Anti-ransomware is a category of strategies, technologies, and best practices that help organizations prevent, detect, mitigate, and remediate ransomware attacks.
Anti-ransomware refers to cybersecurity solutions designed to detect, prevent, and respond to ransomware attacks. Anti-ransomware measures include various technologies as well as best practices for avoiding ransomware infections and responding to ransomware attacks.
What is ransomware?
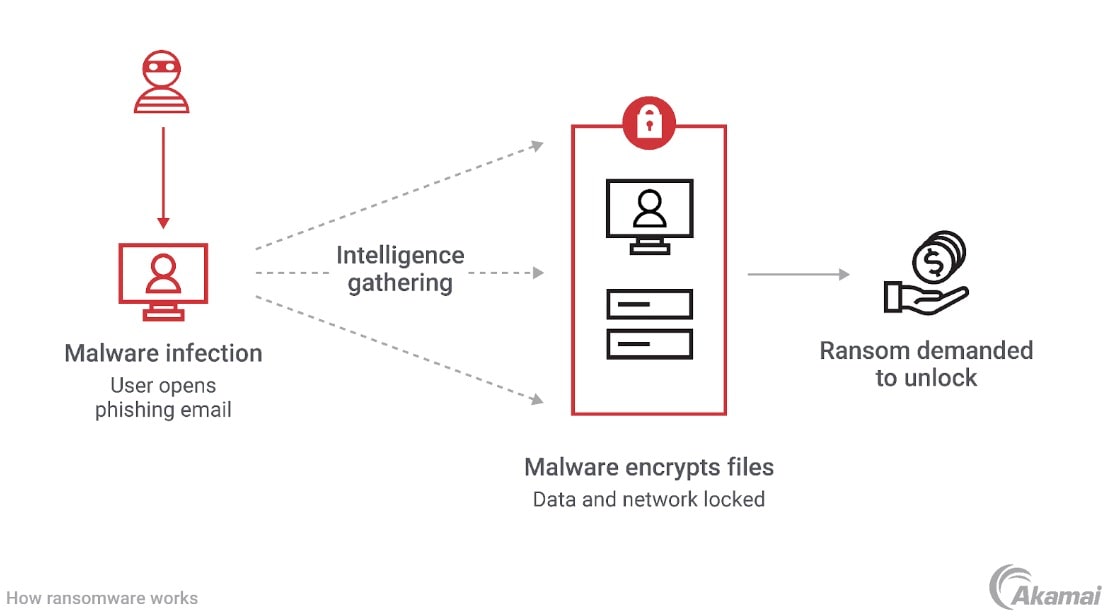
Ransomware is a type of malware, or malicious software, that encrypts files on computers and servers, allowing cybercriminals to demand a ransom in exchange for decryption keys. Ransomware is usually deployed by organized groups of attackers who target vulnerable systems, unprotected endpoints, and poorly secured networks.
Ransomware can be distributed in a variety of ways. Hackers may use phishing attacks to trick users into downloading ransomware, or they may gain access to an IT environment by exploiting vulnerabilities in software or systems.
Once a device is infected, the ransomware encrypts files and presents users with a ransom demand. In addition to holding files hostage, cybercriminals may extort companies by exfiltrating sensitive data and threatening to make it public unless a ransom is paid.
Ransomware can infect a wide range of computers and machines, including laptops and PCs, mobile devices running iOS or Android, and network devices running Windows, Mac, and Linux operating systems.
The importance of anti-ransomware solutions
Ransomware attacks can be devastating. Losses in data, productivity, business opportunities, and public trust can cost an organization millions of dollars. For businesses that choose to pay a ransom — which is discouraged by federal cybersecurity and law enforcement agencies — the cost in actual dollars may exceed tens of millions of dollars. Anti-ransomware strategies and technology help businesses to avoid these direct and indirect costs.
How do anti-ransomware technologies work?
Anti-ransomware tools provide multiple layers of protection and focus on ransomware prevention, detection, response, and recovery.
Prevention
- Email filtering and scanning tools monitor email for malicious links and attachments that are commonly used in ransomware attacks.
- Ad blocking and web filtering tools prevent users from accessing malicious websites that are known to distribute ransomware. These solutions may also prevent harmful scripts from running.
- Microsegmentation tools can prevent malicious lateral movement that may occur before detection, which ransomware relies on to escalate privileges and find high-value assets.
Detection
- Anti-ransomware security products include antivirus solutions, firewalls, threat protection technologies, malware protection solutions, DNS filters, VPNs for remote access points, intrusion prevention systems (IPS), multi-factor authentication, and other forms of anti-ransomware protection from trusted providers.
- Threat intelligence feeds provide security solutions with information about known and emerging threats from intelligence gathered on the dark web. Threat intelligence solutions may also use advanced algorithms to predict and identify potential ransomware threats.
- Real-time monitoring solutions continuously scan traffic for signs of ransomware code or suspicious behavior on devices and networks.
- Anomaly detection solutions use artificial intelligence (AI) and machine learning (ML) capabilities to analyze vast datasets from previous malware attacks and identify potential ransomware activities based on unusual patterns and behavior. AI and ML solutions have been successful at blocking ransomware even when the specific code has never been encountered before.
Response
- Incident response technology includes tools for automatically quarantining infected files and processes, and alerting security teams to the detection of potential ransomware.
Recovery
- Decryption tools offered by anti-ransomware providers may help unlock encrypted files affected by certain types of ransomware.
- Removal tools help IT teams to identify the ransomware variant and remove malicious code. Removal of the ransomware virus is essential to prevent reinfection of files and backups.
- Recovery solutions enable IT teams to restore data from backups quickly after an attack.
What are anti-ransomware best practices?
The best anti-ransomware strategy is a multilayered approach to security that includes practices for ransomware prevention, mitigation, and remediation.
- Zero Trust architecture: To improve security posture, organizations may adopt a Zero Trust security model that assumes everything inside or outside the network may be a threat. This approach requires users, devices, and applications to be authenticated and verified on every request for access.
- Regular backups: IT teams must regularly back up data and systems in on-premises, cloud, and edge environments. Keeping a backup that is isolated from the network helps to protect backups from ransomware infection.
- Incident response plan: A well-planned incident response strategy can help organizations react swiftly to a ransomware infection. By quickly identifying the breach, containing the ransomware virus, eradicating the infection, and recovering data, organizations can minimize downtime and damage.
- Zero Trust security model: To improve security posture, organizations may adopt a Zero Trust security model that assumes everything inside or outside the network may be a threat. This approach requires users, devices, and applications to be authenticated and verified on every request for access. Zero Trust architecture grants only minimal privileges rather than broad access, and it continuously monitors all network traffic for any signs of cyberattack like ransomware.
- Vulnerability scanning: Regularly scanning software and hardware for known vulnerabilities can help IT teams to address issues before they can be exploited by attackers.
- Regular patches and updates: IT and security teams must regularly update operating systems and firmware to close security gaps caused by vulnerabilities in software and hardware.
- Security awareness training: Since human error often plays a significant role allowing ransomware to spread, educating employees about phishing attacks and other ways that ransomware spreads is one of the most important anti-ransomware measure
Frequently Asked Questions (FAQ)
Why customers choose Akamai
Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.