The Race to Patch: Attackers Leverage Sample Exploit Code in WordPress Plug-in

Editorial and additional commentary by Tricia Howard
Executive summary
The Akamai Security Intelligence Group (SIG) has been analyzing attack attempt activity following the announcement of a critical vulnerability in a WordPress custom fields plug-in affecting more than 2 million sites.
Exploiting this vulnerability could lead to a reflected cross-site scripting (XSS) attack, in which malicious code is injected into a victim site and pushed to its visitors.
On May 4, 2023, the WP Engine team announced the security fix in version 6.1.6, including sample exploit code as a proof of concept (PoC).
Starting on May 6, less than 48 hours after the announcement, the SIG observed significant attack attempt activity, scanning for vulnerable sites using the sample code provided in the technical write-up.
This highlights that the response time for attackers is rapidly decreasing, increasing the need for vigorous and prompt patch management.
Introduction
The widespread usage of web applications, APIs, and other third parties has dramatically increased the attack surface and exploit impact in that vector. The more complex environments become, the more ground attackers have to exploit — often with a low barrier to entry.
A recent example of this was exhibited earlier this month with a critical vulnerability affecting a WordPress custom field plug-in. Within a number of hours following the company’s announcement of the vulnerability and the associated patch, we saw increased XSS activity. One, in particular, stood out: the PoC query itself.
As an example, we will examine a sample scanning actor that our team monitored after the vulnerability was posted. In the immediate 48 hours after the details were published, we saw a significant amount of scanning activity. This is consistent with attacker activity we’ve seen in other zero-days as well.
It is becoming increasingly more common for attackers to “leverage the knowns” even more deeply than before (such as abusing a holiday sentiment or a trend such as cryptocurrency). Let’s examine the initial vulnerability, the actor we observed, and the traffic we analyzed.
The initial vulnerability
The vulnerability assigned CVE-2023-30777 was originally discovered in May of this year with a CVSS base score of 7.1. Exploitation of this leads to a reflected XSS attack in which a threat actor can inject malicious scripts, redirects, ads, and other forms of URL manipulation into a victim site. This would, in turn, push those illegitimate scripts to visitors of that affected site. This manipulation is essentially blind to the site owner, making these threats even more dangerous.
With more than 2 million active users of the plug-in, the impact of this vulnerability made headlines when the exploit PoC and patch were released. A detailed write-up on the findings, including example payloads (Figure 1) was published on May 5, 2023 by Patchstack, a WordPress security company, following their responsible disclosure.
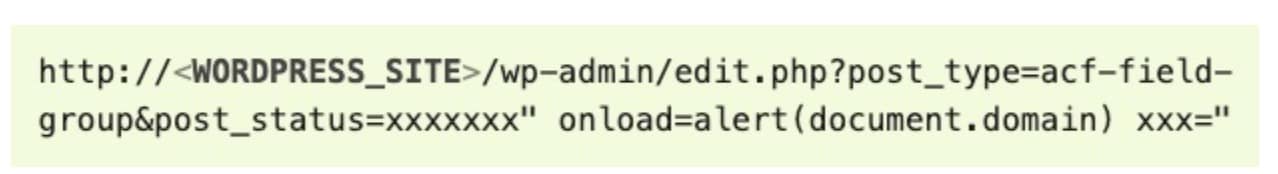 Fig. 1: CVE-2023-30777 attack vector image from Patchstack
Fig. 1: CVE-2023-30777 attack vector image from Patchstack
The observed active exploitation
Once exploit vector details are publicly released, scanning and exploitation attempts rapidly increase. It is common for security researchers, hobbyists, and companies searching for their risk profile to examine new vulnerabilities upon release. However, the volume is increasing, and the amount of time between release and said growth is drastically decreasing. The Akamai SIG analyzed XSS attack data and identified attacks starting within 24 hours of the exploit PoC being made public.
What is particularly interesting about this is the query itself: The threat actor copied and used the Patchstack sample code from the write-up.
You can see the monitored activity in Figure 2 — a screenshot from Akamai’s Web Security Analytics dashboard that shows vulnerability scanning activity for this actor. This activity spanned all verticals without distinction. This breadth of activity and the complete lack of effort to create a new exploit code tells us the threat actor is not sophisticated. The actor was scanning for vulnerable sites and attempting to exploit an easy target.
 Fig. 2: Web Security Analytics’ screenshot showing XSS attacks
Fig. 2: Web Security Analytics’ screenshot showing XSS attacks
Recommendations and mitigations
Akamai App & API Protector customers can stay calm as they are already protected against this zero-day by the XSS attack group. To ensure safety, we recommend you have the full group in deny; however; if that is not feasible, please make sure at least the following rules are in deny:
3000111 - Cross-site Scripting (XSS) Attack (Common PoC Probes 1)
3000110 - Cross-site Scripting (XSS) Attack (SmartDetect)
3000081 - Cross-site Scripting (XSS) Attack (Attribute Injection 2)
3000039 - Cross-site Scripting (XSS) Attack (DOM Document Methods)
3000037 - Cross-site Scripting (XSS) Attack (JS On-Event Handler)
958052 - Cross-site Scripting (XSS) Attack (Common PoC DOM Event Triggers)
For customers without App & API Protector, the most effective mitigation is patch management. We urge WordPress owners with the vulnerable versions to deploy recent patches as quickly as possible.
Summary
Patch management is a critical part of an organization’s security and risk-reduction strategy. As was demonstrated here, the rate of exploitation of emerging and recently disclosed vulnerabilities remains high — and is getting faster. Attackers often exploit trends within the first 24 to 48 hours of public announcement, leaving practically no time for proper mitigations to be applied, even in the most robust security ecosystems.
This highlights the need for proper tooling to provide real-time visibility and mitigation options for these types of attacks. Web application firewalls provide security teams with needed protections to prevent attacks, while security patches are applied to web applications.
The Akamai SIG will continue to monitor this activity and provide valuable insights to our customers and the community at large. For more real-time information on vulnerabilities and other breaking security research, follow us on Twitter.


