DDoS Attack Trends in 2024 Signify That Sophistication Overshadows Size
Executive summary
Modern distributed denial-of-service (DDoS) attacks have evolved to be more sophisticated than traditional large-scale volumetric attacks.
The pivot toward sophistication over volume is reflected in simultaneous attacks on multiple destination IPs (horizontal DDoS attacks), the use of simultaneous multiple attack vectors, and the use of AI-enabled tools to systematically check defenses and then launch the attack on the weakest network surface of a target organization.
Ongoing geopolitical crises (including the Russia-Ukraine war and the Israel-Hamas war), motivated hacktivism, and the proliferation of AI-enabled tools continue to make DDoS mitigation more complex than ever before. In a digital-first world, going offline is simply not an acceptable outcome for organizations.
Sophisticated DDoS attacks need an equally sophisticated DDoS defense platform and a strategy that combines machine-level automation with critical human intelligence. When automation fails — and it does often fail, either by under- or overmitigating an attack — security experts and robust processes save the day.
The value of preparing in advance cannot be overstated. A true DDoS defense system and strategy should not only protect your network during an active attack campaign, but also continuously build a proactive defense posture.
What’s new with good old DDoS attacks?
It’s 2025. Everyone’s talking about artificial general intelligence and post-quantum computing, and other next-generation technologies that promise to fundamentally change the way our digital systems operate. So, what about good old distributed denial-of-service (DDoS) cyberattacks?
It is undeniable that DDoS attacks have only grown into a more potent form of cyber nuisance, and DDoS threats continue to be a persistent cybersecurity challenge for businesses, governments, and public infrastructure.
What is the best way to understand the scale and the impact of such attacks? The old technique of measuring DDoS attacks in terms of size — gigabits per second (Gbps), terabits per second (Tbps) or million packets per second (Mpps) — is often not relevant or sufficient today.
Yesterday’s size is today’s sophistication
Most modern DDoS protection platforms and security vendors offer a baseline degree of security that can easily counter simple or rudimentary volumetric attacks. Some vendors have even dipped into creative marketing to invent fancy terms like “hypervolumetric DDoS attacks” to grab attention and stay relevant in this evolving threat landscape. But if size does not matter, what does?
A single-word answer: sophistication.
However, the level of sophistication in a DDoS attack cannot be easily distilled into a single metric. The sophistication of an attack is a mosaic of more seasoned attack types and advanced tactics, techniques, and procedures (TTPs). Cybercriminals and hacktivists employ these TTPs to easily overwhelm inadequate DDoS cybersecurity systems that depend on automated algorithms alone, or on an on-prem–only approach.
In this blog post, we will discuss the most relevant DDoS attack trends observed by Akamai in 2024 — and provide three key takeaways that will help you protect your organization in 2025 and beyond.
A retrospective of the DDoS attack trends and patterns in 2024
More horizontal DDoS attacks
If there was one common theme among almost all DDoS attacks observed by Akamai’s DDoS protection solutions, including Akamai Prolexic, Akamai Edge DNS, and Akamai App & API Protector, is that cybercriminals were consistent in targeting multiple IP addresses and internet-facing assets and services with a variety of DDoS attack types. These assets and services include HTTP, DNS, IPSEC, SD-WAN, security information and event management (SIEM) web front ends, FTPS services, Transmission Control Protocol (TCP), User Datagram Protocol (UDP), SYN floods, and others.
These “horizontal DDoS attacks” have become fairly common with the wide availability of AI tools that can cast a wide net, systematically check for defense vulnerabilities, identify weak points, and then pool resources to go after the weakest points in an organization’s defense posture.
Figure 1 shows the wide prevalence of horizontal DDoS attacks. Almost 30% of the total DDoS attacks mitigated by Akamai Prolexic were multidestination, horizontal DDoS attacks. It is important to note that until as recently as Q3 2022, horizontal DDoS attacks accounted for fewer than 20% of the total DDoS attacks.
However, since Q4 2022, these types of attacks have accounted for up to 30% of the total DDoS attacks mitigated by Akamai.
Not just multiple destinations but also multiple DDoS attack vectors
Do you remember the name of the movie that won the Academy Award for Best Picture in 2023? If not, here’s a reminder: Everything Everywhere All at Once. You could be forgiven for believing that cybercriminals took this movie title as an inspiration for their attacks in 2024 … and beyond.
Almost all the DDoS attacks mitigated by Akamai in 2024 were highly sophisticated attacks that employed multiple attack vectors, used either simultaneously or in a rapidly evolving cycle to overwhelm DDoS defense platforms that depend on automation only. Modern attacks — on multiple destinations, multiple vectors, and multiple layers of a network (Layers 3, 4, 5, 6, and 7, including HTTP and DNS) per the Open Systems Interconnection (OSI) model, and with rapidly evolving TTPs — can truly be summarized as everything everywhere all at once.”
Figure 2 showcases the increasing variety of DDoS attack vectors employed by cybercriminals and threat actors to overwhelm automation-only DDoS defense platforms. The increasing number of DDoS attack vectors and the rapidly cycled manner in which they are used for amplifying an attack’s impact attests to the pivot of cybercriminals from volume to sophistication.
But wait, there’s more! The DDoS attacks are getting longer, too.
It’s not just that the modern DDoS attacks are multidestination and multi-vector. They are also getting longer in duration, often running as well-orchestrated DDoS campaigns for several hours, or even days and weeks, at a time.
There are two key underlying factors that support this trend.
Multiple geopolitical conflicts around the world have enabled threat actors with the financial and technical resources necessary to launch and sustain massive, long-duration DDoS attack campaigns on their enemies.
The other factor is that the wide proliferation of AI-enabled systems and infected Internet of Things devices that turn into bots are extremely useful to the threat actors. As the new generation of technologies rapidly evolves, it has become a game of one-upmanship between the criminals and security systems.
DDoS attacks that last longer than 60 minutes often systematically test weaker points in a network’s defense systems before pooling resources to overwhelm the bandwidth of the network and impact connectivity.
Figure 3 showcases that while the average duration of DDoS attacks has remained flat over the past three years, the number of highly sophisticated and orchestrated attacks that last 60 minutes or more have continued to increase.
More than 60% of DDoS attacks have a DNS component
We’ve said it before and we’ll say this again: If your DNS goes down, your online presence disappears. It is therefore not surprising that threat actors are doubling down on attacking the DNS infrastructure of vulnerable organizations.
What makes DNS a particularly easy target is that unlike modern network infrastructures, DNS was developed in the early days of the internet when security wasn’t a major concern. Back then, the focus was on the speed and convenience of using human language to interact with digital assets.
Over the decades, many organizations that invested capital in developing on-prem DNS infrastructure have been left vulnerable to DNS DDoS attacks.
Figure 4 shows more than 60% of the total DDoS attacks mitigated by Akamai in Q1, Q3, and Q4 2024 had a DNS component. It is interesting to note that while DNS resource exhaustion (or Layer 7 DNS query flood) attacks were the leading type of DNS-focused attacks in 2023, threat actors have pivoted back to DNS reflection as a preferred vector of DNS attacks since Q2 of 2024. Additionally, in some instances, infrastructure that hosts DNS and DNS-related services could be underprovisioned or inadequately protected from the evolving threats. These changes emphasize the need for robust DNS DDoS defense systems that can easily adapt to evolving threat variables.
So, what about the volumetric gorilla in the room?
Although the impact of the sophistication and complexity of modern DDoS attacks outweighs the impact of their size, it is also important to acknowledge that threat actors are employing all the TTPs available to them to orchestrate debilitating DDoS attacks.
And one potent variable is, in fact, size — which, when combined with multiple vectors and multiple destinations all at once, makes it easy to overwhelm and bring down DDoS defense platforms that aren’t equipped to handle the onslaught of such attacks.
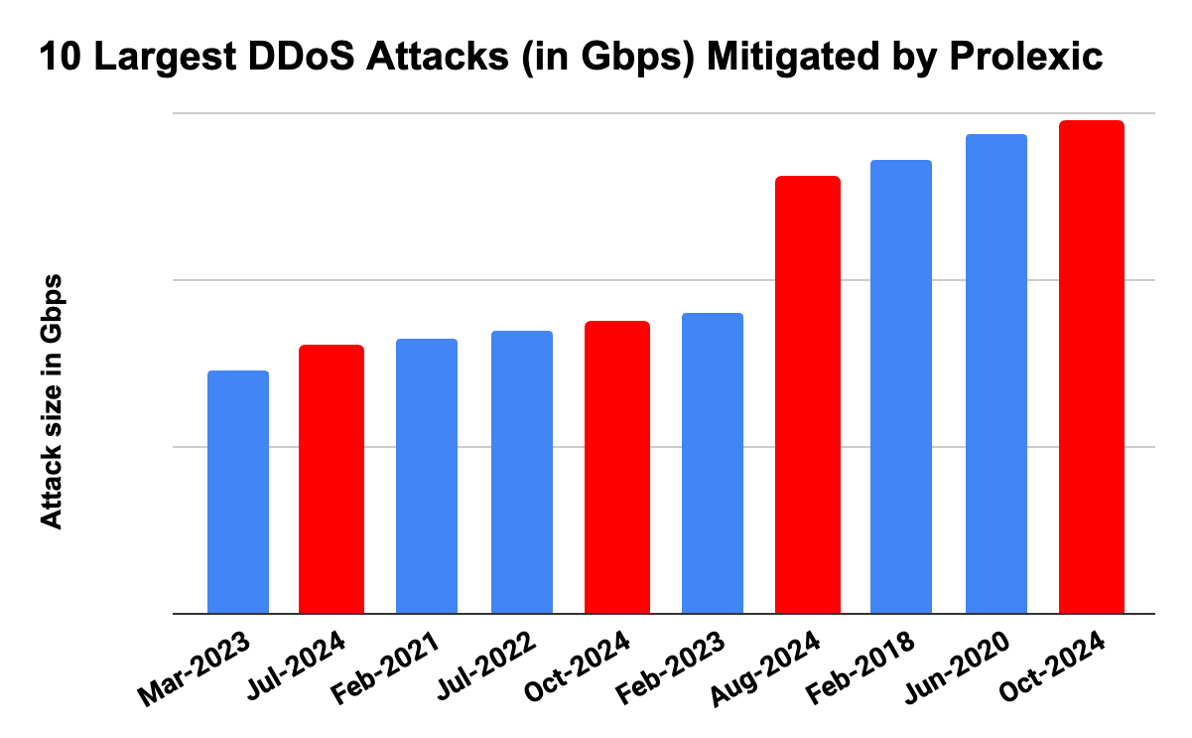
Four of the 10 largest DDoS attacks ever mitigated by Akamai Prolexic took place in 2024. The proliferation of AI-powered tools and global botnets have made it relatively easy and inexpensive for attackers to scale up the size of DDoS attacks..
Who runs the world? Apps and APIs
Let’s state the obvious: Web applications and APIs run the world today. You are probably reading this blog post using a web browser — that is, an application — on your computer or phone. Or maybe you saw a post about this blog on the LinkedIn app on your smartphone or tablet. When internet-facing applications drive the modern world, it is not surprising that cybercriminals often tend to focus their DDoS attacks on the applications of a victim organization.
In 2024, Akamai observed a continuing trend of massive Layer 7 attacks, or application-layer attacks, primarily in North America and the Europe, Middle East, and Africa region. Figure 6 shows an increase in application-layer attack traffic in the final months of the year. There was a noticeable spike in Layer 7 DDoS attacks in the Asia-Pacific region during the final quarter of the year, often targeting financial services organizations and critical infrastructure for public services.
Behavioral DDoS Engine protects applications and APIs under attack
App & API Protector’s Behavioral DDoS Engine has played a key role in automatically protecting customer applications and APIs from malicious DDoS traffic by intelligently identifying patterns and blocking such traffic at the edge of an organization’s network.
Three key takeaways
Prepare your defenses proactively. Reduce the attack surface of your network and build robust runbooks that can save precious seconds during an inevitable DDoS attack.
Appreciate the fact that modern sophisticated DDoS attacks are no longer just about volume. Today’s DDoS defenses require advanced machine-level automation along with invaluable human expertise and tight processes to be effective. Automation alone could lead to overmitigation and block genuine user traffic. It could also be easily and accidentally misconfigured with unintended consequences. Use automation wisely, tactically, and safely with the consultation of trained professionals.
Recognize that in a digital-first world, going offline — even for a second — or unintentionally blocking some percentage of legitimate users to give the perception of uptime are unacceptable outcomes. Trust your security to solutions that have withstood the test of time. DDoS defense platforms that go offline themselves cannot protect your network during times of need. Choose wisely, or you might end up spending many hours (and dollars!) trying to restore your network after a DDoS attack.