A Retrospective on DDoS Trends in 2023 and Actionable Strategies for 2024

Executive summary
The year 2023 was a milestone year in terms of distributed denial-of-service (DDoS) attack trends. Cybercriminal groups, geopolitically motivated hacktivists, and malicious actors utilized the relatively inexpensive cost of launching DDoS attacks, the scale of massive botnets built from everyday digital and Internet of Things (IoT) devices, and protocol-level zero-day vulnerabilities to launch record-breaking attacks on businesses, government institutions, and, most disturbingly, on critical but vulnerable public infrastructure, including hospitals.
In most cases, the assumed goals are to cause damage, productivity loss, and financial losses and to gain public attention, which is why these threat actors select an increasingly broad range of victims who are known to have insufficient IT security. It is important to remember that DDoS attacks are targeted attacks for which the threat actors consciously select their targets.
Throughout 2023, DDoS attacks became more frequent, longer, highly sophisticated (with multiple vectors), and focused on horizontal targets (attacking multiple IP destinations in the same attack event). Banking and financial services industries topped the charts of the most targeted verticals. The attacks on these industries often aimed to inflict reputational damage or distract security professionals to launch secondary ransomware attacks. The number and scale of DDoS attacks in Europe, the Middle East, Africa (EMEA) region, and the Asia-Pacific (APAC) region now rival those in North America.
It is in this intense threat landscape that Akamai proactively upgraded the Prolexic DDoS protection platform with a new software-defined architecture; launched several new cloud scrubbing centers to create a massive dedicated defense capacity; and added multiple new capabilities that provide comprehensive, flexible, and reliable DDoS protection whenever, wherever, and however customers need it.
A year of broken records
DDoS attacks have continually grown in size and sophistication, but 2023 accelerated this trend at an unforeseen pace. Even security vendors and their respective websites are being attacked, and although Akamai has been effective in mitigating attacks, others have not. In February 2023, Akamai successfully protected a customer in APAC from the largest DDoS attack ever launched against a Prolexic customer. The attack peaked at 900.1 gigabits per second (Gbps) and 158.2 million packets per second (Mpps). In September, Akamai again detected and prevented the largest DDoS attack directed at one of the biggest and most influential U.S. financial institutions. Cybercriminals used a combination of ACK, PUSH, RESET, and SYN flood attack vectors, peaking at 633.7 Gbps and 55.1 Mpps.
Were these record-setting attacks in 2023 an anomaly in an otherwise staid state of cybercrime? Not at all! These attacks were very much in line with the trend of “shock and awe” DDoS attacks that started in 2022. Last year, Akamai successfully and repeatedly defended a customer in Europe from a record-breaking DDoS assault that peaked at 704.8 Mpps. In fact, 8 of the 10 largest DDoS attacks mitigated by Akamai took place in just the past 18 months.
While these attacks grabbed headlines for their complexity, sophistication, and size, there were several additional high packets-per-second Layer 3 and Layer 4 DDoS attacks this year driven by geopolitical hacktivism and other malicious motivations. In fact, Akamai observed the highest number of such attacks in 2023 — nearly a 50% increase from 2021 (Figure 1).
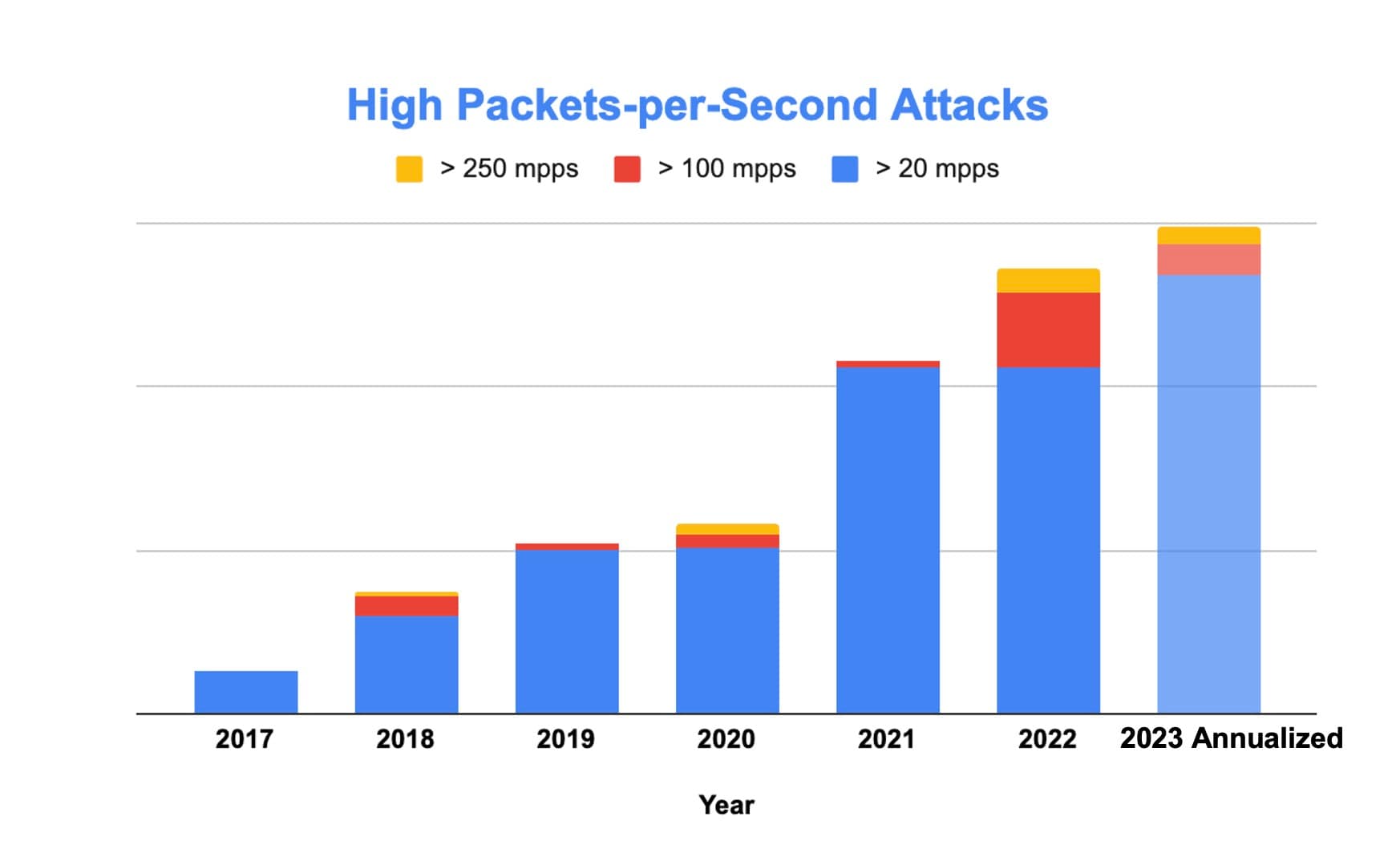 Fig. 1: The total number of high packets-per-second Layer 3 and Layer 4 DDoS attacks increased by nearly 50% between 2021 and 2023. Source: Akamai Prolexic DDoS threat intelligence
Fig. 1: The total number of high packets-per-second Layer 3 and Layer 4 DDoS attacks increased by nearly 50% between 2021 and 2023. Source: Akamai Prolexic DDoS threat intelligence
Old protocol, new zero-day vulnerability — and a whole lot of DDoS
In September and October 2023, Akamai collaborated with key industry stakeholders and partners to develop a response to the HTTP/2 Rapid Reset zero-day vulnerability (CVE-2023-44487) that cybercriminals exploited to launch massive Layer 7 DDoS attacks. The ability of HTTP/2 to use multiplexing to process up to 100 active streams over a single TCP connection became a highly potent vulnerability when attackers launched a sequence of stream requests, immediately followed by a reset for that stream.
This triggered request logic in the web application server, but since the stream was immediately canceled, the intended target continued to process all previously initiated streams, ultimately resulting in hundreds of millions of requests hitting a web server every second, and thereby completely overwhelming the server.
Customers using Akamai Connected Cloud and Akamai’s DDoS protection solutions did not have to take any additional steps to protect their web servers from this novel DDoS attack. Fundamental Akamai security capabilities like Layer 7 HTTP rate controls, caching, web application firewall rules, and IP blocking and/or geoblocking via Akamai App & API Protector effectively protected customers from HTTP/2 Rapid Reset attacks.
Attacking DNS infrastructure to take businesses offline
Akamai observes more than 11 trillion DNS requests daily, and this vantage point provides deep insight into the tactics, techniques, and procedures (TTP) utilized by attackers to take down the DNS infrastructure of businesses and institutions. After a short dip in H1 of 2022, there has been a major resurgence in DNS attacks. Almost 60% of the DDoS attacks mitigated by Akamai in 2023 had a DNS component (Figure 2).
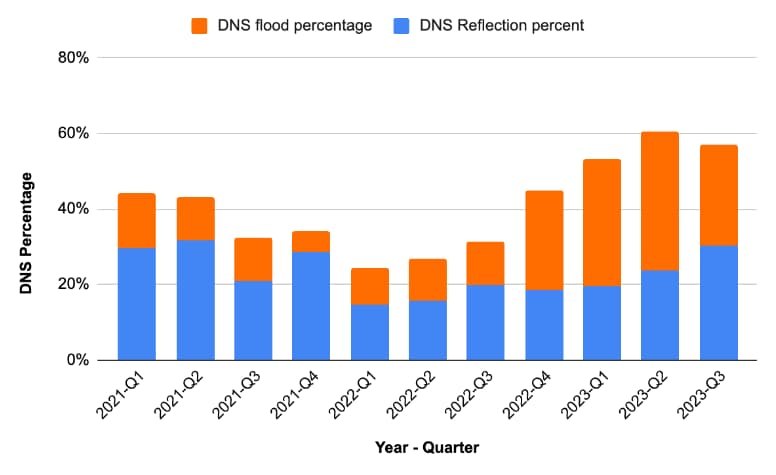 Fig. 2: Nearly 60% of DDoS attacks in 2023 had a DNS component, which is a nearly 200% increase from the Q1 of 2022. Source: Akamai Prolexic DDoS threat intelligence
Fig. 2: Nearly 60% of DDoS attacks in 2023 had a DNS component, which is a nearly 200% increase from the Q1 of 2022. Source: Akamai Prolexic DDoS threat intelligence
According to an Akamai State of the Internet (SOTI) report published in March 2023, up to 16% of organizations encountered command and control (C2) traffic in their network, thereby indicating an attack in progress or a breach that could further pave the path for a ransomware attack. The all-pervasiveness of the DNS attack surface was evident by the fact that attackers targeted everything from websites and IoT-enabled devices to home networks and everything in between.
Banking and financial institutions under attack
The banking and financial services industry vertical claimed the number 1 spot for the highest number of DDoS attacks in 2023 — not a prize you want to win! Financial institutions have increasingly been a target since 2021 (Figure 3). In the prior years, roughly 10% of the DDoS attacks were targeted at financial services institutions. That rate increased to about 20% in 2021 and 2022 and peaked at about 35% in 2023.
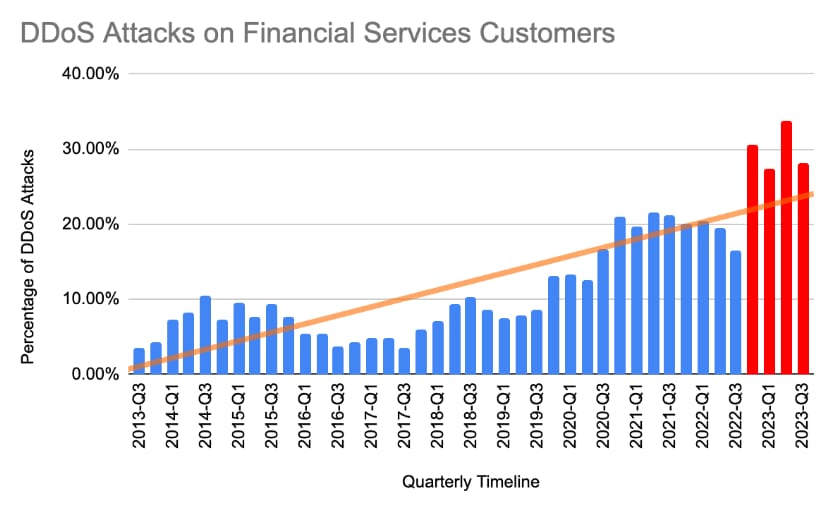 Fig. 3: Companies in the banking and financial services industry witnessed the largest number of DDoS attacks in 2023. Nearly 35% of all DDoS attacks were aimed at the financial sector. Source: Akamai Prolexic DDoS threat intelligence
Fig. 3: Companies in the banking and financial services industry witnessed the largest number of DDoS attacks in 2023. Nearly 35% of all DDoS attacks were aimed at the financial sector. Source: Akamai Prolexic DDoS threat intelligence
Our SOTI report from September 2023, The High Stakes of Innovation: Attack Trends in Financial Services, provides an in-depth look at how cybercriminals are utilizing DDoS attacks to target financial services institutions across the world.
DDoS attacks in the financial services industry have also been on the rise because of the dramatic increase in the power of virtual machine botnets and geopolitical hacktivism motivated by the wars in Ukraine and Israel.
In fact, pro-Russian hacktivist groups announced in early June 2023 that they would carry out massive coordinated DDoS attacks on both European and U.S. financial organizations. Killnet, REvil, and Anonymous Sudan were among the adversaries mentioned. Perhaps this pro-Russian hacktivism better explains the regional shift in DDoS attacks in the financial services vertical, as EMEA now has almost double the number of events as North America (Figure 4).
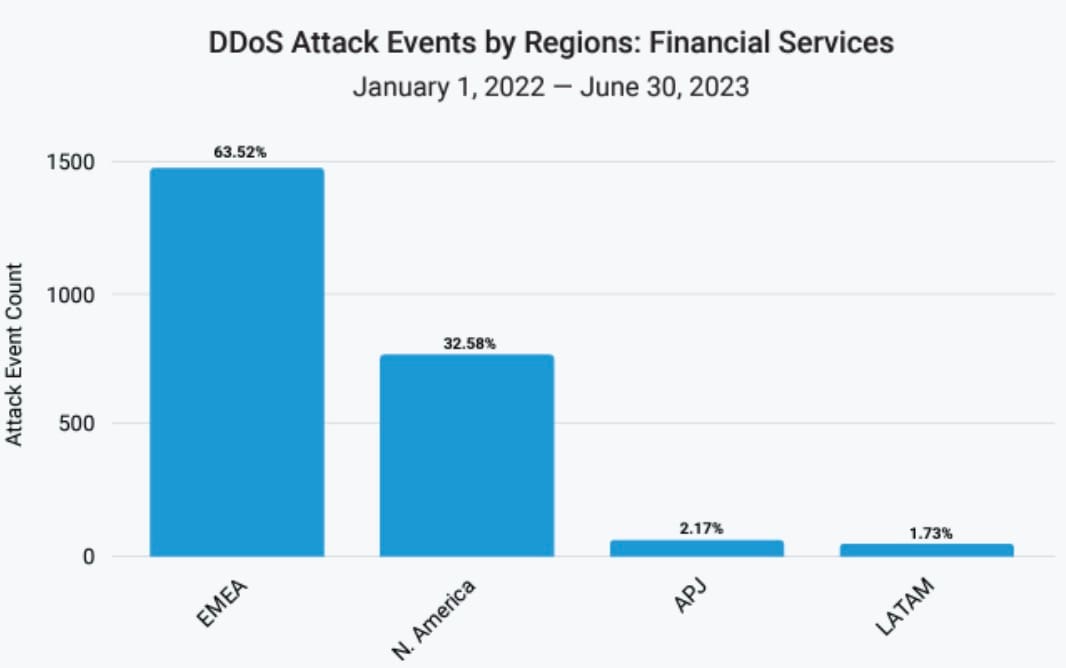 Fig. 4: EMEA has now almost double the number of Layer 3 and Layer 4 DDoS attack events as North America in the financial services vertical. Source: https://www.akamai.com/lp/soti/high-stakes-of-innovation
Fig. 4: EMEA has now almost double the number of Layer 3 and Layer 4 DDoS attack events as North America in the financial services vertical. Source: https://www.akamai.com/lp/soti/high-stakes-of-innovation
Layer 7 DDoS attacks also continue to be a problem for financial applications. Threat actors are making nonstop efforts to elevate their attack operations, networks, and TTPs to evade stronger defenses. Some of the most common characteristics we’ve observed from many large-scale DDoS attacks include:
Highly distributed IP/subnet and country targets
Abundant attack sources, including infected/leased cloud service providers, Tor exit nodes, and anonymous/open proxy nodes
HTTP and DNS query floods
Noncacheable URLs, such as home page, random URLs, search inputs, and login endpoints
IP spoofing by advanced attackers who create botnets behind residential ISPs, mobile carrier networks, or university networks.
Dynamic and adaptive strikes, based on defenders’ responses
The other flavors of DDoS attacks in 2023: long, frequent, sophisticated — and more
It wasn’t just the number of DDoS attacks that increased in 2023, but also the variety of attack types that stood out from previous years. Horizontal DDoS attacks, which are sometimes referred to as “carpet bombing DDoS attacks,” witnessed a marked increase since the last quarter of 2022. Until Q3 of 2022, less than 20% of DDoS attacks observed by Akamai were categorized as horizontal attacks (Figure 5). In the 12-month period between Q4 of 2022 and Q3 of 2023, we consistently observed that nearly 30% of the DDoS attacks were horizontal and multidestination attacks, an increase of nearly 50%.
 Fig. 5: Nearly 30% of DDoS attacks in 2023 were horizontal, or carpet bombing, DDoS attacks. This is an increase of 50% from the previous years. Source: Akamai Prolexic DDoS threat intelligence
Fig. 5: Nearly 30% of DDoS attacks in 2023 were horizontal, or carpet bombing, DDoS attacks. This is an increase of 50% from the previous years. Source: Akamai Prolexic DDoS threat intelligence
Another distinct trend with DDoS attacks in 2023 was the ever-increasing number of vectors employed by cybercriminals when they target a business or an institution. Some of the largest and most sophisticated DDoS attacks defended by Akamai in 2023 had a mix of more than 14 different vectors, clearly intended to achieve resource exhaustion and overwhelm the network security teams of target businesses. In many instances, such complex and multi-vector DDoS attacks intended to serve the additional purpose of being a smokescreen for triple extortion attacks.
Thankfully, the combination of Akamai customers’ proactive defense posture, a comprehensive set of DDoS protection solutions, and a team of highly trained security experts from the global Security Operations Command Center (SOCC) team prevented such attacks from having any impact on those businesses. Figure 6 shows the different vectors utilized by cybercriminals for DDoS attacks in the third quarter of 2023.
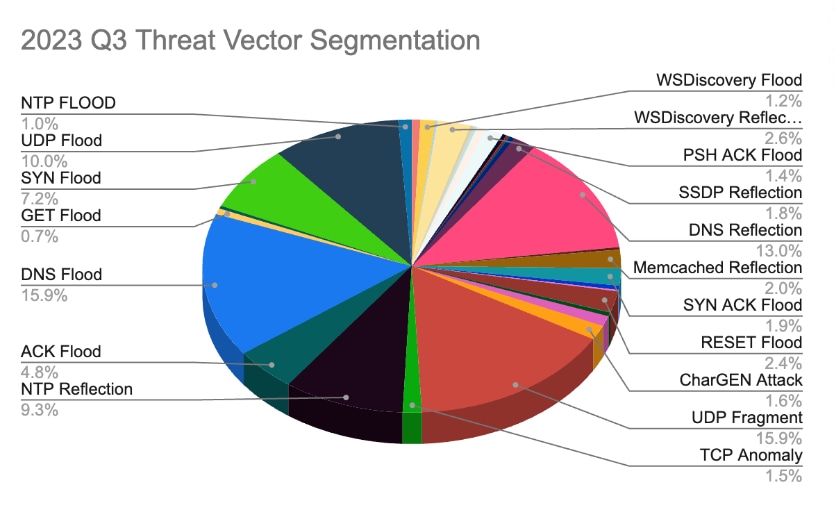 Fig. 6: A distribution of the various vectors used by cybercriminals to launch DDoS attacks in Q3 of 2023. Source: Akamai Prolexic DDoS threat intelligence
Fig. 6: A distribution of the various vectors used by cybercriminals to launch DDoS attacks in Q3 of 2023. Source: Akamai Prolexic DDoS threat intelligence
Cybercriminals have also made a concerted effort to go after what are perceived as “vulnerable targets.” During the reconnaissance or mapping phase of attacks, threat actors know what production services have protections in place and plan accordingly. Small and medium-sized organizations; government institutions; and critical public infrastructures like schools, hospitals, airports, and other transportation and logistics centers were repeatedly attacked with DDoS in 2023. While several major airports in the United States were attacked by the pro-Russian hacktivist group KillNet in 2022, another Russian hacking group called NoName057(16) attacked several Canadian airports, government, and financial institutions in 2023.
Similarly, the notorious hacktivist group Anonymous Sudan attacked six major Indian airports and multiple healthcare institutions in April 2023. This is, of course, by no means an exhaustive list of such DDoS attacks. Cybercriminals continued to leverage DDoS as a relatively inexpensive but effective attack format to cause a nuisance and distraction for the concerned security teams and cause reputational damage for governments and businesses.
Finally, throughout 2023, we observed that there has been a resurgence of longer DDoS attack campaigns. On average, many attacks were sustained campaigns for 20+ minutes, and the number of attacks that continued for more than one hour increased by 50% between 2021 and 2023. This is a remarkable reversal of the previously observed trend of extremely sharp but short attacks that often lasted less than 2 minutes.
Short-burst attacks are very effective if organizations do not have proactive defenses in place and do not allow responders to react quickly. Prolonged attacks burden productivity and the ability of operations to maintain continuity when other threats are detected, and responses are required.
Protecting customers with a world-class DDoS protection platform
It is in this rapidly evolving and increasingly challenging DDoS threat landscape that Akamai provides one of the most comprehensive, flexible, and reliable DDoS protection solutions for customers to defend their digital infrastructure across all layers, ports, and protocols.
New architecture, new scrubbing centers, and global benefits
Over the past 15 months, there have been several significant milestones, additions, and upgrades to the Akamai Prolexic platform, delivering protection and value to customers across all major segments, industries, and geographies worldwide. The series of transformations began with the launch of Prolexic’s fully software-defined architecture in response to changing network trends related to edge computing, 5G, and network virtualization.
With the transition to virtualized software environments, Prolexic removed all dependencies on specialized hardware. This standardization of deployment across the board empowers Akamai to serve evolving customer needs faster, facilitate modular deployments for capacity extension, provide better regional coverage with low-latency links, and improve redundancy on the platform. Additionally, the new architecture accelerates Prolexic’s advanced behavioral learning capabilities to learn from attack signatures, adapt to emerging threat vectors, and proactively build DDoS-resilient postures for customers.
The new Prolexic architecture helped rapidly and massively increase the total number of Prolexic cloud scrubbing centers worldwide. Today, Prolexic has multiple scrubbing centers across 32 global metro areas and a total 20+ Tbps of dedicated defense capacity. The keyword to note here is “dedicated.” Unlike some solutions that piggyback on their content delivery network capacity, thereby offering cybercriminals a single point of defense to overcome,
Prolexic is a purpose-built platform that is integrated with Akamai Connected Cloud but also offers the level of dedicated DDoS security that enterprise customers require. To put Prolexic’s defense capacity in perspective, even the largest known Layer 3 and Layer 4 DDoS attacks don’t make up 10% of the capacity available to Prolexic customers.
During 2023, Akamai Prolexic launched new cloud scrubbing centers in the following locations:
Madrid, Spain
Mexico City, Mexico
Milan, Italy
Rio de Janeiro, Brazil
Zurich, Switzerland
The geographic spread and the local presence of Prolexic scrubbing centers deliver several benefits to customers, including:
Minimizing latency and maximizing network performance
Optimizing operational costs related to network traffic redirection
Enhancing visibility into and control over the region-specific patterns of DDoS attacks
Complete DDoS protection when and where customers need it — on-prem, cloud, or hybrid
In September, Akamai entered into a strategic partnership with Corero, a leading specialist in on-premises DDoS solutions, to extend the Prolexic platform with Prolexic On-Prem (powered by Corero) and Prolexic Hybrid.
Prolexic On-Prem provides always-on, physical or logical, inline, and datapath DDoS protection that natively integrates with edge routers to automatically stop more than 98% of the attacks at the edge of a customer’s network without requiring traffic backhaul. This is ideal for the vast majority of the small and fast attacks and for businesses that require ultra-low latency DDoS protection.
Prolexic Hybrid combines the power, automation, and performance of Prolexic On-Prem with the industry-leading scale and capacity of Prolexic Cloud on-demand to protect customer origins from the largest volumetric DDoS attacks.
Extending Prolexic to go beyond DDoS
In April 2023, Akamai announced the launch of Prolexic Network Cloud Firewall — a fully self-serviceable and user-configurable capability that empowers customers to easily define, deploy, and manage their own access control lists (ACLs) and the rules that they want enforced at the very edge of their network. It’s a firewall in front of all other firewalls.
With Network Cloud Firewall, customers can quickly, centrally, and globally block traffic that they don’t want to hit their networks or certain targets within their networks. Network Cloud Firewall also recommends ACLs for the best proactive defense posture based on Akamai’s threat intelligence data and delivers actionable analytics of existing rules. As a next-generation firewall as a service (FWaaS), Network Cloud Firewall empowers customers to:
Define proactive defenses to block malicious traffic instantly.
Alleviate local infrastructure by moving rules to the edge.
Quickly adapt to network changes via a new user interface.
Three actionable strategies for proactive and effective DDoS protection in 2024
If 2023 was a year in which businesses, government institutions, and critical public infrastructure were relentlessly targeted with highly sophisticated cyberattacks, then it is probably safe to anticipate that cybercriminals will set their goals even higher in 2024. The proliferation of digital devices that can be infected and turned into botnets, the rapid adoption of digital infrastructure in the EMEA and APAC regions, and the ongoing geopolitical tensions in Europe and the Middle East will continue to foster a chaotic environment that plays into the hands of motivated cybercriminals.
In this landscape, Akamai recommends the following three actionable strategies:
Proactively prepare with a DDoS protection posture
Shield your DNS infrastructure
Don’t rely on solutions that are “good enough”
1. Proactively prepare with a DDoS protection posture
The relatively low cost of launching DDoS attacks, particularly with the proliferation of DDoS as a Service, has made them a potent cybercrime weapon in the hands of malicious actors. Although DDoS attacks can’t be prevented, it is 100% possible to protect your digital assets from such attacks by adopting the following steps:
Review all your critical subnets and IP spaces and ensure that you have mitigation controls in place.
Deploy DDoS security controls in an always-on protection posture as a first layer of defense to avoid an emergency integration scenario and to reduce the burden on incident responders.
Proactively designate a crisis response team and ensure your runbooks and incident response plans are up-to-date. Don’t get caught off guard when you are under attack!
Back up your on-prem DDoS protection with a hybrid protection platform that protects against attacks that overload your on-prem appliances.
Extend your security posture beyond basic DDoS protection by setting up proactive security controls through a network cloud firewall.
Finally, utilize the expertise and experience of a global and battle-tested SOCC team to alleviate the pressure from your critical in-house resources. SOCC services complement the automation and capabilities of a robust DDoS platform.
2. Shield your DNS infrastructure
DNS infrastructure has resurfaced as a major target for DDoS attacks. If your DNS goes down, so does your online presence. The attacks may not always have the goal of taking the DNS nameservers down. Instead may just hope to achieve resource exhaustion and deteriorate your global server load balancing performance to a point where legitimate requests suffer.
In some cases, protecting the security and the performance of your DNS infrastructure can be challenging if your setup manages some zones in the cloud and others on-prem. In many such cases, a traditional DNS firewall provides inadequate protection. The most optimal solution is a hybrid platform that empowers you to:
Protect your DNS zones both on-prem and in the cloud from all kinds of attacks, including DNS water torture, DNS flood, and others
Intuitively and easily manage policies and IP allow lists and provide actionable analytics in real time to help you adopt a proactive security posture
Improve DNS performance by using a highly distributed point-of-presence infrastructure to respond to users from the closest location
3. Don’t rely on solutions that are “good enough”
Perhaps most importantly: Don’t assume your existing DDoS and DNS security posture is “good enough” or that your business is not on somebody’s target list. 2023 was the year of unsuspecting and insufficiently prepared victims in this area, many of whom had underestimated how DDoS threats had evolved and had overestimated what their existing security could manage.
Be cautious of the true cost of “freemium” solutions that lure you into an entry-level service with a free or relatively inexpensive solution but carefully hide any effective levels of service behind a paywall. It might be tempting to believe that you can engage higher levels of protection as required, but when you are under attack, the last thing on your mind would be signing order fulfillment forms.
Finally, do not forget to stress-test your defenses both from a technological solutions perspective as well as from a best practices perspective. This includes incident runbooks, processes, documentation, and so forth that can be the difference between questionable adequacy of preparedness and world-class cybersecurity.
If 2023 has taught businesses and institutions one lesson about DDoS, then it is that the previous year’s protections were no longer sufficient to handle this year’s attacks. You don’t want to be in that same situation in 2024.





