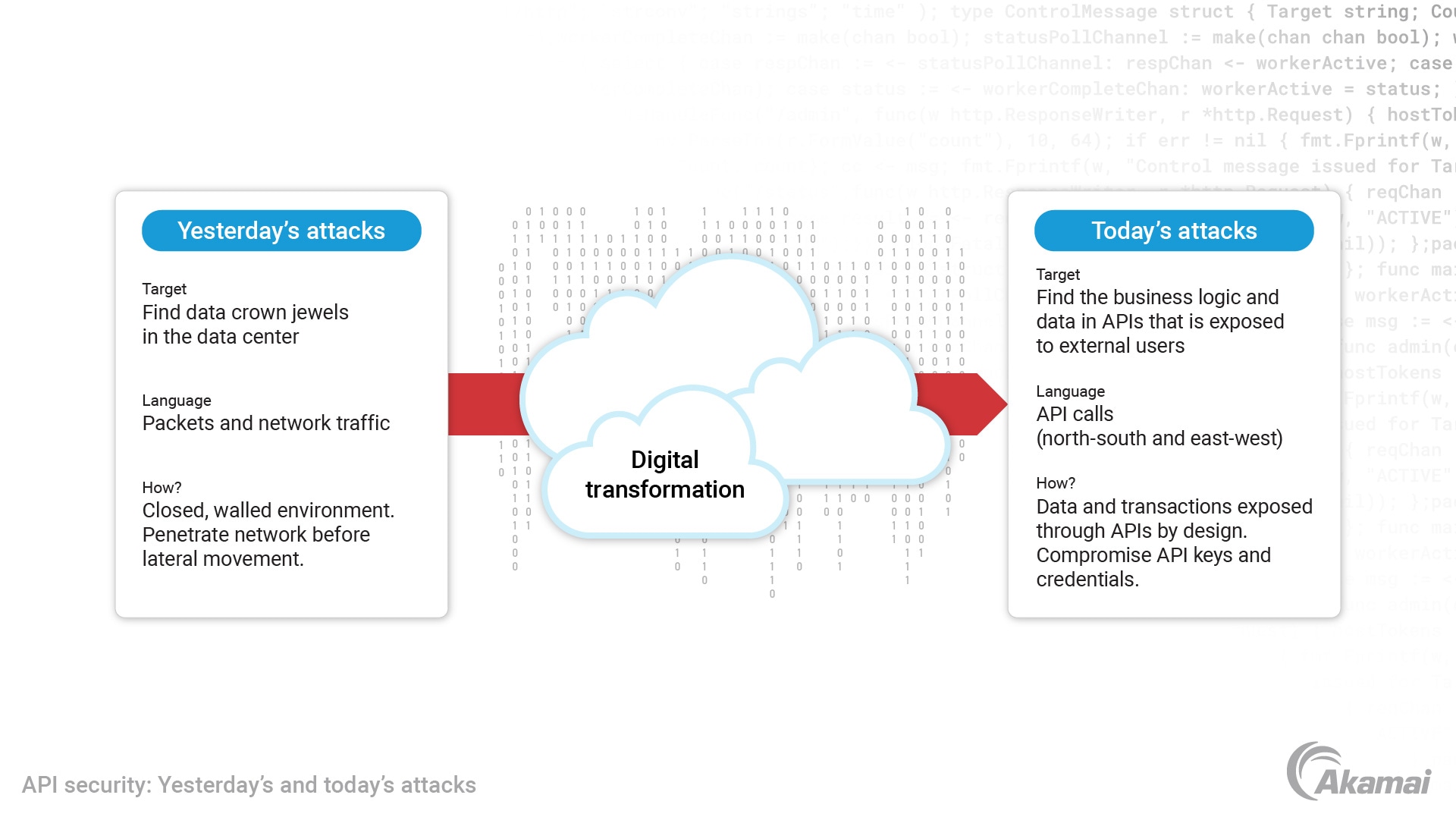
An API security breach refers to a cyber incident where an unauthorized entity gains access to a system or data through the API. This can occur when the security measures protecting the API are compromised, manipulated, or insufficient, enabling malicious actors to exploit the system’s vulnerabilities.
APIs are interfaces that allow different software applications to communicate with each other and exchange data. They are crucial for the functionality of modern software and web services, enabling the integration of diverse systems and services.
However, APIs also represent potential security risks. An API security breach can lead to unauthorized data access, data theft, or even manipulation of the system’s functionality. This could include gaining access to sensitive customer information, corporate data, or control over integral parts of the system.
Common API security vulnerabilities include weak authentication, lack of encryption, insecure endpoints, improper key management, and faulty API logic. Addressing these issues with robust API security measures, like implementing stringent authentication and authorization protocols, regular security audits, and using API gateways, are important for stopping potential breaches.