It’s All In the Cards: Preventing Payment Abuse for Retailers
The evolving challenge of carding and payment abuse for retailers
In the United States alone, there has been a 140% increase in credit card fraud attacks against ecommerce merchants over the past three years. Carding attacks have become a serious challenge for retailers, and attackers are getting smarter about how they pull them off.
Using a combination of sophisticated artificial intelligence (AI) and human-assisted bots, fraudsters can test thousands of stolen credit card numbers at scale — mimicking real users, bypassing defenses, and adapting in real time to avoid detection. What looks like normal traffic can be a wave of fraud attempts, leading to chargebacks, skewed analytics, and performance issues for a business.
How does a carding attack work?
Fraudsters can carry out a carding attack in five simple steps.
Fraudsters acquire a list of stolen credit card details.
They visit online stores with open payment flows — whether through guest checkout, logged-in sessions, or account pages that allow adding new cards. Guest checkout, in particular, is a favorite target since it offers fewer barriers and often lacks tailored fraud detection.
They place small orders to see if the card works.
If the payment is approved, they know the card is active and can use it for larger purchases or sell the verified card for a higher price.
If the payment fails, they move on to the next stolen card.
Key signs to identify carding attacks
Spotting a carding attack isn’t always obvious, but there are key signs retailers should watch for, including:
A sudden spike in failed payment attempts, especially if they’re clustered around certain products or locations
Unusual patterns, like multiple small transactions in a short time frame or a surge in guest checkout activity
A rise in chargebacks or fraud alerts from your payment processor
In addition, if your analytics start showing a high bounce rate from the checkout page, that may indicate that bots are running tests and abandoning the cart once a card fails.
How Akamai Account Protector identifies carding attacks
Akamai Account Protector helps stop carding attacks by protecting at every stage of the account lifecycle, not just at account login. It uses advanced behavioral analytics and machine learning to understand what real user behavior looks like so it can quickly spot when something’s off — such as fraudsters testing stolen cards during checkout, whether as logged-in users or via guest checkout, where traditional fraud controls are often weaker.
By analyzing signals like device characteristics, abnormal email syntax, phone use, and interaction patterns in real time, Account Protector can flag and block suspicious activity before any damage is done.
Flagging suspicious carding attempts for immediate mitigation
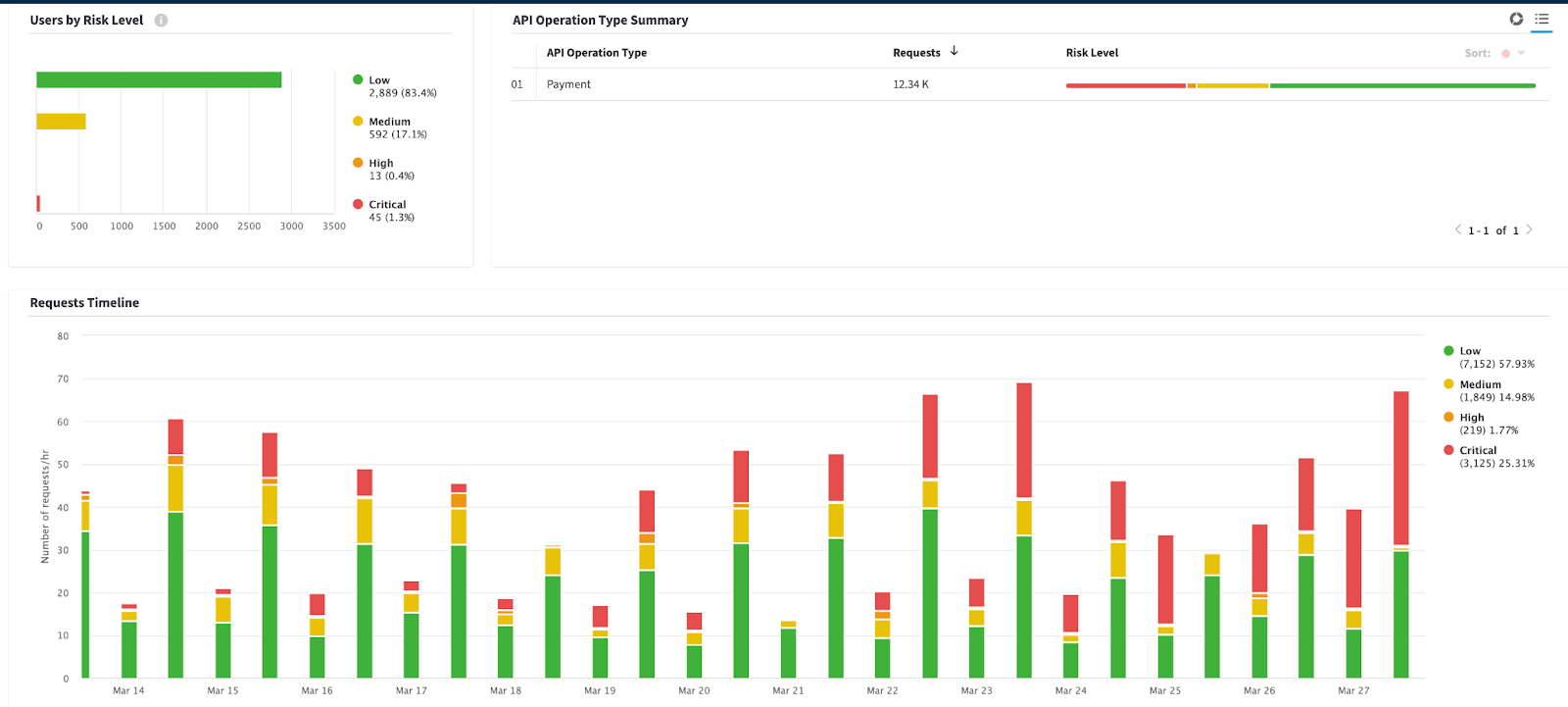
Recently, a leading U.S. grocery retailer experienced suspicious activity targeting their online checkout — specifically, the part of the customer journey flow where users are prompted to enter payment card information before purchasing. With Account Protector configured on their payment operation endpoint, the retailer was able to detect 45 unique user IDs making 3,125 requests in just two weeks.
These behaviors aligned with carding attack patterns: rapid-fire requests across multiple accounts, often using similar devices or IP addresses. By applying a risk score to user behavior, Account Protector was able to flag the suspicious carding attempts for immediate mitigation (Figure 1).
Identifying an attack on payment operation endpoints
In another case, a major U.S. retailer was experiencing heightened abuse on their payment operation endpoints. This attack involved testing large volumes of stolen credit cards and initiating large-scale fraudulent transactions with the active cards.
The stakes were high as this retailer relies on a third-party provider to validate credit cards, and each validation request came with a direct cost. A surge in unauthorized payment attempts not only heightened operational expenses but also risked penalties or even service suspension from the validation provider.
Account Protector swiftly identified the attack on the customer’s payment operation endpoints by assessing each request against a range of risk indicators and flagging critical/high-risk requests for immediate mitigation, either through challenge actions like CAPTCHA or via alerting and blocking (Figure 2). The retailer was able to stop fraudulent purchases, reduce unnecessary card validation costs, and avoid reputational damage.
In both logged-in and guest checkout flows, Akamai Account Protector helps retailers stop carding attempts in real time, no matter where fraudsters try to sneak in.
Why understanding user risk is key to preventing payment abuse
Understanding user risk is essential to staying ahead of carding attacks and general account abuse. Not all users and not all traffic pose the same level of threat, which is why a one-size-fits-all approach to fraud prevention often falls short. By evaluating risk in real time based on behavior, device signals, and context, businesses can make smarter decisions about when to step up security to prevent fraudulent activity.
This kind of risk-based approach is especially important in detecting carding attacks, which often blend in with normal traffic patterns. When you understand which users are likely attackers, you can stop fraud before it happens without slowing down the experience for everyone else.
Account Protector separates trusted users from potential attackers
Account Protector continuously analyzes a wide range of risk indicators during real user sessions, such as device type, IP reputation, and behavior patterns. It also observes behavior over time to detect abnormal activity, such as the excessive use of certain IP addresses, emails, phone numbers, devices, and user accounts.
The solution compares the activity of a particular user to the activity of the entire application’s user base. For example, if a user suddenly starts attempting dozens of requests from a new device or location, as seen in the example of the grocery retailer, Account Protector flags that as suspicious and provides businesses with methods of blocking the requests.
This behavioral insight allows it to identify carding attacks and payment abuse in real time, even when they come from seemingly legitimate sessions. By combining signals across the entire account journey, it can accurately separate trusted users from potential attackers without relying on static rules or causing unnecessary friction.
Protecting the full journey
Carding attacks aren’t going away. With bots and human fraudsters getting smarter, businesses need smarter defenses. Account Protector provides a powerful way to detect and stop these threats in real time, using behavioral intelligence and dynamic risk scoring to protect every part of the customer journey — including high-risk flows like guest checkout, where attackers often strike.
For retailers looking to reduce fraud without adding friction, it's not just about blocking bad traffic, it's about understanding user intent and acting on it with precision.
Learn more
Ready to defend against carding and payment abuse? Learn how Akamai Account Protector helps businesses stop fraud and payment abuse in real time by checking out our product page or contacting an Akamai expert.