The frequency varies, but with the increasing sophistication of cyberthreats, organizations must remain vigilant and implement robust security measures.
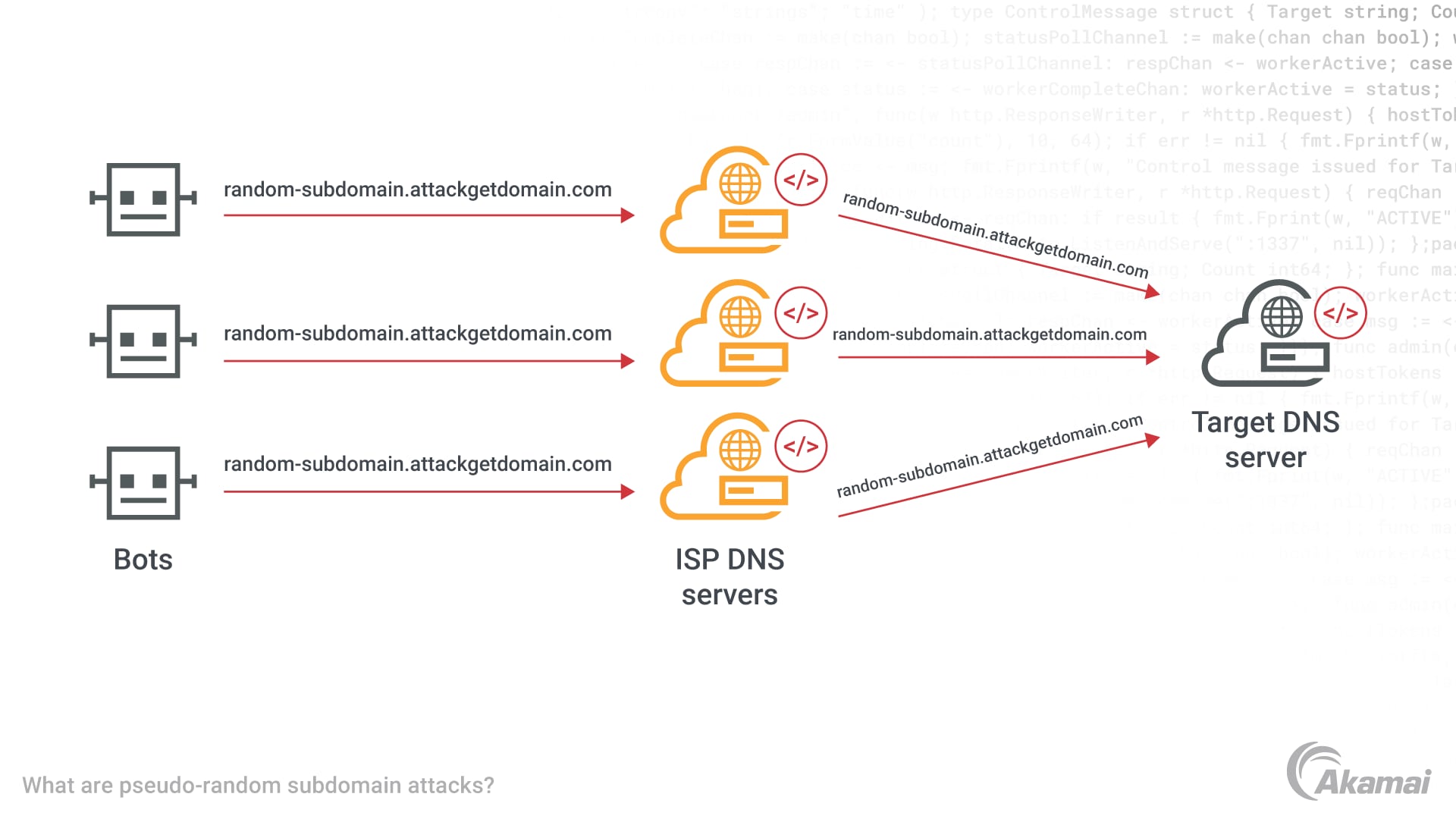
A pseudo-random subdomain (PRSD) attack, also known as a random subdomain attack or a water torture attack, is a type of distributed denial-of-service (DDoS) attack. Directed at a specific web domain, PRSD attacks flood the Domain Name System (DNS) nameservers with thousands of apparently legitimate but malicious DNS requests. As a result, both recursive DNS servers and authoritative DNS nameservers and its infrastructure environment become overloaded with requests and will slow down or crash, preventing the servers from responding to legitimate traffic and causing the domain to become unavailable. These types of attacks are highly effective because rather than simply flooding DNS servers with illegitimate packets, PRSD attacks send DNS requests for subdomains that appear to be legitimate and are harder to recognize as malicious.
Subdomains play a crucial role in website organization, acting as prefixes to the main domain. A pseudo-random subdomain attack manipulates this structure, creating unpredictable subdomains to avoid detection.
What is DNS?
The Domain Name System (DNS) is essentially an index that translates web domain names like “example.com” into IP addresses like “2001:db8:3e8:2a3::b63.” Internet protocol (IP) addresses are what computers and devices use to communicate with other machines over a network like the internet. IP addresses are difficult for human users to remember and relate to the service’s location rather than its identity. The DNS, on the other hand, enables users to work with easy-to-read domain names that identify a service. The DNS is responsible for quickly returning the correct IP address for every domain a user or machine wants to connect to.
How does DNS work?
The DNS includes two types of servers that help resolve requests from devices and applications for IP addresses: authoritative and recursive nameservers. Authoritative DNS servers keep the official DNS records for each domain. Recursive DNS resolvers, which sit closer to users, help to lighten the workload of authoritative servers and return records faster by responding to DNS requests from records stored in their cache memory when available.
While the DNS process typically takes a fraction of a second, there are a number of steps involved in resolving a DNS request. For example:
- When a link is clicked, a web domain is typed into a browser, or an application needs to connect to another machine, the requesting device typically issues a DNS query that is sent to a recursive DNS resolver.
- If the recursive server has the DNS record stored in its cache memory, it immediately returns the correct IP address or answer.
- If no DNS record is stored in its DNS cache, the recursive server forwards the request to other nameservers and eventually to an authoritative DNS server, which returns the correct IP address.
- The recursive server then returns the correct IP address to the user’s device, which loads the web page or creates a connection.
How does a pseudo-random subdomain attack work?
To execute a pseudo-random subdomain attack against a target domain such as example.com, hackers use domain-generating algorithms or automated tools to generate a list of thousands or millions of nonexistent subdomains (i.e., names that don’t have answers in DNS) based on random strings (e.g., asdf). Using a botnet — a network of malware-infected computers under the attacker’s control — attackers initiate simultaneous DNS queries for these nonexistent subdomains. The recursive DNS servers receiving the request can’t resolve requests since the nonexistent subdomain is not stored in cache memory, so the request is forwarded to authoritative DNS servers. Authoritative nameservers issue an NXDOMAIN response, meaning the domain can’t be found. As the authoritative server becomes overwhelmed by thousands or millions of simultaneous requests for nonexistent subdomains, it will either crash or trigger a rate-limiting mechanism that slows performance. At the same time, the malicious request can quickly consume all available resources within the recursive DNS resolvers and its environment infrastructure that are waiting for responses from the authoritative nameservers. As a result, legitimate users will experience “failure” responses.
How can organizations stop PRSD attacks?
Pseudo-random subdomain attacks are some of the more challenging DNS attacks to mitigate because the packets used are correctly formed DNS requests. Additionally, the queries in this DNS DDoS attack are typically issued from legitimate ISP clients, making it difficult to use source-based filtering to block the malicious DNS traffic. To mitigate PRSD attacks or minimize their impact, cybersecurity teams can follow several best practices.
- Increase query capacity. Provisioning more memory for existing DNS servers and adding DNS servers will allow resolvers to sustain higher query loads and prevent them from running out of critical system resources.
- Maximize queries allowed. Tuning the DNS configuration to maximize the number of simultaneous recursive queries allowed may enable DNS servers to continue responding to legitimate requests during an attack.
- Deploy pattern recognition mitigation. Certain security solutions use machine learning to identify the patterns of attack traffic and automatically create a filter to block it or manage the traffic.
- Choose a DNS platform with a global scale. Working with a DNS provider that offers many points of presence with algorithmic controls to manage PRSD traffic around the world enables organizations to mitigate the impact of the largest DDoS attacks based on DNS floods.
Frequently Asked Questions (FAQ)
Yes, while challenging, proactive monitoring and the use of advanced threat detection tools can help identify patterns associated with pseudo-random subdomain attacks.
No industry is entirely immune. However, sectors handling sensitive data, such as finance and healthcare, are particularly attractive targets for pseudo-random subdomain attacks.
Yes, small businesses are also potential targets, as attackers often exploit vulnerabilities regardless of the organization’s size.
Absolutely. AI-driven cybersecurity solutions can analyze vast datasets, identify patterns, and swiftly respond to potential pseudo-random subdomain attacks.
In the unfortunate event of an attack, prompt incident response — including isolating affected systems and collaborating with cybersecurity experts — is crucial to minimizing damage.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.