Ransomware Attack on Airline Industry: Turning Point for India and Others

A tempting target
Recently, the airline industry in India was hit by a ransomware attack that frustrated passengers. Although the attack was contained, there was an unfortunate impact on the flight scheduling system that caused major delays for several hours. This most recent attack comes on the heels of previous major data breaches affecting airlines in India in 2021, which exposed more than one million customers’ accounts.
Cyber public enemy #1
The good news was that this ransomware attack did not create a complete shutdown of airline services; the impact was limited to a few hours of flight delays and some frustrated customers.
The fact that this ransomware attack was contained indicates that the airline has taken actions to adjust their security posture to prevent further data breaches. The restoration of services, though it took several hours, was possible because the attackers were not able to encrypt all backups.
But this attack highlights the fact that ransomware criminal gangs will keep coming back after successfully breaching an organization, and that post-attack recovery is just as important as mitigation.
Despite the fact that ransomware attacks are not new and have increased in frequency these past two years, this particular attack was widely picked up by news outlets around the world and created a sense of urgency to tackle this critical security threat.
This attack showed that threat actors will target any company, irrespective of industry, and will not hesitate to disrupt essential services for monetary purposes. Ransomware attacks have become the cyber public enemy #1 as they have affected people's abilities to pump gas, buy groceries, and now fly.
Ransomware: today’s attack method of choice
Since the beginning of the COVID-19 pandemic, with the increased digitization of the economy, the rapid growth of digital commerce, and the increase of the remote workforce, the world has seen a surge in the number of ransomware attacks.
Ransomware is a very profitable business for cybercriminal gangs. Australia, India, and Japan were the most-attacked countries in the Asia-Pacific (APAC) region in 2022. It is challenging to accurately quantify the number of ransomware attacks in this region as some organizations choose not to report those attacks to avoid the risk of bad press or government fines.
In Figure 1, we see that, as of April 2022, India accounts for 5% of all ransomware attacks reported globally, which is quite significant.
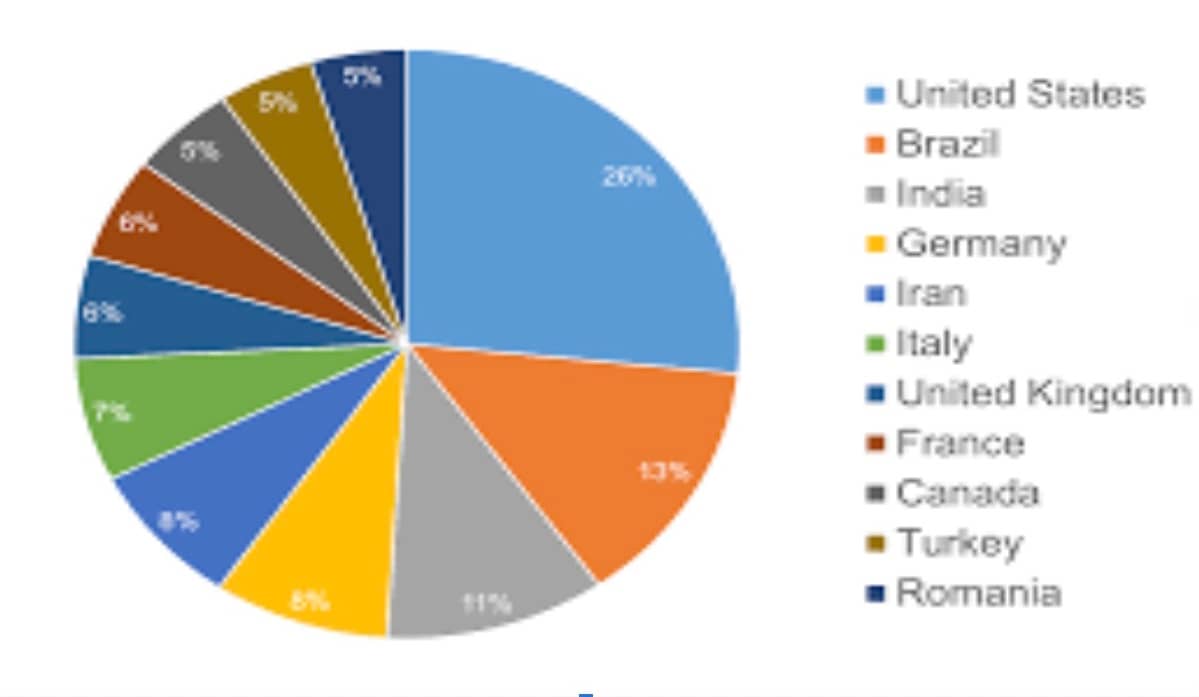 Fig. 1: The top 11 countries hit by ransomware attacks as of April 2022 (Source: BitDefender)
Fig. 1: The top 11 countries hit by ransomware attacks as of April 2022 (Source: BitDefender)
Ransomware attacks by the numbers
According to the Global State of Industrial Cybersecurity — an independent global survey to find out how organizations deal with ransomware, and determine their levels of readiness and resilience — 80% of organizations across all industries were impacted by ransomware attacks in 2021, with 52% paying a ransom.
India ranked fourth worldwide in the percentage of its organizations that were hit by ransomware in 2021, with 78% of respondents reporting attacks (Figure 2).
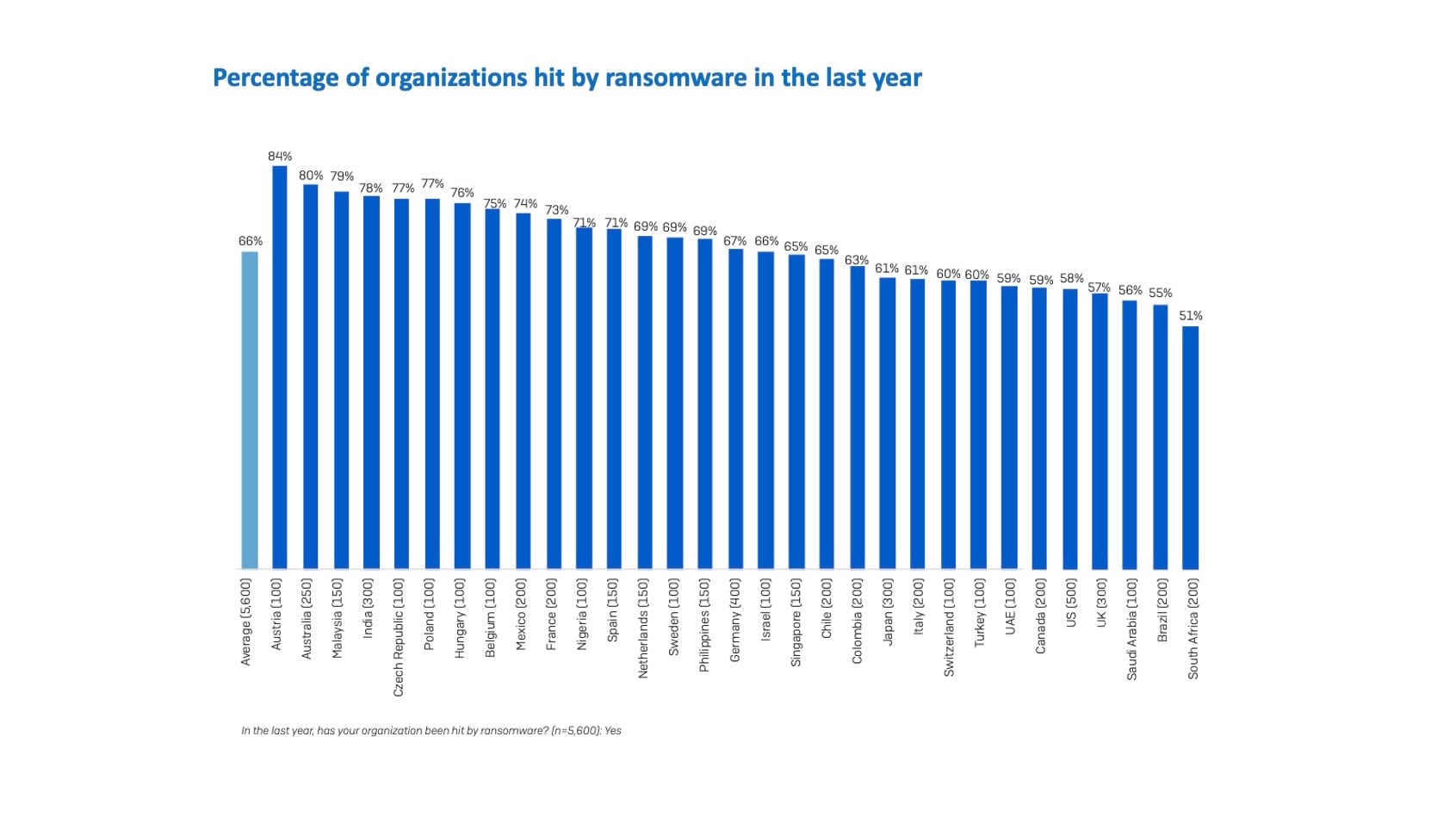 Fig. 2: Percentage of organizations hit by ransomware in 2021 (Source: Sophos)
Fig. 2: Percentage of organizations hit by ransomware in 2021 (Source: Sophos)
Cybercriminal gangs are targeting government organizations, as well as companies, and the Cyber Security Agency of Singapore has reported a rise of 154% in ransomware cases that impact government organizations and industries such as digital commerce, healthcare, and finance.
High rate of encryption
India leads the global rate of cybercriminals’ successful encryption of their organizations data, with 80% of all data being encrypted on their servers and backups (Figure 3). This will have a grave impact on those organizations.
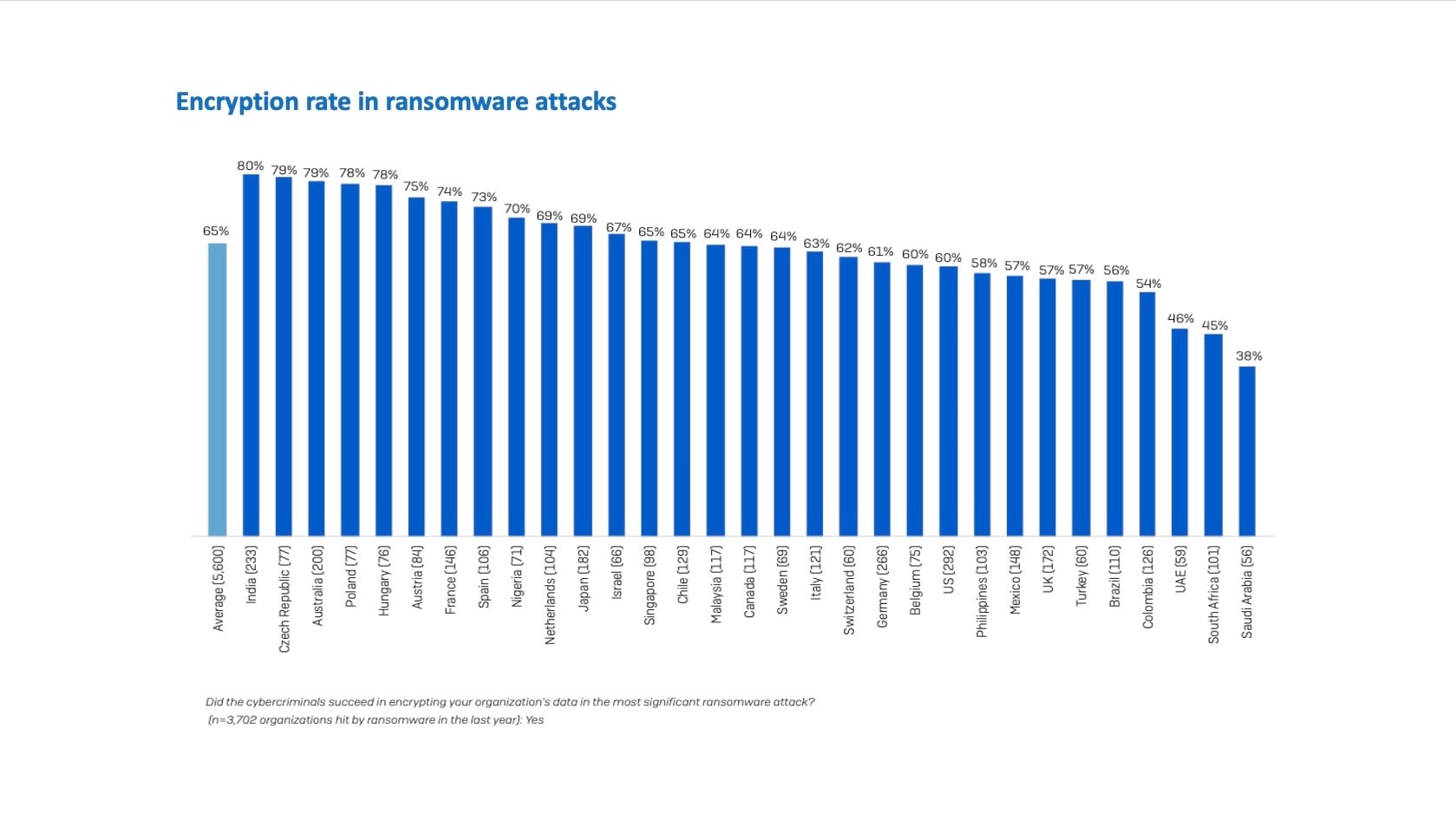 Fig. 3: Encryption rate in ransomware attacks in 2021 (Source: Sophos)
Fig. 3: Encryption rate in ransomware attacks in 2021 (Source: Sophos)
It is essential that Indian businesses across all industries adopt an effective security strategy to prevent ransomware attacks from encrypting critical systems data and their backups to prevent any disruption to their business and operations.
Ransoms: a profitable business
Another great concern is that 71% of organizations in APAC have paid ransom fees of between US$100,000 and $1 million, and 13% have paid between US$1 million and $5 million. The problem is now being inflated by criminal gangs, like Conti and REvil, that sell ransomware as a service, which enables other threat actors with lower technical skills to launch attacks.
How does a ransomware attack unfold?
It is important to understand what ransomware is and how a ransomware attack unfolds. The ransomware file is a malicious file (or malware) used to encrypt data on a server. The ransomware file is added to a script or attack toolkit that is propagated over the network to vulnerable servers in order to encrypt all data. The ransomware attack is thus a lateral movement attack from a server that was breached and where the ransomware file was downloaded (Figure 4).
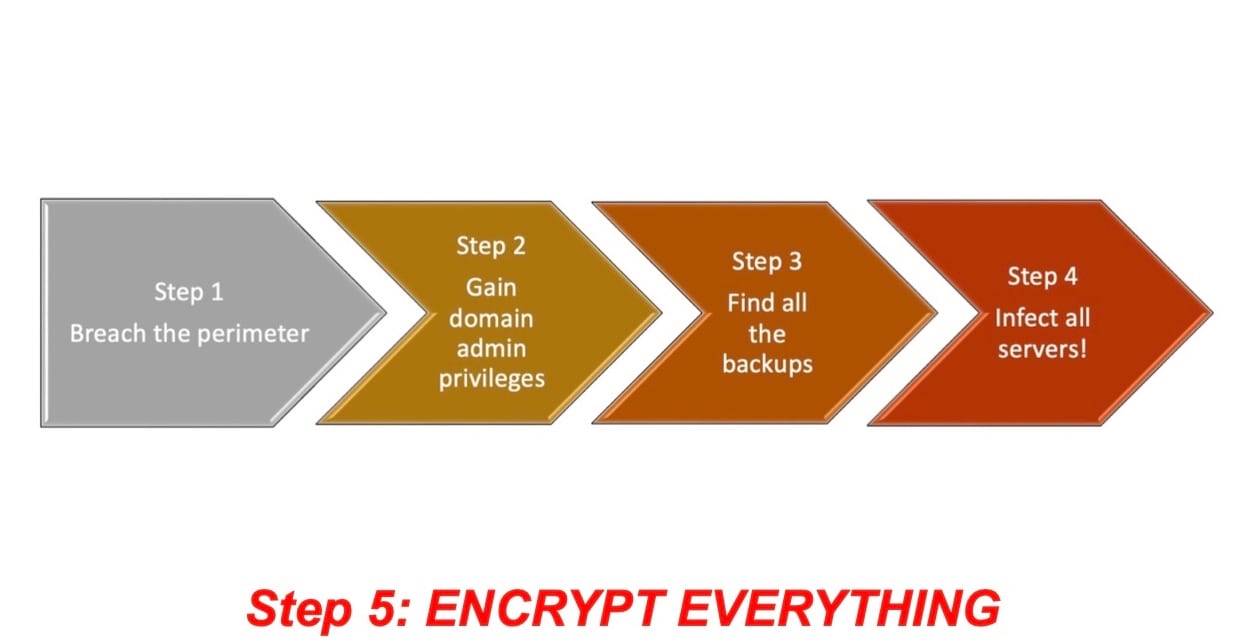 Fig. 4: The five steps in a ransomware attack
Fig. 4: The five steps in a ransomware attack
Step 1
Ransomware attacks are run by criminal gangs (such as Conti, Avaddon, or REvil) and will first work to penetrate the security perimeter of a company. They will use techniques such as spear-phishing emails and phishing attacks to harvest credentials, or use zero-day vulnerabilities like Log4j for remote code execution.
Steps 2 – 4
Once the perimeter has been breached and a server compromised, the attackers will perform network reconnaissance to identify key servers that host critical systems and data, as well as their backups. The criminals will work to further harvest credentials and gain domain admin privileges in order to move laterally toward those identified systems and their backups.
Step 5
The criminals will then start the attack by propagating the ransomware attack toolkit to those systems over the network and encrypting all files and their backups. This attack can take a day or less and prevent a company’s users and applications from accessing needed data to run their operation.
Mitigation and recovery
The ransomware threat is here to stay and is likely to increase in scale and complexity. It is therefore essential that Indian businesses across all industries adopt an effective security strategy, not only to contain but also to effectively mitigate ransomware attacks.
There will be breaches
Shipbuilding practices from as early as the 15th century involved adding bulkheads to prevent a ship from sinking in the event of a breach, rather than relying solely on preventing water from breaching the hull (Figure 5).
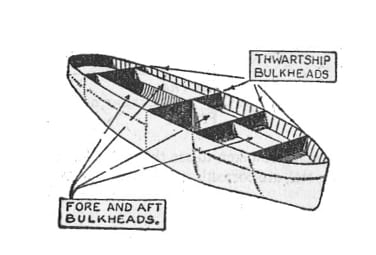 Fig. 5: Compartmentalization of a ship to reduce floodability. The ship is divided into watertight compartments by walls called bulkheads.
Fig. 5: Compartmentalization of a ship to reduce floodability. The ship is divided into watertight compartments by walls called bulkheads.
Similarly, security teams need to accept the fact that the security perimeter can, and likely will, be breached at some point (Figure 6). It is therefore essential that security teams adopt and implement a security strategy to prevent such a breach from shutting down system operations — as well as the propagation of the ransomware attack tool over the network to the domain controller, crown jewel servers, and their backups.
The latest attack on an Indian airline, which caused key systems to be offline for a few hours, demonstrates that adopting the most effective ransomware mitigation security solution is critical.
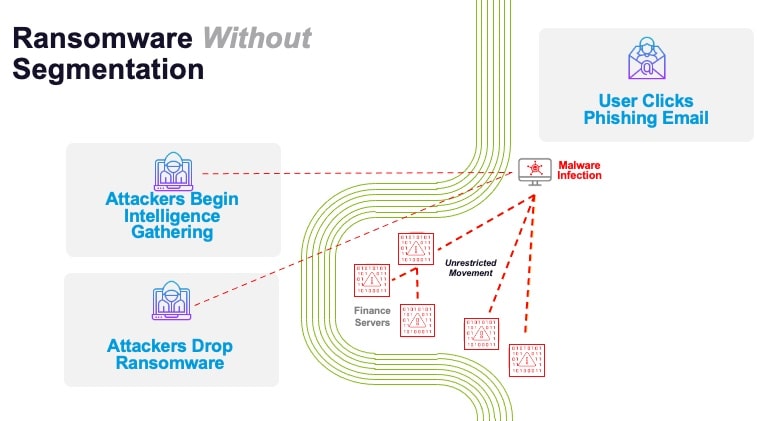 Fig. 6: A ransomware attack on an organization without microsegmention
Fig. 6: A ransomware attack on an organization without microsegmention
Zero Trust network security with software microsegmentation is the most effective strategy to fully mitigate and recover from a ransomware attack and help protect business operations from disruption even though the security perimeter was breached and a server infected (Figure 7).
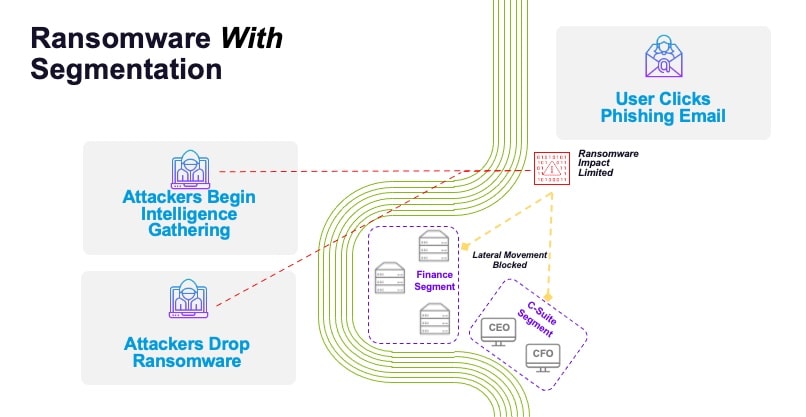 Fig. 7: A ransomware attack on an organization with microsegmention
Fig. 7: A ransomware attack on an organization with microsegmention
Network segmentation also needs to become simple, affordable, and painless. We must move away from the idea that segmentation should be accomplished at the infrastructure layer with traditional firewalls, which is complicated and requires multiple approaches as you adopt new technologies.
Preventing lateral movement is the best strategy
The answer is to start with a simple, flat, underlying network and then apply a software-defined overlay that is easy to visualize, easy to change without disruption, and works consistently across all your environments and technologies: on-premises, hybrid, or multicloud.
It is crucial to quickly segment your environment and ringfence your crown jewel servers and their backups, regardless of geographical location and underlying infrastructure.
Once you’re infected with ransomware, recovery is very difficult. Backups are often the first target of malware so the easiest path to recovery is often cut off.
Ransomware gangs are increasing the sophistication of their public key encryption techniques, and those techniques are very unlikely to be cracked by the recovery team. Therefore, the best defense against ransomware is to prevent it from propagating across your organization in the first place.
The microsegmentation solution
Forrester evaluated the top nine microsegmentation vendors in the market, including security giants such as Cisco and VMWare, and also Illumio, ColorTokens, and more. Akamai is thrilled to be a Leader in microsegmentation; we received a differentiated rating, the highest score possible, across seven criteria.
According to the Forrester report, Akamai “offers a flexible security tool that goes beyond just microsegmentation. Guardicore’s infinite tagging system and proprietary firewall solve the segmentation problem. … Unlike rigid approaches that force you into a limited set of labels, Guardicore’s proprietary firewall puts no constraints on labeling and tagging, and celebrates flexibility whenever possible.“
Furthermore, the report concludes Akamai Guardicore Segmentation is “an excellent overall microsegmentation solution for IT. Enterprises looking to deploy a host-based, granular network should look at Guardicore.”
Next steps
Lateral movement is critical to the success of a ransomware attack. With Guardicore’s microsegmentation technology — now part of Akamai’s Zero Trust security solutions — you can easily set up control policies to detect breaches and stop the spread of ransomware before attackers can gain access to your infrastructure and applications.


