Ransomware Devastating MySQL Servers
Executive Summary
- PLEASE_READ_ME is an active ransomware campaign targeting MySQL database servers and dates back to at least as early as January 2020.
- The attack chain is extremely simple and exploits weak credentials on internet-facing MySQL servers. There are close to 5M internet-facing MySQL servers worldwide.
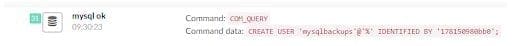
- The attackers leave a backdoor user on the database for persistence, allowing them to re-access the network.
Guardicore Labs have witnessed two variants of the campaign, detailed in this post. - 250,000 databases are offered for sale in the attackers’ dashboard, from 83,000 successfully-breached victims.
- Monetization of the campaign has evolved into a double extortion attempt – publishing and offering data for sale to pressure victims into paying ransom.
- Indicators of Compromise are available at Guardicore Labs campaigns repository.

An Evolving Ransomware Campaign
The first attack on Guardicore Global Sensors Network (GGSN) was captured on January 24, 2020. Since then, a total of 92 attacks have been reported by our sensors, showing a sharp rise in their number since October. The attacks originate from 11 different IP addresses, most of which are from Ireland and the UK. What drove us to closely monitor this threat is its use of double extortion, where stolen data is published and offered for sale as a means to pressure victims into paying the ransom.
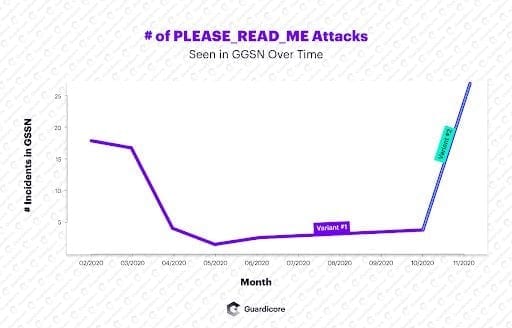
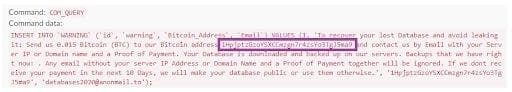
Guardicore Labs observed two different variants during the lifetime of this campaign. In the first, which lasted from January till the end of November, the attackers left a ransom note with their wallet address, the amount of Bitcoin to pay and an email address for technical support. 10 days were given for victims to perform payment. Since Bitcoin wallets were specified explicitly in ransom notes, we could explore the wallets and the amount of BTC transferred to each of them. We found that a total of 1.2867640900000001 BTC had been transferred to these wallets, equivalent to 24,906 USD. Guardicore Sensors captured 63 attacks of this type, coming from 4 different IP addresses.
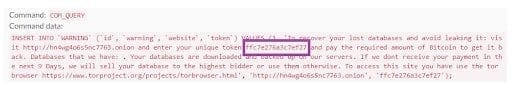
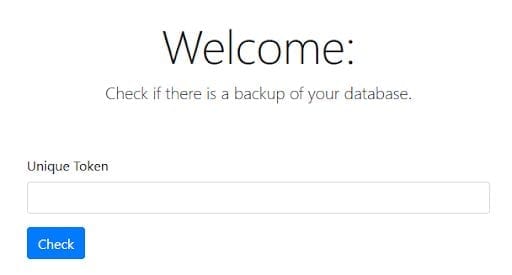
The second phase started on October 3rd and lasted till the end of November, and marked an evolution of the campaign. Payment is no longer done directly to a Bitcoin wallet, and no email communications are needed. Instead, the attackers put up a website in the TOR network where payment can be made. Victims are identified using unique alphanumeric tokens they receive in the ransom note.
The website is a good example of a double extortion mechanism – it contains all leaked databases for which ransom was not paid. The website lists 250k different databases from 83k MySQL servers, with 7TB of stolen data. Up till now, GGSN captured 29 incidents of this variant, originating from 7 different IP addresses.
This phase marks an evolution of the campaign in several ways.
- First, the mapping between a victim and their stolen database is now done automatically, with a unique token, and does not involve searching through IPs and domains to find the stolen database.
- In addition, the “repository” of all stolen databases is managed in one place and is public – victims can see their databases on the list and be pressured into paying the ransom.
- Last, the website creates a smoother experience for the victim and even builds more trust between the victim and the attackers, as the details of the database are provided.
Attack Chain
The attack starts with a password brute-force on the MySQL service. Once successful, the attacker runs a sequence of queries in the database, gathering data on existing tables and users. By the end of execution, the victim’s data is gone – it’s archived in a zipped file which is sent to the attackers’ servers and then deleted from the database. A ransom note is left in a table named WARNING, demanding a ransom payment of up to 0.08 BTC.
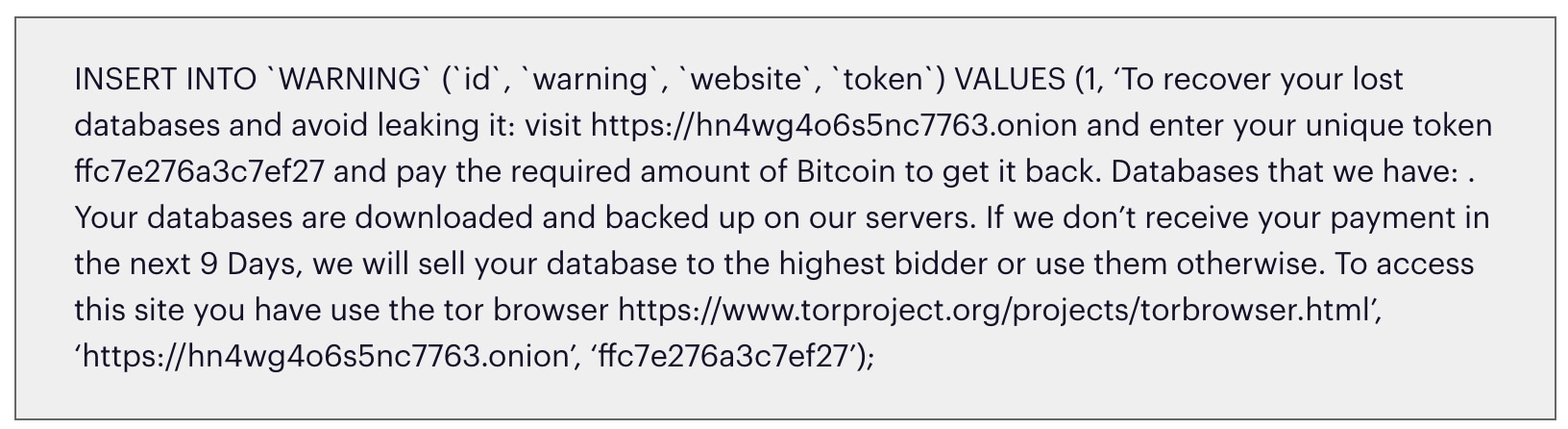
Additionally, a backdoor user mysqlbackups’@’%’ is added to the database for persistence, providing the attackers with future access to the compromised server.
Leak Site Offers Databases for Purchase
The .onion domain – hn4wg4o6s5nc7763.onion – leads to a full-fledged dashboard where victims can provide their token and make the payment. The .onion top-level domain is used to distinguish services hosted in the TOR network. Such websites can only be accessed from the TOR browser, and guarantee that both their operators and the client-side users remain anonymous. Choosing to use an .onion domain makes it harder to trace the attackers and where their infrastructure is hosted.
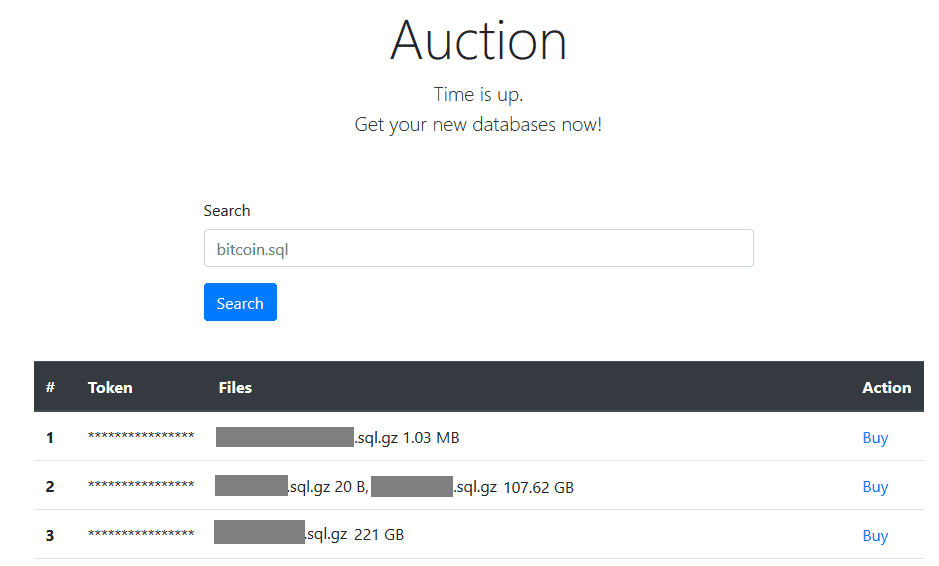
All stolen databases are offered for sale in a section in the website titled Auction, all having a uniform price of 0.03 Bitcoin. A table on this page lists all stolen databases per token, along with their sizes. By crawling the auction pages, Guardicore Labs found nearly 83k unique tokens. Restoring data will cost a victim 0.03 BTC, which equals (at the time of writing) around $520.
Ransomware Attacks Come in Different Forms
Some ransomware campaigns are highly targeted; they are planned ahead for months and are executed flawlessly. Those campaigns are advanced, persistent threats (APTs). They breach the network, perform silent and careful lateral movement to infect multiple assets, encrypt valuable data and demand ransom for restoration.
Others campaigns are opportunistic in nature. These campaigns are usually automatic, meaning they are executed from a script rather than by a human being. Intelligence gathering or reconnaissance are not part of the process. This characteristic allows such campaigns to scale significantly and potentially infect important servers that are mistakenly connected to the internet.
Attack campaigns of this sort are untargeted. They have no interest in the victim’s identity or size, and result in a much larger scale than that available for targeted attacks. Think of it as “Factory Ransomware” – the attackers run the attack, making less money per victim but factoring the number of infected machines.
PLEASE_READ_ME is a great example of the latter type:
- It is untargeted: it attempts to infect any of the 5 million MySQL servers which are internet-facing.
- It is transient – it does not spend time in the network besides that required for the actual attack. With no lateral movement involved, the attack begins and ends inside the MySQL database itself and does not try to escape it.
- It is simple. There are no binary payloads involved in the attack chain, making the attack “malwareless”. Only a simple script which breaks in the database, steals information and leaves a message.
The PLEASE_READ_ME operators are trying to up their game by using double extortion in scale. Factoring their operation will render the campaign more scalable and profitable. Guardicore Labs provides an IOCs repository and will keep monitoring this campaign to help organizations protect against it.


