Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
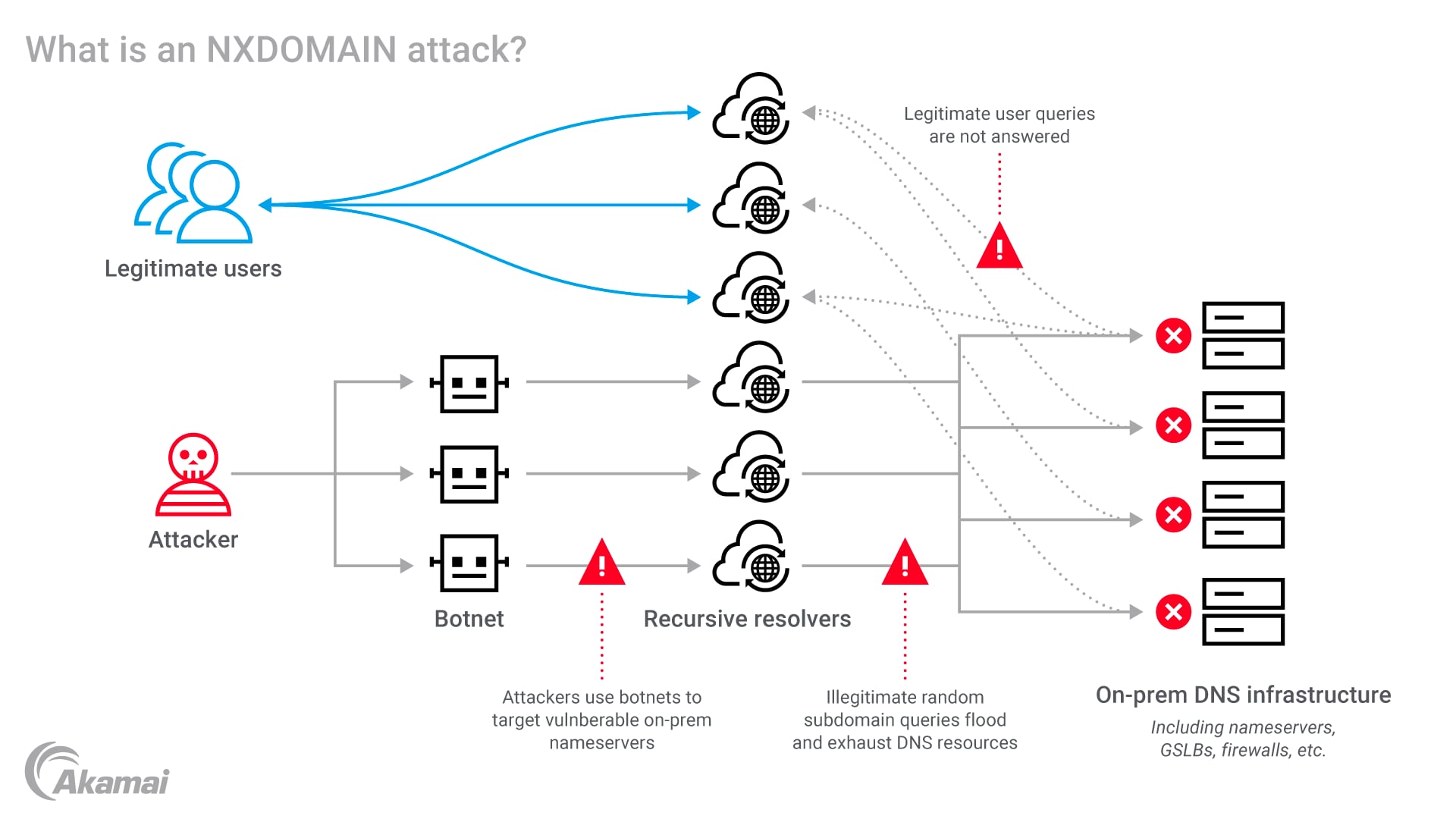
A DNS NXDOMAIN flood — aka pseudo-random subdomain (PRSD) DDoS attack, DNS water torture, or DNS resource exhaustion attack — is a type of denial-of-service attack on Domain Name System (DNS) services and is considered a Layer 7 (application layer) attack type.
DNS is the “GPS of the internet” — it translates human-readable domain names like www.example.com into IP addresses that machines can read, enabling users to quickly access websites without needing to remember long strings of numbers. An NXDOMAIN DDoS attack seeks to exhaust the resources of a DNS infrastructure (DNS nameservers, global server load balancers, firewalls, etc.) and consequently cause DNS services to slow down or crash. The attacks overwhelm DNS servers with requests for nonexistent domains or subdomains, which causes servers to generate NXDOMAIN errors that indicate that the domain or the subdomain does not exist.
DNS and DDoS attacks
DNS services are essential to everyday operations of the internet. When a user enters a fully qualified domain name (website address) into a web browser, the user’s computer or device sends a request to the authoritative DNS servers for the IP address of the domain. The DNS request first goes to recursive servers near the user that cache frequently used addresses. If the recursive server doesn’t have the address, it sends the message on to other servers that might, and ultimately checks with an authoritative nameserver that holds the official DNS record for the domain.
Fast DNS responses are essential to quick page load times and positive user experiences online. Cybercriminals often target DNS services because the Domain Name System was not initially designed with security in mind, leaving it with many vulnerabilities for attackers to exploit — so it should be considered a single point of failure for most, if not all, application or internet services if it becomes unavailable.
Distributed denial-of-service attacks, or DDoS attacks, are a type of cyberattack that aims to disrupt operations of a server, service, or network by overwhelming it with a flood of traffic and requests. DDoS attacks frequently bombard targets with messages sent through botnets or other compromised internet resources — thousands or millions of malware-infected devices that are under the control of threat actors.
By flooding servers or services like DNS with abusive traffic, DDoS attacks cause these devices to slow down or crash, making services unavailable for legitimate users, requests, and traffic. DDoS attacks that target DNS services typically have a relatively low volume of bits per second, but they report as high packets per second or queries per second. The DNS servers receiving large amounts of DNS queries to nonexistent records is what overwhelms the system. This is also referred to as resource exhaustion because it depletes the CPU, memory, and hard drive or database resource allocations.
How an NXDOMAIN water torture DDoS attack works
In an NXDOMAIN DDoS attack, threat actors use botnets to send DNS queries to a targeted DNS server or resolver. These messages ask for IP addresses for websites or subdomains that do not exist. For each query, the DNS server must perform a lookup, which consumes a certain amount of resources. When the website cannot be found, DNS servers return an NXDOMAIN reply. By overwhelming the DNS infrastructure with so many of these requests, an NXDOMAIN attack can deplete the resources of the DNS server, leaving it unable to fulfill legitimate requests and preventing users from accessing websites.
The outcomes of an NXDOMAIN DDoS attack
NXDOMAIN DDoS attacks have a negative impact on users and organizations.
- Poor online experiences: By slowing down or completely halting the DNS resolution process, NXDOMAIN DDoS attacks make the internet unavailable for end users, businesses, and website owners.
- Loss of trust: NXDOMAIN DDoS attacks may undermine trust in the targeted DNS service providers.
- Increased costs: Excessive load on DNS infrastructure can cause premature wear and tear, leading to increased costs for infrastructure and maintenance.
- Disruption of business services: By effectively halting internet activity, NXDOMAIN DDoS attacks can disrupt all manner of business services. In critical sectors like healthcare, these disruptions can have a serious impact on real-time decision-making that may have life-and-death consequences.
- Distraction from other threats: As part of a coordinated cyberattack, threat actors often use DDoS attacks to distract security teams away from other more dangerous attack vectors.
Detecting and preventing NXDOMAIN DDoS attacks
Detecting NXDOMAIN DDoS attacks requires DNS security technology that can monitor and manage DNS request and response rates, and analyze traffic patterns for anomalies that may indicate a DDoS attack. Real-time alerts and cybersecurity tools can help IT teams to quickly identify spikes in NXDOMAIN replies or bad requests that may indicate the start of an attack.
To prevent NXDOMAIN DDoS attacks, security teams can adopt several strategies and technologies:
- Rate limiting technologies restrict the number of requests to DNS resolvers from a single IP source, reducing the load on servers and preventing them from becoming overwhelmed with requests.
- Botnet detection solutions help identify and neutralize attacking forces before they impact DNS services.
- Anycast routing can distribute incoming DNS requests among multiple geographically dispersed servers to minimize the impact of an attack.
- Security teams can configure DNS records with appropriate time-to-live (TTL) values. This mitigates the impact of an attack by affecting how quickly changes to DNS records are propagated.
- DDoS protection solutions from third-party service providers offer threat intelligence and comprehensive security solutions that include firewalls, blackhole routing to filter out malicious traffic, DNS proxies with multi-tenant policy enforcement, and DNS cloud services with wide footprints and capacity.
Get protection from NXDOMAIN attacks
There are three key approaches a company might adopt while dealing with NXDOMAIN DNS attacks.
Provisioning additional redundant capacity
This is the more brute-force approach, in which DNS resource exhaustion attacks (NXDOMAIN attacks) are addressed by provisioning additional redundant DNS resources (e.g., nameservers, firewalls, GSLB). However, this is not a financially prudent approach because the additional resources sit idle during peacetime, and the additional resource capacity is often not enough to scale up to meet attack traffic volumes. Thus, there will be additional capital expenditure and low ROI for such extra infrastructure resources. There are also technological challenges and limits to how much additional redundant capacity the network teams provision.
Using an external cloud-based authoritative DNS solution
Akamai Edge DNS offers a comprehensive, purpose-built, cloud-based authoritative DNS solution that uses the scale, security, and capacity of Akamai Cloud to distribute your DNS zones across several thousand servers across the globe.
Customers delegate their zone authority to Edge DNS by updating nameserver records at the registrar and using those provided by Akamai. Akamai Edge DNS and Akamai Global Traffic Management, the global server load balancing solution offered by Akamai, work together to provide an unparalleled attack surface and proactive security controls that can mitigate even the largest DNS attacks without impacting a customer’s DNS performance, reliability, and availability.
Using robust DNS proxy solutions that can enforce dynamic security policies
In certain specific instances, organizations maintain on-premises DNS infrastructure and cannot delegate their authoritative zones to an external cloud solution to protect themselves from various types of DNS attacks. The reasons for such preferences range from compliance concerns to dynamic configurations on origin GSLB to a simple desire to manage their authoritative zones at the origin.
In certain hybrid scenarios, an organization that has delegated some of its authoritative DNS zones to Edge DNS but prefers to serve the remaining zones from an on-prem origin leaves the on-prem infrastructure vulnerable to DNS resource exhaustion attacks.
Akamai Shield NS53 is a bidirectional DNS proxy solution that protects key components of your origin DNS infrastructure from resource exhaustion attacks. Using an intuitive user interface on the Akamai Control Center, you can self-configure, administer, manage, and enforce your organization’s specific dynamic security policies in real time. Illegitimate DNS queries and DNS attack floods are dropped at the very edge of the Akamai network, keeping your DNS secure, reliable, and available.
How Akamai solutions can help protect your digital infrastructure
Akamai offers a comprehensive portfolio of solutions to protect your digital infrastructure from various DDoS attacks. You can use the following table as a reminder about how to tailor your security solution(s) based on your specific needs.
| Attack type | Recommended Akamai solutions |
|---|---|
| DNS NXDOMAIN attacks | Edge DNS, Global Traffic Management, Shield NS53 |
| DNS direct queries attacks | Edge DNS, Global Traffic Management, Shield NS53 |
| DNS reflection and DNS amplification attacks | Prolexic, Prolexic Network Cloud Firewall |
| DNS source IP spoofing and DNS TTL attacks | Edge DNS, Global Traffic Management |
| Layer 3 and Layer 4 DDoS attacks (across all ports and protocols) | Prolexic (for cloud, on-prem, or hybrid) |
| Application layer (Layer 7) DDoS attacks not related to DNS (not on port 53) | Akamai App & API Protector |
Frequently Asked Questions (FAQ)
NXDOMAIN attacks can use both IPv4 and IPv6 addresses in their DNS requests.
DNS queries are often sent via UDP (User Datagram Protocol) because this protocol allows for faster transmission of small packets. However, the connectionless nature of UDP makes it easier for attackers to spoof source IP addresses, which can hinder mitigation of NXDOMAIN DDoS attacks.