Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
API attacks are attempts to use APIs for malicious or otherwise unsanctioned purposes. API attacks take many forms, including:
- Exploitation of technical vulnerabilities in API implementations
- Use of stolen credentials and other account takeover techniques to masquerade as a legitimate user
- Business logic abuse that enables the use of APIs in unexpected ways
The growing threat of API attacks
APIs are everywhere today. From supporting applications and services on the internet to powering mobile apps and cloud-based customer services, APIs are critical to business operations, agility, and competitiveness. This also makes them a highly desirable target for cybercriminals.
Preventing API attacks is not an easy task. The challenge of securing these digital properties is complicated by modern DevOps practices, cloud journeys, and constantly changing API products that introduce new levels of complexity.
Akamai App & API Protector offers powerful, holistic threat protection for API estates. Designed for simplicity and ease of use, App & API Protector incorporates some of the most advanced security automation available today. With this Akamai solution, you can block API attacks while protecting websites and applications from a broad range of threats, minimizing your attack surface, and reducing burden on IT administrators.
The challenge of defending APIs
By enabling software applications and operating systems to communicate with each other quickly and easily, APIs help to accelerate the pace of business, increase collaboration, and improve performance of locations on the web. Yet organizations that defend APIs with traditional network security solutions are unlikely to prevent a breach.
Common API attacks include several well-known attack vectors:
- Machine in the middle attacks (MITM) allow hackers to quietly intercept communications and requests between two endpoints in a communication channel, enabling them to steal sensitive information.
- DDoS attacks (distributed denial-of-service attacks) attempt to overwhelm memory in an API by requesting thousands of connections simultaneously, tying up all available resources and resulting in a crash.
- SQL injection attacks gain access to software by simply injecting malicious code into poorly developed programs.
- Insecure API key generation allows attackers to subvert traditional API security tools by generating and using a variety of API keys from a large pool of users.
- Insufficient logging and monitoring enable hackers to use an initial vulnerability as a foothold to search for additional weaknesses.
- Broken access controls allow attackers to gain access to privileged functions, to modify or delete contents on the website, or to steal sensitive data.
Why customers choose Akamai
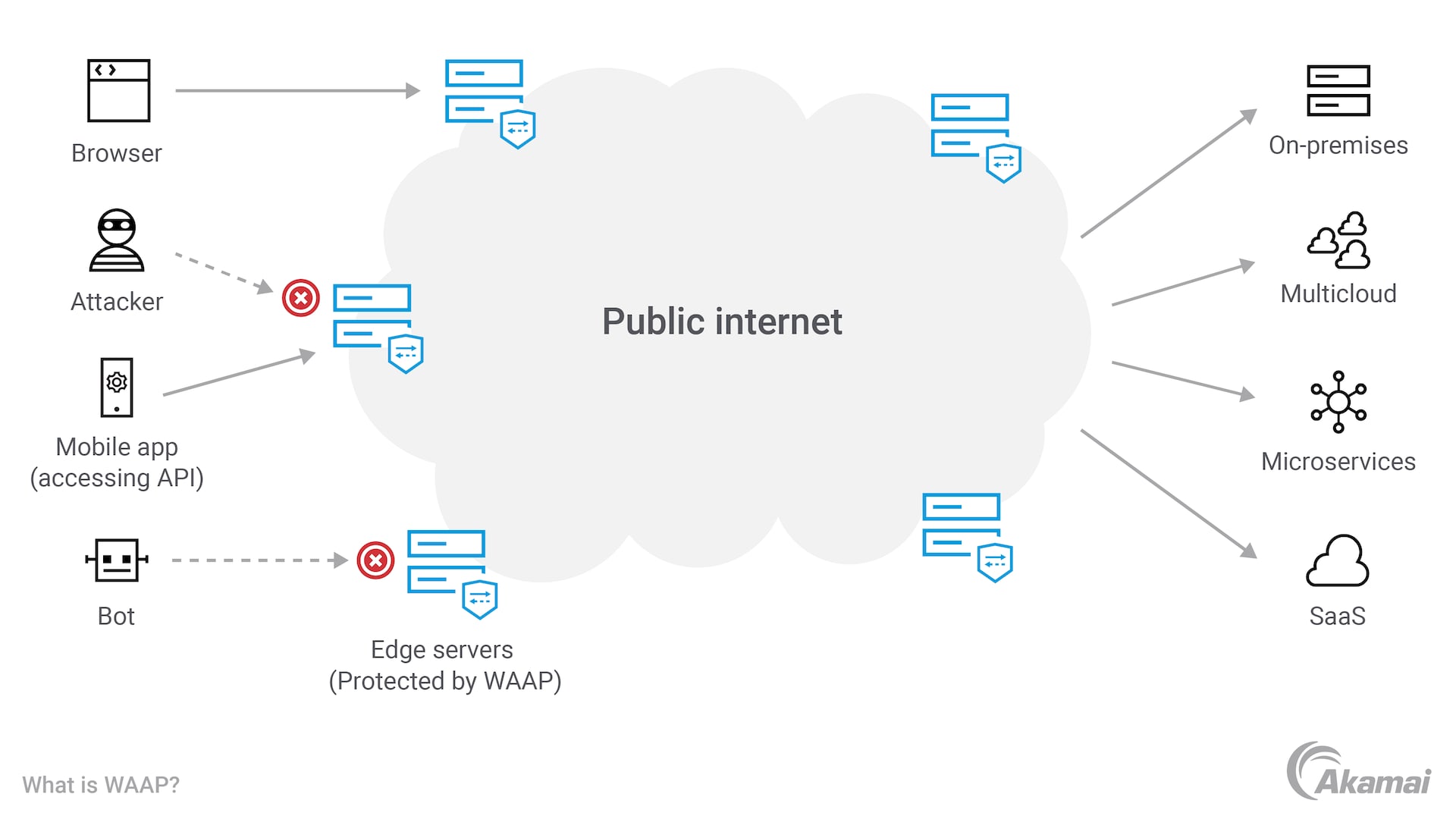
Block API attacks with Akamai
Akamai App & API Protector offers a holistic web application and API protection solution that can strengthen IT security strategies and provide insight into emerging risks, helping IT teams to target security gaps and stop API attacks.
This Akamai solution is powered by the Adaptive Security Engine and combines many industry-leading core technologies in API security as well as cybersecurity solutions for web application firewall, bot mitigation, and DDoS protection.
With App & API Protector, your IT security teams can:
- Reduce your API attack surface. While APIs are an essential mechanism that enable effective web experiences, they may also expose back-end data and logic. Akamai’s solution automatically discovers and protects APIs for vulnerabilities, including the OWASP API Security Top 10.
- Block API attacks. Threat detection capabilities in App & API Protector defend websites, applications, and APIs from a broad range of threats, including broken access control, SQL injection, automated botnets, volumetric DDoS, and more
- .Simplify maintenance. Akamai enables your teams to maintain strong API and application security by relying on automatic updates and automated self-tuning that helps to prevent alert fatigue and allows teams to investigate real cyberattacks, rather than false alerts.
- Deploy a multilayered solution. With Akamai, you can maximize your investment in cyberthreat security technology with a solution that includes web app protections, bot visibility and mitigation, DDoS protection, SIEM connectors, web optimization, edge compute, API acceleration, and more.
Features of Akamai App & API Protector
Akamai App & API Protector offers advanced technology to stop API attacks. Protection begins with visibility, and Akamai’s solution lets you automatically discover a full range of known, unknown, and changing APIs across your web traffic. This allows your teams to protect against hidden attacks, discover errors, and identify unexpected changes. Our technology allows you to easily register newly discovered APIs with just a few clicks. App & API Protector automatically inspects all API requests for malicious code whether APIs are registered or not, establishing strong API security by default.
Additional features of App & API Protector include:
- Bot visibility and mitigation. App & API Protector delivers real-time visibility into bot traffic, with capabilities for detecting and stopping unwanted bots.
- Automatic updates. Our threat researchers analyze more than 454 TB of daily attack data to pinpoint new vectors and identify permutations of existing vectors. Insights gleaned from this research are automatically fed to the adaptive security engine to enable the strongest protection.
- DoS/DDoS protection. Akamai automatically drops network-layer DDoS attacks at the edge, while application-layer attacks can be quickly mitigated within seconds.
- Reporting tools. Akamai’s dashboards, alerting, and reporting tools provide access to detailed attack telemetry and analysis of security events. IT administrators can create real-time email alerts using static filters and thresholds. Web security reporting tools continually monitor and assess the effectiveness of protections against API attacks.
- Simplified onboarding. An easy-to-use wizard makes it simple to onboard properties with integration and configuration workflows that streamline and simplify the onboarding process.
Frequently Asked Questions (FAQ)
Application programming interfaces, or APIs, are the software programs that allow two applications to communicate with each other. APIs simplify and accelerate application development and improve collaboration with customers, partners, vendors, and external users.
An API attack is an attempt by a malicious actor to gain unauthorized access to an API to break into a system or network, or transfer data. When successful, attackers can disrupt business operations or steal data, money, or credentials. Most API attacks take advantage of security vulnerabilities within APIs themselves.
The best defense against API attacks is a multilayered approach to security. Organizations require security solutions that can identify APIs, test them for vulnerabilities, and defend them with an array of protections, including web application firewall technology, multi-factor authentication, bot management solutions, DDoS protections, and other state-of-the-art defenses.
Data exfiltration is a frequent outcome of successful API attacks and abuse. In some cases, it refers to highly sensitive, non-public information that has been stolen by a malicious actor through API attacks and abuse. However, it can also apply to less severe types of API abuse, including aggressive data scraping of publicly available data to assemble large datasets that are valuable in aggregate form.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.

