Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Ryuk ransomware is a type of malware that encrypts files on an organization’s computers and servers, making them inaccessible until a ransom payment — usually in bitcoin — is paid. Ryuk ransomware specifically targets Microsoft Windows operating systems. Unlike most ransomware families, Ryuk also attempts to encrypt system files that would make the host system crash or become unstable.
Ryuk is known for targeting large organizations and institutions that have the financial ability to pay larger ransom amounts. This type of ransomware attack is known as “big game hunting” (BGH). When targeting a company, rather than casting a wide net, Ryuk attackers perform extensive surveillance and use manual efforts to infect their targets.
Ryuk operates as a well-known ransomware as a service (RaaS) program, where developers of the malware offer it to other hackers for use in attacks in exchange for a percentage of the ransom payments.
A timeline of Ryuk ransomware
Ryuk ransomware was first observed in 2018. Its origin can be traced back to Hermes, an earlier form of ransomware that has been widely distributed in the cybercrime world.
Victims of Ryuk ransomware attacks include governments, school systems, IT companies, and public utilities. Ryuk has attacked many healthcare systems, including Universal Health Services (UHS). Other high-profile attacks include Tribune newspaper publishing, a public utility in Florida, and the French IT services firm Sopra Steria.
In 2021, Ryuk ransomware developed a new variant with wormlike capabilities that allow it to spread between computers and systems without needing human intervention. This development makes the attack sequences faster and allows attackers to create more system-wide disruption.
The primary group behind Ryuk ransomware attacks is believed to be Wizard Spider, a Russian cybercriminal collective.
How Ryuk ransomware is spread
The Ryuk ransomware threat uses a variety of tactics, techniques, and procedures (TTPs) to take control of computer networks. Distribution methods include:
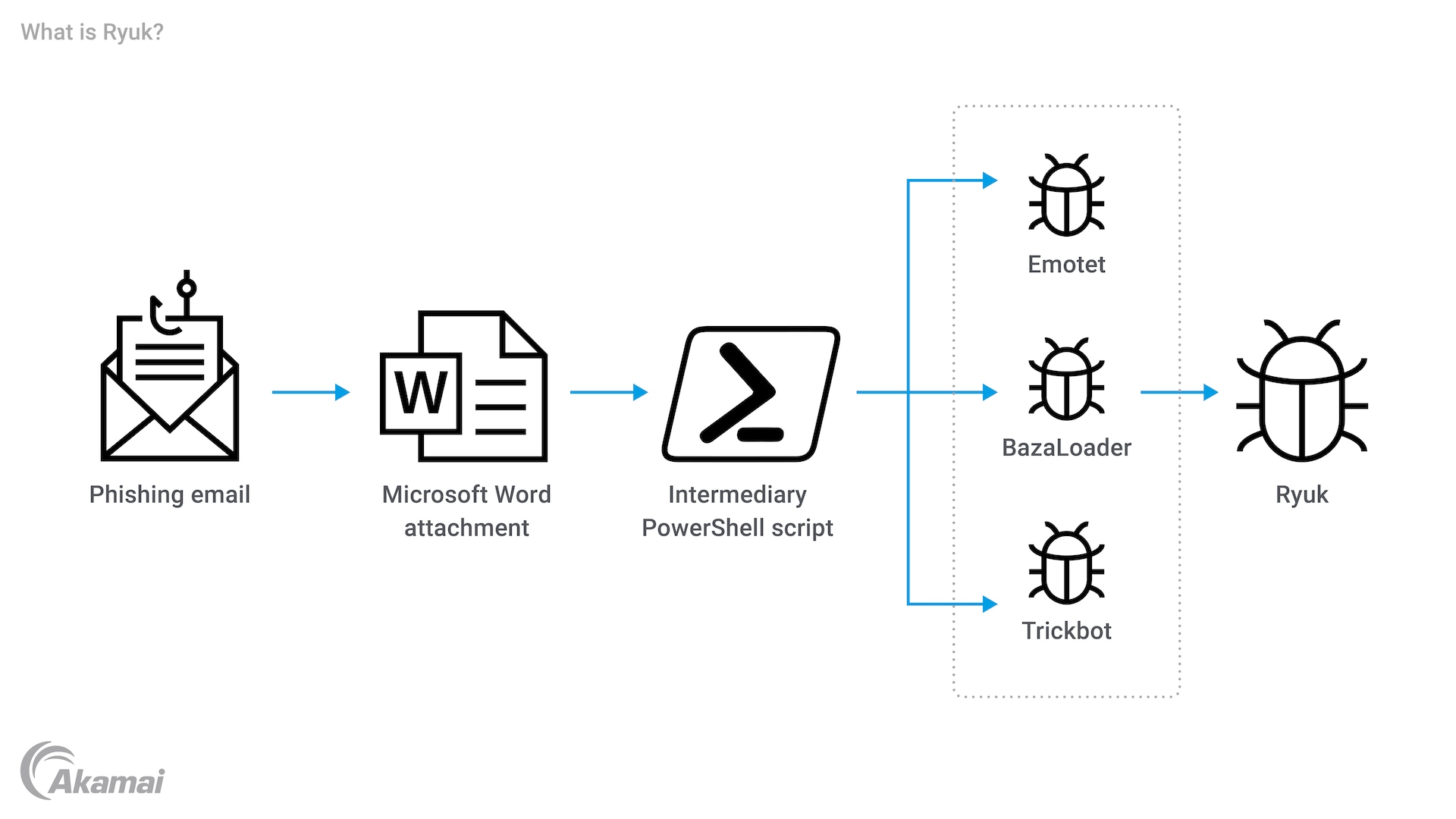
- Phishing emails and spam emails that install malware after users click on a malicious link or open a malicious attachment.
- Vulnerabilities in Remote Desktop Protocol (RDP) applications that allow attackers to gain access to IT environments.
- Pre-existing malware and Trojans like TrickBot and Emotet, which exploit system vulnerabilities to covertly deploy the ransomware’s payload.
Anatomy of a Ryuk ransomware attack
After gaining access to an IT environment, Ryuk ransomware performs a number of tasks to maximize the damage of its eventual attack.
- Lateral movement: Initially, Ryuk only installs malware that lets the ransomware operators take command and control of machines that will be used to deploy ransomware across network drives at a later date. Once a system is infected, threat actors move laterally within the network to infect more devices without triggering security alerts. TrickBot scripts escalate privileges by collecting passwords that enable access to higher levels of the system.
- Preventing recovery: Ryuk disables backups and shadow copies to prevent victims from restoring files easily.
- Reconnaissance: Ryuk explores the IT environment, collecting admin credentials and identifying critical assets to encrypt.
- Encryption: Ryuk ransomware uses a combination of RSA and AES-256 encryption algorithms to lock files and generate encryption keys.
- Ransom demands: Ransom notes are typically left as text files such as RyukReadMe.txt, which instruct victims how to contact the attackers, pay the ransom, and receive a decryption key.
Preventing and detecting Ryuk ransomware
Preventing Ryuk ransomware requires a strategy that involves multiple layers of cybersecurity defenses.
- Backups: Backing up important data and keeping a copy in offline data storage may allow an organization to recover quickly from a Ryuk attack without having to pay a ransom.
- Cybersecurity controls: Employing robust anti-malware, antivirus solutions, anti-ransomware, firewalls, VPNs for remote access, application allowlisting, and other strategies are part of a comprehensive approach to detecting and blocking suspicious activity.
- Updates: Updating systems and regularly patching software minimizes the attackers’ ability to exploit vulnerabilities.
- Multi-factor authentication (MFA): Requiring users to provide two or more forms of identification when requesting access to IT resources helps to prevent unauthorized access to IT environments.
- Microsegmentation: Segmenting networks and individual IT assets protects sensitive data and prevents the kind of lateral movement that ransomware and other cyberattacks rely on.
- Security training: Educating users on the risks of ransomware, best practices for cybersecurity, and how to spot and avoid phishing emails can help to avoid many attacks that rely on human error.
- Endpoint protection: Organizations should also implement endpoint protection tools that monitor end-user devices to detect malicious activity.
- Continuous monitoring: By constantly monitoring network activity in real time with information from threat intelligence feeds, IT teams can quickly identify and mitigate ransomware and malware attacks.
Responding to a Ryuk ransomware attack
Remediation of a Ryuk infection requires swift action and execution of a well-crafted incident response plan.
- Isolating the infected systems from the network prevents the ransomware from spreading further, and disconnecting them from the internet prevents attackers from communicating with the malware.
- Cleaning all affected drives and removing the malware’s executables and payloads with ransomware removal tools is critical to preventing reinfection.
- Restoring encrypted files must be done from backups, since decryption without the private key is generally not feasible with Ryuk.
- Engaging cybersecurity professionals can help to speed recovery.
- Notifying law enforcement agencies like the FBI can help authorities combat ransomware attacks.
FAQs
Indicators of a Ryuk infection include the presence of the RyukReadMe.txt ransom note, unusual .exe and .dll file executions, and the presence of file extensions like .ryk or .rcrypted. Increased activity in PowerShell and command and control (C2) server traffic are also red flags, alongside with the disabling of Windows shadow copies to prevent file restoration.
Ryuk is the name of a character in a popular Japanese manga comic book and anime cartoon series. The character Ryuk is a death god who enables targeted killings.