Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
A data breach is a security incident in which confidential information or sensitive data is stolen, leaked, accessed by unauthorized individuals, or exposed to the public. Data breaches may be the result of unfortunate accidents, inadvertent mistakes, or malicious activity and cybercrime. Data breaches have become quite common as organizations rely more heavily on digital data and as cyberthreats continue to evolve. Consequently, data security has become a top priority for organizations in every industry, including financial companies, healthcare organizations, retailers, and many others.
While a data breach can affect individuals, as well as organizations of any size, larger companies are the most common victim because of the amount of valuable data their systems hold. Some of the most notable breaches have resulted in enormous financial losses for companies such as Microsoft, Marriott, TJX, Yahoo, Verizon, Equifax, SolarWinds, and Colonial Pipeline.
What type of data is exposed in a data breach?
The information exposed in a security breach may include personal data like Social Security numbers and login credentials, or corporate data like intellectual property and bank account numbers. Other information in a data breach may include:
- Personally identifiable information (PII) such as names, Social Security numbers, addresses, phone numbers, first dates, passport numbers, driver’s license numbers, and bank account numbers
- Financial information, including bank account numbers, debit or credit card numbers, tax forms, and financial statements
- Credentials such as usernames and passwords
- Personal health information, including medical records
- Intellectual property such as patents, trade secrets, customer lists, product designs, business research, and source code
What is the impact of a data breach?
When a data breach occurs, organizations may suffer losses at many levels.
- Financial loss. Attackers may use data from a breach to gain access to bank accounts and transfer large amounts of money outside the organization.
- Fines. When data breaches result in the exposure of customer data, organizations may incur huge penalties and fines for violating regulations concerning data privacy.
- Legal consequences. Customers, partners, and employees whose data is exposed may file lawsuits against the company that suffered the breach.
- Damage to reputation. When a company suffers a breach, customers may be unwilling to do business with an organization they don’t trust to protect their data.
- Loss of business opportunity. The loss of intellectual property or confidential business plans may prevent a company from moving forward with new product development and business opportunities.
How does a data breach occur?
Data breaches happen in several ways.
- Inadvertent mistakes. A data breach may occur when an employee mistakenly sends confidential information to the wrong email recipient, fails to encrypt an email attachment, or accidentally loses a laptop, hard drive, or flash drive. Misconfiguration may also lead to inadvertent data breaches when IT teams fail to adequately configure the security settings on a web app or server.
- Malicious insiders. Employees, contractors, or other individuals with access to an organization’s IT environment may cause a data breach by purposefully leaking information, selling data to a third party, providing a competitor with intellectual property, or taking sensitive data with them as they leave the company for other opportunities.
- Cyberattacks. Many data breaches are the result of a cyberattack in which threat actors target an organization, gain access to corporate networks, and steal or exfiltrate valuable data.
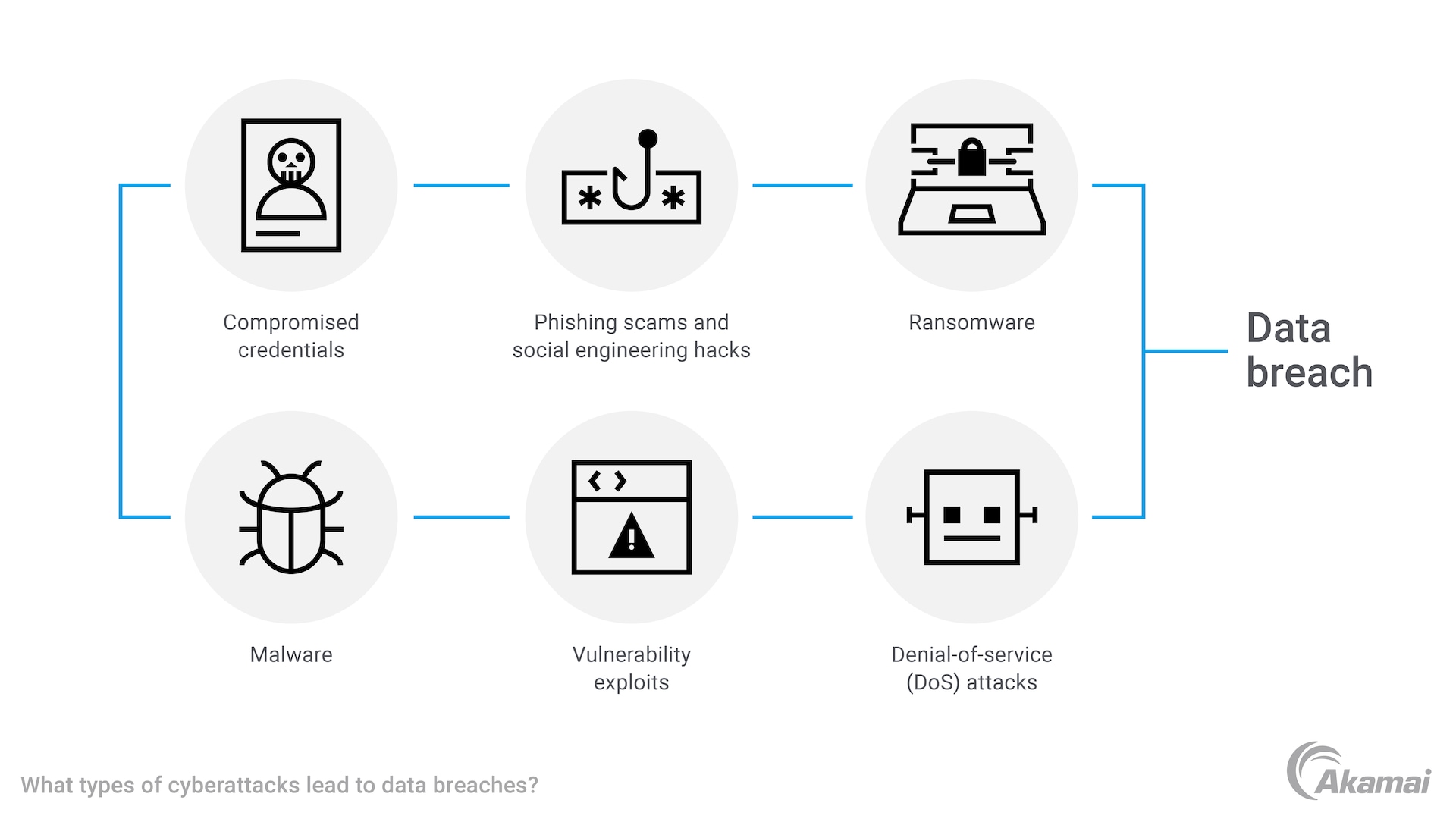
What types of cyberattacks lead to data breaches?
Many of the most common cybersecurity incidents can result in a data breach.
- Compromised credentials. Cybercriminals use a variety of methods to steal login credentials that allow them to easily access a company’s network. In a brute-force attack, for example, hackers use trial-and-error methods to crack a user’s password or other assets such as API keys or SSH logins. Hackers may also use login credentials that were exposed in a previous data breach to gain access to new accounts and systems.
- Phishing scams and social engineering attacks. Many data breaches are the result of phishing attacks, in which criminals use social engineering techniques to dupe victims into revealing login credentials, credit card information, or other data that enables access to a system.
- Ransomware. In a ransomware attack, cybercriminals encrypt important files on a company’s network, preventing users from accessing data or apps until the company has paid a ransom in exchange for a decryption key. In many cases, criminals also steal valuable data before encrypting files, using it for financial gain or extorting the company with the threat of exposing it.
- Vulnerability exploits. Many hardware and software systems contain vulnerabilities that can be exploited by hackers to gain access to a corporate network.
- Denial-of-service (DoS) attacks. In a denial-of-service attack, hackers cause websites, networks, and other IT resources to crash or slow down by overwhelming them with traffic and fake requests. By tying up all available resources, DoS attacks prevent systems from providing services to legitimate users. Attackers may also use a botnet — a robot network of thousands or millions of malware-infected computers and devices — to launch distributed denial-of-service (DDoS) attacks.
- Malware. In a malware attack, cybercriminals introduce malware into a system by tricking victims into clicking on a malicious link, opening a malicious attachment, or visiting a malicious website. The malware that is downloaded to the victim’s computer provides attackers with access to an IT environment and the data within it.
How do criminals profit from data breaches?
Data breaches often result in the exposure of information like credit card numbers, bank accounts, or usernames and passwords that attackers may use to access financial accounts, drain funds, or sell on the dark web. Personally identifiable information such as Social Security numbers may be used in identity theft schemes, in which attackers open accounts or take out loans in an individual’s name.
Data breaches can also be a form of corporate or state espionage, in which organizations steal intellectual property from a competitor or a nation-state steals classified data concerning an enemy’s military options.
How can organizations protect against a data breach?
Organizations can deploy a number of strategies and solutions to prevent data breaches.
- A Zero Trust approach. In a zero trust security framework, no user, device, or application is inherently trusted. Instead, each must be authenticated and validated every time a request is made to access an IT asset. Additionally, access is granted only to the resources needed at a given moment to perform a specific task. This approach prevents users and devices from having the kind of overly broad permissions that can lead to data breaches. It also blocks attackers from moving freely throughout an IT environment.
- Identity and access management (IAM). Using multi-factor authentication and enforcing strong password policies can help prevent attackers from gaining unauthorized access to systems.
- Security awareness training. Regular education about the nature of threats can help employees recognize phishing attacks and other threats that may lead to a data breach. Training on security hygiene helps to establish best practices that prevent security mistakes.
- Incident response plan. When a breach occurs, businesses must have a plan for mitigating and reporting the attack, identifying stolen assets, limiting the damage, and communicating with customers, employees, and the media.
- Optimal patching cadence. To prevent attacks that exploit vulnerabilities in software or hardware, security teams must update systems and apply patches in a regular and timely way.
- Enterprise-class encryption. Encrypting sensitive information prevents it from being used or accessed in the event of a data breach.
- Microsegmentation. IT teams can use software-defined microsegmentation to segment a network and place granular security policies around individual, business-critical workloads. This practice prevents attackers who have successfully breached one part of a network from accessing sensitive data in other areas, effectively limiting the “blast radius” of an attack.
- Web and cloud security solutions. Technologies like a web application firewall (WAF) and API gateway security solutions can help to prevent many types of attacks and exploits that may lead to a data breach.
- Network security solutions. Technologies and solutions like firewalls, DDoS protection, bot detection, and data loss prevention (DLP) can help to increase network security.
Frequently Asked Questions (FAQ)
Microsegmentation is a network security technique that segments a network and the assets within it into granular areas or zones to protect individual workloads, applications, and virtual machines (VMs) with narrowly defined security controls. By isolating these workloads with individual security controls, organizations can better contain security threats and stop data breaches by blocking lateral movement.
Credit card security involves a set of protocols, technologies, and best practices that help businesses to protect credit card information processed and/or stored within their IT environments. Credit card security solutions help organizations to protect sensitive financial information, mitigate the loss of credit card data, prevent credit card fraud, and avoid adverse outcomes such as regulatory fines, legal action, and losses to revenue, reputation, and customer trust.