DDoS Attacks in 2022: Targeting Everything Online, All at Once

The year 2022 was marked by significant changes in many areas of cybersecurity. Amid the turmoil, there was a noticeable shift in distributed denial-of-service (DDoS) attacks targeting and adversarial behavior. Perhaps the most significant lesson learned from last year is that DDoS attackers are targeting everything online, sometimes all at once.
Two prominent themes emerged in 2022 — the rise of horizontal DDoS attacks and the increased targeting of customer assets that were previously deemed unattractive targets to adversaries — but we do not believe that the industry provides sufficient end-to-end analyses of DDoS attack techniques, tactics, and procedures (TTPs).
Lack of detailed analyses for DDoS attack TTPs
Although there’s ample data on the number of blocked attacks, the type of attack vectors that were generated, newly discovered attack vectors, and how they were compromised or leveraged in the wild, there is still no comprehensive analysis of the attacked destinations and the techniques surrounding those behaviors.
Attack TTPs should cover essential details, including the targeted assets and their function, as well as the techniques utilized by adversaries to orchestrate these attacks. Although we receive information on attack duration, size, and frequency, there is little focus on the techniques used to attack the destination. Understanding the TTPs used to attack the destination can help network operators and security experts better defend against such attacks.
The prominent DDoS themes of 2022
Let’s explore both of the prominent themes — the rise of horizontal DDoS attacks and the increased targeting of customer assets — in greater depth.
The rise of horizontal attacks
Traditional DDoS attacks typically involve targeting a highly visible asset, such as a company's main website, followed by launching an attack using one or more methods (also known as vectors) to overpower the infrastructure that supports the target.
The success or failure of the attack depends on its size, the vector, and the appropriateness of the detection and mitigation measures implemented by the asset to safeguard against abuse.
Horizontal attacks refer to simultaneous DDoS attacks aimed at multiple, unrelated targets (which is why they’re sometimes called carpet bomb attacks). Instead of prioritizing a single high-value target, the attacker selects multiple targets in order to distribute the attack, making it more challenging for security teams to mitigate and maximizing the possibility of widespread disruption.
For example, adversaries might attack all the IP addresses associated with a particular organization, or they might conduct more in-depth reconnaissance to identify a large number of active services or systems and attack them all at the same time. The record-breaking attack that we wrote about in September 2022, which hit 1813 IP addresses distributed across six physical data centers, is a perfect illustration of this threat.
Despite having existed since the inception of Akamai Prolexic 20 years ago, horizontal attacks remain a relevant threat due to their increasing popularity and complexity. In recent months, we’ve observed a surge in horizontal attacks (Figure 1). Although Prolexic had no issues from a mitigation standpoint, we’ve made improvements to our detection tools to enhance resilience against horizontal attacks and stay ahead of threat actors.
 Fig. 1: The recent surge in horizontal attacks by quarter
Fig. 1: The recent surge in horizontal attacks by quarter
The increased targeting of customer assets
Not all internet-facing assets are equivalent. Every company has its flashy assets, such as the home page, customer portals, API endpoints, or newly implemented SD-WAN. However, companies are equally dependent on less conspicuous assets such as back-end interfaces, employee portals, SSH endpoints, FTPs, and so forth.
When discussing attack trends, we often overlook the target of the attack. However, our colleagues who are responsible for implementing proactive defenses against real-world attacks require this knowledge to ensure they develop the most effective signatures and defensive access-control list postures. This need led to the development of Akamai Prolexic network cloud firewall, which utilizes our traffic profiling views.
By analyzing the flow of data traversing our network, we can gain valuable insight into an IP's activities prior to an attack, which we refer to internally as its "IP day job." Typical web assets work tirelessly on ports tcp:80, tcp:443, or occasionally tcp:8080, but we should not overlook other critical services such as IPSEC/VPN on port 4500, SFTP on port 22, and DNS on port 53.
We ran a few filters on this data to ensure that:
They saw levels of traffic that indicated ongoing use (i.e., the IP had a day job)
Most of that traffic was to a dominant port. (i.e., it didn’t have too many day jobs and/or wasn’t receiving traffic from ephemeral ports)
 Fig. 2: Attacks by most used port on IP
Fig. 2: Attacks by most used port on IP
The IPs attacked in 2022 had more than 187 different day jobs. To demonstrate the diversity of targeted assets' activities, we created a scatterplot shown in Figure 2. TCP:443 emerged as the most commonly used port, followed closely by customized ports anonymized for customer protection.
Deeper understanding, better defense
One approach we can take to bolster our defenses is to examine the targets and determine the most common attack vector used against them.
Figure 3 shows the most common attack vectors used against some ports of interest.
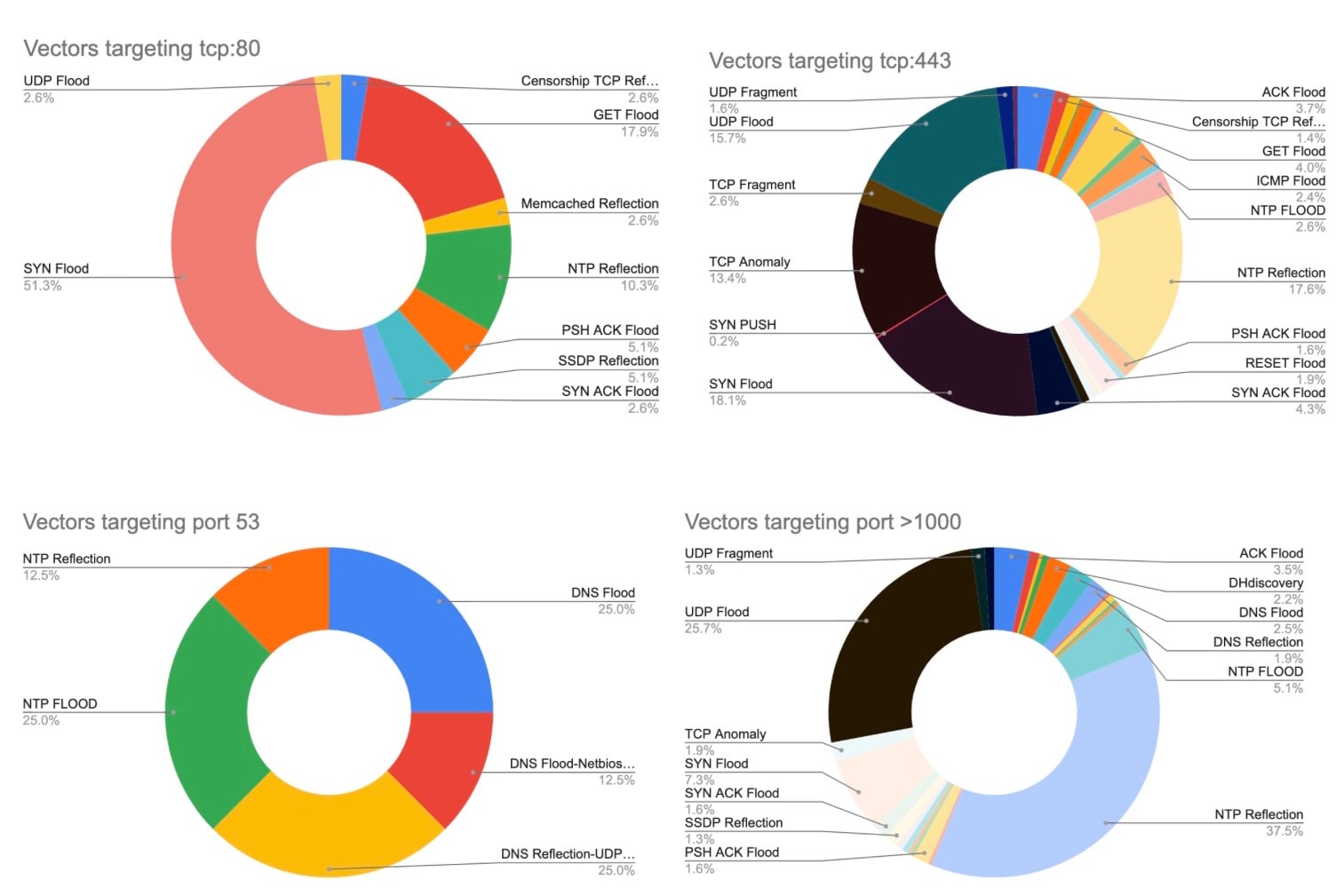 Fig. 3: The most common attack vectors targeting tcp:80, tcp:443, port 53, and port >1000
Fig. 3: The most common attack vectors targeting tcp:80, tcp:443, port 53, and port >1000
By understanding the day job of the targeted IPs and the methods used to attack them, network operators and security experts can better defend against such attacks. Although not all DDoS techniques can be thwarted through IP hygiene and protocol misuse abuse strategies, using these tactics in conjunction with other defensive measures is like peeling back the layers of an onion to build a strong defense.
Blocking DDoS attacks
Proactive mitigations enable us to achieve zero-second service-level agreements (SLAs) and maintain high-quality and consistent mitigation. While reactive mitigations are necessary, they should not come at the expense of user impact or service degradation. Akamai Prolexic has a proven track record of blocking a wide majority of DDoS attacks within zero seconds while maintaining consistency in mitigation.
How to minimize DDoS risk: 5 steps to take
As threats become more sophisticated, the deployment of robust DDoS controls and resiliency plans is essential for minimizing the risk of downtime and disruption. Organizations are encouraged to take the following steps to harden their security posture.
Review critical subnets and IP spaces, and ensure that they have mitigation controls in place.
Review security postures on wider network spaces that share infrastructure and can cause collateral damage, if attacked.
Deploy DDoS security controls in an always-on mitigation posture as a first layer of defense to avoid an emergency integration scenario and to reduce the burden on incident responders. If you don’t have a trusted and proven cloud-based provider, get one now.
Proactively pull together a crisis response team and ensure runbooks and incident response plans are up-to-date:
Do you have a runbook to deal with catastrophic events?
Are the contacts within the playbooks updated? An up-to-date runbook could be the difference between maintaining business continuity or suffering a potentially disastrous service disruption.
Protect your process by evaluating what the bulk removal of alerts would look like in your current security orchestration, automation, and response tools; security information and event management tools; or other incident response tools. Understand how to easily group, filter, acknowledge, and view alerts during a widespread attack.
Learn more
For additional information on the steps you can take to protect your organization, please visit the following Cybersecurity and Infrastructure Security Agency resources:
Understanding and Mitigating Russian State-Sponsored Cyber Threats to U.S. Critical Infrastructure
Shields Up (steps to reduce cybersecurity risk)


