Analyzing Malicious CrowdStrike Domains: Who Is Affected and What Could Come Next
Editorial and additional commentary by Tricia Howard
Copy edited by Maria Vlasak
Executive summary
Following the July 19, 2024, CrowdStrike incident, Akamai researchers uncovered more than 180 newly created malicious domains purporting to assist with navigating the incident, and that number continues to grow.
We identified the top trafficked malicious domains associated with the CrowdStrike incident and have developed a list of indicators of compromise (IOCs) for block list consideration or to analyze further on your own.
One of the malicious domains observed here was ranked in the top 200,000 sites for associated keywords.
Nonprofit and education were among the top industries affected, collectively composing more than 20% of the observed attack traffic.
In this blog post, we explore some of the types of scams that are currently active and look into who is being targeted, and we provide mitigation tips for both organizations and individuals affected by this incident.
Introduction
On Friday, July 19, 2024, the world buzzed with the manifestation of blue screens across a majority of devices after a recent CrowdStrike Falcon content update. The update triggered bug checks on Windows hosts that induced a global sea of blue screens of death (BSODs) — causing billions of system outages across various locations.
With 8.5 million devices affected globally, just about every industry was hit by this outage, including critical services such as aviation, government, and healthcare, which produced real-world impacts, some continuing even days after the incident.
As is often the case with newsworthy events, threat actors immediately attempted to exploit the situation by piggybacking on the widespread confusion and disruption caused by the update. The extent of the outage, tied with the extent of the news coverage surrounding it, led to a number of disconcerted users searching for answers wherever they could find them.
Threat actors take advantage
Threat actors saw this incident as a prime opportunity for social engineering — they rapidly set up scam sites that targeted impacted CrowdStrike customers to steal information and spread malware.
By analyzing the data we saw on our worldwide edge network, we identified the top malicious domains being used for scams surrounding this incident (Figure 1). The threats we’ve already seen span disciplines, including wipers, stealers, and remote access tools (RATs).
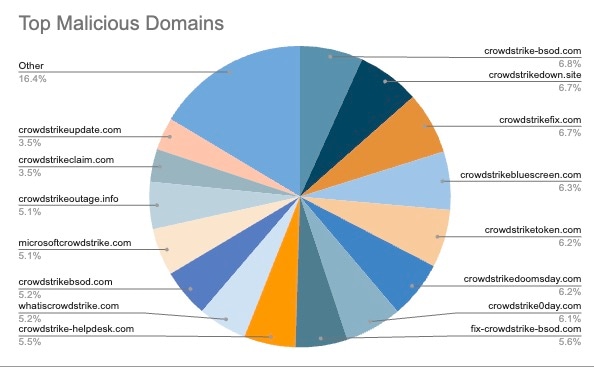 Fig. 1: Top malicious domains purporting to be associated with CrowdStrike assistance
Fig. 1: Top malicious domains purporting to be associated with CrowdStrike assistance
Each of these top domains had roughly equal market share. The majority of these domains have the [.]com top level domain, which holds a subtle air of legitimacy because of its ubiquity. Common keywords, such as “bsod” and “microsoft,” are present in several of the domains — these keywords are common ancillary search terms a knowledge-hungry victim would have turned to for information gathering.
Everyone is potential prey
The broad spectrum of the incident is best displayed by the lack of industry focus across the attack data (Figure 2). We found it surprising that some of the industries that were heavily affected by this incident are not often the targets of cyberattacks, notably education and the public sector.
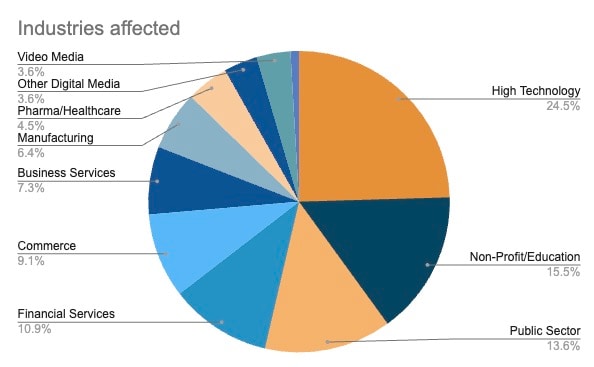 Fig. 2: Attack data breakdown by industry
Fig. 2: Attack data breakdown by industry
Nonprofit and education: Unfortunate targets
Although we are accustomed to seeing high technology and financial services bear the brunt of zero-day attacks, the nonprofit and education sector and the public sector, which compose more than 29%, stand out here. This industry is also greatly affected in terms of remediation — the number of managed devices for students on a single campus can be in the thousands, depending on the size of the institution.
The education sector also relies on people with a wide variety of technical skill levels, including people who are not tech savvy at all. Despite increasing IT budgets, the often small security team at an education institution has a seemingly Sisyphean task in trying to protect these environments. An attacker with social engineering experience would be aware of this deficit and may take advantage of it, which could also contribute to the high amount of traffic.
Identifying phishing infrastructure by campaigns
It is common for these phishing campaigns to be part of a resilient infrastructure if they are orchestrated by professional threat actors with the skills to rival an enterprise environment. These more sophisticated campaigns can have failover and obfuscation mechanisms and quickly change appearance: One of the observed domains in this campaign is tied to a known malicious source that took advantage of pandemic hardship.
In addition, many of these sites have built-in trust-building activities that users are accustomed to associating with security, such as SSL validation or IT support. As of the publication date of this blog post, more than 180 different domains have been identified, all registered between July 19 and July 21. That number will likely increase as the remediation process continues.
Top domains affected
The impact of these sites is remarkable, which is evidenced by how much traffic points to them. These sites garner millions of views, some even ranking in the top 200,000 domains for associated keywords globally for the period, according to AkaRank.
We analyzed some of the most trafficked domains to see their modus operandi and we’ve grouped together some of the sites on the basis of the ways they feign legitimacy: fake IT services, fake solutions, and fake legal support. Note: Some more advanced examples of these malicious sites also include other deceptions, including “phone support” or redirecting to the actual CrowdStrike site, building further credibility with the unsuspecting user.
Fake IT services
After the CrowdStrike outage, we noticed that several domains were created that were typosquats of CrowdStrike, containing the word “crowdstrike” in their domain names. These domains claimed to provide technical support for the issue for victims who contact them (Figure 3).
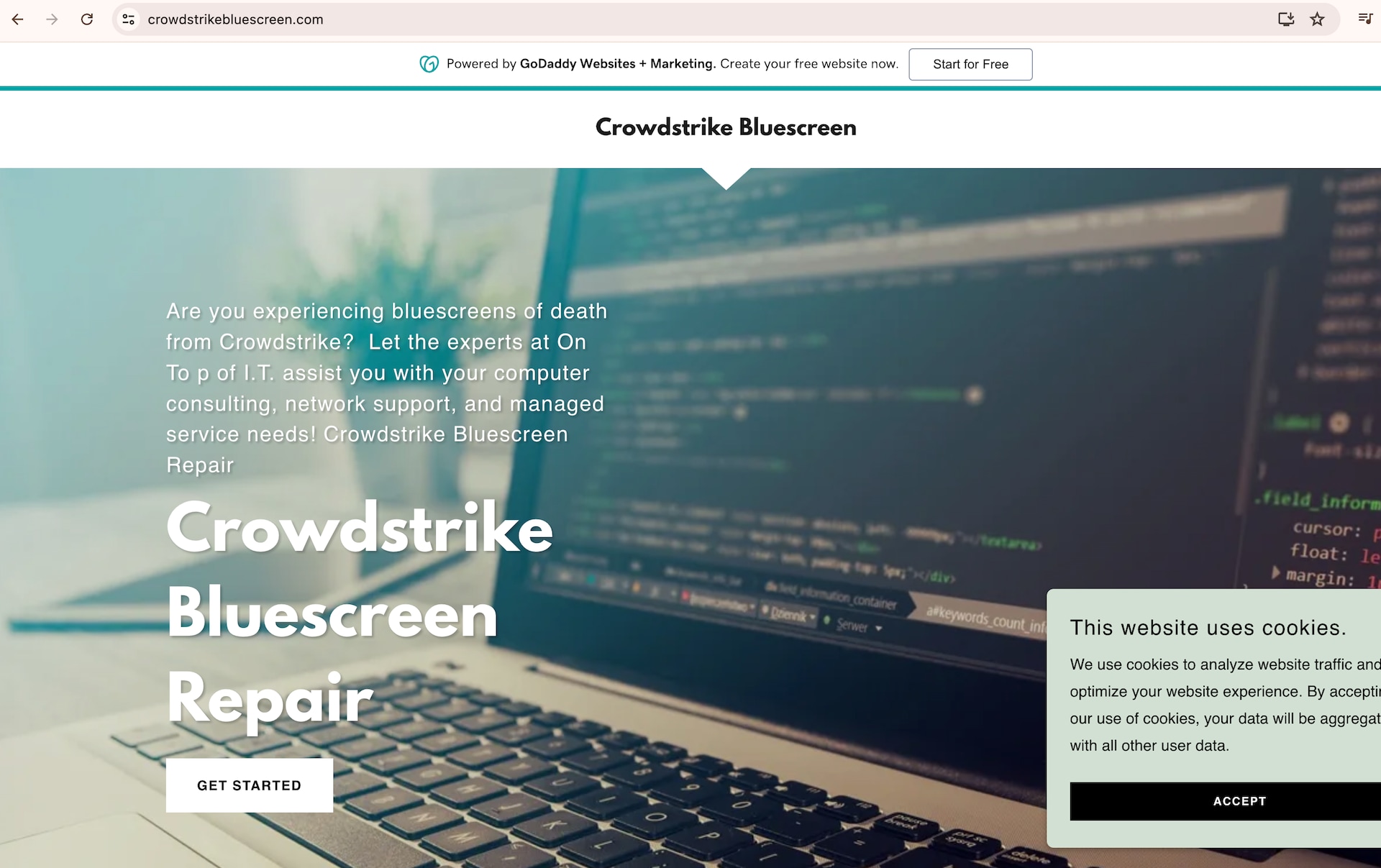 Fig. 3: Example of fake services scam
Fig. 3: Example of fake services scam
This type of scam site pretends to be IT professional humans available to aid in quick recovery — and they have an equal level of urgency in tone. The sense of emergency may entice the visitors to provide personal information, which is a common characteristic of a phishing setup. The goal here is to steal sensitive information directly from user input.
Fake solutions
For the victims who are looking for a quick fix without human assistance, we have the fake solution campaigns (Figure 4). These campaigns focus on quick fixes provided by fake repair scripts or executable files that can be downloaded with a click of a button.
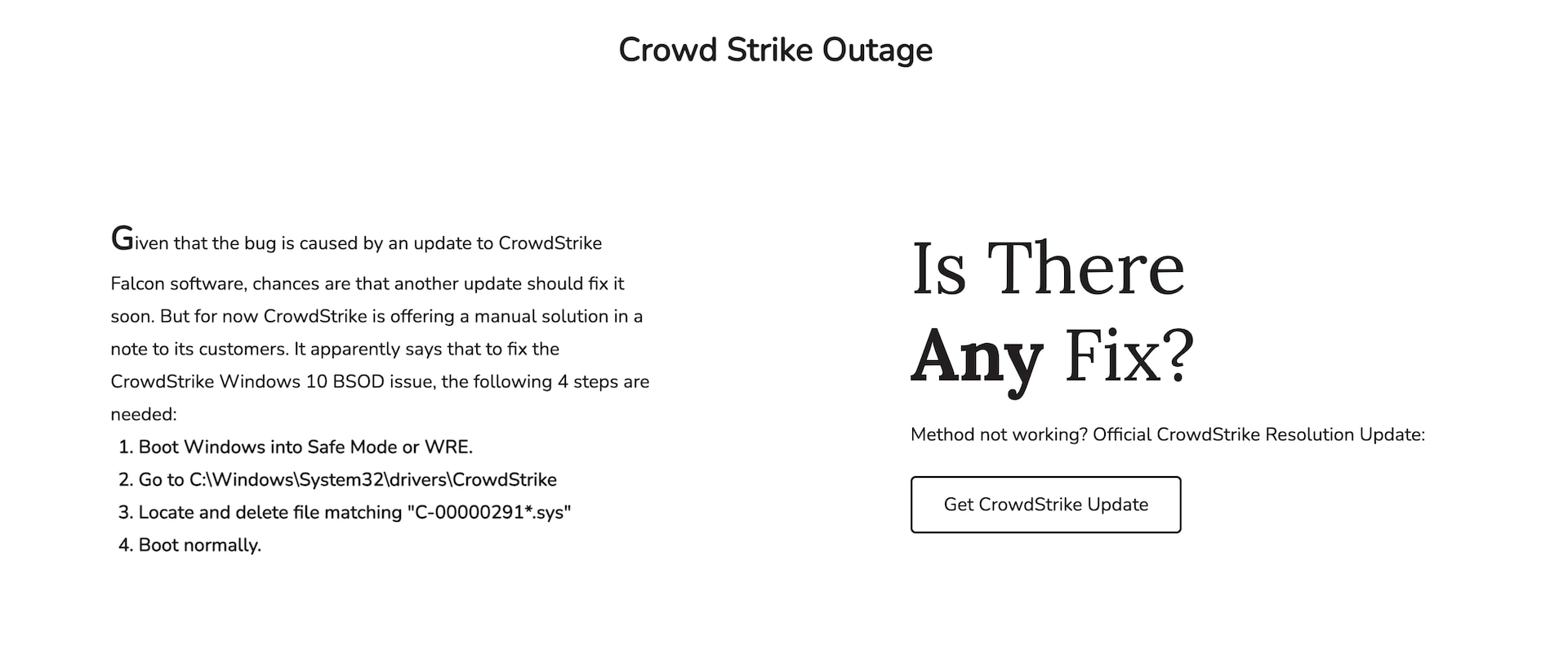 Fig. 4: Screenshot of a fake solution campaign
Fig. 4: Screenshot of a fake solution campaign
A quick read of the instructions makes it seem like a legitimate fix. The files are named “CrowdStrike,” they mention the current issue, and provide a reasonable number of steps. An unsuspecting victim who is looking to get back to work could easily introduce malware into their environment on their own.
Fake legal support
Not all the malicious campaigns focused on the technical aspects — some went the litigious route. These campaigns attempted to collect personal information from users under the guise of offering legal assistance related to the CrowdStrike outage. The landing page in the example in Figure 5 contains the logos of a legal firm and of CrowdStrike to increase its reliability.
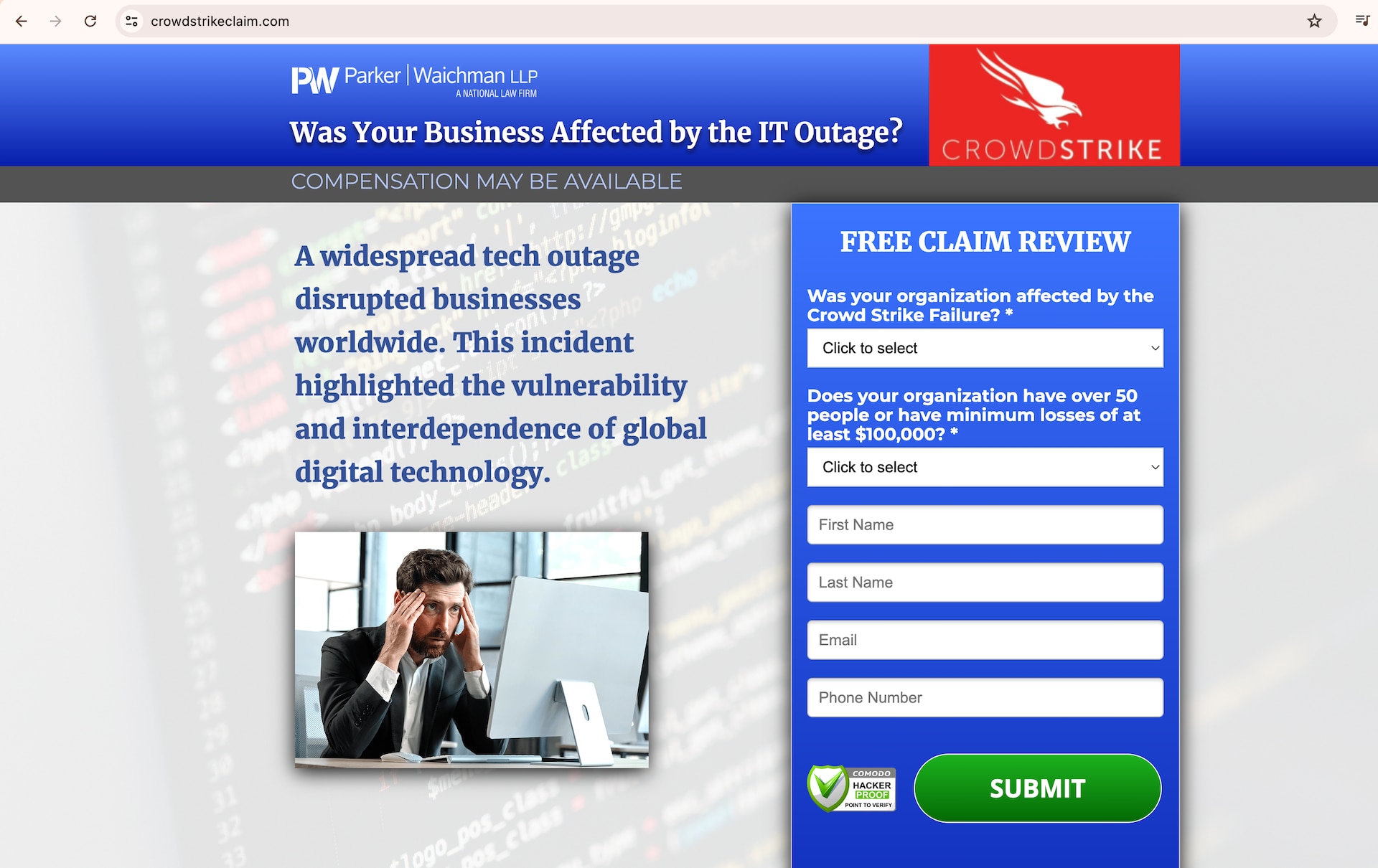 Fig. 5: Malicious legal phishing site
Fig. 5: Malicious legal phishing site
This particular IOC (crowdstrikeclaim[.]com) stood out because it is likely part of a widespread phishing infrastructure. The Akamai Security Intelligence Response Team was part of this analysis and identified this domain as having an embedded Facebook ID known to be malicious — one that used to link to covid19-business-help.qualified-case[.]com. That site, in turn, has another embedded Facebook ID that links to approximately 40 other websites.
Mitigations
If you are affected by the outage and are looking for information, we recommend that you consult credible sources such as CrowdStrike or Microsoft. Although other outlets may seem to have more up-to-date information, it may not be accurate — or worse, the site may have a malignant purpose.
For individuals
If you find yourself on a page that claims to offer assistance with the CrowdStrike outage, there are a few ways you can check legitimacy.
Check the certificate and issuer of the domain when accessing over HTTPS
Know that the domain is likely illegitimate if it requests sensitive information, such as credit card numbers, social security numbers, or banking information
Only follow recovery information directly from CrowdStrike
Do not open email attachments that claim to be able fix the issue, even if they arrive from domains that resemble CrowdStrike
For organizations
Security professionals who are dealing with the effects of this incident also have a few ways to help remediate and limit further exposure.
Perform a lateral movement gap analysis or adversary emulation. Threat actors with financial aspirations will find more opportunities to drop ransomware into an environment. Although this wasn’t a CVE to be exploited, there are potential technical impacts from a threat actor who knows a critical piece of your security stack. We recommend a gap analysis or even an adversary emulation to get a current view of your threat landscape.
Block known and related IOCs. There are a number of credible intel sources of known IOCs associated with this campaign, including this list we built. If this list is consistent with your own risk management analysis, block the domains outright, or even DNS sinkhole them, to stop communications with malicious domains.
Conclusion
It is likely we will see more phishing attempts associated with this issue beyond the time when every device is remediated. A simple scroll through social media can provide an attacker with a sense of which brands generate the most heightened emotions and which are ripe to impersonate for malevolent gain.
This is an attacker’s job, and it’s important to remember that. Malicious campaign operations function just as we do in legitimate corporations: The victims are their “customers,” and the varied tactics presented in this post show how “plugged in” to their customers they are. They know how to effectively diversify their portfolio to ensure they end up with money in the bank.
Future effects
It is also notable that due to the public nature of this incident, attackers now have a better understanding of certain targets’ tech stacks. This could become relevant in the event that a future CVE is discovered within the Falcon product. Attackers are only getting more sophisticated, and each additional piece of the tech stack puzzle they have makes that puzzle easier to solve.
Want to learn more?
The Akamai Security Intelligence Group (SIG) will continue to monitor and report on threats such as these to provide intel to our customers and the security community at large. For a full list of the work happening at SIG you can check out our dedicated research page or follow us on X, formerly Twitter, for the most real-time updates.





