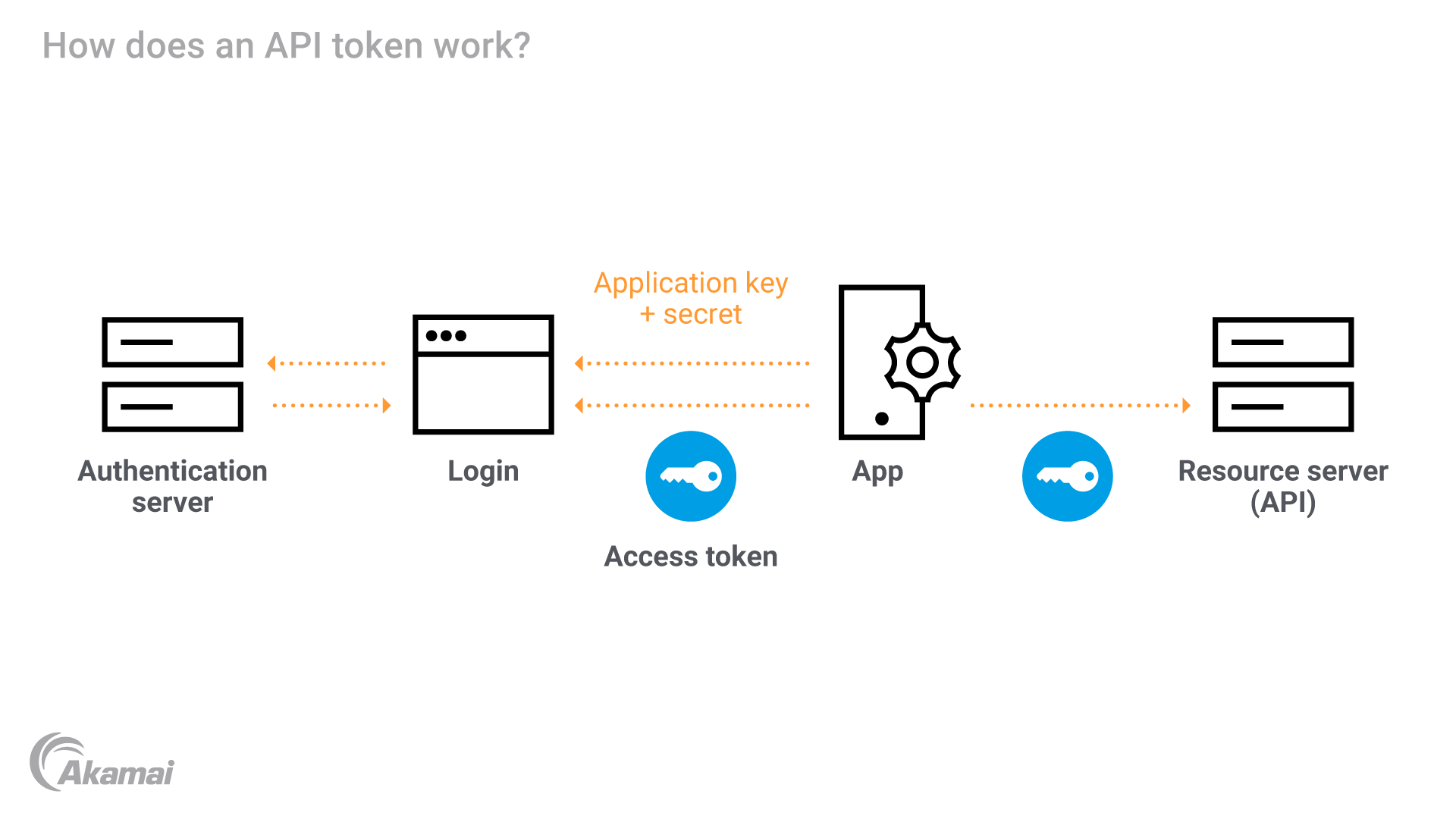
Yes. One example is our native connector technology that integrates Akamai App & API Protector and Akamai API Security. When pulling data from the Akamai platform, API Security adds one additional layer of control by tokenizing some of the headers and metadata and only granting authorized people the ability to detokenize them.
In the world of data security and payment processing, tokenization is the practice of protecting sensitive data by replacing it with a token — a unique and nonsensitive string of symbols randomly generated by an algorithm that has no meaning or exploitable value. The token is a unique identifier that links to the original data but cannot be deciphered or “cracked” in order to access the original information, which is kept safe in a centralized server or “token vault” that typically resides outside of an organization’s IT environment. The only way to see the original data is by using the system that created the token.
Why is tokenization important?
The concept of tokenization plays an important role in protecting sensitive data such as financial account information, credit card numbers, personally identifiable information (PII), medical records, and other confidential and important data. Digital transformation has led to an exponential growth of information and has been accompanied by a rapid rise in cybercrime , with attackers seeking to steal and exploit a broad range of sensitive data. Tokenization is critical to cyber resilience, data leak protection, and data breach protection, helping organizations avoid the adverse outcomes that accompany devastating cyberattacks .
What kind of information may be tokenized?
Tokenization has traditionally been used to protect credit card data, bank account numbers, payment details, and other financial information that’s stored on servers. However, recently tokenization has expanded to protect other types of information, including:
Social Security numbers, driver’s license numbers, passport numbers, and other types of identifiers
Medical data or health insurance information
Education and employment details
Email addresses, postal addresses, and telephone numbers
What are the most common use cases for tokenization?
Tokenization plays a role in many digital processes.
Payments. Tokenization enables information about credit cards and financial accounts to be transmitted over the internet or various networks without exposing sensitive data. By protecting financial information in this way, tokenization enables commerce and financial communications while preventing hackers from stealing or duplicating financial data.
Blockchain. A blockchain is a decentralized ledger that exists across a distributed computer network to digitally record transactions. Blockchain technology uses tokenization to create a digital representation of an asset. Digital assets may be physical items like art, financial assets like equities or bonds, intangible assets like intellectual property, or non-fungible tokens (NFTs) that can’t be replicated and provide digital proof of ownership that can be bought and sold.
Smart contracts. A smart contract is an application that automatically executes when specific conditions are met — the terms of a smart contract are established in code on a blockchain that cannot be altered.
How tokenization works?
The tokenization process generates tokens in one of several ways: through mathematical reversible algorithms, through one-way nonreversible cryptographic functions, or through static tables that randomly generate token values. Once it is generated, the digital token becomes the exposed information that is stored on servers while the sensitive information remains safe within a token vault. For tokens in the financial industry, the vault is typically in a merchant’s payment gateway and is the only place where the token can be mapped back to the sensitive data it represents.
Vaultless tokenization offers an alternative to the traditional token vault. In this scenario, sensitive information is tokenized using a reversible algorithm, which precludes the need to store the original information in a vault.
Benefits of tokenization
Data protection. Tokenization solutions minimize the impact of a data breach by making data unreadable to hackers. Even when attackers gain access to tokenized data, they cannot read it unless they access the corresponding secure vault where the real data is stored.
Compliance. Tokenization provides organizations with an easier way to comply with regulations such as the Payment Card Industry Data Security Standard (PCI DSS). This regulatory framework requires that retailers not store credit card numbers on point-of-sale terminals or in databases after customer transactions. Tokenization provides an affordable way to comply with PCI DSS regulations by minimizing the number of systems that have access to sensitive information, thereby reducing the potential scope of sensitive data exposure.
Maintenance. Tokenization does not usually require IT teams to constantly upgrade systems in order to meet evolving standards.
Compatibility. Tokenization is often a more compatible security solution than encryption for legacy systems.
Efficiency. Tokenization is also less resource-intensive than encryption processes.
Types of tokens
Tokenization processes typically use several types of tokens.
Currency/payment tokens. These tokens exist solely as a way to pay for goods and services.
Utility tokens. These tokens offer something other than a means of payment. A utility token may offer direct access to a platform or product or discount on future offerings.
- Asset/security tokens. Asset tokenization is the process of creating a token that offers a positive return on investment, similar to a bond or equity.
FAQs
Encryption differs from tokenization in two important ways. While tokenization replaces data with a string of symbols that match the length and the type of data being protected, encryption may alter both the length and the data type. Additionally, encrypted data may be decrypted by anyone with access to the encryption key. In contrast, because tokenization does not use decryptable information to represent sensitive data, it cannot be mathematically reversed with a decryption key. However, reversible tokens can be detokenized and reverted back to their original values.
Credit card security refers to the practices, technologies, and protocols that retailers and payment card issuers use to protect credit card information from being lost, leaked, or stolen. Effective credit card security involves a multilayered approach to web security and network security that may include solutions for tokenization, encryption, authentication, firewalls, fraud detection, and data loss prevention.
APIs can have a lot of sensitive data, such as payment card industry (PCI) compliance, personally identifiable information (PII), and protected health information (PHI). Tokenization offers the ability to differentiate between different values while masking the actual values. With Akamai API Security (link to https://www.akamai.com/products/api-security), tokenization is reversible by the customer, which enables both automated response as well as manual investigation.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.