Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
DarkSide ransomware is a type of malicious software, or malware, that encrypts files on servers and devices, allowing attackers to demand a ransom in exchange for decryption keys. DarkSide ransomware operators are known for employing double extortion tactics: In addition to demanding a ransom to decrypt files, they exfiltrate sensitive data and threaten to publicly release the stolen data if the victim organization doesn’t comply with ransom demands.
DarkSide also operates as ransomware as a service (RaaS), a business model in which the operators of ransomware lease it to other cybercriminals known as affiliates in exchange for a percentage of the ransom profits.
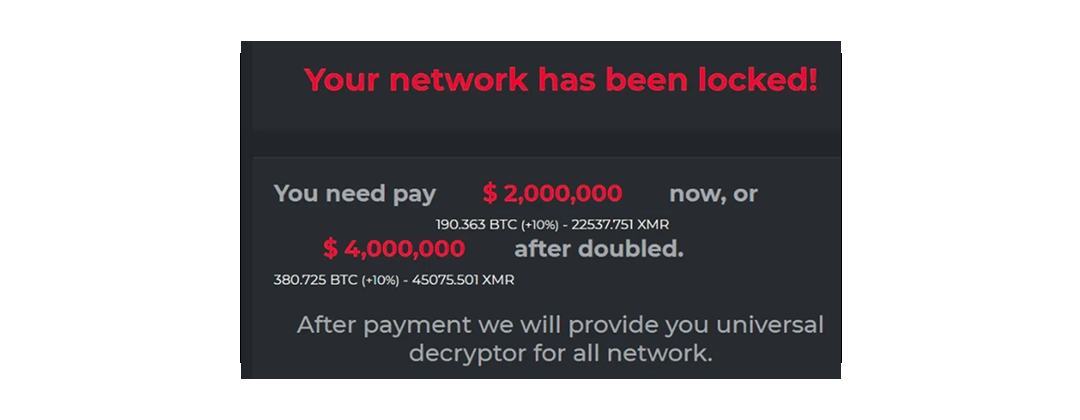 An example of a DarkSide ransomware notice that appears on victims’ computer screens
An example of a DarkSide ransomware notice that appears on victims’ computer screens
Who operates DarkSide ransomware?
DarkSide ransomware is run by the DarkSide Hacker Group, a cybercrime organization that operates worldwide. The DarkSide group is known for publicly stating a preference for targeting large and profitable corporations and critical infrastructure rather than nonprofits like medical, educational, or government organizations.
The DarkSide group is believed to be Russian or Eastern European, but it is thought to be a for-profit operation rather than a state-sponsored group. Because the code used by DarkSide resembles software used by REvil ransomware, experts speculate that DarkSide may be an offshoot or affiliate of REvil.
A history of DarkSide ransomware
The DarkSide ransomware group emerged around August 2020, conducting sophisticated attacks on high-profile targets. The group began offering its ransomware as a service in November 2021, and it published version 2.0 in March 2021.
In May 2021, the DarkSide group claimed it was shutting down its operations and RaaS affiliate programs in response to pressure from the U.S. government. However, security experts suggest that the group may have simply reorganized its hacking activities under a different name. In April 2022, the FBI released an advisory notice that several criminals related to BlackCat ransomware have links to DarkSide, suggesting that the BlackCat ransomware variant might be a rebranded version of DarkSide.
How does DarkSide ransomware spread?
Rather than using phishing or spear phishing like many other types of ransomware, the DarkSide variant typically gains initial access by exploiting vulnerabilities in Windows and Linux operating systems, principally through Remote Desktop Protocol (RDP). DarkSide also gains access by exploiting weak passwords, improperly configured firewalls, and lack of strong authentication controls.
How does DarkSide ransomware work?
After accessing an IT network with ransomware, DarkSide threat actors perform a series of steps to increase the impact of the attack.
- Command and control: A DarkSide ransomware attack typically involves command and control through an RDP client running over port 443, routed over Tor. They may also use Cobalt Strike as a secondary mechanism.
- Credential theft: Attackers escalate privileges to steal credentials, allowing them to gain access to other parts of the network.
- File deletion: DarkSide ransomware deletes volume shadow copies of files on computers so that victim organizations cannot easily restore access by reverting to these copies.
- Evasion: DarkSide attackers take certain steps to avoid possible detection, including deleting registry keys, stopping event logging processes, or interfering with tools for security scanning.
- Reconnaissance: Hackers employ lateral movement within compromised networks to identify high-value targets with sensitive information.
- Encryption: DarkSide hackers encrypt files only after they have mapped the environment and exfiltrated sensitive data. The ransomware code is distributed using well-known backdoors, and the payload contains an executable file, a unique file extension, and a unique victim ID that enables organizations to make a payment on DarkSide’s website. These unique identifiers enable the ransomware to avoid detection by signature-based systems.
- Ransom note: DarkSide uses the Tor network to communicate anonymously with victims and to manage ransom payments in bitcoin. Ransom demands have ranged from $200,000 to $20 million.
Famous DarkSide ransomware cyberattacks
The most notable ransomware DarkSide ransomware incident was the attack on Colonial Pipeline in May 2021. This attack resulted in a massive shutdown of operations and caused a fuel shortage for a large part of the East Coast in the United States. Additional high-profile incidents include attacks on the IT managed services provider CompuCom, the German chemical distribution company Brenntag, and the Toshiba Tec Corp in France.
Mitigating DarkSide ransomware attacks
Preventing a DarkSide ransomware attack requires a multilayered approach to security that includes:
- Regular updates and patches to operating systems and software to remediate vulnerabilities
- Robust segmentation, antivirus and anti-malware software, intrusion prevention systems (IPS), and other cybersecurity tools informed by the latest threat intel
- Multi-factor authentication (MFA) for remote access to IT networks
- Email filters to prevent messages with executable files from reaching end users
- Network filters that block communications with IP addresses known to be malicious
- Endpoint security to detect and eliminate ransomware infections on devices
- Security awareness training to help users recognize signs of ransomware
- Frequent backups of important data, stored offline to avoid infection
- Adopting best practices from cybersecurity information organizations like CIS and MITRE
Removing DarkSide code
DarkSide ransomware removal requires a comprehensive incident response plan. Steps include:
- Isolating infected systems to prevent the malware from spreading to other servers and devices
- Using cybersecurity tools to identify and remove components of the ransomware
- Restoring affected encrypted files from backups
- Contacting law enforcement agencies like the FBI
FAQs
DarkSide ransomware is a form of malware that’s operated by the DarkSide cybercriminal group, believed to be located in Russia. The group infiltrates IT environments of large corporations, exfiltrates high-value and sensitive information, and encrypts files on servers and computers. The group then demands a ransom in exchange for a decryption key and a promise to not leak sensitive files online.
Ransomware as a service (RaaS) is a cybercrime model in which developers of ransomware allow other hackers to use their code to carry out attacks in exchange for a percentage of the ransom revenue. RaaS enables criminals with little expertise in ransomware to conduct sophisticated and lucrative attacks.

