SASE, or secure access service edge, is a security framework defined by Gartner. In a SASE architecture, security and network connectivity technologies converge in a single cloud-delivered platform to enable secure and fast digital transformation.
Enhance network security with Zero Trust principles
The nature of the IT network is rapidly changing, requiring a different approach to network security. Traditionally, security teams were focused on defending the perimeter of the IT network. Information security solutions were designed to keep malicious activity out while allowing legitimate network traffic in, and anything that was deemed “safe” within the network was automatically trusted.
But with the rise of cloud computing and remote workforces, the idea of a network perimeter has become obsolete. Legitimate users and applications are just as likely to seek access to IT resources from outside the network perimeter, and attackers will often move laterally within a network in addition to targeting it from outside.
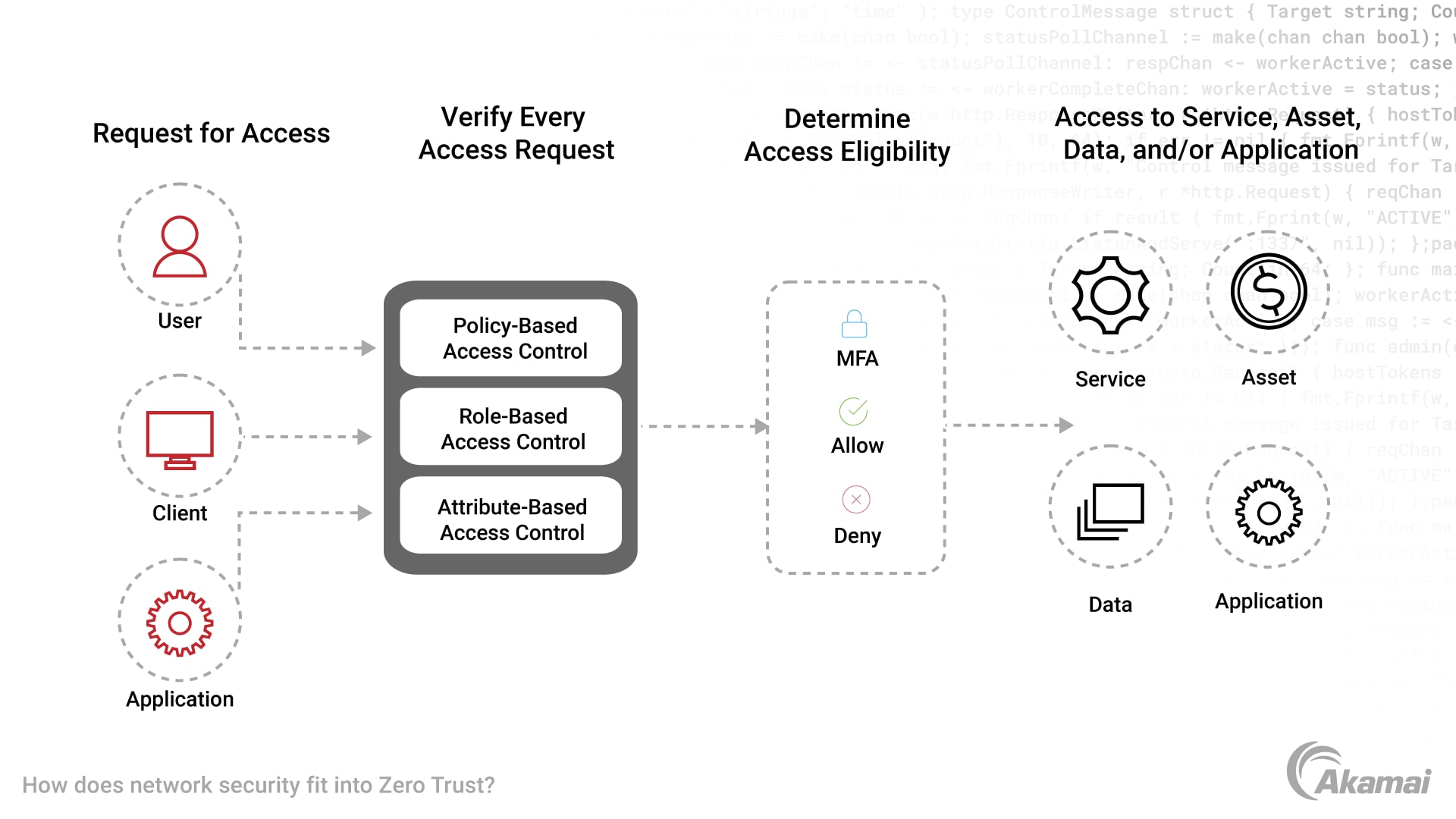
Zero Trust security is the answer to the challenges posed by this evolution in network infrastructure configurations. Zero Trust is a type of network security model based on the philosophy that no person or device inside or outside of the network should automatically be granted access to systems or services unless they are authenticated and continuously verified.
As a powerhouse in the network security space, Akamai delivers security solutions that support Zero Trust, securing remote access to corporate apps and the internet from anywhere, and reducing the impact of cyberthreats without hindering workforce productivity.
How Zero Trust improves network security
In a Zero Trust framework, all users and devices are assumed to be malicious or compromised until they have been verified as legitimate and authorized. This is in complete contrast to the traditional approach to network security, which automatically trusts any user, device, or request already within the network perimeter.
Zero Trust security requires strong authentication and authorization for every user and device before access is granted or data is transferred. Using behavioral analytics, filtering, and logging to verify actions and identify signs of compromise, security solutions that support the Zero Trust model should take note of any signs that a user is acting differently, or that a request for access is an anomaly. This fundamental shift in the approach to network security defeats many common security threats. It becomes much harder for hackers to take advantage of a vulnerability in the perimeter, gain unauthorized access, and then spend days or weeks exploiting sensitive data and applications once they are in the network.
With Zero Trust for network security, you can:
- Stop malicious attacks. A Zero Trust approach can proactively identify, block, and mitigate targeted threats like malware, spyware, ransomware, phishing, zero-day attacks, and other advanced campaigns to improve cyberthreat security.
- Provide secure access. Zero Trust security work can reduce the risk and complexity of providing fast and simple access for all users, including third-party vendors and providers.
- Minimize complexity and save on costs. A Zero Trust model reduces the complexity of enterprise access and network security, eliminating the need to make time-consuming and costly changes to traditional security tools.
Zero Trust network security with Akamai
Akamai provides a suite of cybersecurity solutions and services — powered by sophisticated threat intelligence — that support Zero Trust for network security. As the world’s largest compute platform, we have unparalleled insight into worldwide internet traffic and visibility into global attacks. This enables our security teams to develop in-depth understanding of emerging threats and informs our security measures to proactively and predictably stop the most sophisticated and dangerous attacks — without impacting network performance.
Secure Internet Access
Akamai Secure Internet Access is a cloud-based secure web gateway that delivers threat protection for organizations and users against advanced targeted threats such as malware, ransomware, and phishing, as well as data breaches and exfiltration. This Akamai technology ensures that users and devices can securely connect to the internet wherever they are, without the complexity and management overhead associated with other legacy security controls. Powered by real-time threat intelligence, Secure Internet Access has multiple layers of protection that leverage static and dynamic detection engines to proactively identify and block targeted threats.
Enterprise Application Access
Akamai Enterprise Application Access enables Zero Trust Network Access (ZTNA) by replacing virtual private networks (VPNs) with an identity-aware proxy in the cloud. This flexible and adaptable service enables granular decision-making access based on real-time signals that include threat intelligence, device posture, and user information. Enterprise Application Access improves network security by integrating technologies for data loss prevention, application security, identity and access management, multi-factor authentication (MFA), single sign-on (SSO), and management visibility and network access control.
Akamai MFA
Akamai’s multi-factor authentication technology Akamai MFA, is a next-generation solution that offers a phish-proof authentication factor. Leveraging FIDO2, the strongest standards-based authentication method available, Akamai MFA uses an app on a mobile device to provide multi-factor authentication with a familiar and frictionless user experience, without the need for costly and cumbersome hardware security keys. With end-to-end cryptography and a sealed challenge/response flow, Akamai MFA makes the authentication process confidential and unphishable.
Achieve network security with microsegmentation
Akamai also provides powerful protections for network security with Akamai Guardicore Segmentation, the simplest, fastest, and most intuitive way to enforce Zero Trust principles within a segmented network, and Akamai Hunt, our managed threat hunting service.
Akamai Guardicore Segmentation collects detailed information about an organization’s IT infrastructure, creating a dynamic map that allows security teams to view activity with user- and process-level granularity on a real-time and historical basis. When combined with AI-powered security policy workflows, these detailed insights enable security teams to create segmentation policies for individual IT assets, effectively blocking cyberattacks like ransomware that spread via lateral movement.
Akamai’s segmentation technology works with both modern and legacy operating systems across bare metal servers, virtual machines, IoT, containers, cloud instances, and IoT devices. Akamai Guardicore Segmentation also offers multiple methods in its intrusion detection system, including a threat intelligence firewall, reputation analysis, and dynamic deception solutions.
Akamai Hunt is our managed threat hunting service that stops the most evasive threats in your network, leveraging an existing deployment of Akamai Guardicore Segmentation and the massive global threat intelligence of Akamai Cloud. The Hunt team proactively hunts for ongoing and emerging attacks in your network, reinforcing Zero Trust principles by providing continuous monitoring of the IT environment.
Frequently Asked Questions (FAQ)
Remote work security is the practice of ensuring secure access to the internet and to an organization’s resources for employees who are working outside the office on devices and technologies that are not protected by a corporate firewall.
The most effective remote work security solutions include multi-factor authentication services, cloud-based secure web gateways, and Zero Trust Network Access solutions that constantly validate and authenticate requests for access to assets and applications.
The SASE framework incorporates multiple security technologies in a single service model. These include Zero Trust Network Access (ZTNA), software-defined wide area networking (SD-WAN), cloud access security broker (CASB), next-generation firewalls, firewall as a service (FWaaS), secure web gateways (SWG), and multi-factor authentication (MFA).
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.