Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
LockBit ransomware is a type of cyberattack that encrypts files on infected computers, allowing attackers to demand ransom payments in exchange for decryption keys. Originally known as “ABCD ransomware,” LockBit ransomware has been active since at least January 2020. The cybercriminals that developed LockBit offer it as ransomware as a service (RaaS), allowing affiliates to use the malware to conduct ransomware attacks in exchange for a percentage of the ransom revenue.
LockBit was the world’s most prevalent form of ransomware in 2022, and by 2024, had amassed more than 2,000 victims and collected more than $120 million in ransom payments. LockBit operations have targeted organizations and enterprises in multiple industries, including healthcare, education, finance, government, technology, automotive, and retail companies in the U.S., Canada, India, Brazil, and many other countries. (cited source)
In February 2024, law enforcement agencies charged two Russian nationals connected to the LockBit ransomware group and seized a number of websites connected to the LockBit crime organization, disrupting the ability of threat actors to use the malware to encrypt files and extort victims. However, within a few days of being dismantled, the LockBit gang was able to restore its servers and get its software up and running again.
How LockBit ransomware attacks work
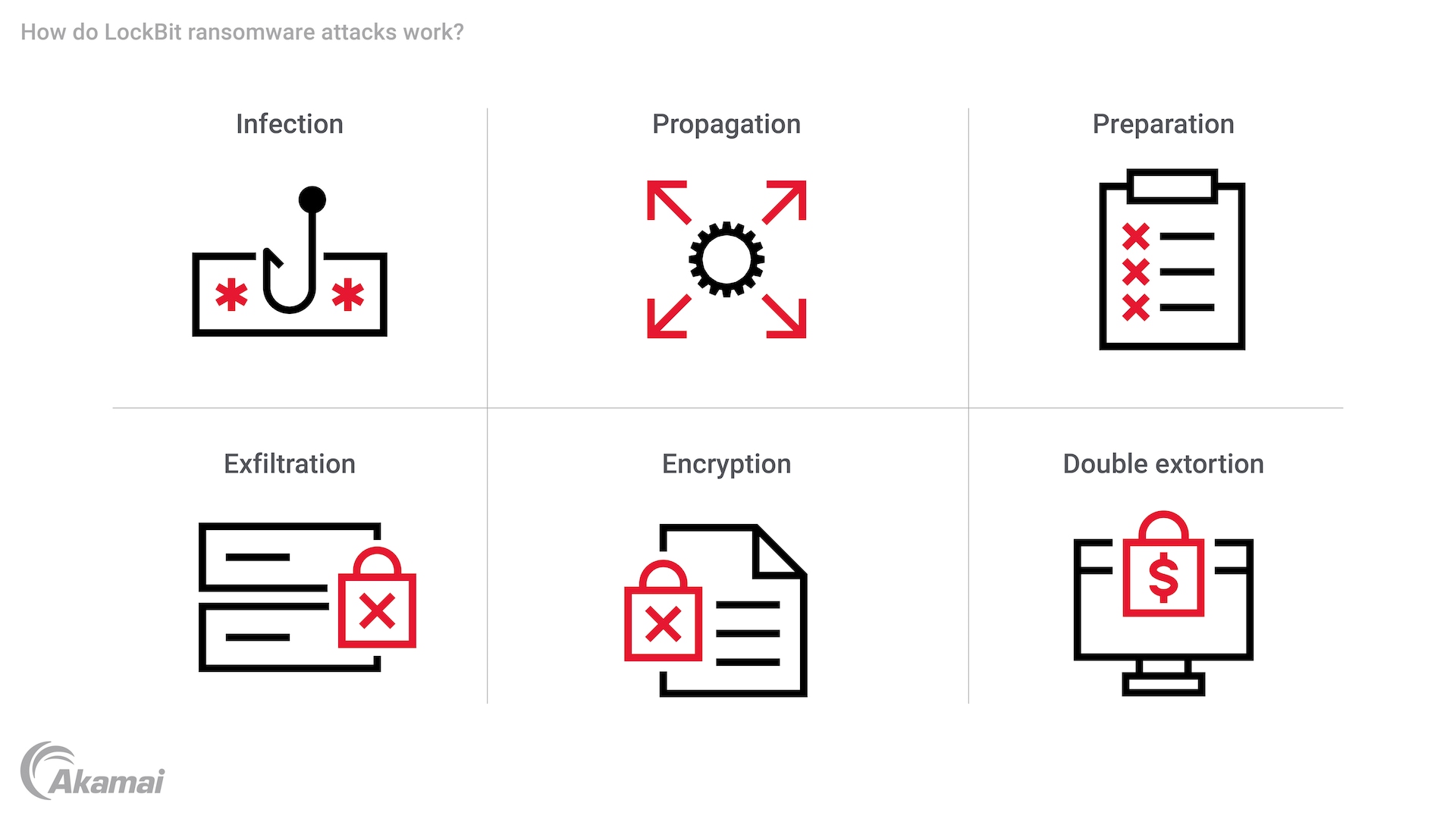
LockBit ransomware uses a variety of techniques and tactics to access systems and encrypt files.
- Infection. LockBit ransomware achieves initial access to IT environments through phishing emails, by exploiting software vulnerabilities, or by using stolen credentials to access systems through VPNs, Remote Desktop Protocol (RDP), or other points of entry. The LockBit gang also attempts to recruit disgruntled insiders, who can receive a payout for providing account credentials or launching an attack from inside the network.
- Propagation. After gaining access, the LockBit group uses tools like Windows PowerShell and PsExec, as well as lateral movement techniques, to explore the network and identify high-value targets. LockBit also has the ability to self-propagate, spreading on its own to find additional accessible hosts in an IT environment without requiring intervention by attackers.
- Preparation. LockBit malware uses post-exploitation tools to gain account privileges, force group policy updates, and take a variety of actions before encrypting files. These actions include disabling security programs and tools that would allow the victim to recover data. The objective of this stage is to make it impossible or prohibitive for the victim to regain access to data without paying the ransom.
- Exfiltration. Later forms of LockBit are designed to exfiltrate targeted files to an external server, allowing hackers to extort the victim by threatening to publish sensitive data on a leak site.
- Encryption. Once preparation is completed, the ransomware payload encrypts files, effectively preventing the victim from accessing them without a decryption key. The software also leaves copies of a ransom note in every system folder.LockBit ransomware uses a variety of techniques and tactics to access systems and encrypt files.
- Double extortion. Later forms of LockBit ransomware provide tools for data exfiltration, allowing LockBit operators to perform double extortion by demanding a ransom to restore access to files and another ransom to prevent stolen data from being leaked on Tor sites on the dark web.
Variants of LockBit ransomware
The LockBit ransomware virus has evolved quickly over several years. Ransomware using LockBit code was initially observed in 2019. The initial version of the software used the file extension “.ABCD” to rename files.
- January 2020: A ransomware variant using “LockBit” as an extension was first seen in Russian-language cybercrime forums.
- June 2021: LockBit version 2 (LockBit 2.0) arrived, with a built-in tool for stealing information known as “StealBit.”
- October 2021: The Linux-ESXi Locker version of LockBit 1.0 expanded the ransomware’s capabilities to target systems to Linux and VMware ESXi.
- March 2022: LockBit 3.0, or LockBit Black, emerged as a new variant, sharing similarities with Black Matter and ALPHV or BlackCat ransomware.
- January 2023: The LockBit Green variant incorporated source code from Conti ransomware.
- April 2023: LockBit ransomware encryptors targeting macOS were seen on VirusTotal.
Defending against LockBit ransomware
To defend against LockBit ransomware and other forms of ransomware, law enforcement and cybersecurity organizations like the FBI and CISA encourage companies to adopt several best practices.
- Multilayered defenses. Ransomware protection includes antivirus and anti-ransomware software, endpoint detection and response (EDR) tools, and security awareness training to help users recognize social engineering and phishing attacks. Security teams can also potentially use ransomware removal tools to clean systems of LockBit code.
- Network segmentation. Segmenting networks and individual assets reduces the ability of LockBit ransomware and attackers to move laterally through a system after gaining initial access.
- Strong access control. Using multi-factor authentication (MFA) and strong passwords can help prevent attackers from gaining unauthorized permission to accounts.
- Regular backups. Organizations that back up files regularly, and store copies of critical data in offline backups, may be able to achieve recovery without paying ransom.
- Vulnerability management. Regularly updating and patching software and operating systems is essential for fixing vulnerabilities that could be exploited by attackers. This is especially critical for software like Microsoft Windows and Linux that use the Server Message Block (SMB) protocol or RDP.
- Continuous monitoring. Using advanced threat detection tools and adopting a robust incident response plan can help to quickly identify LockBit ransomware attacks, minimize damage, and speed recovery.
Frequently Asked Questions (FAQ)
Ransomware is a form of malicious software or malware that infects machines and encrypts files on computers and servers in an IT network. This allows attackers to issue a demand for a ransom payment, in exchange for the decryption keys that will restore access to a victim’s data. Ransomware threats have risen sharply in recent years, and are among the most dangerous and costly forms of cyberattacks today for organizations in nearly every industry.
In the ransomware as a service (RaaS) business model, operators of ransomware lease the malware to affiliates who carry out attacks and pay the operators a portion of their ransom revenue. Because of the large number of LockBit affiliates, LockBit ransomware operations vary widely in their use of tactics, techniques, and procedures (TTPs), making attacks more challenging for security teams to detect and mitigate.