Chatbots, Celebrities, and Victim Retargeting: Why Crypto Giveaway Scams Are Still So Successful
Editorial and additional contributions by Tricia Howard

Executive summary
Akamai researchers have been monitoring several cryptocurrency giveaway scam kits that impersonate celebrities and brands, notably Elon Musk and his associated companies. The scams are delivered through various social media platforms as well as direct messaging apps such as WhatsApp or Telegram.
The kits leverage myriad social engineering techniques to ensure success, such as countdown timers, live chat functionality, and bots for “ease of entry” to the “giveaway.”
Based on IP address, the majority of the kits seem to originate from Russia and other parts of Europe.
Some of the kits had a feature to send notes back to the attacker with information about the victim as well as the site they visited.
Although the technical specs of most of these kits are relatively simple, the level of detail on multiple angles of these scams reveals why crypto scams continue to remain profitable.
Introduction
The fight to stop phishing and other scams has been ongoing for many years. From sweethearts to the IRS, the victims may change, but the underlying principles of scams remain the same now as they were 20 years ago. Phishing victims are exploited by those willing to take advantage of current events, personal situations, and emotional responses.
Despite extensive public awareness, these scams continue to work. The damages of crypto fraud alone have exceeded $1 billion since 2021, and we can expect to see more as crypto becomes more societally ingrained.
For several years cryptocurrency and social media have been fertile ground for scammers to exploit. Threat actors can create fake accounts to impersonate brands, celebrities, and other people of note. We have analyzed a set of scam kits that have been successful in stealing crypto from hopeful victims by impersonating people and brands, and we’ve put together a list of things you can do to avoid becoming a victim of a crypto giveaway scam. In this post, we will also explore these scam kits from a technical perspective to foster awareness.
What are crypto giveaway scams?
Crypto giveaway scams are a form of fraud that leverages social media and phishing campaigns to gain crypto-enthusiasts’ trust with the promise of high-yield giveaways. A common way is to impersonate notable figures with significant financial resources, such as Elon Musk, who has a large following and a known presence within the crypto community.
Several actions help make these scams seem legitimate: from factoring in the popularity of the coin at the time to leveraging known names and brands illegitimately, all the way to hijacking YouTube accounts, creating fake coins, and even holding face-to-face meetings.
How do crypto giveaway scams work?
Although the delivery medium varies, the base method of the scam is the same: lure a victim to the kit site and convince them to transfer crypto to the scam wallet.
Delivering the scam
These scams are delivered in varying levels of elaboration. The most common way is through social media platforms like Twitter, Telegram, and YouTube. This tactic, along with the social engineering strides the attackers take, allows them to reach a large audience and increase their chances of successful attacks.
The idea is to build enough trust with the intended victim that the victim does not try to independently verify that this is legitimate.
You can see an example of this in Figure 1.This screenshot makes it seem as if the person being impersonated (Musk) legitimately endorsed the link the scammer is pushing. A quick look at the Twitter account would prove this untrue, hence the effort to keep the intended victim(s) from taking that action.

Fig. 1: Fake screenshot of tweet feigning legitimacy of crypto scam
It is also common practice for scammers to reply to long threads initiated by the legitimate entity as a means of gathering potential victims. Even if the initial tweet had nothing to do with crypto, since the impersonated entity has a known stake in crypto, it stands to reason their followers could also have that interest. Replying to a legitimate tweet serves two purposes: wide dissemination by leveraging their large following and feigning association with said entity (Figure 2).
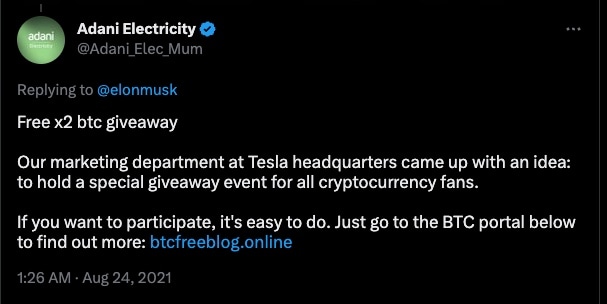
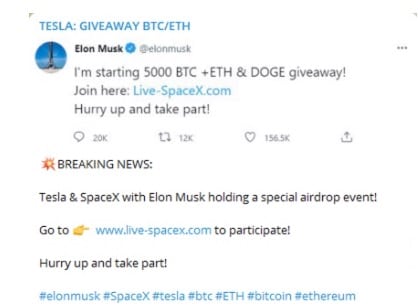
Fig. 2: Examples of tweets that further the scam
It is also common to see these scams delivered through direct messaging platforms, such as WhatsApp or Telegram. There are large groups with various interests on these apps, and crypto is a popular subject. Attackers infiltrate these groups and post the scam links while posing as a participant, the associated celebrity, or someone close to the associated celebrity (Figure 3). These can look quite legitimate; some of them even have bots built for “ease of entry.”
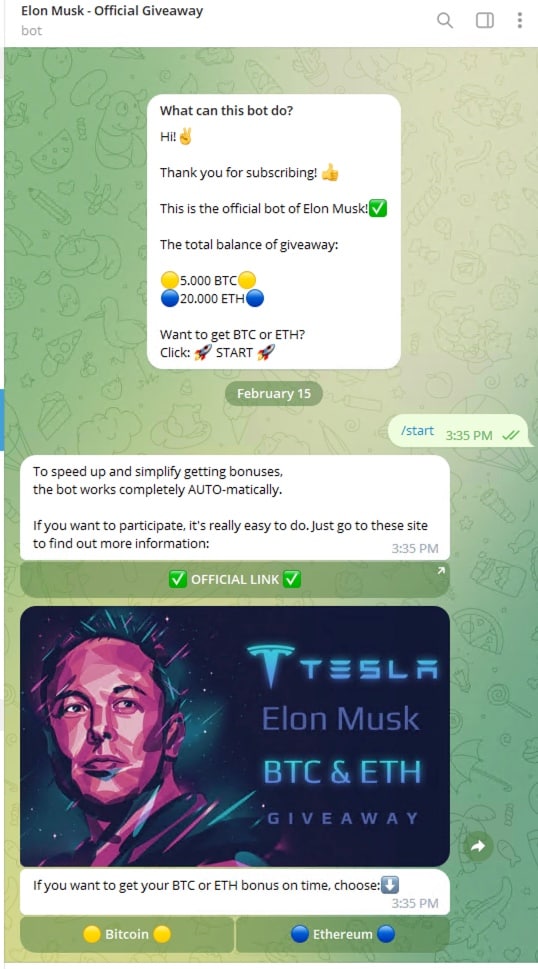
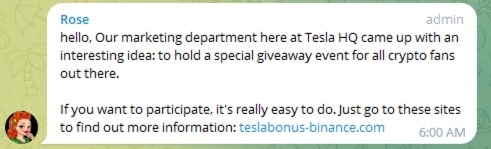

Fig. 3: Examples of scams delivered through WhatsApp and Telegram
Scam kit sites
Through social engineering and a promise of a large sum of cryptocurrency, nefarious actors have made these scams quite lucrative. The attackers leverage industry knowns such as coin popularity, celebrities or other known figures, and affiliation with specific organizations to create highly realistic phishing kits (Figure 4).
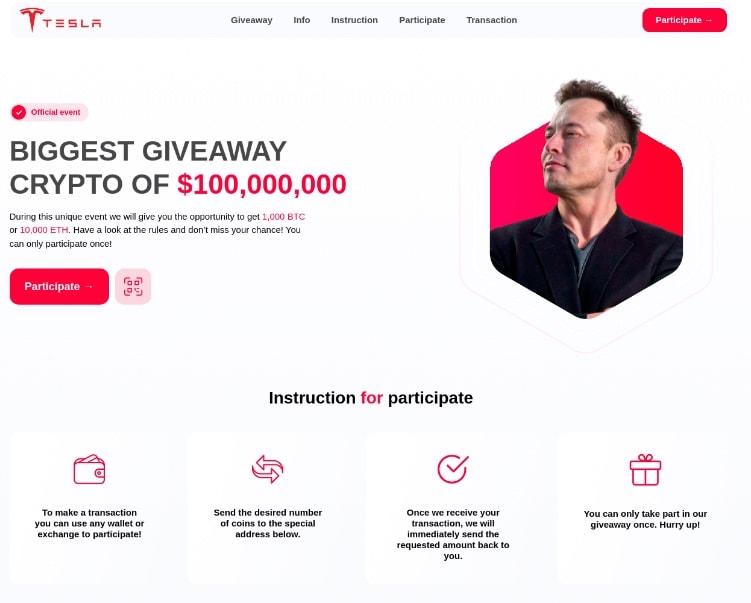

Fig. 4: Example of crypto scam kit site
These sites are engineered to build trust with the person who comes upon them. As you can see in Figure 4, minus mildly broken English, the sites look legitimate. This is a far cry from the plain-text email scams of the past; these kits even have live chatbot “technical support” to help users “enter the contest.”
Between the visually pleasing mimicry of legitimate marketing campaign landing pages, the FOMO-incurred pressure of the “real-time countdown timer,” and the relevant celebrity “endorsement,” the level of detail to ensure the success of the scam is indicative of how lucrative they are.
A seasoned individual may recognize a scam right away. Still, it would be easy for the average social media user to fall for it. The scam itself is designed to build trust. The kit requires “authentication” to ensure a person only enters the contest once. The victim sends crypto under the guise of being immediately refunded once the authentication phase is complete. The attacker then takes their money and moves on to the next victim once this has occurred.
Technical analysis from one of the scam kits distributed on the dark web
Although the look and feel of these kits are very sleek, the code behind them is pretty straightforward. The kits we observed had some variance in the feature set, but they all were relatively simple on the backend. They contain a mix of HTML and JavaScript, with the following elements:
A script that initializes and sets up the Smartsupp Live Chat service on the website (Figure 5)
Two hidden inputs that contain the values of Bitcoin and Ethereum addresses
HTML elements for styling and display purposes, including an iframe displaying a cryptocurrency widget from “coinlib.io” providing some form of authenticity to the page showing live data
Some of the analyzed kits also include the collection of the victim's information and a push to a Telegram channel owned by the attacker. This is likely a method for re-targeting the victim with additional scams.
 Fig. 5: A Smartsupp widget
Fig. 5: A Smartsupp widget
 Fig. 6: Code of a Telegram bot
Fig. 6: Code of a Telegram bot
As you can see in Figure 6, the attacker uses IP API information attribution and pushes it to his Telegram bot. Notice the message in Russian, which translates as “Visited to Tesla website.”
We looked into the Bitcoin and Ethereum addresses included in the kit, which were likely used to receive payments from victims. As you can see in Figures 7 and 8, the wallets show multiple small transactions of accepted funds for a total 0.3 BTC (0.31 ETH at the time of verification).
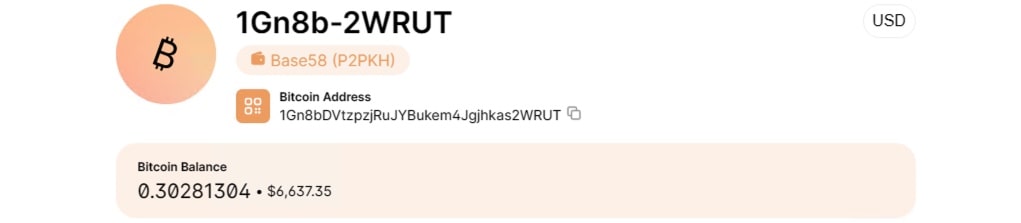 Fig. 7: Screenshot of bitcoin wallet from the crypto scam kit
Fig. 7: Screenshot of bitcoin wallet from the crypto scam kit
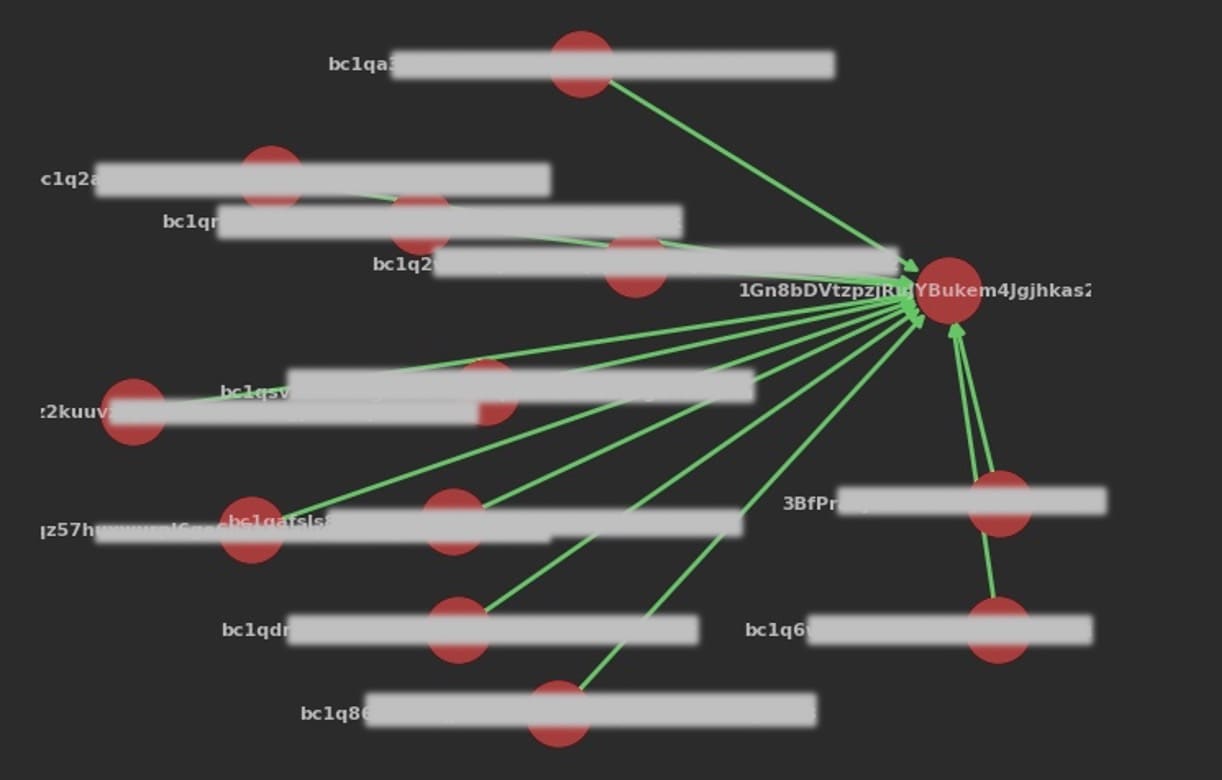 Fig. 8: Visual representation of multiple crypto transactions into scam wallet
Fig. 8: Visual representation of multiple crypto transactions into scam wallet
The presence of the Smartsupp Live Chat service is a feature that has gained popularity in recent months with these scam kits. It is used to (falsely) indicate that the website owner is attempting to provide customer support, which may build trust with users. Even if the victims don’t use the service, its presence alone subconsciously builds trust. It is a regular practice to have chatbots or live chat as a touchpoint for site visitors nowadays, so it would likely seem suspicious if an organization purporting to be Tesla didn’t have something similar on the site. This is especially true if the intended victim had visited a legitimate site, which does have a chat feature.
Another particularly interesting element of some of these kits is the sending of the victim’s information back to the attacker, with a note of what site was visited. This could mean the attackers are running multiple scams and are looking to “build a customer base.” They could then re-target these victims with other scams or pass their info along to other nefarious actors. Additionally, they could track these scam sites to see which are the most lucrative. These scams rely on mimicking legitimate marketing practices, so it stands to reason they would mimic this one as well.
Attackers' kits spotted in the wild
According to their IP addresses, most of the scam kits we observed were from Europe, with a concentration in Russia (Figure 9). Although this method does not confirm where the attacks are originating, it correlates with other cyber activity we have observed in this region. There were also several, which seem to be in the Netherlands, Austria, Italy, Germany, and Ukraine, which we gleaned from our internal data sources and popular scanning tools such as Shodan.io.
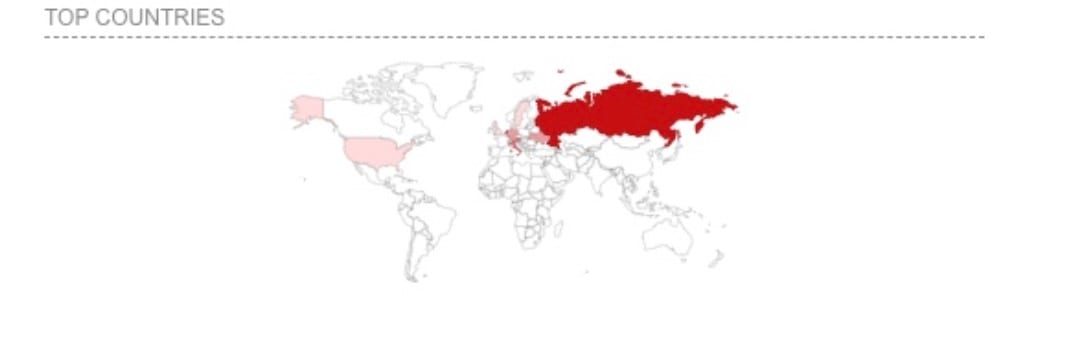 Fig. 9: Most of the scam kits we observed were from Europe, with a concentration in Russia
Fig. 9: Most of the scam kits we observed were from Europe, with a concentration in Russia
Sample of the kit in action
https://tesla-show{.}net
https://elongivex{.}space
https://teslaevent{.}tech
https://tesla-m{.}com
https://spaceX-crew6{.}com
How to avoid becoming a victim of a crypto giveaway scam
These scam kits will continue to surface as long as they are successful. Vigilance against these illegitimate sites is the only way to ensure you don’t become a victim. Being able to spot crypto giveaway scams, like those in Figure 10, is a critical tool in your arsenal. There are several red flags that can help you.
There are NO free gifts! Exercise extreme caution when encountering any site purporting to give something away for free. Even on legitimate sites, there are no truly free gifts. If it sounds too good to be true, it is.
Don't send cryptocurrency to anyone you don’t know: If someone on social media promises you a reward in exchange for cryptocurrency, don't send them anything. It's likely a scam.
Check and double-check the verification status of an account: Recent changes surrounding verification on Twitter have made it more difficult to discern a legitimate entity from an illegitimate one on the platform. The blue checkmark alone is insufficient, but it’s a good place to start. You can read more about Twitter’s verification policy on their website.
Check the username: A quick search for the impersonated celebrity + “social media” will yield the official account. If the official account’s username differs from the one interacting with you, the one you're dealing with is fake.
The account is new: Celebrities have had active social media accounts for years. If the account you're seeing is brand new, it's likely a fake.
Do your research: Legitimate giveaways do exist, but It’s always best to verify. A legitimate giveaway from an entity of this size would have multiple press releases and articles announcing it. If not, it’s likely a scam. You can also look up the account or phone number on Google and see if other people have reported it as a scam.
If you come across a giveaway scam, report it to the platform and to the authorities. By reporting the fraud, you can help prevent others from falling for it.
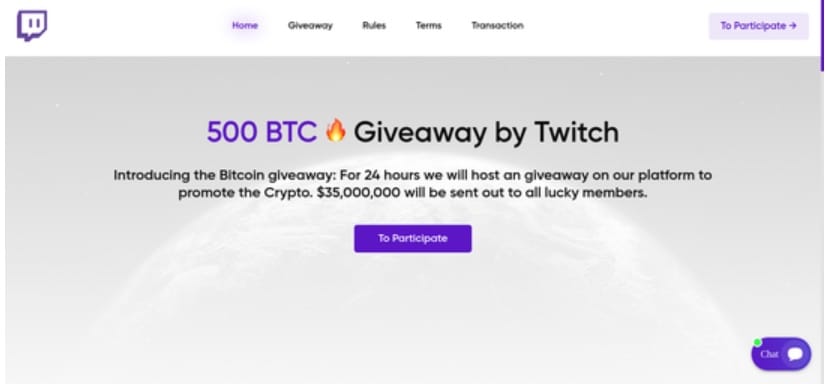



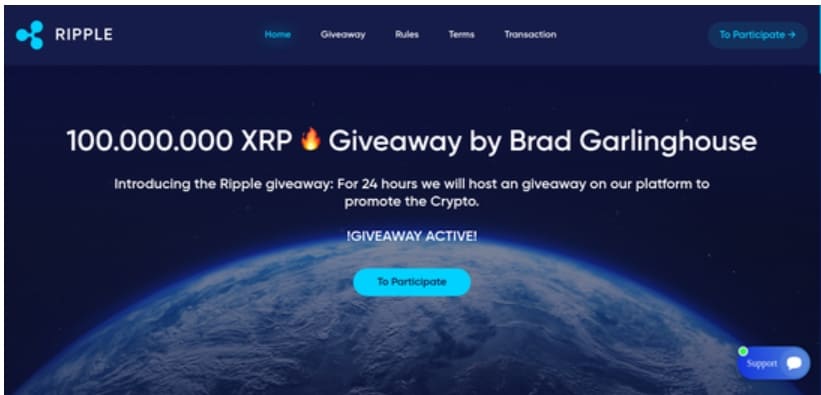
Fig. 10: More examples of crypto scam pages
Conclusion
Giveaway scams are a growing problem on social media. They hit on two major emotional elements: FOMO (the fear of missing out) and the prospect of significant, possibly life-changing financial gain. When paired with extensive social engineering tactics, these scams can cause people to ignore teachings about online vigilance.
However, under scrutiny, these kits can be relatively easy to spot. Staying educated about new methods and measures that threat actors are employing is critical to avoid falling for these scams and to keeping your cryptocurrency safe. Remember: If it seems too good to be true, it is!
Learn more
Akamai researchers are constantly looking for these types of scams and other malicious activity. To keep up with breaking research across all security domains, follow us on Twitter.


