Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
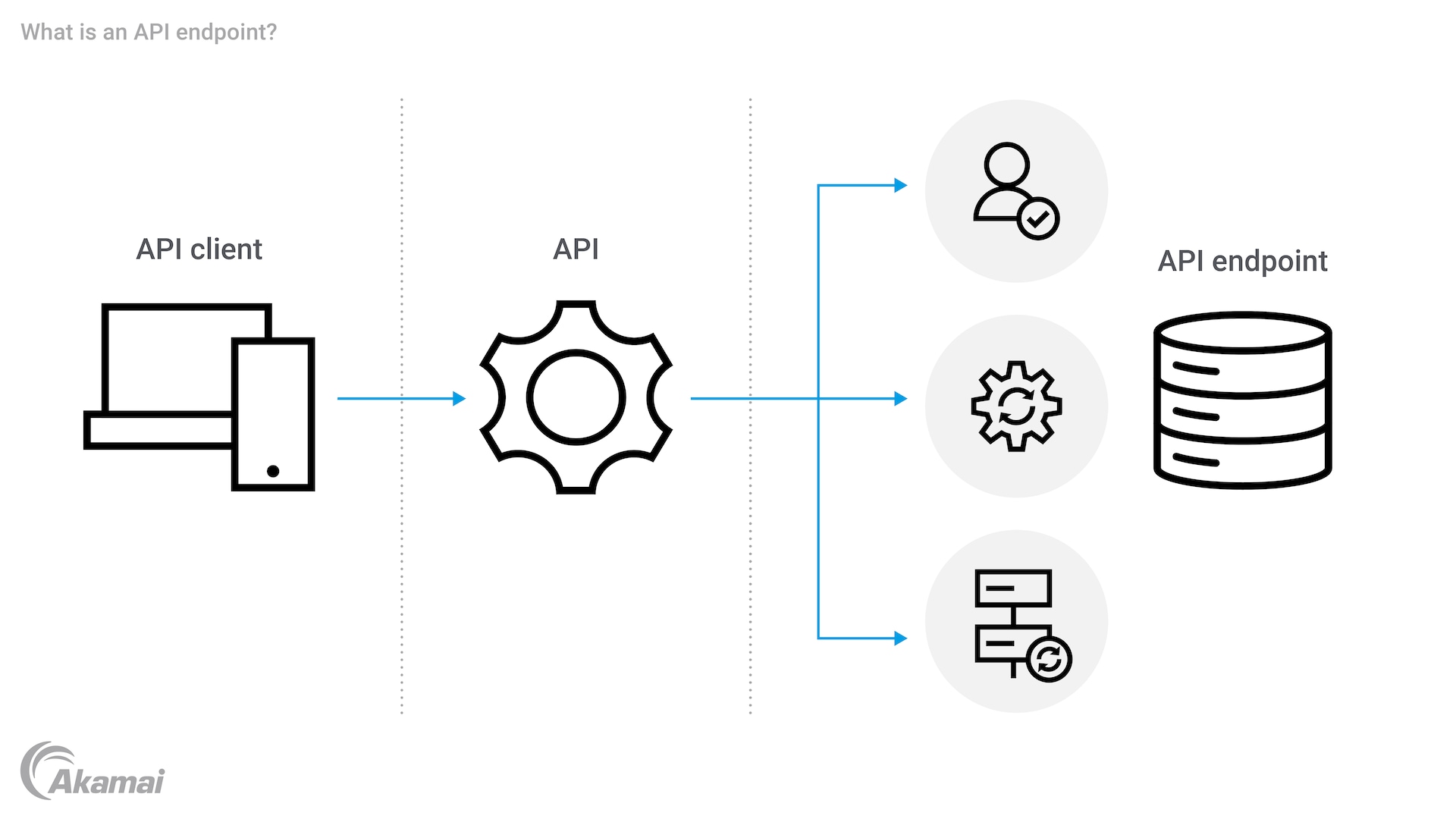
Application programming interface (API) endpoints are specific paths or URLs where a client can access an API. These endpoints serve as an authorized entryway that enables applications to interact with services, retrieve data, and perform certain functions.
Because endpoints may expose sensitive information and allow access to critical systems, cybercriminals view API endpoints as a highly effective attack vector. To secure API endpoints, security teams must adopt a multilayered approach to security and adhere to several key best practices.
What are API endpoints?
An API is a set of definitions and protocols that lets one software program or system communicate with another. Serving an intermediary role, APIs govern how systems are permitted to interact and enable applications to share data and functionality with other applications, customers, and external users. Because they allow an application to access data and functionality from other applications, APIs help connect applications and systems while enabling developers to create more powerful applications faster.
API endpoints act as gateways for communication between applications, providing the exact location of data or resources. At a basic level, API endpoints are specific URLs that enable applications or systems to access the resources or services offered by another application or system. These endpoint URLs enable client applications to make HTTP requests such as GET, POST, PUT, or DELETE as they interact with the API. Requests to endpoints are made by sending a specific HTTP method along with the URL. The API server processes the request and returns a response. This simple interaction is the foundation for modern web applications.
The need for API endpoint security
Because APIs play an essential role in modern applications and digital systems, enterprise security teams must protect and secure API endpoints. Superior API endpoint protection enables organizations to achieve critical objectives.
- Protecting sensitive data: API endpoints often handle sensitive data like personal information, financial details, and intellectual property. When endpoints are not secured, attackers may exploit them to exfiltrate data or compromise the confidentiality and integrity of sensitive information.
- Maintaining user trust: A failure to secure API endpoints can significantly damage an organization’s reputation and erode the trust of users, customers, and partners. Building trust with these stakeholders requires strong endpoint security.
- Ensuring compliance: In many regulated industries, failure to protect sensitive customer information and confidential data may result in steep fines and legal penalties. Superior security helps avoid these outcomes by ensuring compliance with regulations and standards like GDPR, HIPAA, and PCI DSS.
- Preventing financial damage: Data breaches and security incidents often result in direct financial losses when threat actors drain bank accounts or fraudulently transfer funds. However, failure to secure API endpoints also comes with indirect costs of remediation, forensic investigations, and lost business opportunity.
- Avoiding business disruption: API endpoints are integral to the performance of applications and systems. Strong endpoint security helps to prevent outages and downtime as well as denial-of-service (DoS) or distributed denial-of-service DDoS attacks that can cause applications to slow down or crash.
Challenges of securing API endpoints
Maintaining strong API endpoint security requires IT teams to manage a range of challenges.
- Complex attack surface: To make various functions available to other applications and systems, APIs must expose multiple endpoints. This exposure, in conjunction with the growing number of APIs, results in a much larger attack surface. Each exposed endpoint is a potential point of entry for attackers.
- New threats: Attackers are continuously refining their methods and searching for new vulnerabilities to attack. Keeping up with the latest threats and ensuring all API endpoints are protected against threats requires constant vigilance.
- Lack of visibility: IT security personnel often face difficulties in visualizing and inventorying 100% of their APIs, due to the growing complexity and decentralization of IT ecosystems spanning on-premises and cloud. Third-party APIs, open-source APIs, and shadow APIs make the task of identifying assets even more of a challenge.
- Impact on performance: Many of the techniques to secure API endpoints — such as encryption, validation, and rate limiting — have the potential to adversely impact the responsiveness and performance of APIs, depending on the types of tools used. IT teams must closely balance the need for security with the need to provide users with a fast and seamless experience.
- Development timelines: Development teams are constantly under pressure to release new apps and APIs faster. When teams are releasing new products or new versions every day under pressure, the rigor of security testing and adherence to security protocols may suffer.
- Rapid growth: In many organizations, APIs and API endpoints are developed by multiple teams in different areas, without a central framework for introducing security into the process. As a result, it often becomes more difficult to secure API endpoints in production.
- Integrations: APIs are often integrated with other systems, web services, and web applications. When the security posture of these external systems is not up to par, it can introduce new vulnerabilities.
Threats to API endpoint security
The universe of threats to secure API endpoints is large and growing. Some of the most common threats include:
- Broken authentication and authorization processes: When authentication mechanisms are weak or improperly implemented, it may allow attackers to gain unauthorized API access. Issues with authorization processes may enable legitimate users or threat actors to have permissions they should not have, leading to potential breaches.
- Injection attacks: Injection attacks occur when malicious code or data is inserted into an API request to exploit vulnerabilities or flaws in the API’s code. As a result, attackers may be able to execute malicious commands or access unauthorized data.
- Denial-of-service (DoS) attacks: A DoS attack on API endpoints seeks to make an API unavailable to legitimate users by overwhelming it with excessive requests or exploiting vulnerabilities that consume all its resources. Attackers may send a massive number of requests to the endpoint, exceeding its capacity to handle traffic. In other methods, attackers open excessive connections to the API or send maliciously crafted XML payloads to consume server, memory, and CPU resources.
- Exposure of sensitive data: Some attacks exploit information gained from unencrypted traffic, or where an API endpoint unintentionally exposes too much information in response to an API request.
- Machine-in-the-middle (MITM) attacks: In this form of API endpoint threat, attackers intercept and/or alter the communication between two unsuspecting parties, potentially leading to data theft, manipulation, and unauthorized access. To position themselves between a client and an API server, attackers may use techniques like eavesdropping or DNS spoofing.
- Security misconfiguration: When IT teams improperly configure API endpoints, attackers may have an easy way to gain unauthorized access. Misconfiguration may be the result of incomplete setups, insecure settings, or failure to update.
- Brute-force attacks: Attackers frequently use automated tools to attempt to log in to an account using multiple username and password combinations.
Solutions to secure API endpoints
To secure API endpoints, IT teams may deploy a broad range of technologies and solutions.
Authentication and authorization technology: Implementing proven frameworks and technologies for authenticating and authorizing clients is one of the most important steps in securing API endpoints. OAuth 2.0 is a framework that manages secure, token-based authorization and provides limited access to user accounts on an HTTP service. OpenID Connect adds an identity layer on top of OAuth 2.0. JSON Web Tokens (JWT) are a compact, URL-safe means of representing claims to be transferred between two parties.
Data encryption solutions: Using SSL/TLS protocols to encrypt data in transit ensures that API calls cannot be intercepted or tampered with. Transport Layer Security (TLS) technology encrypts data as it moves between the client and the server to prevent eavesdropping and tampering. Secure Socket Layer (SSL) is an older encryption model now mostly replaced by TLS for stronger security.
API gateways: Gateways provide certain protections at API endpoints by acting as a single entry point for API requests. This allows gateways to perform certain security functions such as rate limiting, load balancing, and monitoring.
Rate limiting and throttling: By controlling the number of API requests a client can make in a given time period, rate limiting technology prevents abuse and mitigates DoS attacks. Throttling limits the bandwidth available to clients to prevent resources from being overused.
Firewalls: A web application firewall (WAF) protects endpoints from common exploits like cross-site scripting (XSS), SQL injection, and other security threats.
SIEM: Security information and event management systems collect and analyze activity from different resources across an IT ecosystem — including API endpoints — to provide real-time analysis of security alerts.
Access control: Technology that provides role-based access control (RBAC) restricts access to API endpoints based on the roles of individual users. Attribute-based access control (ABAC) uses attributes such as user, resource, and environment to control access and make context-aware access decisions.
API management platforms: These solutions provide tools for creating, publishing, monitoring, and securing API endpoints. Built-in security features may include tools for API key management, user authentication, analytics, and more.
Monitoring and logging: Tools for contingency monitoring API traffic can reveal unusual patterns that might indicate malicious activity. Logging solutions keep detailed records of API requests and responses for auditing and forensic analysis.
Bot management platforms: Bot management solutions detect and manage traffic from bots to prevent automated attacks, data scraping, and other malicious activities directed at API endpoints.
Security testing: Security testing technology includes automated scanners and manual pen tests.
Best practices to secure API endpoints
In addition to specific security technology, organizations can help secure API endpoints by adhering to several best practices.
- Input validation: Ensuring that all inputs are properly validated can prevent threats like injection attacks. Cleaning or sanitizing inputs to remove potentially harmful data can also help prevent attacks.
- Adopting Zero Trust: In a Zero Trust security model, no entity inside or outside the organization is trusted by default. Every user, device, and application requesting access to an API endpoint must be continuously authenticated and validated on each request. Zero Trust also includes the principle of least privilege, where users and applications have only the very minimum level of access they need to perform their tasks.
- Use HTTPS: By making HTTPS the only communication option available, IT teams can prevent passwords, private keys, and credit card information being easily stolen or read from plaintext by packet sniffers and machine-in-the-middle (MITM) attacks.
- Always use a one-way password hashing technique: Securing passwords with one-way encryption (hashing), rather than symmetric encryption, makes them more secure from attackers.
- Secure API design: Introducing security measures into the development process can help to produce API endpoints with fewer vulnerabilities and flaws.
- Patching and updating: IT teams should regularly apply patches and updates to endpoints to eradicate known flaws, vulnerabilities, and other security risks.
- Threat intelligence: IT teams must keep up with intelligence on API security best practices and the latest threats to API endpoints, such as those found in the OWASP API Security Top 10.
FAQs
API endpoints are specific paths within an API that allow clients to interact with back-end services. Each endpoint represents a unique function or resource.
REST (Representational State Transfer) APIs and SOAP (Simple Object Access Protocol) APIs require different approaches to security due to their underlying protocols and standards. Rest APIs are lighter and simpler, allowing for easier implementation but requiring more comprehensive security mechanisms. Rest API security primarily relies on transport-level security, token-based authentication, and HTTP security mechanisms. SOAP API endpoints require both transport-level security and message-level security using WS-Security standards.
Akamai Security solutions
Akamai Security protects the applications that drive your business at every point of interaction, without compromising performance or customer experience. By leveraging the scale of our global platform and its visibility to threats, we partner with you to prevent, detect, and mitigate threats, so you can build brand trust and deliver on your vision.