While it’s possible to implement some protective measures, it’s advisable to seek professional assistance, as attackers are becoming increasingly sophisticated. Having enough network capacity to consume volumetric attacks, while also serving legitimate services, is key to being successful when blocking these types of events.
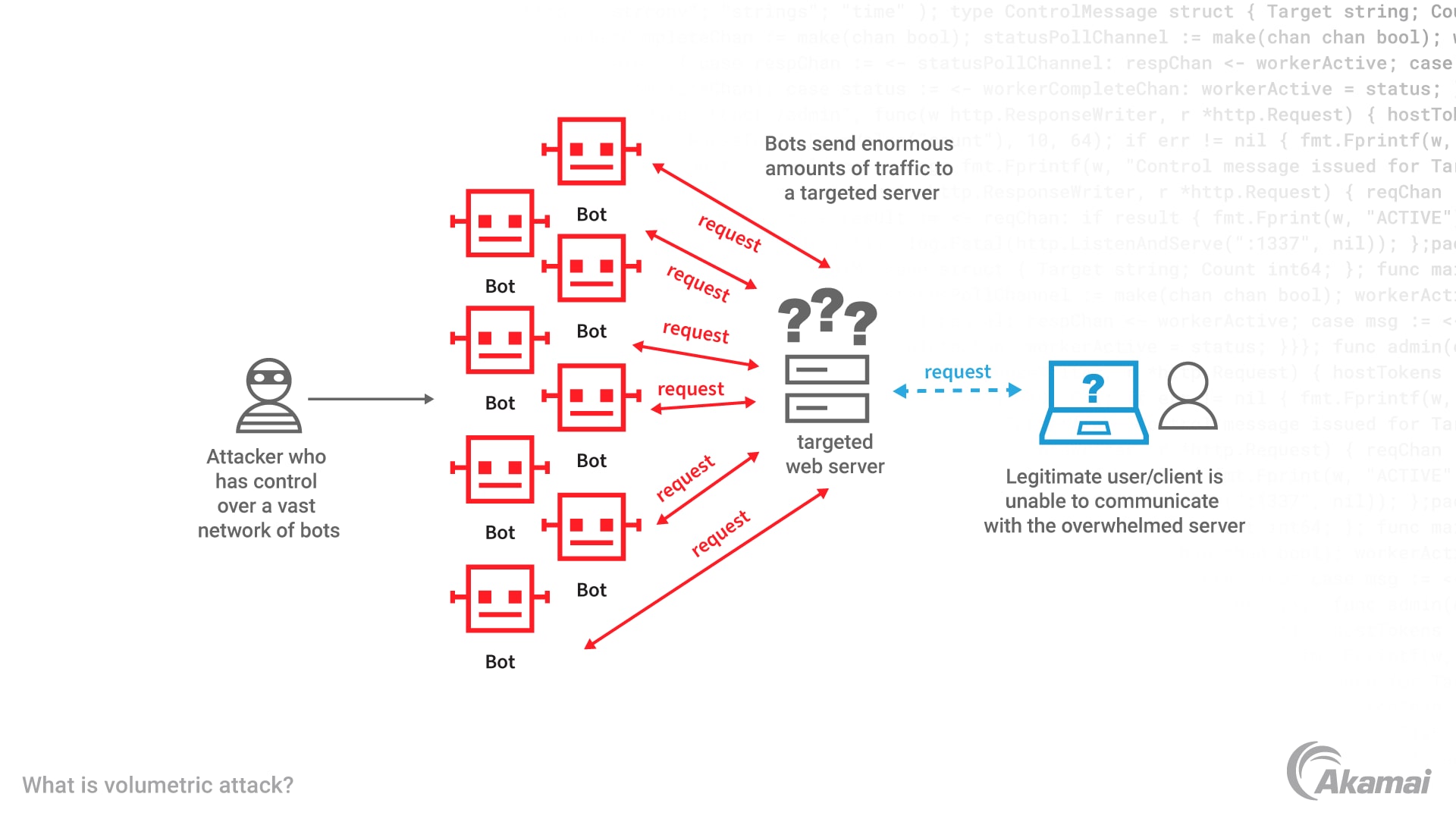
A volumetric attack is typically attributed to a distributed denial-of-service (DDoS) attack that is designed to overwhelm the capacity of a server or network and cause it to slow down or fail. Volumetric attacks send enormous amounts of traffic to a targeted server, causing network congestion, packet loss, and service disruptions. These attacks are usually measured in the rate of bits per second (bps), packets per second (pps), or connections per second (cps). Volumetric attacks generally affect Layers 3 and 4 of the OSI (Open Systems Interconnection) model, which is the gold standard for defining how the technology services communicate. The high volume of traffic tends to make it difficult for the server, network device, or its security defenses to distinguish legitimate requests from malicious traffic. As the server tries to manage and respond to each request in incoming traffic, resources such as bandwidth, processing power, and memory become exhausted. The machine eventually slows down or crashes, denying service to legitimate users. Volumetric cyberattacks are believed to comprise more than 75% of DDoS attacks.
How does a volumetric DDoS attack work?
Volumetric attacks are typically conducted by attackers who have control over a vast network of bots, known as a botnet, but can also leverage reflection protocols that are amplified and exposed across the internet. Botnets are computers, IoT devices, and other machines that have been surreptitiously infected with malware that allows attackers to control them remotely. By issuing commands to thousands or millions of compromised devices, attackers can force them to simultaneously direct requests and traffic to a targeted server.
What are the different types of volumetric attacks?
There are several types of DDoS attacks that rely on volume. These include:
- ICMP floods. ICMP (Internet Control Message Protocol) flood attacks overwhelm a server or network device with ICMP pings, or echo-request packets, designed to test the health and connectivity of the device. When a targeted device is inundated with a flood of ping requests, it exhausts its capacity to respond and becomes unavailable to legitimate traffic.
- DNS reflection floods. This attack leverages the Domain Name System (DNS) and is generated from what are referred to as open DNS resolvers. These attacks can target any internet-facing service, including websites, DNS authoritative systems, or any other routable endpoint. DNS reflection typically makes up 15%–25% of all DDoS attack vectors that Akamai monitors.
- UDP floods. A UDP (User Datagram Protocol) flood directs large amounts of UDP traffic from spoofed IP addresses to random ports on a targeted system. As the targeted device attempts to check the port specified in each incoming packet, its bandwidth and capacity become overwhelmed, rendering it unavailable to normal traffic and legitimate users. These attacks also include fragmented UDP packets, which makes it even more difficult to determine if the request is legitimate or malicious.
- TCP out-of-state floods (SYN, SYN-ACK, ACK, etc.). These types of attacks are normally generated from compromised hosts (aka bots) and can cause serious impact to legitimate network services that monitor and manage stateful connections. Attackers take advantage of the ability to generate what looks like legitimate attempts to initiate a TCP connection, but they do it with high rates of requests to connect, and from endpoints that did not initiate the request, known as spoofed packets. SYN floods have consistently made up 15%–25% of all DDoS attacks mitigated by Akamai.
- Reflection amplification attacks. In these attacks, hackers use a spoofed or forged IP address to send packet requests or queries to certain kinds of servers that, when responding, send response packets that contain far more data than the initial request. Because the attacker has used the IP address of the server they wish to target, the queried service responds to the target rather than the attacker’s machines, inundating it with massive amounts of packets that each contain a great deal of data. In this way, attackers can use a small amount of effort and resources to mount a large volumetric attack. These types of attacks make up 40%–50% of all volumetric attacks.
What are the dangers of a volumetric attack?
The initial impact of a volumetric attack is to create congestion that degrades the performance of network connections to the internet, servers, and protocols, potentially causing outages. However, attackers may also use volumetric attacks as a cover for more sophisticated exploits, which we refer to as “smoke screen” attacks. As security teams work diligently to mitigate the volumetric attack, attackers may launch additional attacks (multi-vector) that allow them to surreptitiously penetrate network defenses to steal data, transfer funds, access high-value accounts, or cause further exploitation.
How can a volumetric attack be mitigated?
A multilayered approach to security is the best way to mitigate volumetric DDoS attacks. Actions that security teams may take include:
- Flow telemetry analysis. Using flow telemetry analysis along with behavioral analysis can help security teams detect abnormalities in network traffic that may signal a DDoS attack. When security teams first have a clear understanding of what normal traffic looks like, it becomes easier to identify potentially suspicious behavior.
- Web application firewall (WAF). A web application firewall can filter, monitor, and block malicious traffic that may be part of a volumetric DDoS attack.
- Rate limiting. Limiting the number of requests a server can accept over a certain time period can help to prevent it from being overwhelmed by a deluge of requests.
- DDoS mitigation services. One of the best ways to mitigate and prevent DDoS attacks is to use the DDoS mitigation services of a large cybersecurity provider. A DDoS protection service will detect and block DDoS attacks as quickly as possible, filtering out malicious traffic and preventing it from reaching the intended targeted asset. Attack traffic may be blocked by a DDoS scrubbing service, a cloud-based DNS service, or a CDN-based web protection service.
- Positive security model. Building proactive mitigations is a big key to success when mitigating volumetric DDoS. Akamai blocks 65%–80% of volumetric DDoS attacks in zero seconds with 100% consistency of mitigation. Profiling the internet traffic mix and only allowing trusted sources and permitted protocols is the core basis for positive security for network services. Scalable cloud network firewalls are one mechanism to configure proactive mitigations.
Frequently Asked Questions (FAQ)
Early signs include a significant drop in all network services, reduced website performance, or accessibility issues. Monitoring your traffic and network activity can help you detect an attack.
Yes. Volumetric attacks focus on overwhelming a network with traffic, while other DDoS attacks may exploit vulnerabilities in the target’s system.
Common targets include internet routing networks and systems that manage stateful connections. High-profile industries like ecommerce websites, online gaming platforms, and government websites commonly experience DDoS attacks and are also at risk for volumetric attacks.
The damage can be extensive, leading to financial losses, reputational damage, and even legal consequences in some cases.
Prevention involves a combination of security measures, including robust cloud network scrubbing, scalable firewalls, intrusion detection systems, and secure coding practices.
Learn more about DDoS attacks
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.