Broken Object Level Authorization (BOLA) is a security vulnerability that is considered the #1 threat for application programming interfaces (APIs), according to the list of OWASP Top 10 API Security risks for 2023. The BOLA vulnerability is a flaw in the access control mechanism of a web application, which allows users to access or manipulate “objects” — database records, files, or other resources within an IT environment. When the application’s mechanism doesn’t properly enforce access controls, unauthorized users are allowed to perform actions on objects that they should not have permission to access.
Broken Object Property Level Authorization (BOPLA) is a security vulnerability in application programming interfaces (APIs) that, because of inadequate authorization checks, may allow hackers to view or manipulate the properties of sensitive objects. This may potentially result in data loss, exposure of sensitive data, privilege escalation, or account takeover. BOPLA is listed at #3 in the 2023 list of the OWASP Top 10 API security issues.
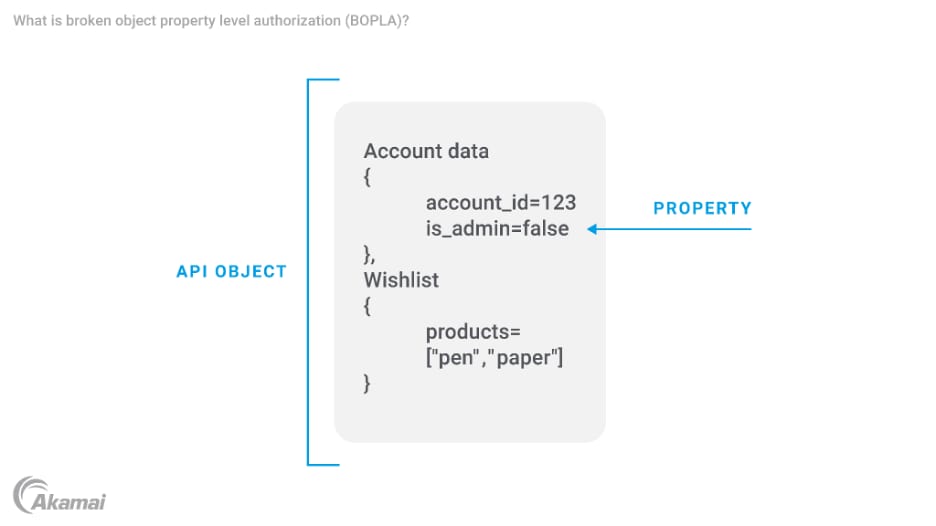
What is the BOPLA vulnerability?
Web applications retrieve data and populate fields on front-end pages by querying APIs for information about objects like database records or files. Each object typically contains several data points or “properties.” For example, the profile associated with a user account may include properties like first_name, last_name, email_address, password, SSN_number, and is_admin, which indicates whether the user has administrative privileges.
During an API call, APIs often send more information than is technically required in the API response, leaving it to the client application to extract the data it needs and render a view for the user. This vulnerability creates risk in an API endpoint in two different ways:
Excessive Data Exposure. This occurs when an API response includes more information than the API call requested, and possibly includes sensitive information — password and SSN_number in this example — that a user or app should not have access to. When it comes to API responses that are shown in a website or app, some of the excessive data is only in the API response itself and can be extracted easily.
Mass Assignment. This occurs when an API endpoint allows an unauthorized user to change, add, or delete the value of an object property. In the example record above, when the API response unnecessarily reveals that an is_admin property exists, attackers could escalate privileges in an unauthorized way by changing the is_admin property to TRUE. This may also let them make changes to other properties or to access other objects that they should not be able to access.
BOPLA was first introduced in the OWASP Top 10 API Security issues for 2023, combining these two previous threats of Excessive Data Exposure and Mass Assignment that appeared separately on earlier lists.
What is BOPLA vs. BOLA?
BOPLA is related to Broken Object Level Authorization (BOLA), which appears at #1 on the OWASP Top 10 API Security list. However, BOLA refers to the authorization to access a whole object, while BOPLA refers to vulnerabilities affecting individual properties within an object.
The basic difference between Broken Object Level Authorization (BOLA) and BOPLA is that BOLA refers to a whole object, while BOPLA refers to a property inside an object.
Even if an API enforces sufficient object level authorization to prevent BOLA attacks, these measures might not be sufficient to protect against BOPLA attacks. To mitigate the BOPLA vulnerability, teams must adopt more specific authorizations that cover the objects as well as their characteristics, and they must also consider the different access levels within API objects, which often have both public and private properties.
What damage can a BOPLA attack do?
Attacks that focus on the BOPLA vulnerability may allow attackers to:
- Alter the properties of objects to which they should not have access
- View sensitive data that should be prohibited from their access
- Escalate privileges to take over accounts
Why are BOPLA vulnerabilities difficult to detect?
Traditionally, security teams have relied on web application firewalls and API gateways to defend APIs from threats. However, WAFs and API gateway security do not take business logic and API context into account, making it impossible to spot sensitive data being sent over an API or to understand the level of exposure that individual data assets represent. These API protection solutions also cannot always distinguish between legitimate calls and malicious activity — for example, a malicious API call that sends a request using the PUT method with additional parameters will appear like a normal API call to a WAF or API gateway.
To detect BOPLA vulnerabilities, security teams need technology that can identify and report on a broad range of sensitive data types that may be included in API requests and responses. Superior solutions should also track anomalous activity where attackers have manipulated API requests with unauthorized parameters. The ability to baseline and track API access for each endpoint and user can help identify excessive consumption, and uncover instances where additional parameters in API calls fall outside of normal behavior. API security should also be able to detect attackers who are probing APIs during the research phase of an attack as they seek to understand the structure and business logic of an API.
How can BOPLA attacks be prevented?
Making sure that code is secure — and that there are no issues with object property permission — should be a high priority for developers. However, BOPLA vulnerabilities are increasingly occurring in third-party APIs that security teams have no control over.
To prevent BOPLA attacks, security teams can take several essential steps.
Educate developers on secure code. Security teams must help developers understand the need for correctly assigning property-level permissions while enforcing a standardized authorization strategy for all API endpoints. Secure code must take into account the user authorization level and authorization requirements of all reference resources. Security policies must rigorously control which fields are editable via allowlists. Developers should also be conservative about the amount and kinds of data returned in API responses, and should only include data that’s necessary for use cases that are well understood.
Zero Trust. Implementing the principle of least privilege — a foundational element of a Zero Trust approach to security — restricts users to the minimum level of access required, helping to prevent BOPLA attacks or to limit the damage they can cause.
Discovery. By identifying vulnerable API endpoints, teams can alert developers to issues and let vendors know when their APIs are vulnerable.
Monitoring. An API security tool can monitor traffic for attacks — including Mass Assignment — that exploit the BOPLA vulnerability.
Strong authorization. When exposing an object within an API endpoint, authorization processes should ensure that the user is actually allowed access to the object properties. Adopting role-based access control (RBAC) ensures that only authorized individuals can access specific properties.
Audits and updates. Continuously checking and updating permissions helps to ensure that they stay current and accurate.
Frequently Asked Questions (FAQ)
An application programming interface (API) is a set of protocols and definitions that allows very different software programs and components to communicate, exchange data, and share functionality. By defining the ways that applications interact, APIs enable different software systems to request and share information that supports important functions in ecommerce, mobile payments, social media cloud services, and many other areas of computing.
The Open Worldwide Application Security Project (OWASP) is a nonprofit organization dedicated to improving software security. Each year, OWASP publishes a list of the Top 10 security risks for web applications as well as APIs. The report is compiled by a team of security experts from around the world.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.