Akamai is the cybersecurity and cloud computing company that powers and protects business online. Our market-leading security solutions, superior threat intelligence, and global operations team provide defense in depth to safeguard enterprise data and applications everywhere. Akamai’s full-stack cloud computing solutions deliver performance and affordability on the world’s most distributed platform. Global enterprises trust Akamai to provide the industry-leading reliability, scale, and expertise they need to grow their business with confidence.
Application programming interfaces (APIs) are integral to modern application architecture. APIs define rules and protocols that enable an application to communicate and exchange data with other software, services, and platforms. This capability allows developers to build more powerful applications by leveraging data and functions from existing software, and it enables businesses to integrate IT systems with external services and third-party platforms.
APIs also present major operational risks. As organizations become increasingly cloud-centric and digital, their API estate grows in scope, scale, and complexity. APIs are often spread across multiple environments, from on-prem to hybrid cloud. Adding to the complexity, an organization’s API ecosystem likely extends far beyond its own network and cloud presence. Consider the myriad connections API forge with apps, services, and systems belonging to third parties and developer ecosystems.
As your APIs increase in scope, scale, and complexity, it’s difficult to gain real-time insights into:
Where your APIs are located across various business units that in many cases have their own developer teams
How your APIs are configured, where they’re routed, and if they have proper authentication and authorization controls
If your APIs return sensitive data when called, and who can gain access to that data
Making matters more challenging, a large portion of the API that organizations accumulate are unmanaged, unseen, and often unprotected. This includes dormant, shadow, and zombie APIs that in many cases slip by the defenses of commonly used tools.
To secure APIs — as well as the applications, web services, and IT environments that APIs interact with — enterprise security teams must adopt technologies and best practices to secure against API attacks, API breaches, and API abuse.
Top threats to APIs
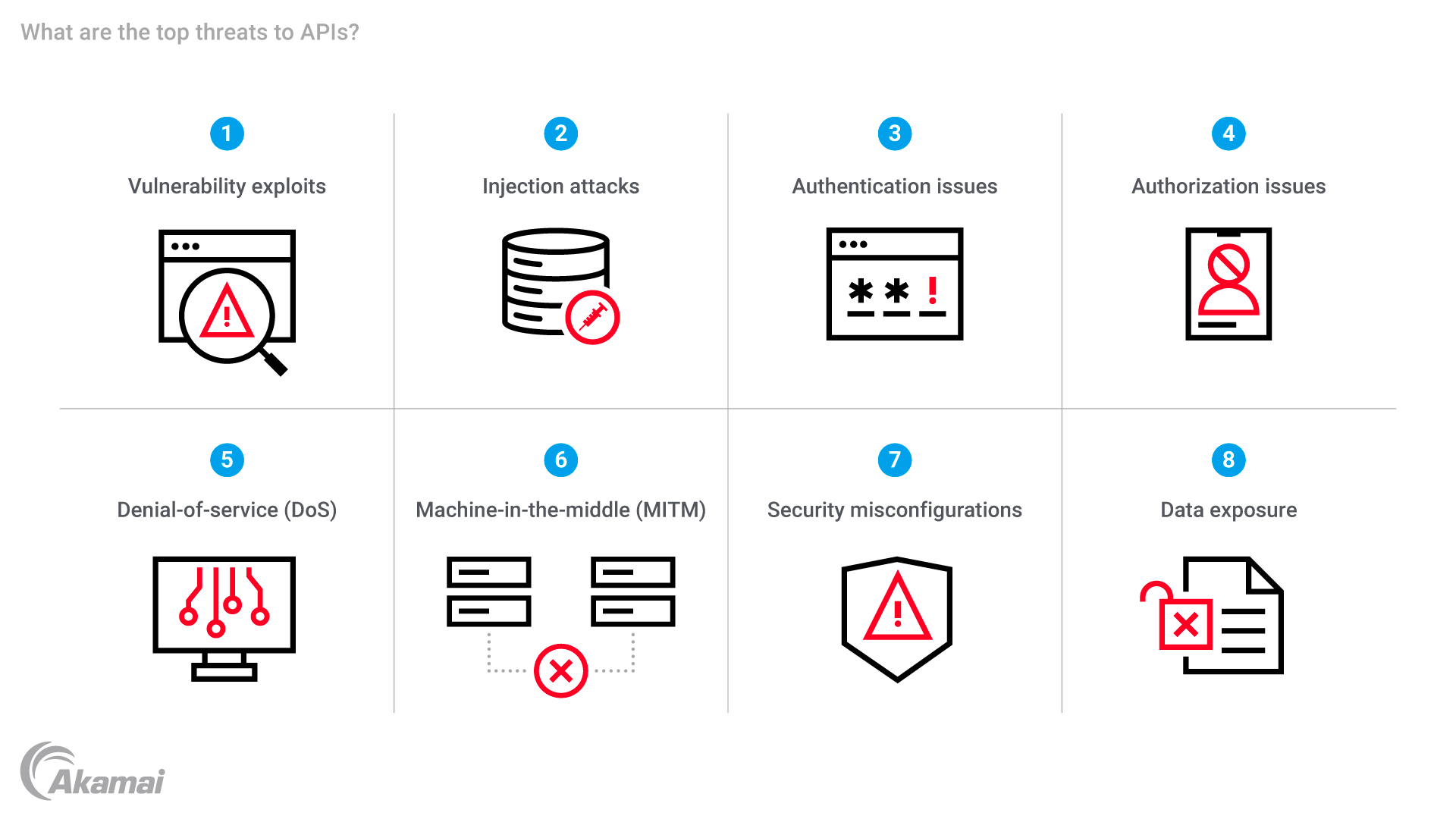
The most common threats to APIs fall into several categories.
Vulnerability exploits: Many APIs are created with vulnerabilities that enable attackers to send API requests that result in unwanted behavior. By exploiting these vulnerabilities, attackers can gain unauthorized access to an API or related applications. Common examples include attacks like cross-site request forgery (CSRF).
Injection attacks: In attacks like SQL injection, cross-site scripting (XSS), XML injection, and scripting, attackers inject malicious code into API requests. When the code is executed by a server, the API may perform certain unwanted or malicious actions.
Authentication issues: Authentication is the process of determining whether a user, application, or device is a legitimate client before accepting and processing API requests. When an organization has weak authentication mechanisms, attackers may obtain the credentials of a legitimate user, steal an API key, intercept and use an authentication token, or try many different password or encryption key combinations in a brute-force attack.
Authorization issues: Authorization is the task of determining what level of API access a client is permitted. When authorization is not well managed, an API client may have access to data that should not be available to them, increasing the risk of data breach. A common example is a threat called Broken Object Level Authorization (BOLA), where an attacker can access or manipulate objects that they should not have access to, due to insufficient access control.
Denial-of-service (DoS) or distributed denial-of-service (DDoS) attacks: These attacks overwhelm an API by flooding it with more traffic than it can handle, causing the API to crash or slow down. As a result, service may be denied to legitimate users.
Machine-in-the-middle (MITM) attacks: When an attacker is able to intercept traffic and communications between two systems, they may be able to capture sensitive data like API keys, access tokens, and user credentials, or manipulate data sent from one party to another.
Security misconfigurations: When IT teams fail to adequately configure security settings for APIs, they may enable attackers to gain unauthorized access, escalate privileges, and compromise the IT environment.
Data exposure: Many APIs can be manipulated into divulging more information than necessary when responding to API requests — a flaw that attackers can exploit to steal data or gain unauthorized access.
The need to secure APIs
Given the critical role APIs play in modern web applications and apps, the task of securing APIs is critical to overall cybersecurity. Failure to properly secure APIs can have a significant adverse impact on an organization.
Loss of sensitive data: When attackers use APIs to gain access to back-end systems, they may be able to steal sensitive data like personally identifiable information for customers, business plans, financial records, and intellectual property.
Loss of trust: Organizations that succumb to API security threats often experience a loss of trust from customers and partners, significantly impacting business opportunities and the bottom line. Following an API attack, a security team may also face a loss of trust and damaged credibility amongst key internal stakeholders such as senior leadership and the board of directors.
Compliance failures: When sensitive information is stolen or exposed in a data breach, it may result in significant fines and legal penalties for organizations in heavily regulated industries. Many organizations have APIs in mind when considering their approach to complying with data security regulations, but far fewer are aware of the best practices for API security and compliance.
Data breaches and cyberattacks: Many cybercriminals use API attacks to gain access to IT environments to launch larger malicious cyberattacks.
Service disruptions: Because APIs are essential for connecting applications and systems, an attack on an API may break services and systems, causing outages or a significant loss of productivity.
Financial damage: In addition to enabling attackers to drain financial accounts, API attacks represent a significant cost to an organization in mitigation process, forensic investigations, loss of productivity, and loss of business opportunity.
Challenges in API security
To secure APIs, IT teams must overcome a number of significant challenges.
Complex API ecosystems: With thousands of APIs, numerous API endpoints, and different types of requests, an organization’s API ecosystem is typically quite complex. Additionally, an organization’s digital footprint may contain open-source, third-party, and shadow APIs that make it difficult to inventory every asset. As a result, IT teams may be unable to even visualize 100% of APIs, let alone protect them with strong security measures.
Evolving threats: Attackers are constantly developing new ways to exploit APIs, requiring constant vigilance and updates to security measures.
Interconnectedness: Because APIs are so interwoven throughout an IT environment, IT teams are reluctant to introduce security measures that may lead to latency, poor performance, or limits on scalability.
Unmanaged proliferation: In many enterprises, APIs are quickly developed by diverse teams without a central framework to secure APIs and manage development.
Delivery pressure: The rapid pace of the modern software development lifecycle leads to tension between the need to secure APIs and the pressure to quickly move new versions into production.
Technology to secure APIs
IT teams may adopt multiple layers of technology to properly secure APIs. Here are four examples of traditional tools that organizations typically use to manage APIs and provide a baseline set of protections.
Authentication and authorization protocols: Authentication and authorization are essential elements of API security . Protocols like OAuth 2.0, OpenID Connect, and JSON Web Tokens (JWT) can help to verify the identity of users and control access to resources. Implementing these technologies in combination with role-based access control and attribute-based access control can significantly improve efforts to secure APIs.
API management platforms: API management platform providers offer comprehensive tools to help organizations create, publish, monitor, analyze, and secure APIs. These solutions offer a centralized way to manage the entire API lifecycle from development to retirement.
API gateway: An API gateway serves as a single entry point for all API traffic, managing tasks such as rate limiting, throttling, and validation of API requests. Because APIs and gateways capture detailed logs of traffic and activities, they can also provide real-time monitoring capabilities.
Web application firewall (WAF): WAFs protect APIs by filtering and monitoring HTTP requests. A WAF sits between clients and servers to monitor, filter, and analyze HTTP/HTTPS traffic to and from web applications. It is especially helpful in defending against attacks that target the application layer.
However, the complexity and frequency of API attacks calls for another security layer beyond the traditional tools used by many organizations. Enterprises should use a complete API security solution that provides API discovery, API security posture management, runtime protection, and API security testing.
This comprehensive approach works as an important complement to an organization’s existing tools for managing and securing APIs such as API gateways and WAFs.
API discovery: Most organizations have little to no visibility into a large percentage of their API traffic, often because they assume all of their APIs are routed through an API gateway. But that is not the case. Many of a typical organization’s APIs are unmanaged (e.g., dormant APIs that are forgotten about, but still running and still in contact with sensitive data). Your enterprise is exposed to a range of risks without a complete and accurate inventory. Core capabilities needed:
Locating and inventorying all of your APIs, regardless of configuration or type
Detecting dormant, legacy, and zombie APIs
Identifying forgotten, neglected, or otherwise unknown shadow domains
Eliminating blind spots and uncovering potential attack paths
API posture management: With a complete API inventory in place, it’s critical to understand what types of data flow through your APIs and how that affects your ability to comply with regulatory requirements. API posture management provides a comprehensive view of traffic, code, and configurations to assess your organization’s API security posture. Core capabilities needed:
Automatically scanning infrastructure to uncover misconfigurations and hidden risks
Creating custom workflows to notify key stakeholders of vulnerabilities
Identifying which APIs and internal users are able to access sensitive data
Assigning severity rankings to detected issues to prioritize remediation
API runtime security: You’re no doubt familiar with the concept of “assume a breach.” API-specific breaches and attacks are reaching that same degree of inevitability. For all of your APIs that are live in production, you need to be able to detect and block attacks in real time. Core capabilities needed:
Monitoring for data tampering and leakage, policy violations, suspicious behavior, and API attacks
Analyzing API traffic without additional network changes or difficult-to-install agents
Integrating with existing workflows (ticketing, SIEM, etc.) to alert security/ operations teams
Preventing attacks and misuse in real time with partially or fully automated remediation
API security testing: API development teams are under pressure to work as quickly as possible. Speed is essential for every application developed, making it easier for a vulnerability or design flaw to happen and subsequently go undetected. Testing APIs in development before they are released into production greatly reduces both risk and the cost of fixing an API that is vulnerable. Core capabilities needed:
Running a wide range of automated tests that simulate malicious traffic
Discovering vulnerabilities before APIs enter production, reducing the risk of successful attacks
Inspecting your API specifications against established governance policies and rules
Running API-focused security tests that run on demand or as part of a CI/CD pipeline
Note: In addition to API security solutions, organizations can explore the capabilities of web application and API protection (WAAP). Designed to quickly identify and mitigate threats from multiple attack vectors, WAAP extends the traditional protections of a WAF. An API security solution — working in tandem with WAF and WAAP — extends protections even further beyond the firewall to create the strongest defense possible.
Overall best practices to secure APIs
These API security best practices can help organizations mitigate security risks and ensure robust web application security:
Encrypt data in transit: Use Transport Layer Security (TLS) and Secure Sockets Layer (SSL) protocols to encrypt data as it moves between clients and the API, ensuring that API calls cannot be intercepted or tampered with.
Validate and sanitize inputs: Ensure that all inputs are properly validated and sanitized to prevent injection attacks. Validation is the process of checking to make sure that inputs conform with expectations for what is considered valid data. Sanitization is the process of cleaning or filtering inputs to remove any potentially malicious or harmful content.
Use rate limiting and throttling: Control the number of API requests to avoid abuse or overuse of APIs, prevent excessive consumption of resources, and block potential DoS and DDoS attacks.
Monitor and log API activity: Keep detailed logs of API calls and monitor them for unusual activity. By analyzing logs, security teams can uncover suspicious or anomalous patterns of activity such as abnormal traffic spikes or repeated failed login attempts that may indicate a security threat.
Conduct regular security testing: Use regular security testing and audits to identify and fix vulnerabilities. Testing may be performed in development as well as in production environments to maximize a security team’s ability to uncover flaws.
Implement least privilege access: Ensure that users and services have only the minimum level of access necessary to perform their functions. This helps to prevent unauthorized access to APIs and IT resources.
Secure API endpoints: Protect API endpoints with appropriate security measures, such as using an API gateway and web application firewall.
Practice secure API design: One of the most important ways to secure APIs is to introduce security as early in the design process as possible. By testing for and eradicating flaws during development, development teams can limit the risk of vulnerabilities being exploited by attackers after APIs move into production.
Monitor the OWASP Top 10: The Open Worldwide Application Security Project (OWASP) is a nonprofit foundation that works to improve the security of software. The OWASP API Security Top 10 is a list of the most critical API security issues that developers and security professionals should address.
Adopt Zero Trust principles: a Zero Trust approach to security assumes that no user, device, or application inside or outside an IT environment can be inherently trusted. By requiring continuous authentication and validation on every request for access to APIs, a Zero Trust framework prevents unauthorized access and limits the damage of attacks that have successfully breached an organization’s defenses.
Use API keys: An API key is a unique identifier that authenticates the application or website making an API call, rather than the person using the website. API keys help prevent unwanted calls, unauthorized access, and data breaches.
FAQs
Simple Object Access Protocol (SOAP) and Representational State Transfer (REST) are different types of APIs. As a highly structured message protocol that uses XML for messaging, SOAP APIs are more secure by design because of built-in standards like WS-Security. REST APIs offer a simpler approach to APIs, but they have no built-in security capabilities. Security must be added for data transmission, deployment, and interaction.
API endpoints are specific paths through which APIs interact with other systems or applications. Each endpoint represents a unique function or resource in the API, and securing these endpoints is crucial to prevent unauthorized access and attacks.

