BOPLA stands for Broken Object Property Level Authorization. While BOLA refers to a whole object, BOPLA refers to a property inside an object. Because API security controls designed to identify and defend against BOLA attacks may not provide adequate defense against BOPLA, security teams deploy measures designed to defend against both types of attacks.
Broken Object Level Authorization (BOLA) is a security vulnerability that is considered the number one threat for application programming interfaces (APIs), according to the list of OWASP Top 10 API Security Risks for 2023.
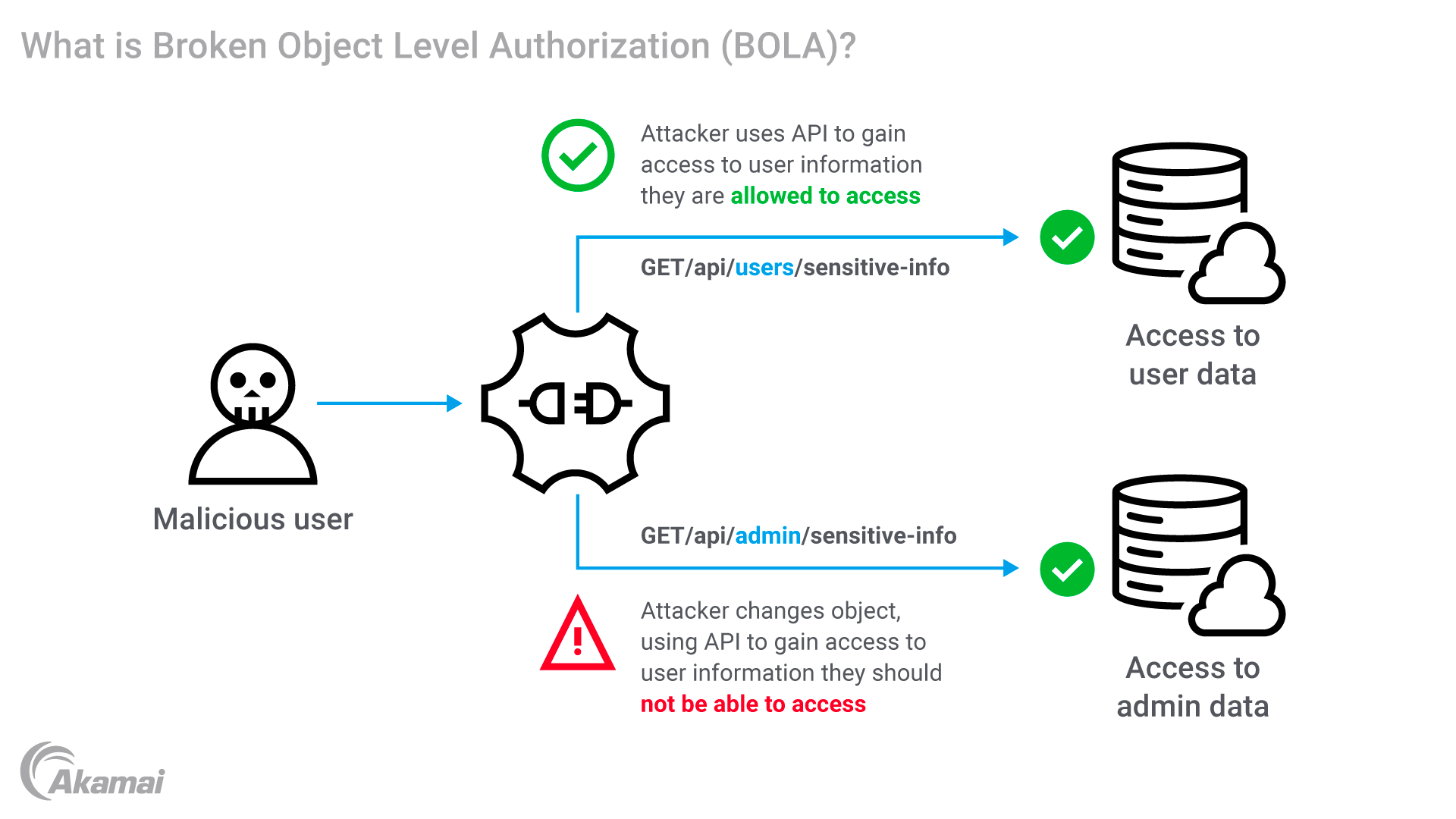
The BOLA vulnerability is a flaw in the access control mechanism of a web application, which allows users to access or manipulate “objects” such as database records, files, or other resources within an IT environment. When the application’s mechanism doesn’t properly enforce access controls, unauthorized users are allowed to perform actions on objects that they should not have permission to access.
While almost every company has APIs that are subject to this vulnerability, BOLA is hard to detect with a vulnerability scanner. That makes BOLA a very attractive target for cybercriminals seeking to access sensitive data. Several major data breaches — including the hack of the United States Postal System (USPS) — have been tied to this particular vulnerability.
How is the BOLA vulnerability created?
BOLA vulnerabilities are often the result of insecure coding practices, where developers fail to write code that properly validates user input or that checks permissions before allowing a user to access an object, even if validation has been granted before.
The BOLA vulnerability is usually caused by flaws in the authorization process, including:
- Failure to validate user-supplied inputs
- Misconfiguration of authorization checks
- Revealing easily identifiable or enumerated resource IDs in the URI, request header, or body
- Failure to check permissions upon each individual request
How does an attack based on the BOLA vulnerability work?
BOLA abuses the process of object level authorization, an access control mechanism for APIs, a process that defines whether users have permission to access data objects. An object is any information that an application can access or use, such as database records or files. When a user is granted authorization, the permission may include the authority to read-only, edit, or add/delete. Permissions may differ based on user groups and roles.
Broken Object Level Authorization occurs when an application does not correctly confirm that the user requesting access actually has the required privileges to access an object or the resources of another user. As a result, users can access other users’ data. Once this happens, hackers can automate requests and gain other authorized access to thousands of records.
For hackers, the first step in a BOLA attack is identifying the vulnerability by testing applications to see how it constructs URLs or API endpoints. Applications that use direct references to internal implementation objects are a strong candidate for a BOLA attack.
To exploit the vulnerability, hackers can use very simple scripting that exchanges the ID of their own resource in an API call with the ID of a resource that belongs to another user. Because the API does not properly check the authorization, it may provide the hacker with access to the requested resource.
What is the impact of a BOLA attack?
BOLA attacks are considered both easy to execute and highly dangerous. This vulnerability may allow attackers to:
- View unauthorized data
- Access sensitive information
- Hijack administrative accounts
- Steal data for financial fraud and identity theft
How can security teams detect BOLA vulnerabilities?
Scanning and testing APIs is the most effective way to uncover BOLA vulnerabilities. These steps may include:
- Reviewing all API endpoints and identifying the uses
- Writing test cases that require object IDs to be replaced — if error messages are not returned, the API may be vulnerable
- Testing objects for read, update, edit, and delete actions
- Reviewing functions that access objects through secondary routes
- Automating the process with API testing solutions to find flaws more quickly
- Conducting manual penetration testing to uncover flaws that live in an API’s business logic layer
How can organizations address BOLA vulnerability?
Security teams can take several steps to protect their organizations against Broken Object Level Authorization.
- Implement robust authorization. Having strong authentication is not enough — all API calls must also be authorized, and the authorization mechanism should be managed from one location for all APIs. Security teams must constantly test well-controlled authorization policies to make sure they’re free of loopholes and logic flaws.
- Map users and accessible objects. Keeping track of which objects can be accessed by each user makes it easier to determine whether a user has a right to access an object upon request.
- Use random IDs. Universally unique identifiers (UUIDs) are far more difficult for unauthorized attackers to guess than auto-incrementing IDs. By using IDs that comprise a combination of numbers, letters and symbols, organizations can minimize the risk of malicious tampering.
- Deploy API gateway security and rate limiting. Serving as a single entry point for all API requests, an API gateway provides greater security by controlling how requests are managed. Rate limiting prevents attackers from making too many requests in a limited period of time — a hallmark of BOLA attacks.
- Focus on the business logic layer. BOLA flaws are difficult to find because they often exist in an API’s business logic layer. IT teams must meticulously test to find vulnerabilities that may not be discovered with vulnerability scanners.
- Encrypt sensitive data. Encryption ensures the data will be harder or impossible to read if it is exposed via a BOLA attack.
- Adopt a Zero Trust framework. Zero Trust requires all users be authenticated and authorized before accessing resources. Under a Zero Trust model, each API call must be authenticated, and then authentication mechanisms must determine whether the user is allowed to access the resource.
- Implement AI-based API security testing AI testing platforms deliver comprehensive and continuous testing of APIs.
Frequently Asked Questions (FAQ)
An application programming interface (API) is a set of protocols and definitions that allows very different software programs and components to communicate, exchange data, and share functionality. By defining the ways that applications interact, APIs make it possible for diverse systems to request and share information involved in many important functions and common transactions, from ecommerce and mobile payments to social media and cloud services.
The Open Worldwide Application Security Project (OWASP) is a nonprofit organization dedicated to improving software security. Each year, OWASP publishes a list of the top 10 security risks for web applications as well as APIs. The report is compiled by a team of security experts from around the world.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.