API-first is a development model that prioritizes APIs throughout the development process. An API-first approach recognizes APIs as the building blocks of development and writes code for APIs before other applications, rather than treating APIs as afterthoughts.
Application programming interfaces (APIs) have become essential building blocks of the digital economy. By enabling different software components to communicate with each other easily, APIs are vital to innovation, rapid software development, and the ability to share data across platforms.
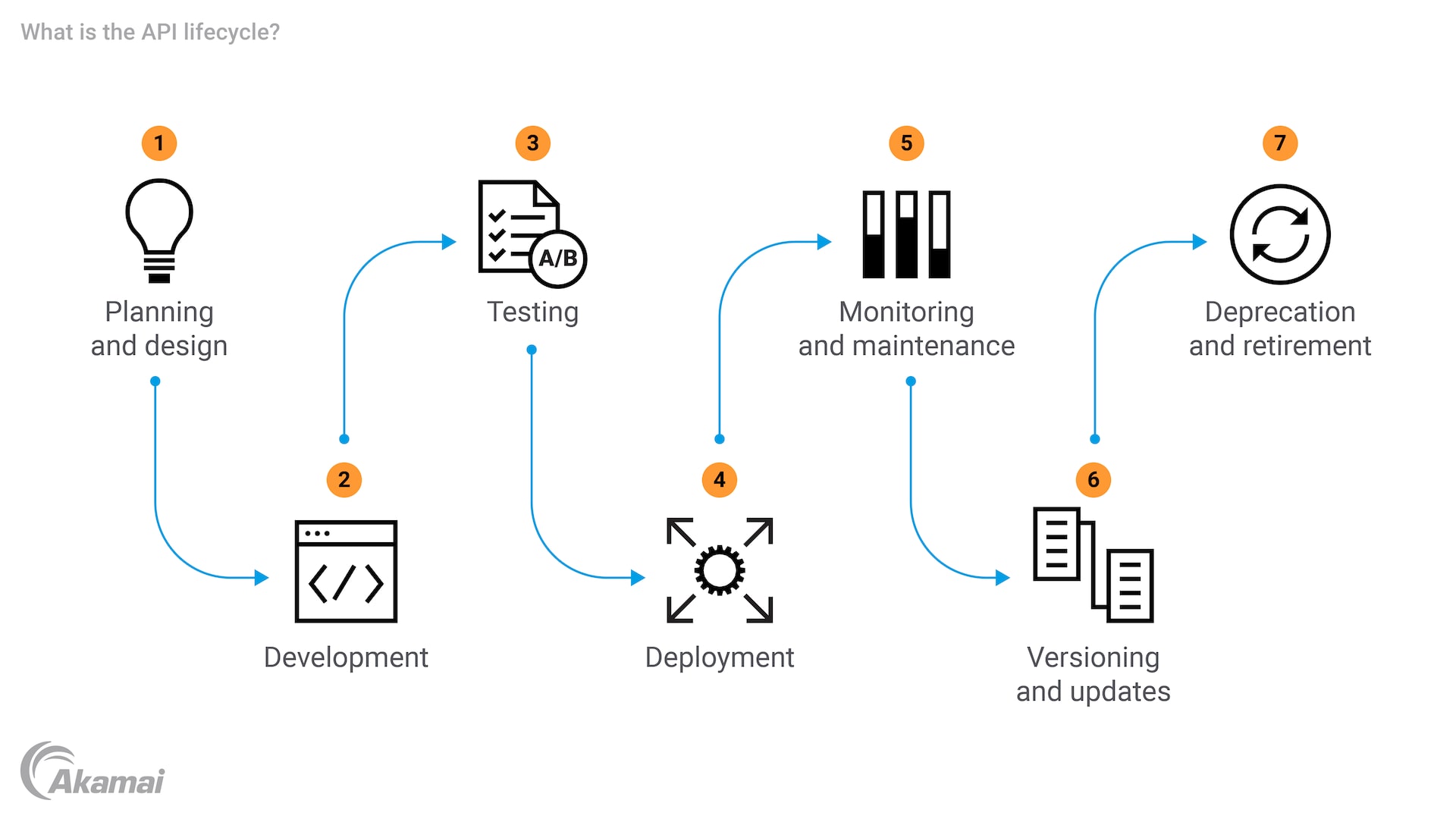
The API lifecycle is the process of designing, building, managing, and eventually retiring an API. The stages of an API lifecycle begin with an idea for a new API and move through design, development, testing, deployment, and eventual deprecation. Each stage of the lifecycle helps to ensure that APIs remain functional, secure, and valuable to users.
API lifecycle management
API lifecycle management refers to the strategic oversight and administration of an API throughout every stage of its lifecycle. By coordinating the various stages of API development and deployment, API lifecycle management ensures that APIs deliver high-quality functionality, are protected from cyberthreats, and meet the needs of API stakeholders.
API lifecycle management is typically the responsibility of several teams:
Development teams are responsible for API design, development, and testing.
DevOps teams focus on deployment, automation, and maintaining production environments.
Product managers may be involved in creating API strategy and defining use cases.
The stages of the API lifecycle
There is no single definition of the various phases of full lifecycle API management. However, most API programs include the following stages:
1. Planning and design
The initial design phase of the API lifecycle establishes an API strategy, defines the API’s purpose, identifies potential use cases, and outlines the API’s functionality. API design requires decisions about API architecture — a high-level plan for the structure of the API that determines how it will interact with other systems and components, especially in microservices architectures. An API contract outlines the API’s expected behavior. API design also includes creation of API specifications and schema, often using tools like OpenAPI for REST APIs, SDL for GraphQL APIs, and Swagger for documenting and testing different types of APIs.
2. Development
During the development phase, development teams code the API to the specifications outlined in the API contract. Teams also configure APIs using various settings and parameters to define how the API will operate and interact with other systems. Configurations include specifying the endpoints, methods, authentication mechanisms, rate limits, response formats, and other critical aspects that ensure the API functions correctly and securely.
3. Testing
During this phase, APIs are submitted to rigorous tests in a runtime environment to identify and fix any vulnerabilities or bugs in the software. API testing ensures that APIs meet defined specifications and work with endpoints as intended. Quality assurance testers manually test the functionality, performance, and security of each API. Organizations should begin testing APIs early in the development lifecycle to:
Ensure each API is built with proper security controls in place
Address potential vulnerabilities such as coding errors and misconfigurations before an API reaches production
API testing may also be automatically run from different geographic regions or within CI/CD pipelines. Various API tests include:
Contract tests that ensure the API delivers on the expectations outlined during the design stage
Performance tests that confirm an API can deliver responses in a specified amount of time
API security tests to find and remediate API vulnerabilities
For more on API security testing, see “Key capabilities for API security” below.
4. Deployment
After successful tests are completed, APIs are deployed to production environments. Development teams may use CI/CD pipelines and API gateways to standardize and automate deployment processes. During deployment, public APIs are made available to external users and developers.
5. Monitoring and maintenance
After deployment, the performance, security, and usage of APIs are continuously monitored. DevOps engineers may configure alerts to automatically notify them when API performance and security do not meet certain thresholds or metrics. This phase surfaces security vulnerabilities, errors, and latency that may be addressed through maintenance and updates.
6. Versioning and updates
When issues within API are discovered, development and DevOps teams may develop and release new API versions. These versions must be managed to ensure backward compatibility.
7. Deprecation and retirement
Deprecation is the term for replacing an API when it becomes obsolete or when significant issues require a new version. During deprecation, stakeholders and users are notified and a timeline for retirement is provided. In retirement, DevOps teams remove APIs from active use and ensure that any dependencies are appropriately managed to avoid creating functionality issues for users.
Key capabilities for API security
Today’s threat landscape calls for a complete API security solution that provides API discovery, posture management, runtime protection, and API security testing. This comprehensive approach works as an important complement to an organization’s existing tools for managing and securing APIs across the API lifecycle.
API discovery: Most organizations have little to no visibility into a large percentage of their API traffic, often because they assume all of their APIs are routed through an API gateway. But that is not the case. Many of a typical organization’s APIs are unmanaged (e.g., dormant APIs that are forgotten about, but still running and still in contact with sensitive data). Your enterprise is exposed to a range of risks without a complete and accurate inventory. Core capabilities needed:
Locating and inventorying all of your APIs, regardless of configuration or type
Detecting dormant, legacy, and zombie APIs
Identifying forgotten, neglected, or otherwise unknown shadow domains
Eliminating blind spots and uncovering potential attack paths
API posture management: With a complete API inventory in place, it’s critical to understand what types of data flow through your APIs and how that affects your ability to comply with regulatory requirements. API posture management provides a comprehensive view of traffic, code, and configurations to assess your organization’s API security posture. Core capabilities needed:
Automatically scanning infrastructure to uncover misconfigurations and hidden risks
Creating custom workflows to notify key stakeholders of vulnerabilities
Identifying which APIs and internal users are able to access sensitive data
Assigning severity rankings to detected issues to prioritize remediation
API runtime security: You’re no doubt familiar with the concept of “assume a breach.” API-specific breaches and attacks are reaching that same degree of inevitability. For all of your APIs that are live in production, you need to be able to detect and block attacks in real time. Core capabilities needed:
Monitoring for data tampering and leakage, policy violations, suspicious behavior, and API attacks
Analyzing API traffic without additional network changes or difficult-to-install agents
Integrating with existing workflows (ticketing, SIEMs, etc.) to alert security/ operations teams
Preventing attacks and misuse in real time with partially or fully automated remediation
API security testing: API development teams are under pressure to work as quickly as possible. Speed is essential for every application developed, making it easier for a vulnerability or design flaw to happen and subsequently go undetected. Testing APIs in development before they are released into production greatly reduces both risk and the cost of fixing an API that is vulnerable. Core capabilities needed:
Running a wide range of automated tests that simulate malicious traffic
Discovering vulnerabilities before APIs enter production, reducing the risk of successful attacks
Inspecting your API specifications against established governance policies and rules
Running API-focused security tests that run on demand or as part of a CI/CD pipeline
The benefits of API lifecycle management
Effective API lifecycle management provides organizations and teams with several significant benefits.
High-quality APIs: Proper lifecycle management ensures that APIs are well designed and secure, and that they meet the needs of users.
Strong API security: Lifecycle management enables teams to improve API security by identifying and fixing API vulnerabilities to prevent threat actors from using APIs as an attack vector.
Efficient development: Quality lifecycle management streamlines the development process, allowing teams to produce new APIs and iterations faster.
Better performance: Continuous monitoring in the API lifecycle helps to optimize API performance.
Version control: API lifecycle management enables teams to seamlessly upgrade APIs to new versions or roll back to previous versions when needed.
The challenges of API lifecycle management
Managing the API lifecycle can present IT teams with several challenges.
Security: Since APIs often expose sensitive data — and are often inadequately secured — they have become a primary attack vector for cybercriminals. To prevent threats, security teams should put capabilities in place for rate limiting, robust authentication, and identifying and eradicating any security vulnerabilities in the code.
Versioning: Teams must ensure that each new version of an API is backward compatible to avoid creating problems for existing integrations.
Documentation: Maintaining up-to-date documentation is essential for developers and stakeholders who rely on APIs. It’s easy for this task to be overlooked as teams race to develop and deploy new versions.
Tools for managing the API lifecycle
IT teams may use a variety of API management solutions to navigate the API lifecycle.
API management platforms: Platforms like AWS API Gateway and Microsoft Azure API Management provide comprehensive solutions for managing, securing, and monitoring the API ecosystem.
API design tools: Solutions like Swagger and OpenAPI provide tools for creating API specifications and documentation.
Automation tools: When testing and deploying APIs, tools like Jenkins or GitLab CI/CD can streamline workflows.
API analytics: Platforms like Google Analytics for APIs track API usage, performance, and metrics.
Developer portals: These provide a centralized hub for API documentation, testing, and community engagement.
FAQs
API stands for application programming interface, a set of protocols and definitions that allow different software components or programs to communicate with each other and share data. By defining the ways that applications interact, APIs make it possible for different applications to request and share information.
The API lifecycle is the series of steps that IT teams take to design, develop, test, deploy, monitor, and retire APIs.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.