Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
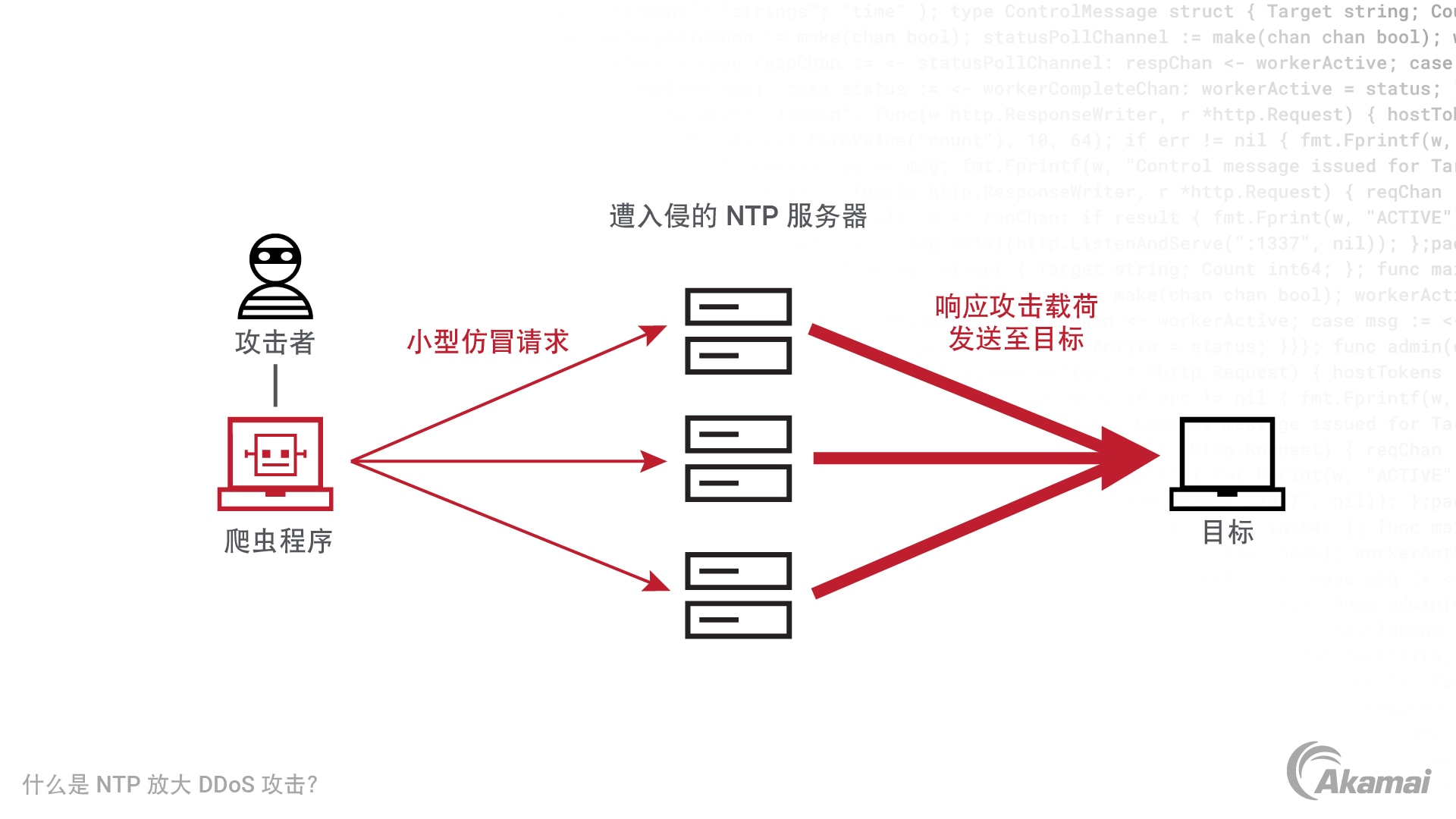
An Network Time Protocol (NTP) amplification attack is a type of distributed denial-of-service (DDoS) attack in which an attacker spoofs their own IP address to send a request to a vulnerable NTP server, resulting in the server responding with a much larger response than normal. This is then amplified and sent to the victim, flooding their servers and causing them to slow down or crash completely.
The objective of an NTP amplification attack is to inundate the target’s internet resources with an overwhelming amount of traffic. This is achieved by exploiting an NTP server that has been incorrectly configured, allowing external sources to directly access it. By spoofing the IP address of the victim and leveraging a network of compromised bots, attackers can access a list of open NTP servers to initiate the attack. This results in a significant surge of User Datagram Protocol (UDP) traffic directed toward the victim’s network. Such attacks pose severe consequences for the victim, including prolonged outages, decreased productivity, and disruption of services for users and customers.
How can I prevent an NTP amplification attack?
Preventing NTP amplification attacks requires careful configuration of your NTP servers so that only trusted hosts have access to them. It also involves monitoring user activity on your system for any suspicious requests coming from untrusted sources. Some best practices for preventing NTP amplification attacks include disabling anonymous binding on your NTP servers, restricting access only to known hosts or networks via access control lists (ACLs) or firewalls, monitoring user traffic closely for any abnormal requests coming from external sources, and configuring rate-limiting on your systems so that malicious traffic can be blocked before it reaches your network. Additionally, you should ensure that your security patches are up to date so that any potential vulnerabilities on your system are closed off quickly.
To detect an ongoing attack, administrators should closely monitor all incoming traffic patterns and look out for any sudden increases or spikes in requests coming from outside sources, as they could be indicative of an attack underway. Additionally, monitoring logs generated by intrusion detection systems should also reveal any possible attempts at amplification attacks, as these will usually generate many false positive alerts when malicious actors spoof source IP addresses with bogus values that do not match up with legitimate network hosts or addresses listed in ACLs or firewall tables.
Responding to an active NTP amplification attack requires swift action both in terms of mitigating its impact as well as identifying where it originated from, if possible, so that appropriate steps can be taken against perpetrators, if necessary, such as reporting abuse incidents. Best practices include blocking suspect sources at firewalls using information gathered through IDS/IPS logs; setting rate limits on upstream links; throttling packet rates; implementing anti-spoofing measures such as reverse path forwarding checks; deploying application-layer mitigation solutions such as IPsec VPN tunnels; segmenting networks into smaller sections; filtering traffic based on predefined rules; ensuring proper patch management; working with ISPs/CDNs where applicable; decreasing TTL thresholds used by clients; keeping track of changes made during periods when attacks occur; and monitoring logs consistently.
To recover from an active attack situation involves first restoring service by deploying mitigations discussed above, and simultaneously identifying root causes, such as vulnerable services left exposed online without proper security configurations, which allow attackers access in. Prioritizing efforts here will help administrators quickly regain control over compromised resources while also taking necessary steps toward further hardening overall security configurations, thus mitigating chances of similar attacks happening in the future.
Prevent NTP amplification attacks and DDoS attacks with Akamai
Akamai offers end-to-end DDoS protection that acts as a first line of defense, providing dedicated edge, distributed DNS, and cloud mitigation strategies designed to prevent collateral damage and single points of failure. Our purpose-built DDoS clouds offer dedicated scrubbing capacity and higher quality of mitigation, which can be fine-tuned to the specific requirements of web applications or internet-based services.
One of the most effective ways to stop NTP amplification attacks and other DDoS attacks is with Akamai Prolexic, a proven cloud scrubbing service that protects entire data centers and internet-facing infrastructure from DDoS attacks across all ports and protocols. With Prolexic, traffic is routed via BGP anycast across globally distributed, high-capacity scrubbing centers, where our Security Operations Command Center (SOCC) can deploy proactive and/or custom mitigation controls to stop attacks instantly. By routing traffic to the nearest scrubbing center, Prolexic can stop attacks closer to the source to maximize performance for users and maintain network resiliency through cloud distribution. Once scrubbing is complete, clean traffic is returned to the customer origin via logical or dedicated active connections.
Available as an always-on or on-demand service, Prolexic offers flexible integration models to serve the needs of a variety of security postures across hybrid origins.
With Akamai Prolexic, your security teams can:
- Reduce risk of DDoS attacks, thanks to proactive mitigation controls and Prolexic’s zero-second SLA.
- Stop highly complex NTP amplification attacks without sacrificing quality of mitigation.
- Unify security postures by consistently applying DDoS mitigation policies throughout your organization, regardless of where applications are hosted.
- Optimize incident response to ensure business continuity with service validation exercises, custom runbooks, and operational readiness drills.
- Scale security resources with our fully managed solution that is backed by 225+ front-line SOCC responders.