Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Hive ransomware is a form of malware that encrypts the files on a victim’s servers, allowing cybercriminals to hold the files hostage until a ransom has been paid. The Hive ransomware operation is known for targeting healthcare organizations and public health institutions in addition to government facilities, communications businesses, IT companies, critical infrastructure in manufacturing, and others.
Hive is a double extortion ransomware variant. In addition to encrypting files, threat actors steal high-value data and sensitive information, threatening to make it public if the ransom is not paid.
Hive ransomware is operated as a ransomware as a service (RaaS) model, where the developers who create, maintain, and update the malware allow affiliates to use it to conduct attacks in exchange for a percentage of the profits.
A history of Hive ransomware
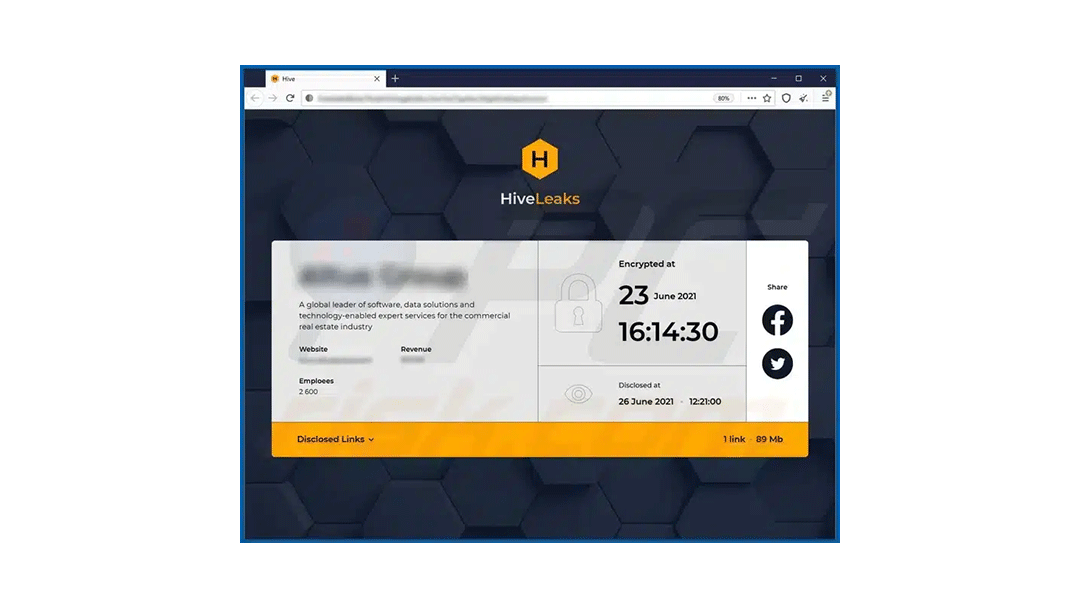 An example of a Hive ransomware notice that appears on victims’ computer screens
An example of a Hive ransomware notice that appears on victims’ computer screens
Hive ransomware was first observed in June 2021 and was active for roughly 18 months. In January 2023, U.S. Attorney General Merrick Garland announced that law enforcement officials from the Department of Justice and FBI had disrupted the Hive ransomware group through a seven-month campaign conducted in cooperation with security agencies from Germany, the Netherlands, and Europol. The investigative team lawfully infiltrated Hive’s network and hid there for a number of months, watching the group’s activity and secretly capturing decryption keys. By making decryption keys available to victims worldwide, these efforts prevented $130 million in ransom payments from being made. Eventually, law enforcement agencies seized the group’s servers in California and the EU.
Who operates Hive ransomware?
The Hive ransomware operations are believed to be run by a Russian organization. Some members of the Hive ransomware gang are thought to have migrated from other ransomware campaigns, including Conti ransomware.
Hive ransomware distribution
This ransomware variant targets the Microsoft Windows operating system as well as Linux, VMware ESXi, and FreeBSD. It uses a variety of tactics, techniques, and procedures (TTPs) to compromise IT networks, steal data, and encrypt files. Threat actors using Hive have exploited single-factor logins on Remote Desktop Protocol (RDP) applications, virtual private networks (VPNs), and other remote connection protocols to distribute the malware. Cybercrime gangs have also gained access by exploiting common vulnerabilities in software and operating systems and by distributing phishing emails with malicious attachments.
How Hive ransomware works
After attackers have accessed a victim’s IT environment, they perform a number of actions to maximize the impact of their efforts.
Creating users: Attackers establish persistent access by creating a new user and adding it to remote desktop user and administrator groups.
Impeding recovery: Hive shuts down backup-and-restore capabilities to prevent victims from easily recovering their files.
Evading detection: Hive terminates antivirus, anti-spyware, and anti-malware capabilities on the victim’s network to avoid detection. It also removes virus definitions and disables Windows Defender and other common antivirus programs in the system registry.
Exfiltrating data: Hive actors seek out high-value information and sensitive data, exfiltrating it to external servers for leverage in extorting the victim.
Encrypting files: Hive encrypts data on servers and devices with an executable file called Windows.exe.
Demanding ransom: Attackers leave a ransom note in a file called how_to_decrypt.txt in each affected directory. The note directs victims to a .onion link via a Tor browser. In addition to a ransom demand, the note threatens to publicly disclose sensitive information on its leak site, HiveLeaks.
Notable attacks
High-profile incidents involving Hive ransomware include attacks on CNA Insurance, Memorial Health System, Microsoft exchange servers, the Bank of Zambia, the government of Costa Rica, Bell Canada telecommunications, and the Swiss sporting-goods maker Intersport.
Mitigation of Hive ransomware
To block Hive ransomware variants and other ransomware from accessing and network encrypting files, IT teams can deploy multiple levels of cybersecurity that include:
Segmentation. Segmentation and microsegmentation prevent ransomware from spreading by blocking lateral movement within a network.
Updates and patches. By regularly installing updates for operating systems, software, and firmware as soon as they are released, IT teams can prevent attackers from exploiting known vulnerabilities.
Multi-factor authentication (MFA). Requiring MFA for as many services as possible helps to ensure that hackers cannot gain unauthorized access to a network.
Frequent backups. Regularly backing up valuable data — and ensuring a backup is disconnected from the network — enables faster recovery after a Hive ransomware attack. Backups should be encrypted and immutable, meaning they cannot be altered or deleted.
Continuous monitoring. Tools that monitor web and network activity for signs of suspicious behavior can help to uncover threats early.
Antivirus/anti-malware. These technologies, powered by up-to-the-minute threat intelligence, can help detect and block ransomware on networks and devices.
Eradicating Hive ransomware
When a cyberattack like Hive ransomware is detected, IT organizations must work quickly to perform the following steps.
Isolate the infection. To prevent the ransomware from spreading to other devices, IT teams must disconnect the infected system from the network and all networking capabilities, including wireless and Bluetooth networks.
Eradicate the code. Using ransomware removal tools, teams must clean infected drives and servers to be sure all ransomware code has been eradicated.
Recover files. Teams can restore data by recovering clean copies of encrypted files from backup storage.
FAQs
Hive ransomware is a form of malware that encrypts files on a victim’s devices and servers, holding data hostage until ransom has been paid. Hive operators also exfiltrate high-value files, allowing them to extort victim organizations by threatening to publish sensitive data on leak sites if the ransom is not paid. Hive uses a ransomware as a service (RaaS) model, where the ransomware operators “lease” their code to other cybercriminals for a percentage of the ransom payments.
Following the 2023 takedown of the Hive ransomware operation, the group’s ability to launch attacks was significantly impaired. However, as with many other forms of ransomware, the threat actors involved in the Hive operation have likely moved on to other groups that are creating new variants.

