How Akamai Protects Customers from HTTP/2 Rapid Reset DDoS Attacks

Executive summary
HTTP/2 is a web protocol that is used by the vast majority of today’s web servers and applications. However, a recently identified zero-day vulnerability — HTTP/2 Rapid Reset — can be exploited by cybercriminals to launch large-scale Layer 7 distributed denial-of-service (DDoS) attacks.
Akamai Connected Cloud and DDoS protection solutions provide highly effective DDoS defense to customers without requiring additional steps. This blog post provides a more detailed explanation of the HTTP/2 protocol, the Rapid Reset vulnerability, and how Akamai customers are maintaining a strong defense posture against DDoS attacks.
Discovering a zero-day vulnerability
Over the past several weeks, Akamai has collaborated with key industry stakeholders and partners to develop a response to the HTTP/2 Rapid Reset zero-day vulnerability (CVE-2023-44487) that cybercriminals have exploited to launch massive Layer 7 DDoS attacks.
After an information embargo period designed to help businesses and institutions adopt the required cyberdefenses to protect their internet-facing assets from these DDoS attacks, information about the zero-day vulnerability was publicly announced by the United States Cybersecurity & Infrastructure Security Agency (CISA) on October 10, 2023.
What are HTTP/2 DDoS attacks?
HTTP/2 is the second major version of the Hypertext Transfer Protocol (HTTP), the protocol that delivers internet websites and API services. It was designed to improve the performance of websites and web applications, primarily by reducing latency and enhancing the efficiency of data transfer.
In the previous versions, HTTP/1 and HTTP/1.1, a web server sequentially processed a single request and response ( Figure 1).
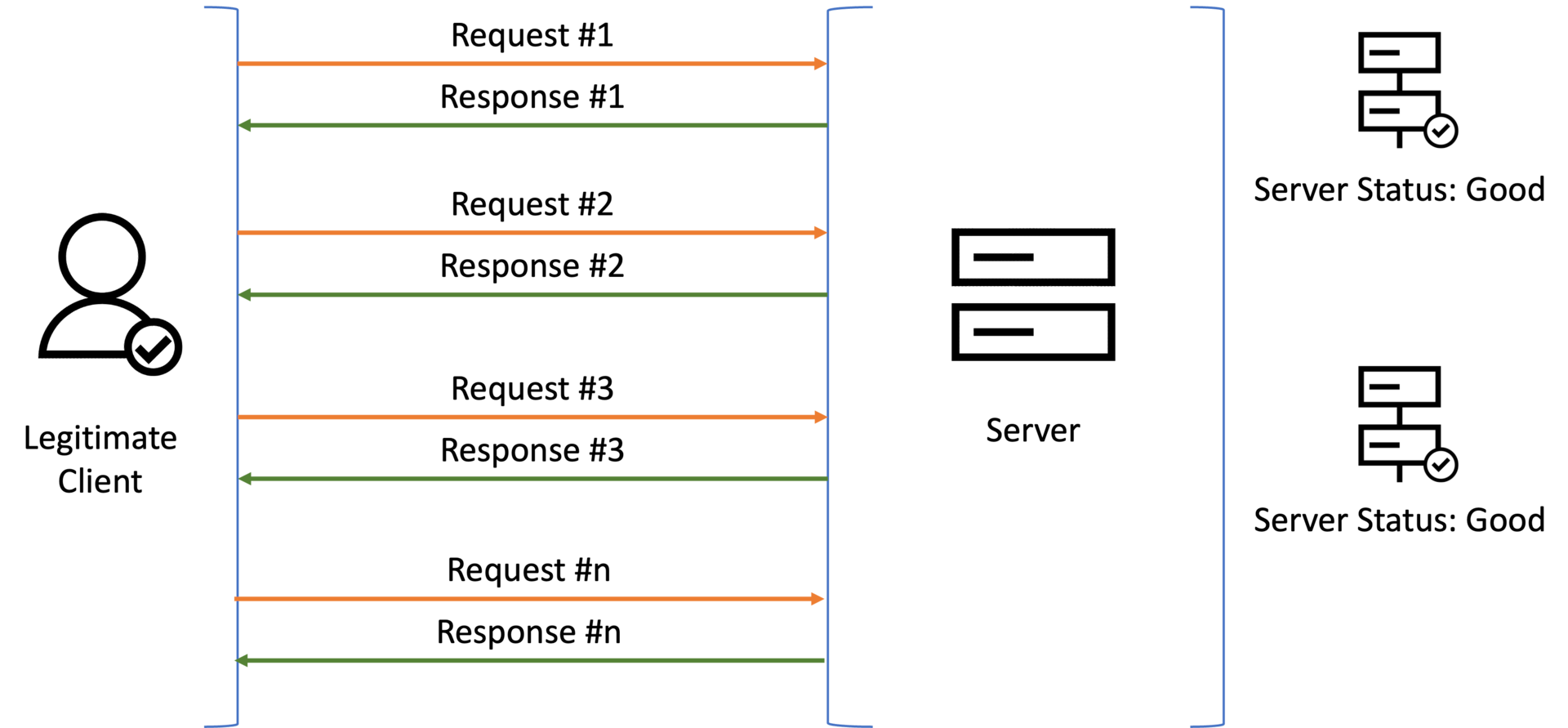 Fig. 1: The standard client–server interaction in HTTP/1.1 protocol. HTTP/1.1 allowed only one request over a single TCP connection
Fig. 1: The standard client–server interaction in HTTP/1.1 protocol. HTTP/1.1 allowed only one request over a single TCP connection
With HTTP/2, a web server can theoretically process up to 100 simultaneous requests over a single TCP connection (Figure 2). This capability is called “stream multiplexing” and helps load websites or exchange data in a significantly faster and more efficient manner.
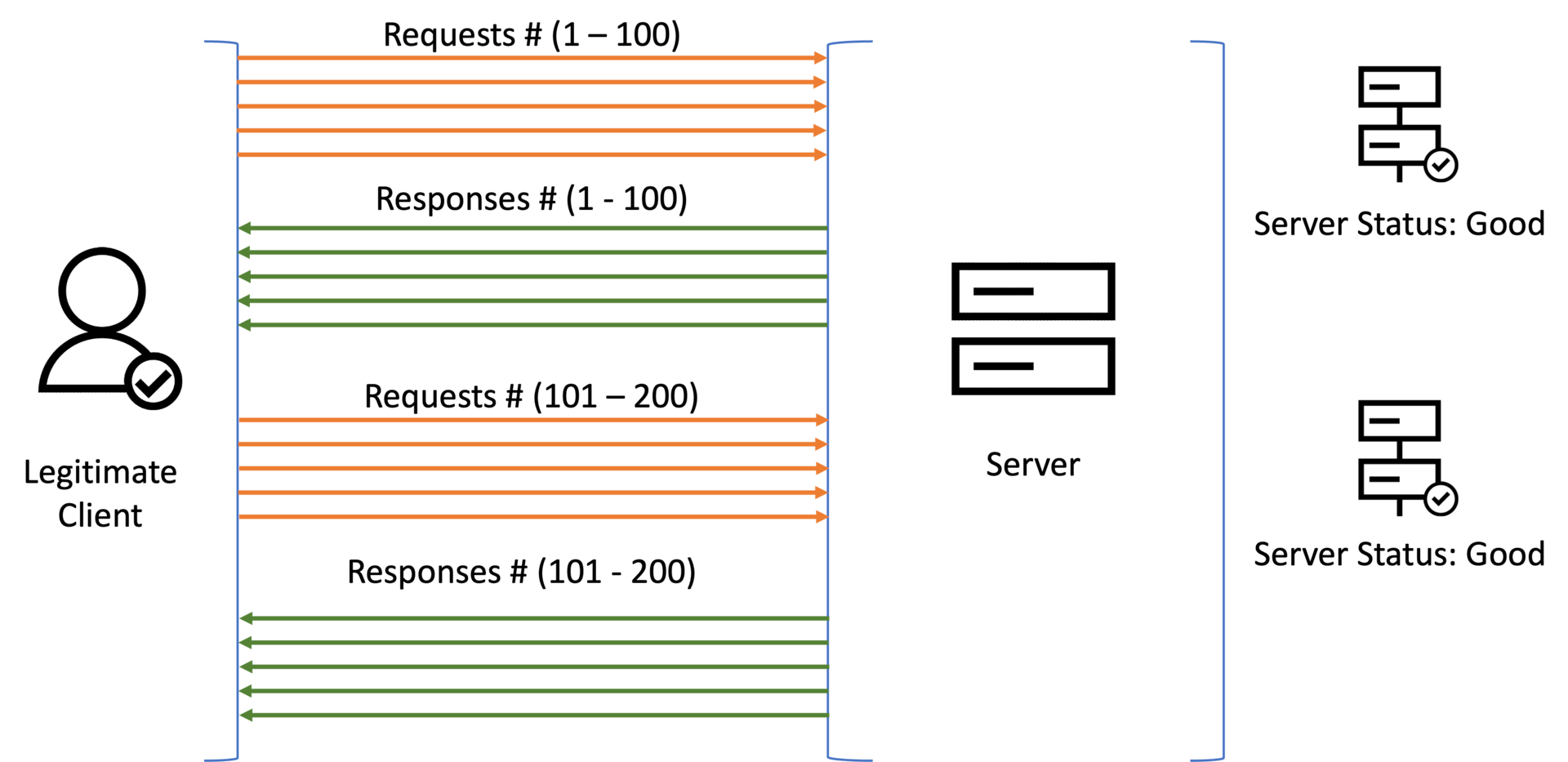 Fig. 2: The more efficient stream multiplexing interaction between a legitimate client and a server in HTTP/2 protocol
Fig. 2: The more efficient stream multiplexing interaction between a legitimate client and a server in HTTP/2 protocol
HTTP/2 offers numerous benefits, but cybercriminals can also exploit this protocol to launch large-scale DDoS attacks. While the previous protocols are also vulnerable to Layer 7 DDoS attacks, the unique structure of HTTP/2, which we examine in the next section, enables attackers to amplify the scale of their attacks.
DDoS attacks overwhelm a target website or service with a massive amount of traffic, often from a network of compromised computers, IoT devices, or botnets. The goal is to disrupt the target's availability and make it inaccessible to legitimate users.
A deeper look at how HTTP can be vulnerable to DDoS attacks
Layer 7 DDoS floods. HTTP/2 is more efficient than HTTP/1.1 in multiplexing multiple requests and responses over a single TCP connection, which reduces the overhead of setting up and tearing down TCP sessions. However, it can also make Layer 7 DDoS attacks more resource-intensive because attackers can generate a large number of requests on a single TCP session. This can consume server resources more quickly, leading to performance degradation.
Layer 7 HTTP Rapid Reset DDoS attacks. The ability of HTTP/2 to use multiplexing to process up to 100 active streams over a single TCP connection becomes a highly potent vulnerability when attackers launch a sequence of stream requests, immediately followed by a reset for that stream. This would trigger request logic in the web application server, but since the stream was immediately canceled, the intended target would continue to process all previously initiated streams, which can ultimately result in hundreds of millions of requests hitting a web server per second, thereby completely overwhelming the server (Figure 3).
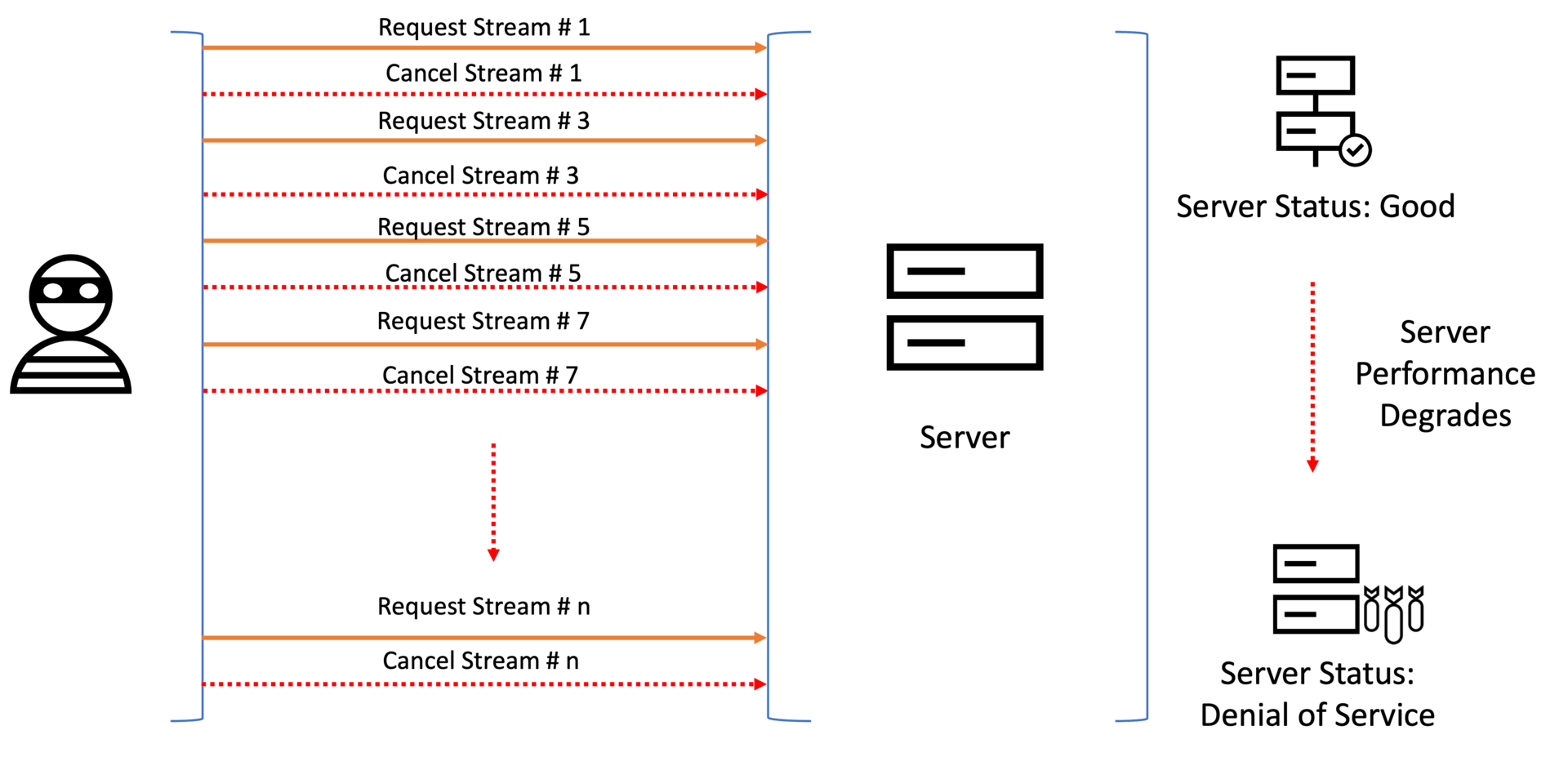 Fig. 3: How an attacker uses multiple streams of requests and resets in HTTP/2 protocol to launch a DDoS attack on a web server; as the attack proceeds, the server performance degrades to denial of service
Fig. 3: How an attacker uses multiple streams of requests and resets in HTTP/2 protocol to launch a DDoS attack on a web server; as the attack proceeds, the server performance degrades to denial of service
Attacking Layer 7 via large pools of IP distribution. This also increases the likelihood of resource exhaustion for HTTP services that rely on other networking components like global traffic management, local traffic management, or any device downstack that manages TCP session tables. When attackers leverage large networks of infected machines, source IP counts can be in the millions (e.g., the Conficker and Mariposa botnets).
Slowloris attacks. Slowloris is a type of HTTP DDoS attack that specifically targets web and API services. Attackers open multiple connections to the server and send HTTP requests just below the TCP connection window, keeping the server busy. This can tie up server resources, TCP session tables, and prevent legitimate users from establishing connections. HTTP2 is not immune to Slowloris attacks.
Layer 7 amplification attacks. Attackers can use HTTP to amplify their attacks by sending small requests that generate large responses. For example, a small header request could trigger a server to send a much larger response, potentially consuming more bandwidth and server resources. Middlebox Reflection is an example of an HTTP amplification attack vector.
An example (with pizza!)
To understand the HTTP/2 Rapid Reset vulnerability with a simple example in layman’s language, imagine the following scenario: You could previously order only a single pizza with one phone call to your favorite pizza delivery service (read: HTTP/1.1). Therefore, if you wanted 20 pizzas for a weekend party, you would have to place 20 separate calls, one after another. But with HTTP/2, you can now order up to 20 pizzas with a single call. Theoretically, this improves the efficiency of your efforts.
However, if someone wanted to play a prank on the pizza delivery service (read: DDoS attack), they could call the service, place an order, and then immediately change their order while still on the same call. It is still a single call, but now the kitchen receiving the order is overwhelmed by simultaneously taking and canceling large pizza orders. If a whole group of pranksters (read: cybercriminals or a botnet) joined in, the whole pizza delivery service would come to a grinding halt.
Akamai offers seamless DDoS protection
HTTP/2 Rapid Reset DDoS attacks, while novel in their nature, happen essentially at the protocol level and are mitigated by Akamai similarly to any other layer 7 DDoS attack. Over the course of September 2023, we refined our edge delivery software to better detect and manage such attacks, including limiting the streams available to abusive HTTP/2 clients.
Utilizing Akamai security products and capabilities like Layer 7 HTTP rate controls, caching, web application firewall rules, and IP blocking and/or geoblocking via Akamai App & API Protector is a proven strategy. Customers on Akamai Connected Cloud and utilizing Akamai’s DDoS protection solutions do not have to take any additional steps.
However, with the emergence of new threats, we encourage customers to work with their Akamai security team and update their configurations, including rate controls, to ensure they are mitigating Layer 7 DDoS attacks tuned to their organization’s traffic profile.
Additional guidance for HTTP/2 DDoS attack mitigation
Immediately review and implement Cybersecurity and Infrastructure Security Agency (CISA) recommendations.
If an existing Akamai CDN customer does not have rate controls or other security products in “deny mode,” Akamai Connected Cloud will limit clients to 100 simultaneous requests per TCP connection, as per the HTTP/2 specification.
If an existing Akamai CDN customer needs protection against Layer 7 DDoS attacks, they are encouraged to add App & API Protector to improve their Layer 7 DDoS protections.
Akamai Prolexic customers should adopt vendor patches or guidance as soon as they become available. In the meantime, or if you are under HTTP/2 Rapid Reset DDoS attack, and unable to immediately disable HTTP2, utilize the Prolexic Network Cloud Firewall to effectively deny traffic to IP addresses hosting these services, typically reserved on TCP:443 ports. This will include “ALL” HTTPS traffic to that host.
Customers who do not have Akamai DDoS protection, and have their origin infrastructure or other services exposed on the internet, should update their vendors’ software, apply vendor mitigations, or disable HTTP/2 until a fix can be applied.
Proactively pull together a crisis response team and ensure runbooks and incident response plans are up-to-date.
Do you have a runbook to deal with catastrophic events?
Are the contacts within the playbooks updated? (A playbook that references outdated tech assets or people who have long left the company isn’t going to help.)
Under attack?
If you are currently under DDoS attack or threat of extortion, please reach out for 24/7 emergency DDoS protection.
Learn more
Want to learn more about the evolution and growing threat of DDoS attacks?




