprise networks than traditional perimeter defenses. Zero Trust security assumes that every user identity, device, system, and application is already compromised. Rather than focusing on a network perimeter, Zero Trust networks place perimeters around individual assets and strictly control secure access to them. The result: Attacks that originate within an IT environment can be quickly neutralized, as they are unable to spread quickly and easily.
Zero Trust Network Access is not without its challenges. While this approach enables a more rigorous security posture, it can also create enormous administrative burdens for security teams tasked with creating ZTNA policies. When policies are too restrictive, bottlenecks occur, and productivity or the overall user experience takes a hit. The key to adopting a Zero Trust framework is to find tools that greatly reduce the complexity of managing access and setting policies. That’s where Akamai can help.
First articulated by Forrester in 2010, the Zero Trust security model is a reaction to traditional network security that’s focused on building a strong perimeter while trusting assets and users within the network. Network security is a practice that often lets cyberattacks that have breached perimeter defenses spread quickly throughout an IT environment. In contrast, Zero Trust puts an end to the idea of a trusted network perimeter. It assumes that every user, device, system, and connection may already be compromised, and requires validation before it allows access to other IT assets.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.