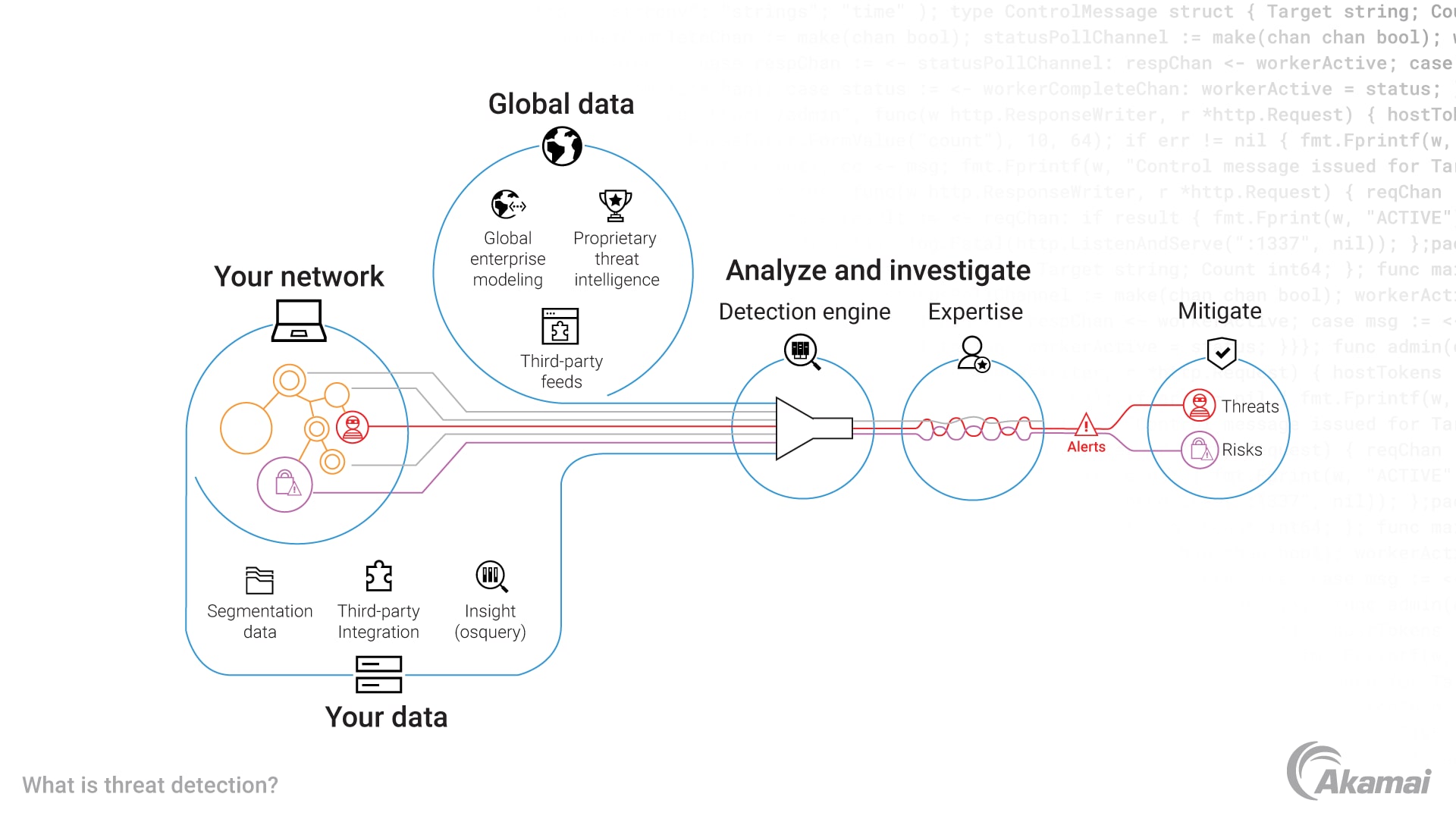
Threat detection is much easier and more accurate when detection engines are continually updated with the latest threat intelligence. Clear insight into the techniques and methods of threat hunting enable security teams to tune and configure threat detection engines more accurately to identify and mitigate threats sooner.
Stopping breaches with superior threat detection
Threat detection is an essential element of cybersecurity today. As cyberattacks grow more sophisticated and devastating, threat detection systems can help to quickly identify attacks in progress and block vulnerabilities or mitigate them before they result in a breach.
Cyberattacks threaten nearly every aspect of your IT ecosystem, from apps and APIs to users and data centers. Consequently, effective threat detection requires multiple layers of security, informed by up-to-the-minute threat intelligence. To minimize cost and effort, automated remediation is critical.
Akamai’s suite of security solutions features multiple threat detection technologies to help your teams identify security threats earlier, mitigate them faster, and minimize the damage and financial consequences.
Akamai security solutions
With more than two decades of security experience, Akamai brings together the best security talent, threat intelligence, and security technology. Our comprehensive platform provides in-depth defense to address our customers’ biggest threats, and the unique breadth of our security tools and defenses enables our customers to access the most effective security capabilities in one platform.
Advanced threat detection is embedded into many of our security solutions.
Akamai Guardicore Segmentation and Akamai Hunt
Our team of Hunters collects indicators of compromise, from IPs and domains to processes, users, and services, by leveraging Akamai Guardicore Segmentation and the massive global threat intelligence of Akamai.
This combination of data generated from Akamai Guardicore Segmentation deployments and Akamai’s global sensors — including more than 7 trillion daily DNS requests made to the Akamai DNS cloud — provides our team with the most comprehensive visibility of your environment.
Secure Internet Access
Protect users and devices with Akamai’s secure web gateway and Secure Internet Access. Multiple static and dynamic malware detection engines proactively identify and block targeted threats like malware, ransomware, phishing, and DNS-based exfiltration of sensitive data. Block malicious payloads for improved zero-day protection by scanning request files and web content to block threats before they compromise endpoint devices.
Client-side Protection & Compliance
Detect and mitigate script-based attacks and web pages by identifying vulnerable resources, detecting suspicious behavior, and blocking malicious activity. By detecting compromised JavaScript behavior, this Akamai technology minimizes user data theft and any compromises to the user experience.
App & API Protector
Multidimensional adaptive threat-based detections correlate threat intelligence across our platform to detect up to 2x more attacks on web applications and APIs. App & API Protector instantly drops network-layer DDoS attacks at the edge while mitigating application-layer attacks within seconds. Enjoy broad protection from injection, Slowloris attacks, automated botnets, and more.
Bot Manager
Rely on unmatched detection and mitigation capabilities to stop bots where they make initial contact — rather than allowing them to reach your site first. Akamai Bot Manager constantly updates protections as threats evolve and new threats arise, automatically incorporating insight from our threat intelligence researchers into intrusion detection and analytics.
Account Protector
Akamai Account Protector uses behavior analytics to profile the activity patterns of account owners, device anomalies, and source reputation. As customer login requests are received, this solution aggregates anomalies from typical user behavior, assessing in real time the risk that the request does not belong to a legitimate account owner.
Threat detection with Akamai Guardicore Segmentation
The threat detection tools in Akamai Guardicore Segmentation can stop dangerous attacks like ransomware, and advanced persistent threats that use lateral movement, to compromise high-value assets within your IT ecosystem. This network security solution is the simplest, fastest, and most intuitive way to segment assets in the data center, cloud, or hybrid cloud infrastructure, enforcing Zero Trust principles within your network.
Akamai Guardicore Segmentation lets you quickly and easily visualize activity within your IT environments and implement precise microsegmentation policies in segmented networks to protect servers, virtual machines, endpoints, and other IT assets. These granular segmentation policies are supported by multiple threat detection methods that allow you to detect breaches faster. These include:
- Reputation analysis. Detect suspicious domain names, IP addresses, and file hashes within traffic flows.
- Policy-based detection. Instantly recognize unauthorized communications and noncompliant traffic with security policies at the network and process level.
- Dynamic deception. Deploy a redirection architecture to dynamically generate live environments that engage hackers and identify their methods of suspicious activity — without disrupting data center performance.
- Managed threat hunting. For Akamai Guardicore Segmentation customers, our team can proactively hunt for ongoing and emerging attacks in your network, minimizing dwell time and reducing overall time to mitigation.
Managed threat detection services
Akamai Managed Security Service (MSS) provides access to experienced security experts and proven online defenses to help achieve a stronger security posture. Our fully managed solution integrates proactive monitoring, reporting, threat detection, fast incident response, periodic tuning, and dedicated security expertise in a service with the scale to protect your organization against the largest, most sophisticated threats and the latest attack vectors.
MSS includes proactive monitoring, with visibility into online activity for early threat detection. Our experts perform real-time analysis to detect anomalies in traffic behavior and prevent potential threats. Additional elements of Akamai MSS include:
- Rapid incident response. When a threat is detected, we deliver help immediately or within 30 minutes depending on the severity of the event.
- Continuous optimization. Our team performs security health checks, in-depth analyses, and configuration fine-tuning.
- Advisory services. Get custom recommendations from a dedicated security expert who understands your goals.
- Operational readiness. Future-proof security processes with exercises and drills to improve communication, escalation paths, and agility.
- In-depth reporting. Uncover new insights through monthly reports, quarterly business reviews, postmortems, and more.
Frequently Asked Questions (FAQ)
Threat detection is the practice of continuously analyzing IT ecosystems to identify potentially malicious activity that could compromise security.
Akamai’s suite of security solutions features multiple threat detection technologies to help your teams identify security threats earlier, mitigate them faster, and minimize the damage and financial consequences.
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.