Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
SSL/TLS is a security protocol that provides encryption and authentication for communication over the internet between a user and a server. It is used to ensure data privacy, secure credit card transactions, authenticate websites, and maintain the integrity of data transmission. SSL/TLS is widely used on the web and is a core component of most secure communication protocols.
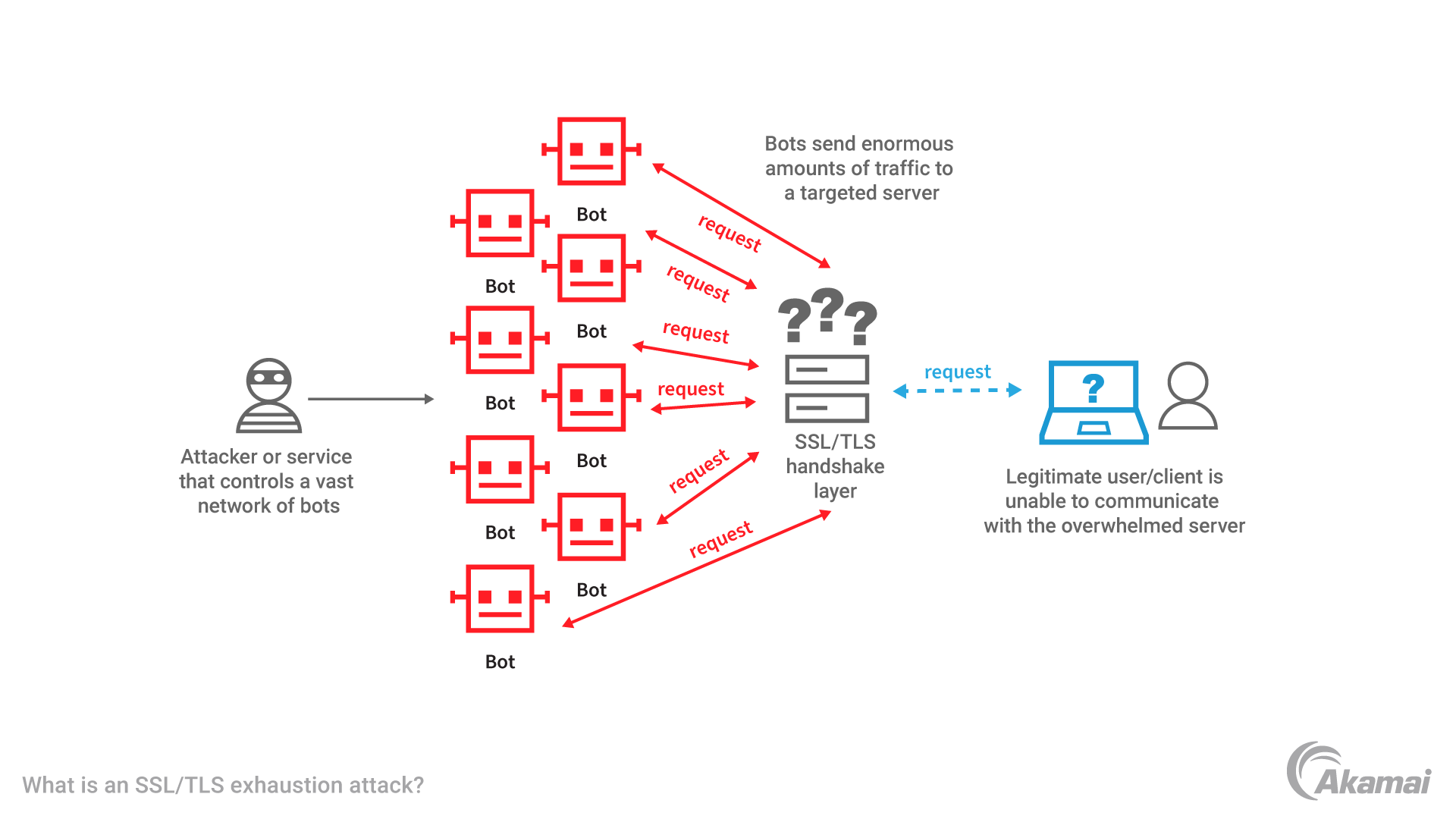
An SSL/TLS exhaustion attack, also known as a cryptographic attack, is a type of attack that attempts to overwhelm the target system’s capacity for secure communication by exhausting the available resources. This type of attack typically attempts to render the target’s services unusable or at least significantly reduce their performance. Common techniques used in SSL/TLS exhaustion attacks may include, but are not limited to:
- Denial of service (DoS) – the attacker floods the target with requests so as to overwhelm it and prevent legitimate requests from being processed
- Brute-force attack – the attacker sends a large number of requests in an attempt to guess authentication credentials
- Amplification attack – an attack where small requests result in multiple replies that can be used to exhaust resources on the target
- TCP connection and session state – the SSL/TLS key exchange process involves cryptographic operations to encrypt and decrypt, which are resource intensive but also requires maintaining session connection states for each active client (spoofed or non-spoofed), which involves storage and memory allocations
By combining various techniques, an attacker can successfully launch an effective SSL/TLS exhaustion attack that is capable of overwhelming a target’s secure communications infrastructure. Furthermore, attackers can also utilize automated scripts and tools that can help them carry out such attacks more efficiently without requiring as much manual labor. As a result, organizations need to remain vigilant and take steps toward protecting themselves from such attacks by implementing security measures such as using multi-factor authentication, encrypting sensitive data, and regularly monitoring their network traffic for possible threats.
How does an SSL/TLS exhaustion attack work?
The basic mechanics of an SSL/TLS exhaustion attack involve flooding a server with thousands or millions of specially crafted requests, typically using automated tools or scripts. These requests can take many different forms, depending on the specific exploit being used, and can often overwhelm the server’s resources, causing it to become unresponsive. This technique involves initiating the data encryption key (DEK), key encryption key (KEK), or the master encryption key (MEK), but never completing the full key exchanges or requesting a file on the server (aka URI or URL).
What are the consequences of an SSL/TLS exhaustion attack?
The consequences of an SSL/TLS exhaustion attack can be severe, including loss of sensitive data and disruption of critical services. To help reduce the impact of these attacks, security and server administrators should take measures to strengthen their security defenses and implement mitigation techniques, such as increasing memory capacity, TLS session resumption, connection or TLS rate limiting, cloud scrubbing, CDNs, or using scalable dedicated hardware for SSL/TLS processing and offloading.
How can I prevent an SSL/TLS exhaustion attack?
If you suspect that your server has been the victim of an SSL/TLS exhaustion attack, you should immediately take steps to contain and mitigate the damage. This may include disconnecting your server from the network or disabling any affected services until the issue can be resolved. Operators should also work with IT professionals or security experts to help identify and remediate any vulnerabilities that may have contributed to the attack. There are many techniques to help reduce the impact of these attacks, but there is nothing that can be done to prevent this attack vector.
What should I do if I’m the victim of an SSL/TLS exhaustion attack?
If you are concerned about potential SSL/TLS exhaustion attacks, there are a number of things that you can do to help during attack events. Firstly, you should have defined runbooks in place to be able to quickly identify the resources being targeted, and align the necessary resources or owners of the systems during incident response. Without efficient escalation procedures in place, you run the risk of prolonged outages that can impact business operations and revenues. Secondly, remain calm, even in the face of a complete outage. Most times, mistakes are made when individuals are overreacting unnecessarily and forget appropriate change controls processes. Lastly, have a governance team review all countermeasures deployed, and apply a rigorous “lessons learned” strategy for reducing exposures or future impactful events.
Prevent SSL/TLS exhaustion attacks and DDoS attacks with Akamai
Akamai offers end-to-end DDoS protection that acts as a first line of defense, providing dedicated edge, distributed DNS, and cloud mitigation strategies designed to prevent collateral damage and single points of failure. Our purpose-built DDoS clouds offer dedicated scrubbing capacity and higher quality of mitigation, which can be fine-tuned to the specific requirements of web applications or internet-based services.
One of the most effective ways to stop SSL/TLS exhaustion and other DDoS attacks is with Akamai Prolexic, a proven cloud scrubbing service that protects entire data centers and internet-facing infrastructure from DDoS attacks across all ports and protocols. With Prolexic, traffic is routed via BGP anycast across globally distributed, high-capacity scrubbing centers, where our Security Operations Command Center (SOCC) can deploy proactive and/or custom mitigation controls to stop attacks instantly. By routing traffic to the nearest scrubbing center, Prolexic can stop attacks closer to the source to maximize performance for users and maintain network resiliency through cloud distribution. Once scrubbing is complete, clean traffic is returned to the customer origin via logical or dedicated active connections.
Available as an always-on or on-demand service, Prolexic offers flexible integration models to serve the needs of a variety of security postures across hybrid origins.
With Akamai Prolexic, your security teams can:
- Reduce risk of DDoS attacks, thanks to proactive mitigation controls and Prolexic’s zero-second SLA
- Stop highly complex SSL/TLS exhaustion DDoS attacks without sacrificing quality of mitigation
- Unify security postures by consistently applying DDoS mitigation policies throughout your organization, regardless of where applications are hosted
- Optimize incident response to ensure business continuity with service validation exercises, custom runbooks, and operational readiness drills
- Scale security resources with our fully managed solution that is backed by 225+ frontline SOCC responders