Highly Sophisticated Phishing Scams Are Abusing Holiday Sentiment
Executive summary
Akamai Security Intelligence Group has observed a new and highly sophisticated phishing kit that is mimicking several large retail brands ahead of the holiday season.
The kit uses a mixture of social engineering, multiple evasion detection techniques, and access control to bypass security measures.
One of the evasion techniques — utilizing URI fragmentation — is novel. The email via which the scam is delivered contains a token, which is later used to reconstruct a URI link that the victim will be redirected to. Any access to a phishing scam without obtaining and using that token will be restricted from accessing the phishing landing page. The kit not only abuses the brands it is mimicking, it also abuses hosting companies by dovetailing on their trusted reputation.
The adversary abuses URL shorteners, fake user profiles and testimonials, and CDN functionality for infrastructure resilience.
The kit is geographically targeted, to the point of blocking access outside of the intended target geography. This campaign is targeting North America, which has made up 89% of the victims.
We have included a list of associated IOCs.
Overview
Phishing still works. Threats continue to evolve in sophistication, and yet — despite years of evangelism and education — phishing is still the most common attack vector. When you combine those two facts and get a very sophisticated phishing kit, it becomes even more dangerous. As we are moving into the holiday season, a known high for phishing success, we must be especially aware of guarding against these scams.
From mid-September to the end of October 2022, Akamai’s researchers were able to uncover and track an ongoing phishing campaign that has preyed on holiday specials. This particular campaign entices victims with the chance to win a prize, requesting credit card details “only” to cover the cost of shipment. Between the timing of the campaign and the common promotional pushes around Labor Day and Halloween, this kit appears entirely legitimate to victims (Figure 1).
By playing into the holiday spirit, this kit mimics a well-known legitimate retail marketing ploy. An emotional response allows the attackers to more convincingly engage with victims. This is social engineering in an all-encompassing sense: Taking advantage of a victim’s holiday spirit and promising them a reward for putting in their personal information. The victim's emotional response results in a favorable outcome for the attacker: credit card information.

Fig. 1: Holiday phishing campaign
As you can see in Figure 1, this kit is sophisticated in its branding. This kit abused several well-known brands in a highly realistic way. On its own, though, this isn’t enough — this campaign also evades detection by creating agile infrastructure and services: an especially dangerous combo.
This type of social engineering is similar to the “question quiz” phishing campaigns we analyzed last year. However, this new campaign is unique in that the fake sites were extremely well-designed visually, which assists in gaining the trust of the victim. By appearing as authentic and trustworthy as possible, the likelihood of a successful capture of a credit card number increases.
These phishing kits are growing in sophistication because the attackers are growing in sophistication. This campaign demonstrates the level of understanding the adversary has on the limitations of security products and the gaps in detecting phishing attacks. In this post, we will explore this new kit, why it is successful, and how we can avoid falling victim to scams like this one as we move into the busy holiday season.
Social engineering techniques
To make the scam more effective, a variety of social engineering tactics and techniques were used against victims to drive a sense of urgency and/or trust. When we have an emotional response to something, we are more likely to act with less attentiveness than we typically would. For example, one of the techniques pressured victims by making the offer time-sensitive (i.e., you have five minutes to answer the questions). This induces stress, which can cause us to overlook details we may have noticed otherwise. Other techniques included creating a fake users forum with fake testimonials from those who had “won” and “received the free prize” from the targeted retailer. This gives a false sense of security because we are accustomed to seeing these types of customer testimonials across the board.
Since this kit mimics multiple brands, an analysis of these fake customer profiles was imperative. The fake user “Natalie Hamilton” was recycled and/or slightly modified for the various scams (Figure 2) The prize review comments are customized, including images, and upon first glance appear genuine as winners gush about the prize. This all builds trust for the victim. Additionally, the profile pictures are altered between scams, so even if a victim was hit by multiple instances, the scam could still go undetected. What gives it away is the strong similarity of the comments across the prize offerings, which would likely go unnoticed by the average internet user.
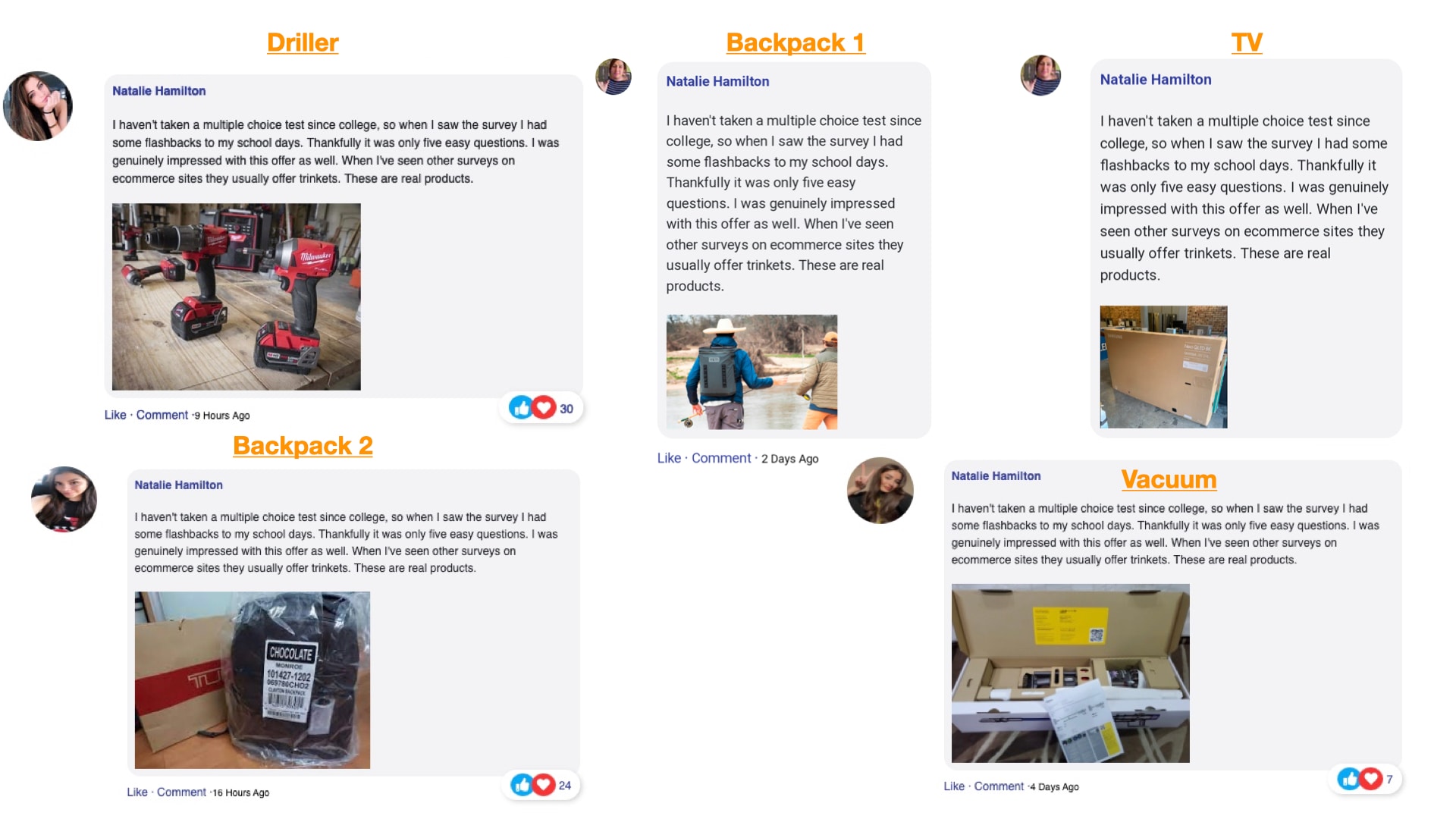
Fig. 2: Fake user “Natalie Hamilton”
Campaign infrastructure
Over the years, phishing products have improved significantly, which has led to a continuous evolution of the evasive techniques used by adversaries to have the upper hand. A large part of their success is keeping the kit active, which means evading detection. This was an important characteristic of this kit: The adversary used tactics that made the kit harder to classify, which allowed them to stay active, and even possibly victimize the same people again. Even once a phishing website was detected and classified as malicious, it still remained active. The adversary used a resilient infrastructure that enabled relaunching new variants of the attacks using the same or similar infrastructure.
In the core of the infrastructure being used, we were able to see a nested chain of redirections starting with the initial link delivered to victims via email phishing message, leading eventually to the landing page of the scam, the phishing website. Those nested chains of redirections are highly sophisticated and serve multiple purposes. Let’s look at some details of the techniques being used.
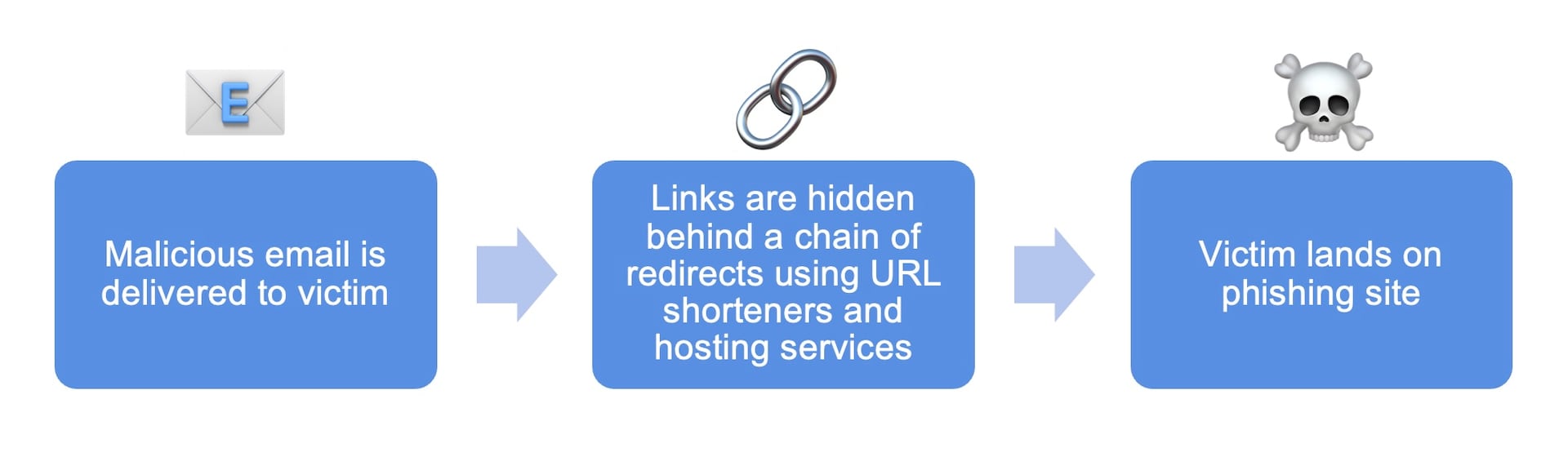
Fig. 3: Nested chain of redirections
Abuse URL shorteners
We internet users have become accustomed to URL shorteners, even trusting them to some degree, depending on the source. Services such as bit.ly or social media sites are so ubiquitous that we don’t even bat an eyelash at clicking on a link without seeing where it’s actually pointing. This is a core success tactic that this kit abuses.
The attack flow looks like this: The scam is delivered via email. In some cases, the adversary masks the destination with a URL shortener. This adversary has created fake LinkedIn profiles to create posts pointing to the malicious destination, which gives them the shortened URL used in the initial email to potential victims. The usage of URL shorteners to conceal the malicious URLs behind the phishing scam challenges security products that need to determine the risk involved with a given email link attachment. This campaign uses multilayered redirections, making it nested and flexible to changes, which make it harder to detect as malicious.
Abuse legitimate web services reputation
To increase sophistication, another optional hop in the redirections chain is the usage of a service provider to host scam redirection functionality. By utilizing various services, such as Google cloud storage, AWS hosting services and Azure blob storage, we highly suspect the attacker is piggybacking on their trustworthy reputation. This increases the chances of bypassing any anti-phishing mechanisms. We can also see that the images being used in the initial phishing email are also being hosted on some of those services with the same objective in mind.
Usage of URI fragment identifier redirection
The URL fragment identifier is a hash mark (#), also known as HTML anchor, in the URI link that points a browser to a specific spot in a page or website. This is a technique commonly used in tables of contents or other categorization lists for a better user experience. The values being after the HTML anchor will not be considered as HTTP parameters and will not be sent to the server, yet this value will be accessible by JavaScript code running on the victim’s browser. In the context of a phishing scam, the value placed after the HTML anchor might be ignored or overlooked when scanned by security products that are verifying whether it is malicious or not. This value will also be missed if viewed by a traffic inspection tool.
In this phishing campaign we were able to see a technique that we have never seen previously: using URI fragmentation not as an HTML anchor, but as an evasive action.
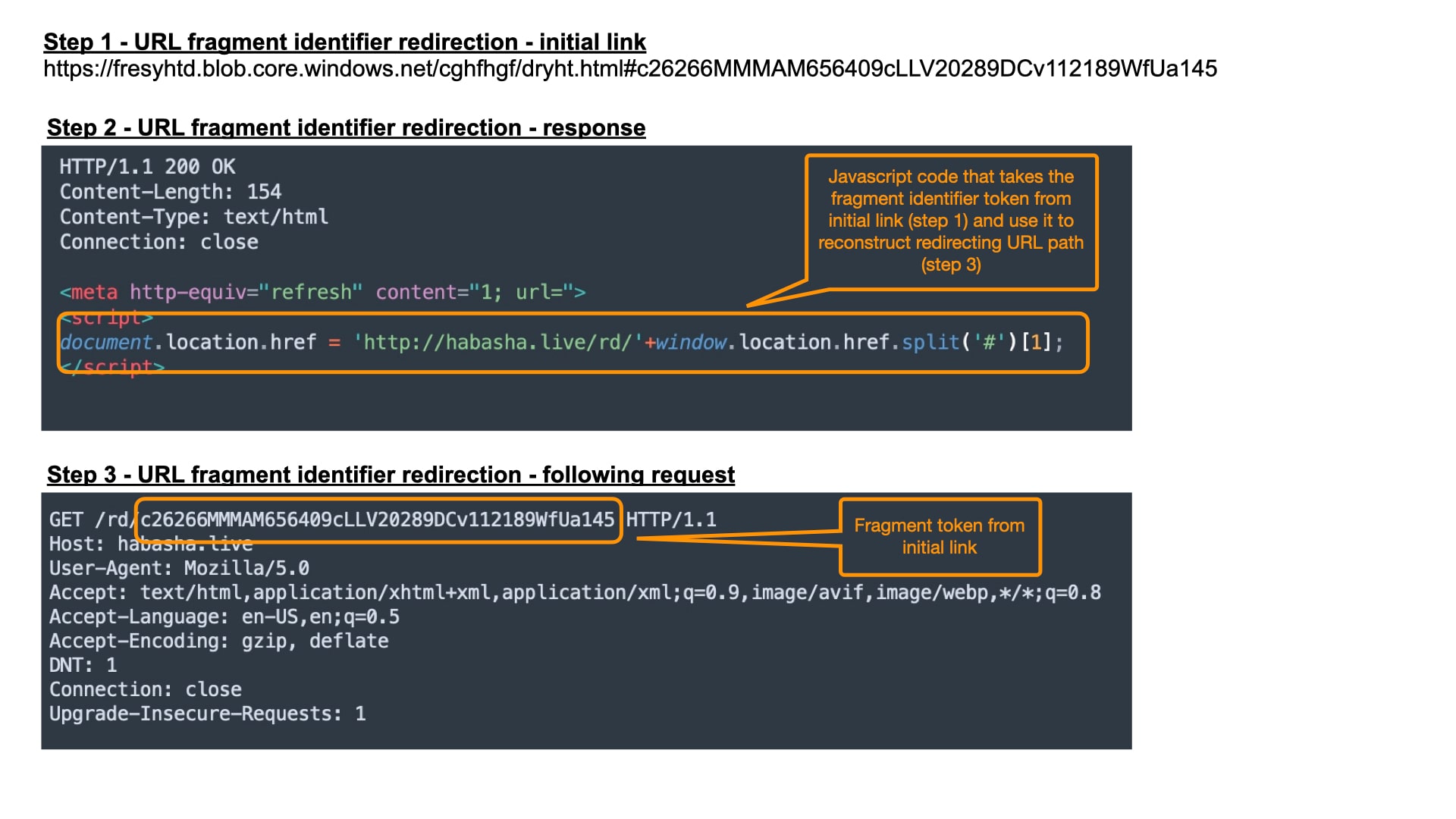
Fig. 4: URL fragment identifier redirection step-by-step
We can see that the initial link being sent to the victims’ email contains an HTML anchor followed by a token (Figure 3, Step 1). That token is later used by JavaScript on the victim’s browser to reconstruct a URI link to which that victim will be redirected (Figure 3, Step 2). Any access to a phishing scam without obtaining and using that token will be restricted from accessing the phishing landing page, meaning that visitors without the initial link will be filtered out. On top of that, browser-based access that is not running JavaScript as part of rendering of redirecting pages will also fail. In order to reach the malicious landing page, the browser must be able to construct the redirect URI. This is yet another direct measure taken to bypass security mechanisms, such as web crawlers that scan suspicious links and are not using headless browser capabilities.
The usage of tokens also enables the adversary to track victims and look for statistics on potential victims’ engagement. This would tell the adversary what is working and what is not, a method that could be used to make targeting more specific, which could increase the chance of success.
Usage of randomly generated URLs
One of the unique parts of this kit is how fiercely it protects who can access it. As part of the campaign effort to filter out unwanted visitors, the kit generates a random URL that is tied to a specific user as part of the chain of redirects. Upon landing on the phishing website, each allocated URL can only be used by the specific user.
Using this functionality enables adversaries to make sure that in case a randomly generated URL is reported as suspicious other users will not have access and, as a result, the website can stay under the detection radar.
Usage of the power of CDN
Similar to abusing web hosting services for their trusted reputation, the landing page of the scam uses some of the services being offered by a CDN vendor, including domain registration. The adversary utilizes quick and easy registration to easily spin up the instance, and then rotates phishing website domain names, both without the need to takedown the phishing website infrastructure. It also rotates IP addresses associated with the CDN and shared across different CDN customers — some might be considered legit and others might be considered malicious. This eliminates the option of blocking based on IP address as blocking might result in the false blocking of legit traffic. We also suspect that defensive CDN features, such as blocking bot traffic, are also in use to protect the phishing website from legitimate security crawlers and scanners.
GEO targeted campaign
According to our research, the landing websites are changing based on the victims geographic location, and some geographic locations are not prohibited at all. The campaign we tracked was mostly accessible from the United States, meaning the campaign was specifically targeting U.S. victims. We suspect that by limiting unwanted access the adversary also reduces the risk of the phishing website being detected by security products that are trying to access this website outside of the United States. That the same phishing link leads to different websites with different geographic customization emphasizes, yet again, the scale, efficacy, and level of sophistication of this campaign.
Akamai's global view validates our assumption of the campaign as being a geographically targeted attack: We can see that 89% of the victims landing on phishing scams are in the United States and Canada.
Summary
If the analysis of this kit teaches us anything, it’s why phishing scams are still so successful. Adversaries know mitigation tips, tactics, and procedures, and when paired with social engineering, it can be difficult (if not impossible) to detect, much less defend against, a kit like this. This blog post is not a dig at any security product or vendor’s efficacy — instead it showcases how even multiple layers of defense can be eroded to achieve a malicious purpose.
There has been a lot of discussion in the information security community about what makes a threat “sophisticated.” Is it how it infects? How it stays persistent? How it evades detection? Regardless of how you define sophistication, this kit qualifies. This kit comprises every element to be successful: the usage of commercial services, a flexible chain of redirects, geoblocking, and a fragmented URI token. Moreover, it is a reflection of the adversary’s understanding of how security products work and how to use them for their own advantage.
The information in this post also puts a spotlight on what guides adversaries to create an effective phishing campaign. It is not a zero-sum game. Just because a phishing kit is detected and mitigated does not mean the adversary was not successful. Success is better determined by a combination of the time the campaign remains alive and undetected, how realistic the scam looks, and the victim's level of engagement with the scam.
The level of sophistication of this scam is somewhat enabled by the usage of commercial services and that should be very concerning. Some of those public free-to-use services enable adversaries to successfully execute their malicious endeavors. Moreover, it’s disturbing to see successful campaigns using this level of infrastructure and advanced techniques in widespread attacks against consumers because these sophisticated targeted phishing attacks are even more challenging to defend against.
As we are just beginning the holiday season in the United States we expect to see more of these attacks to take advantage of the holiday spirit. We advise everyone to stay vigilant and safe. Remember: When you get an offer that is too good to be true, it probably is.
Associated IOCs
Redirecting links
https://bit{.}ly/3UQIwa0
https://lnkd{.}in/edDq4cs3
https://lnkd{.}in/etjsM9uZ
https://lnkd{.}in/e5F472JX
https://bit{.}ly/3SLisva
https://lnkd{.}in/eFnXm9CV
https://nmvcbndhrhasdfsdfasasdfadfdf.storage.googleapis{.}com/ubnxc
https://lnkd{.}in/eAYVYHUq https://dddddmqlkdsfjmlkjfapoieurpaoierqjkdfhlsdjfmklsdfkls.storage.googleapis{.}com/paerili
https://lnkd{.}in/ese6ta3F
https://lnkd{.}in/equr8wQQ
https://lnkd{.}in/equr8wQQ
https://fresyhtd.blob.core.windows{.}net/cghfhgf/dryht.html
https://ecstaticfoll.blob.core.windows{.}net/nsipidityrema/epesthadhusbandsher.html
https://hhhaggatt111.blob.core.windows{.}net/hhhaddafafrra11/newfile222.html
https://erty5h45fgds4j.blob.core.windows{.}net/dfgyhkjdhgfk/fgyh45hgjfghj.html
https://keroighzemhzrs.s3.amazonaws{.}com/ztgeipjmgfze.html
https://cxsdezda.s3.amazonaws{.}com/zsjverghi.html
cohgtdredajisfransi.s3.amazonaws{.}com/mobilise.html
https://lnkd.in/eKtXCivg
Phishing landing domains
opticshair{.}live
metalicanar{.}com
havocblume{.}com
fashionbrall{.}com
stirringglass{.}com
jetingsign{.}info
nauseaspinn{.}info
foresterdam{.}info
wharfposition{.}com
outstriplander{.}live
qualiagolf{.}info
kimonosuit{.}info




