State of the Internet / Security: Year in Review
Introduction
What a year 2021 has been. Even as the world continues to re-open to various degrees, we’re still feeling the impact from 2020’s move to an almost completely virtual world. Many large companies are shifting to a hybrid model, mixing the ability to work from home with working in the office. Some are even offering their employees the opportunity to work remotely indefinitely. There is no denying that the way we work, bank, play, and relax has been impacted by COVID-19. Shouting “pivot” may have shot into popular culture in the TV show Friends, but it’s a rallying cry that’s been revived in the 2020s by businesses, individuals, and criminals alike.
The Year in Review report itself has pivoted — instead of being a full PDF publication, this issue is here, on the new Akamai blog. The purpose of this annual report is to review and remember what we have published over the past year, and we are publishing it directly to the blog, so getting to a report or blog post is just one simple click away.
So without further ado, here is our 2021 Year in Review!
October 2020
Or Katz’s JavaScript obfuscation research dominated most of October last year. Katz’s first blog Catch Me If You Can introduced this technique. While the technique is not considered highly sophisticated or evasive, it is hard to determine that the web page is malicious without rendering the page and evaluating the content. Katz further expanded on this in The Tale of Double JavaScript Obfuscated Scam, where he outlined how it’s being used in many types of scams such as phishing and Magecart attacks. He also followed an example of double obfuscation and encryption recently observed in an active phishing scam. In Phishing JavaScript Obfuscation Techniques Soar, Katz rounded out his findings by showing the increase in the use of this technique. “We see a continued increase in the usage of obfuscation techniques in phishing websites over the 10-month period between November 2019 until August 2020, representing an increase of more than 70% over that time frame.”
November 2020
Larry Cashdollar discovered an infection where a malicious actor added a storefront on top of an existing WordPress installation, and wrote about his findings in WordPress Malware Setting Up SEO Shops. The malware overwrote the index.php file and added a function that checks the query parameter for a certain string. If this string is found, then a different site is served up. “It didn’t take long for the attacker to guess my credentials, and once obtained, they used their access to upload a malware-infected plug-in.”
 We see the request headers are out of order, and the User-Agent string is attempting to look like a Googlebot (from the WordPress Malware Setting Up SEO Shops blog post)
We see the request headers are out of order, and the User-Agent string is attempting to look like a Googlebot (from the WordPress Malware Setting Up SEO Shops blog post)
December 2020
Getting to December 2020 was like a big exhale. We didn’t know what 2021 would bring, but with the first COVID-19 vaccine granted emergency use authorization on December 11, it felt like we were on the cusp of a big shift. The holidays were marked with virtual parties and family gatherings. 2020 was also challenging from a cybersecurity point of view, as nearly the entire workforce moved to remote working. Enterprise boundaries had never before been so vague, which introduced complexities on that end. Katz recapped how phishing trends impacted an unprecedented year.
January 2021
We all hung up our 2021 calendars in hopes for a literal fresh start. However, even as vaccine rollouts started to happen for essential employees, the vast majority of us started the year still at home. Steve Ragan noticed that criminals had a new way of targeting gamers playing popular games. Ragan noted that gamers don’t just have to deal with network-level events like DDoS and credential stuffing attacks; they also have to deal with personal add-on attacks. “Recently, I became aware of a Minecraft player who was targeted by a scammer that demanded a ransom payment via the chat service Discord. The demand was simple, pay roughly $20 via in-game currency (SkyBlock Gems) or face a DDoS attack. Panicked, not wanting to wake their parents and discuss the threat, the victim paid the ransom. Proving that criminals are rarely true to their word, the scammer launched a DDoS attack anyway, and knocked the victim’s network offline until the following day.”
Cashdollar also dove deeper into the weaponization of the KashmirBlack botnet. “The KashmirBlack CVE-2018-9206 exploit scans a list of 85 unique paths, which I believe the botnet author collected, either via Google Dork or from their own exploitation experiences. It checks these paths by making POST requests to upload files to them. The script then checks whether the existence of its uploaded payload file sssp.php exists or not in the corresponding upload files/ directory.”
February 2021
Assaf Vilmovski wanted to do what many of us did in 2020 — he wanted to extend the local Wi-Fi in his home to reach all the floors, so every part of his home could be connected to the internet. However, that wasn’t in the cards for him, so he used the extra router to do a little research. Vilmovski used the D-Link DAP-1360 and discovered a vulnerability in H/W Ver. A1, F/W Ver. 2.5.5, within the ping functionality of the web interface.
February also started a larger rollout of COVID-19 vaccinations, and criminals didn’t miss a beat. Criminals targeted the most vulnerable among us, using the lure of COVID-19 vaccination in their phishing campaigns. Ragan explained the history related to COVID-19 scams, including a large vaccination scam, which the National Health Service (NHS) in the U.K. warned the public about.
Katz unpacked a new phishing campaign that hit U.K. banks, which bypassed 2FA. The actor, Kr3pto, is a phishing kit developer who builds and sells unique kits targeting financial institutions and other brands. “Akamai tracked more than 7,600 domains being deployed with the Kr3pto kit, abusing 8 different banking brands, and using commercial web hosting to scale the various phishing campaigns in an effort to evade detection.”
Evyatar Saias and Chad Seaman worked together on research that centered around a recent piece of malware from a known cryptomining botnet campaign. That piece of malware had started leveraging Bitcoin blockchain transactions to hide its backup C2 IP address. It’s a simple, yet effective, way to defeat takedown attempts. “The operators of a long-running cryptomining botnet campaign began creatively disguising their backup C2 IP address on the Bitcoin blockchain.”
March 2021
We published our first SOTI Research in March, when we looked back at 2020 and examined some of the technological shifts that happened. Rather than simply talking about trends for the world as a whole, we included a look into the attacks against our own systems to provide concrete examples. We pulled the covers back a little bit to see how Akamai used Akamai to defend and protect itself throughout a tumultuous year.
One of the key layers of defense that Akamai uses is Secure Internet Access Enterprise, which uses Akamai’s research and data, augmented with third-party data, to identify malicious domains and block them at the DNS and HTTP level. It addresses several key elements used by criminals, including exfiltration, command and control (C2), and phishing.
Cashdollar also discovered another Golang cryptominer on March 4. “Cryptomining software will continue to evolve and take advantage of the latest software vulnerabilities. Software vulnerabilities like Command Injection and Remote Code Execution will continue to be valued by cybercriminals in order to monetize your CPU cycles.”
Seaman explored a recent string of attacks that Akamai customers had been experiencing that leveraged a networking protocol known as protocol 33, or Datagram Congestion Control Protocol (DCCP). DCCP is a more reliable “unreliable” network protocol. “In the attacks against Akamai customers I observed, 100% of the traffic consisted of DCCP-Request packets. These packets are essentially SYN floods of the DCCP protocol variety.”
April 2021
Typically in the U.S., April means taxes are due. Because of this, criminals predictably target those who are just trying to file their taxes before the due date. Ragan delved into the trends in criminal activity around this annual time period. “The stress and urgency surrounding this time of year makes the victim pool highly vulnerable to various types of schemes. In addition to phishing, tax season is also the time of year when criminals focus their efforts towards other types of attacks including Local File Inclusion (LFI), SQL Injection (SQLi), and credential stuffing.”
On a purely human level, April 2021 was a big month — it marked the first time when all U.S. adults became eligible for a COVID-19 vaccine.
May 2021
Akamai has a long-standing history of being a contributor to Verizon’s Data Breach Investigations Report (DBIR), and this year was no exception. Martin McKeay dove into what this year’s report touched on, and some of the biggest findings — including the impact of COVID-19 on traffic and attack patterns. “I find much to be inspired by in the work the Verizon team does, especially the partnerships they’ve built over the years. Our next State of the Internet / Security report, Phishing for Finance, is a reflection of our own commitment to partnering with other organizations to produce the best research possible.”
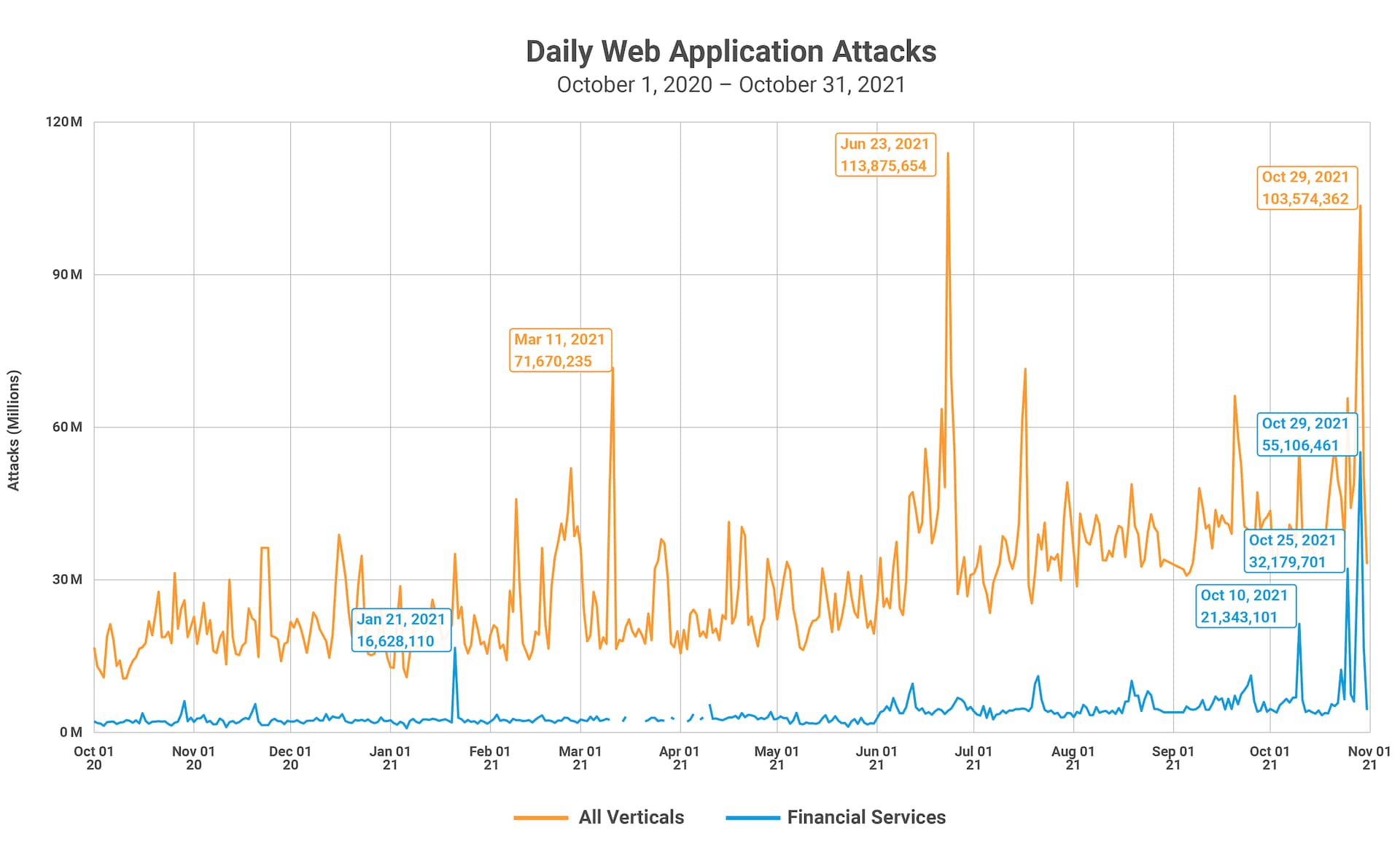
Our first full State of the Internet / Security report of the year, Phishing for Finance, also launched in May. Featuring research and data from threat intelligence company WMC Global, this report focused on the financial services industry. Web-based attacks and application attacks were high in 2020 and show no indication of slowing anytime soon. Akamai observed 6,287,291,470 web attacks globally, with 736,071,428 of them in the financial services sector alone. This report also covered phishing as a service, with the example of the Ex-Robotos phishing kit.
Cashdollar continued his research and discovered a Romanian cryptomining infection. “While cryptomining malware is not new, it was interesting to find a package that deviates from the improperly packed tar packages I’m used to finding. This miner installs XMRig and Perl DDoS IRC Bot v1.0, and it hides its cryptomining activity by using a rootkit similar to other reported cryptominers.”
June 2021
June marked the halfway point of 2021, and our next SOTI Research report, Gaming in a Pandemic, was released. Gaming was a haven for many people around the world, including our own team, especially during the height of lockdown. While the gaming industry saw a decrease in DDoS attacks, the industry also saw more growth in overall attack traffic than any other industry in 2020.
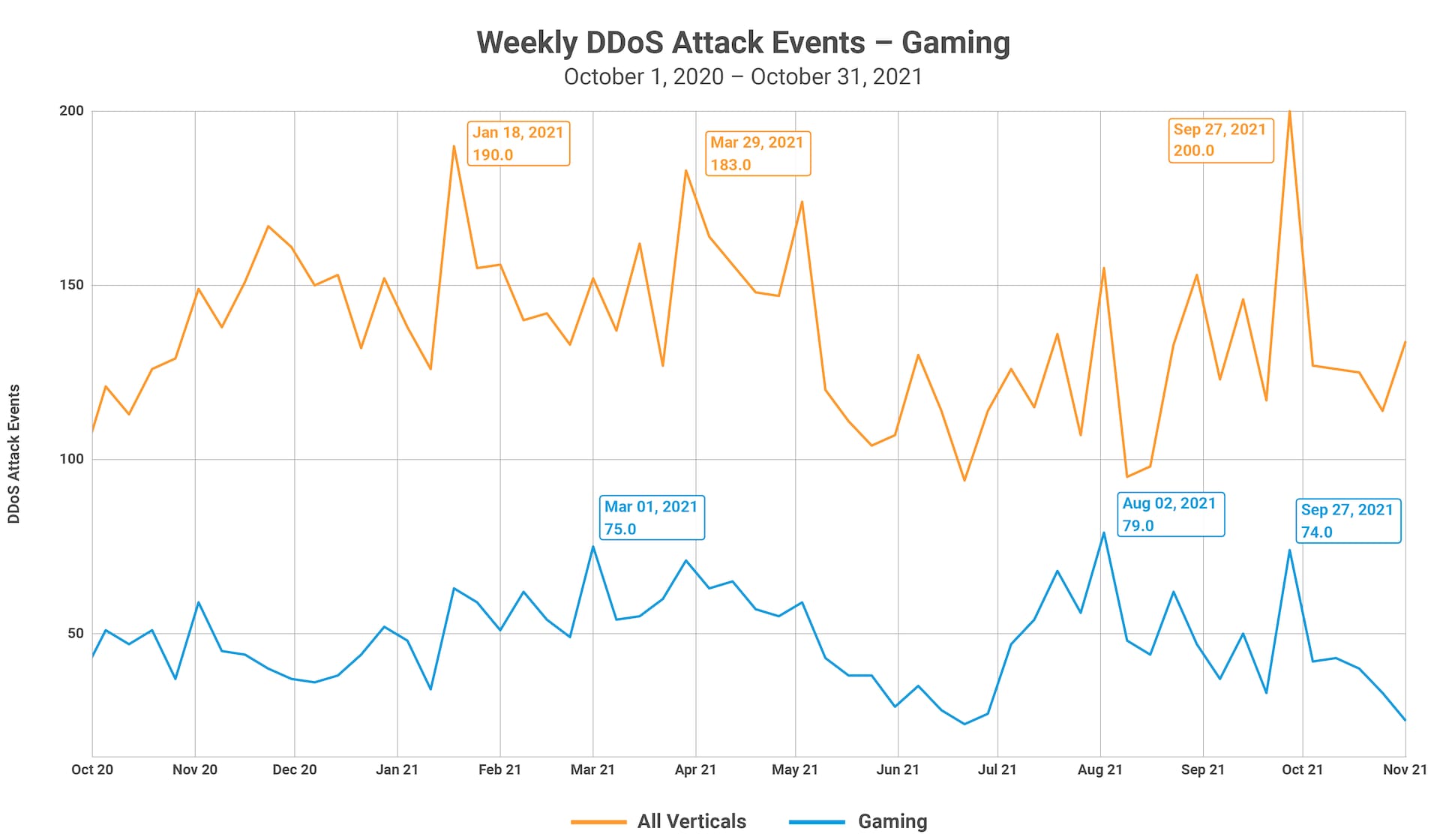
2020 was wild — let’s not ignore that. While we were all at home, adjusting to the “new normal,” trying to balance work, school, and day-to-day existence during a pandemic, many people turned to gaming as an outlet and means of personal connection. Criminals did this too. Make no mistake: While their intentions are malicious, they are still people. They talked to each other, they played games, and in some cases this social bond meant they coordinated their efforts, to varying degrees.
During this time, Akamai began working on our new website and implementing our blog. Big kudos to Julia Tetrud and her teammates for working tirelessly to help manually migrate and integrate our former SIRT blog into the new Akamai blog.
July 2021
Ryan Barnett explored a supply chain ransomware attack that targeted Kaseya. On July 2, Kaseya disclosed an active attack against customers using its VSA product, and urged all on-premises customers to switch off Kaseya VSA. The attackers, affiliates of the REvil ransomware group, exploited authentication bypass and arbitrary command execution vulnerabilities (CVE-2021-30116) that enabled them to distribute ransomware encryptors to targeted systems. To assist defenders, Kaseya released a number of IOCs related to the ransomware attacks.
August 2021
Researching malware has many challenges. One of those challenges is obfuscated code and intentionally corrupted binaries. To address challenges like this, the Akamai SIRT team wrote a small tool in C that could fix intentionally corrupted binaries automatically. They also plan to open-source the project so other researchers could use it, and perhaps improve and expand upon the tool’s capabilities as needed. The Akamai SIRT team detailed their project, and how it works, in UPX Packed Headaches.
 UPX magic and mangled p_info headers from the UPX Packed Headaches blog post
UPX magic and mangled p_info headers from the UPX Packed Headaches blog post
September 2021
As the season started to change, Saias explored a new evolution of Kinsing — which involved it targeting Windows systems. The botnet caught his and the Akamai SIRT’s interest because it has shown to be highly active across a diverse set of geographical regions, including the Americas, Europe, and Asia. The botnet had been operating using the same distribution IP address (194.38.20.199), without needing to rotate, for over six months. The campaign previously only targeted Linux machines.
Around the same time, Cashdollar noticed a plethora of UPX packed cryptomining malware written in Golang, targeting Linux systems. The malware’s primary tactic is to spread by taking advantage of vulnerable systems and weak administrative credentials. Once they’ve been infected, these systems are then used to mine cryptocurrency. Cashdollar named the sample he examined “Capoae,” based on the code’s output to his terminal. Cryptomining campaigns continue to evolve. The Capoae campaign’s use of multiple vulnerabilities and tactics highlights just how intent these operators are on getting a foothold on as many machines as possible.
October 2021
Did you know the first instance of an application programming interface (API) in the wild was created by Salesforce.com on February 7, 2000, according to the API Evangelist blog? What was originally meant as a relatively simple system-to-system communication method has evolved into one of the biggest drivers of internet traffic.
This is why we decided to dive deep into the world of APIs in our State of the Internet / Security report API: The Attack Surface That Connects Us All. Just like in May, we saw and understood the value of collaboration across the industry to paint a larger picture of the trends that we were seeing. For this report, in addition to our own research, we partnered with Veracode, as their insights into the application security space helped further our research into APIs and development challenges.
As our data shows, the attackers are clearly out there lurking, developing new techniques and attack methods — and API functionality is one of their primary targets. While teams are moving toward having security baked into the development lifecycle, the process is slow. This leaves organizations behind the eight ball and forces them in some cases to launch known vulnerable code into the wild, because the business use for said code is critical.
Conclusion
It’s always incredible to see how much can happen in one year. One thing remains the same, though: The State of the Internet will always continue to evolve — both this report and the internet itself. The past two years have shown us that the internet is a vital part of day-to-day life, encompassing everything from school and work, to retail and entertainment, to banking and communication.
Collaboration across the industry is key for creating a well-rounded image of what the internet as a whole is seeing. Without cross-community collaboration, we won’t be as equipped to fully understand and tackle evolving threats and issues that we will continue to see.
We won’t attempt to make any predictions in this post, because if 2020 and 2021 taught us anything, it’s that literally anything can happen. Only time will tell. For now, we hope you have a safe and healthy holiday season — we’ll see you in 2022!
Special thanks and credit go to:
Editorial Staff
Martin McKeay, Editorial Director
Amanda Goedde, Senior Technical Writer, Managing Editor
Steve Ragan, Senior Technical Writer, Editor
Chelsea Tuttle, Senior Data Scientist
Marketing Staff
Georgina Morales Hampe, Project Management
Shivangi Sahu, Program Management
Researchers
Ryan Barnett, Principal Security Researcher
Larry Cashdollar, Security Intelligence Response Team, Senior Engineer II
Or Katz, Principal Lead Security Researcher
Evyatar Saias, Security Researcher
Chad Seaman, Security Intelligence Response Team, Senior Lead Engineer II
External Collaborators
Chris Eng, Chief Research Officer, Veracode
Ian Matthews, CEO, WMC Global
Jake Sloane, Senior Threat Hunter, WMC Global
Elizabeth Snead, Senior Product Manager, WMC Global





