Detecting and Mitigating an Authorization Bypass Vulnerability in Next.js
Executive summary
On March 21, 2025, a new critical authorization bypass vulnerability in Next.js with a CVSS score of 9.1 was assigned CVE‑2025‑29927 and made public. This vulnerability allows attackers to bypass authentication and authorization checks by exploiting a flaw in the framework’s middleware handling, leaving sensitive routes open to unauthorized access.
The vulnerability can be exploited without authentication, granting unauthorized access to protected routes.
The Akamai Security Intelligence Group (SIG) has seen initial exploit attempts probing potential servers for this vulnerability.
In this blog post, Akamai researchers provide in-depth details about the vulnerability, exploitation techniques, and detection strategies.
An Akamai Adaptive Security Engine Rapid Rule is automatically providing protection for Akamai App & API Protector customers.
What is CVE-2025-29927?
CVE‑2025‑29927 is an authorization bypass vulnerability in Next.js, an open source React framework that is widely used to help decrease website loading times and increase SEO value. The vulnerability was made public on March 21, 2025, and was assigned a very critical rating of 9.1 CVSS. If exploited, an attacker could bypass middleware-based security checks by spoofing a header intended solely for internal use.
Next.js uses headers to avoid infinite loops during request processing, but its predictable value, based on the middleware file’s path, can be easily mimicked by an attacker. By including the correct header value in an HTTP request, an attacker can, in some cases, trick the application into skipping authentication and authorization checks and gain access to protected resources.
Vulnerability details
Next.js employs middleware as a way to process incoming HTTP requests before they reach the main application logic. Middleware typically performs important tasks like authentication, authorization, and setting security headers. The framework uses an internal header called “x‑middleware‑subrequest”, which is used to manage these processes, manage internal request flows, and prevent issues like infinite recursion during request handling.
The core issue lies in the improper validation of the “x‑middleware‑subrequest” header. This header is intended for internal use only, but its value is predictable — often based on the middleware file’s location or naming. As a result, an attacker can craft a simple request that mimics this request header, which tricks the system into treating the request as an internal one and bypassing critical checks.
When the middleware is bypassed, the app does not perform its normal security routines, such as identity or role verification, leading to potential unauthorized access to sensitive or restricted parts of the application. When all conditions are met, this vulnerability is especially dangerous because it can be exploited without any prior authentication.
CVE-2025-29927 affects multiple versions of Next.js. While the exploitation method varies slightly across versions, the core issue remains consistent. In older releases, the exploit leverages a crafted request header that includes _middleware as a value; in newer versions it uses middleware or src/middleware to align with the updated middleware file structure and naming conventions.
The vulnerability was fixed in Next.js versions 14.2.25 and 15.2.3, but servers running Next.js versions prior to 14.2.25 (for 14.x) and 15.2.3 (for 15.x), as well as versions 11.1.4–13.5.6 might still be vulnerable.
Observed attack traffic
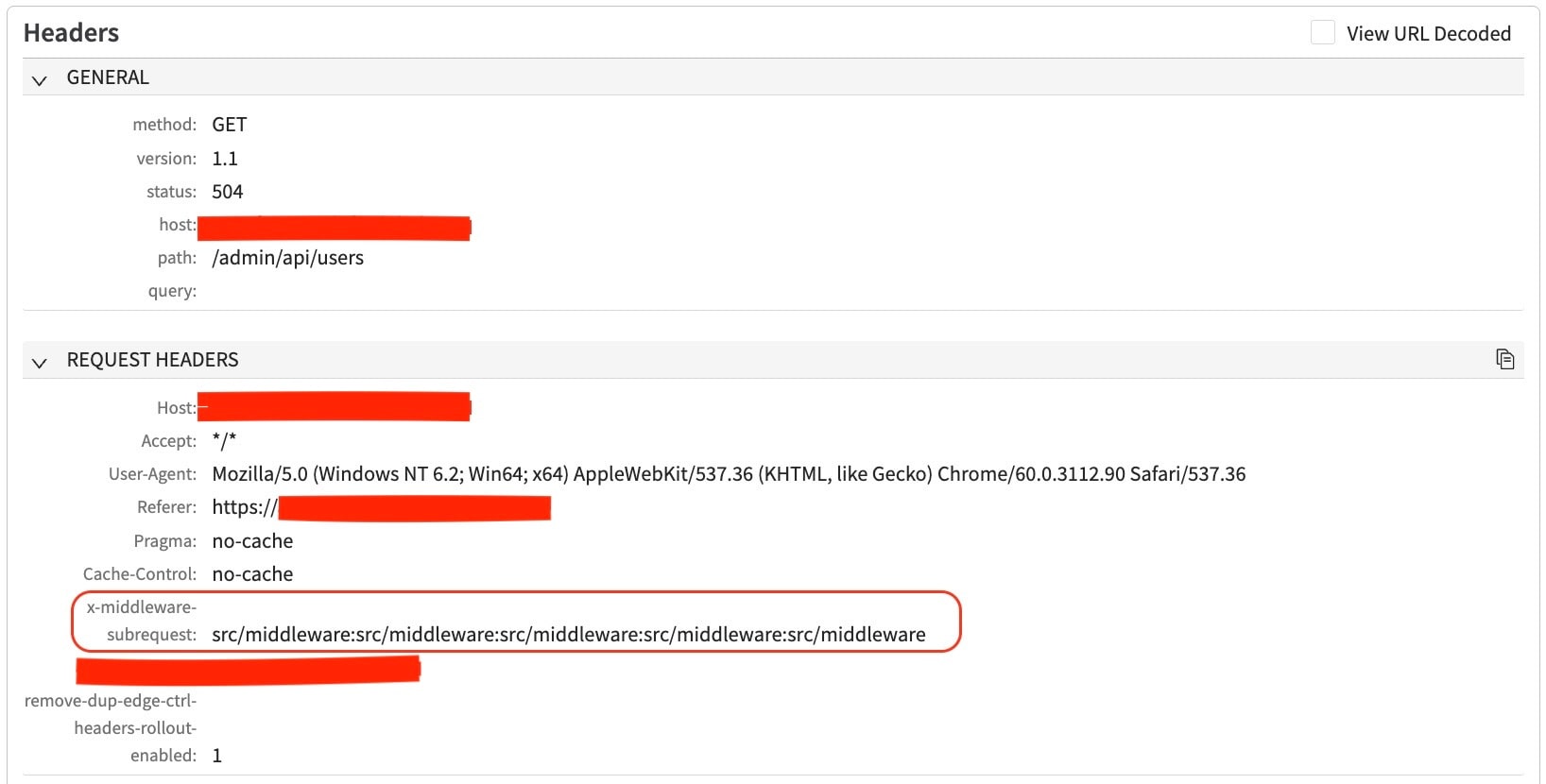
The Akamai SIG has observed initial exploit attempts targeting this vulnerability, with attackers probing potential servers. Among the identified payloads, one notable technique involves using the x-middleware-request header with the value src/middleware:src/middleware:src/middleware:src/middleware:src/middleware.
This approach simulates multiple internal subrequests within a single request, triggering Next.js’s internal redirect logic — closely resembling several publicly available proof-of-concept exploits (Figure 1).
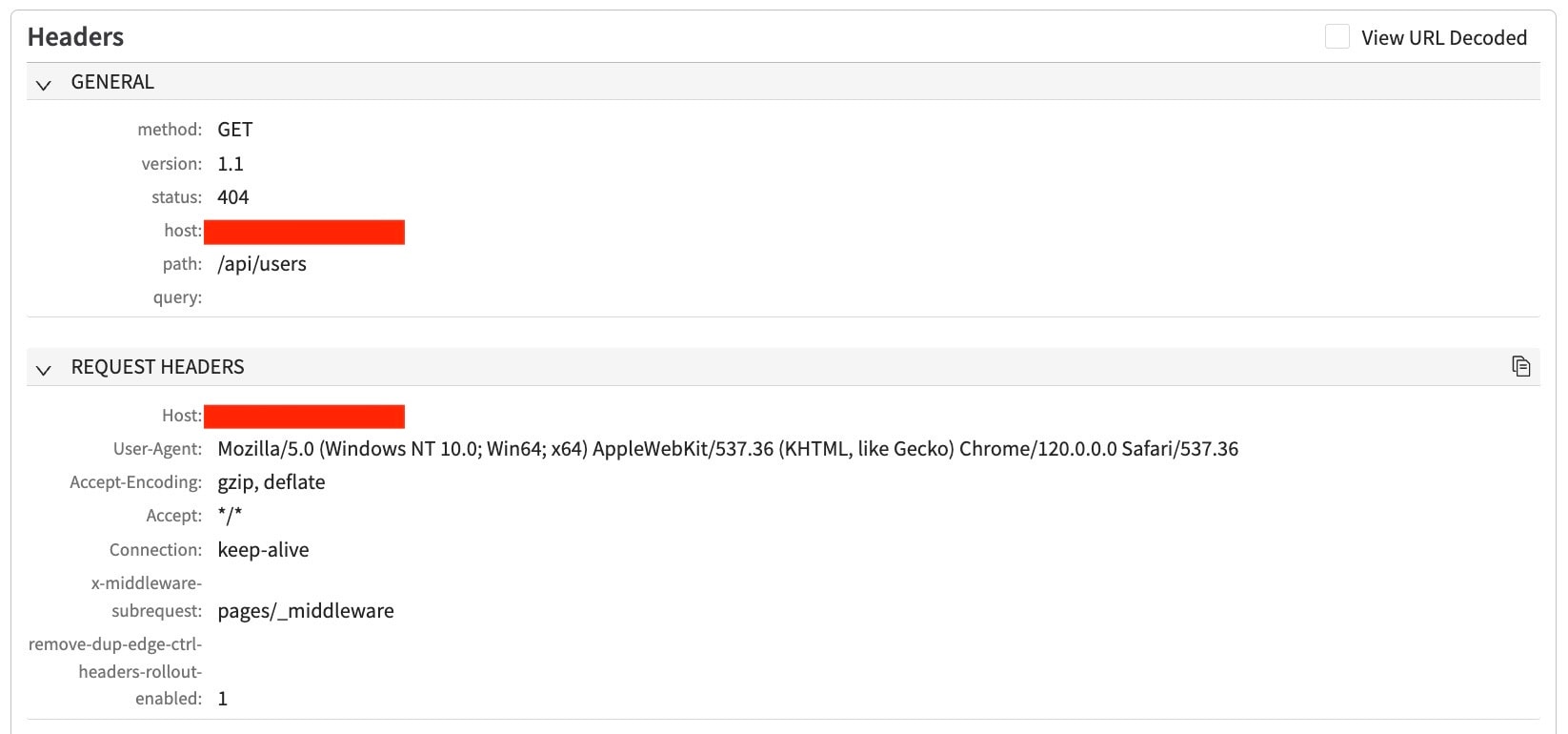
Other attack variants specifically targeting older Next.js versions were observed as well. Figure 2 illustrates a variant that used the payload pages/_middleware=.
Mitigating with Akamai App & API Protector
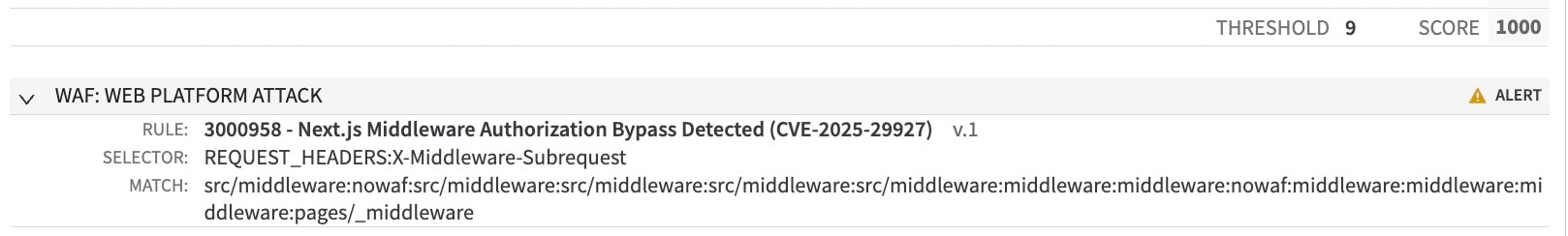
On March 24, 2025, Akamai Threat Research Team also deployed an Adaptive Security Engine Rapid Rule that detects the CVE (Figure 3).
3000958 — Next.js Middleware Authorization Bypass (CVE-2025-29927)
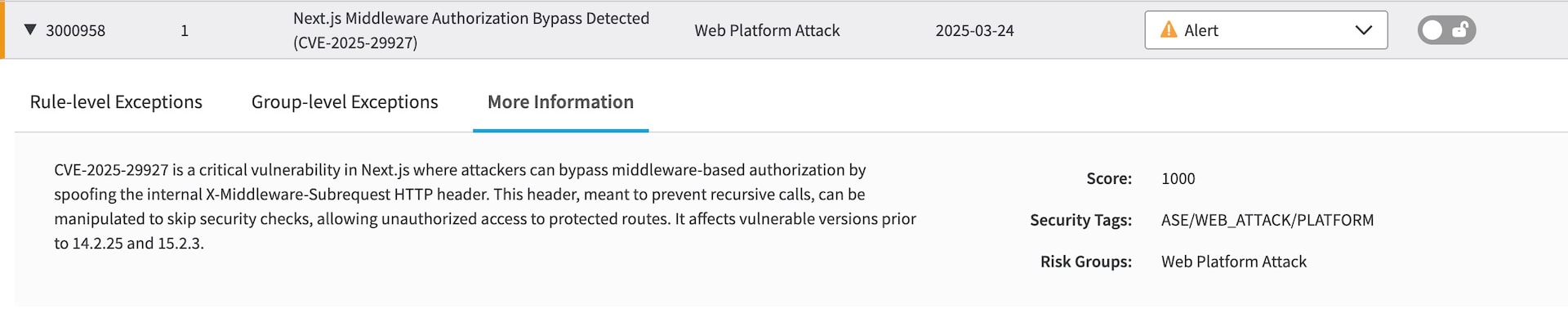
App & API Protector customers have full coverage through this new rule (Figure 4).
Version 1 of the Rapid Rule has default action set to Alert. To block the attack attempts, customers can set the rule action to Deny after reviewing the triggers to eliminate any false positives.
HOWEVER: We've observed that some customers may be legitimately using this header with the middleware name as its value. Therefore, we recommend against changing this rule action to Deny without conducting further analysis and applying additional conditions.
Summary
The Akamai SIG will continue to monitor, report on, and create mitigations for threats such as this one for both our customers and the security community at large. To keep up with more breaking news from the Akamai SIG, check out our research home page and follow us on social media.