Kingsing Evolves | Akamai Blog

Introduction
A large, and persistent, cryptomining botnet is infecting systems at scale across the internet.
The campaign was first seen by the Akamai SIRT on February 16, 2021, and appears to be targeting both Windows and Linux systems. The botnet caught our interest because it has shown to be highly active across a diverse set of geographical regions, including the Americas, Europe, and Asia. The botnet has been operating using the same distribution IP address (194.38.20.199), without needing to rotate for over six months now. The campaign previously only targeted Linux machines, but recently expanded to Windows systems as well.
Infecting Windows systems
To infect Windows machines, the botnet leverages CVE-2020-14883, a vulnerability which affects versions 10.3.6.0.0, 12.1.3.0.0, 12.2.1.3.0, 12.2.1.4.0 and 14.1.1.0.0 of Oracle WebLogic Server. When exploited, it allows an attacker to perform Remote Code Execution (RCE) which can result in a takeover of the Oracle WebLogic Server.
The infection starts by getting the victim machine to download and execute an XML file called wbw.xml. On Windows machines, the XML file is executed via the ClassPathXmlApplicationContext class
 Fig. 1) the victim machine downloads and executes a remote xml file via the ClassPathXmlApplicationContext class, CVE-2020-14883
Fig. 1) the victim machine downloads and executes a remote xml file via the ClassPathXmlApplicationContext class, CVE-2020-14883
The fetched wbw.xml file contains an embedded PowerShell command, which executes on the victim’s machine. The command is:

It attempts to download a PowerShell script called “ 1.ps1” onto the victims machine using the System.Net.WebClient.DownloadString method. It also leverages the Set-ExecutionPolicy Bypass flag to ensure that nothing is blocked, and that no prompts or warnings will be generated during execution.
 Fig. 2) The content of the wbw.xml file which contains a PowerShell command that downloads a PowerShell script called 1.ps1 onto the victim's machine
Fig. 2) The content of the wbw.xml file which contains a PowerShell command that downloads a PowerShell script called 1.ps1 onto the victim's machine
The 1.ps1 script then downloads a crypto miner executable called xmrig.exe, as well as a config.json file, that contains config information for the miner to consume - such as crypto wallet addresses, crypto pool endpoints, and additional configuration settings. In addition to that, the 1.ps1 script also contains a $miner_name variable which stores the new name that the crypto miner executable, xmrig.exe, will be renamed to, in this case it xmrig.exe is renamed to “sysupdate” and then executed.
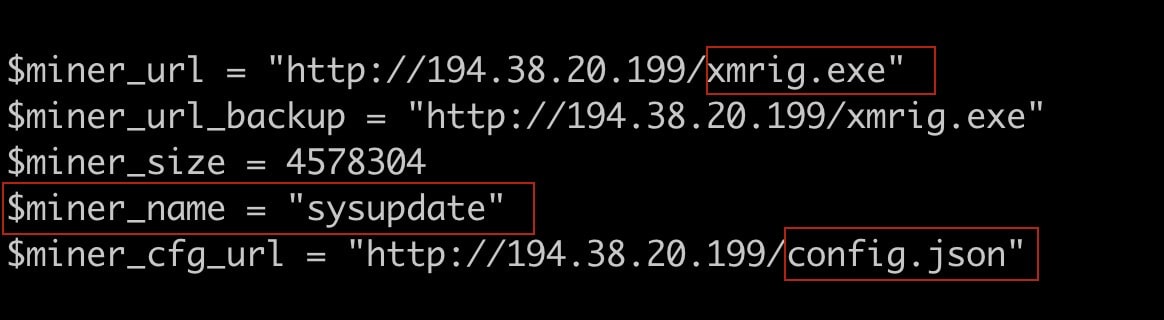 Fig. 3) A portion of the PowerShell script 1.ps1
Fig. 3) A portion of the PowerShell script 1.ps1
 Fig. 4) A portion of the config.json, which contains configurations for the miner executable such as mining pool endpoints and crypto wallet addresses.
Fig. 4) A portion of the config.json, which contains configurations for the miner executable such as mining pool endpoints and crypto wallet addresses.
The 1.ps1 script establishes persistence on the victim's machine in order to update the config.json file and the miner. It does so by leveraging SchTasks.exe, which allows the creation, deletion, and running of scheduled tasks on a local or a remote machine from PowerShell. More info on SchTasks.exe can be found here. The scheduled task is named “Update service for Windows Service” and it again leverages the -ExecutionPolicy bypass flag in order to avoid raising any warnings or prompts while executing, as well as the -windowstyle hidden flag to remain hidden.
 Fig. 5) the PowerShell script 1.ps1 establishes persistence by creating a scheduled task called “Update service for Windows Service” for pushing updates to the config file and the miner executable
Fig. 5) the PowerShell script 1.ps1 establishes persistence by creating a scheduled task called “Update service for Windows Service” for pushing updates to the config file and the miner executable
Infecting Linux systems
The campaign is leveraging multiple CVEs to achieve RCE in order to infect Linux systems. Along with the Kinsing malware, which contains a crypto miner, Linux payloads also have a remote access trojan (RAT). The targeted services include Oracle WebLogic Server, Redis, Apache Solr, PHPUnit, and Supervisor XML-RPC.
The Oracle WebLogic Server CVE-2020-14883 is also leveraged by this campaign on Linux systems. However, unlike the Windows version of this vulnerability, where the RCE happens via the ClassPathXmlApplicationContext class, on Linux it happens via the FileSystemXmlApplicationContext class. The malicious XML file is called wb.xml, which downloads a bash script, instead of the previous wbw.xml for Windows which downloads a PowerShell script.
 Fig. 6) the victim machine downloads and executes a remote xml file via the FileSystemXmlApplicationContext class, CVE-2020-14883
Fig. 6) the victim machine downloads and executes a remote xml file via the FileSystemXmlApplicationContext class, CVE-2020-14883
 Fig. 7) The content of the wb.xml file, which contains a bash command that downloads then executes a bash script called wb.sh on the victim's machine
Fig. 7) The content of the wb.xml file, which contains a bash command that downloads then executes a bash script called wb.sh on the victim's machine
On Linux systems, the infection starts by achieving RCE using any of the CVEs given in the table below to download a bash script file onto the victim’s machine.


 Fig. 8) The CVEs that are leveraged by the campaign to infect victims
Fig. 8) The CVEs that are leveraged by the campaign to infect victims
While the bash script file name varies between s.sh , p.sh, sup.sh, d.sh, ex.sh, r.sh, spr.sh, tf.sh or wb.sh - they all do pretty much the same thing.
The bash script kills any competing miners that might already exist on the system and disables security and logging features. It then downloads the Kinsing malware (written in Golang), establishes persistence using the crontab, and then starts mining crypto.
 Fig. 9) a portion of the malicious bash script that downloads the Kinsing crypto miner on the victim’s Linux machine
Fig. 9) a portion of the malicious bash script that downloads the Kinsing crypto miner on the victim’s Linux machine
Once executed on the victim’s machine, the Kinsing malware creates a second process called kdevtmpfsi in the /tmp directory, which is the xmrig crypto miner, and executes it. The Kinsing malware constantly monitors the kdevtmpfsi process to ensure that it’s running.
Decoding Command & Control IP address
The way the malware communicates to the C2 server is by decoding the C2 IP address at runtime using a function called getActiveC2CUrl. The getActiveC2CUrl function uses a RC4 stream-cipher to XOR plaintext hex data with a plaintext key that are both stored within the binary.
Due to the nature of how strings are stored within a Golang binary, where all static strings are basically concatenated with one another resulting in one big string blob, the plaintext key and hex data can be easily hidden within the massive string. After some reversing of the getActiveC2CUrl function, the location in memory and length of both the key and the hex data can be found.

 Fig. 10) The location in memory and length of both the C2 plaintext hex data and the cipher key are shown.
Fig. 10) The location in memory and length of both the C2 plaintext hex data and the cipher key are shown.
The getActiveC2CUrl function hex decodes the C2 hex data, and then, along with the key, they are both passed into a second function called RC4. The custom RC4 function uses the function func (c *Cipher) XORKeyStream(dst, src []byte) internally from the rc4 golang package to generate the C2 IP address.
Now that both the C2 hex data and the key are obtained, the getActiveC2CUrl function can be further reverse engineered and rewritten in Golang in order to calculate the active C2 IP address.

 Fig. 11) The getActiveC2CUrl() function is rewritten in Golang with the obtained C2 hex data and key to generate the active C2 IP address.
Fig. 11) The getActiveC2CUrl() function is rewritten in Golang with the obtained C2 hex data and key to generate the active C2 IP address.
RAT Capabilities
The Kinsing malware has remote access trojan (RAT) capabilities that can be found in a function called doTask() within the binary. The doTask function contains a few interesting function calls that it executes based on a given input
runTaskWithScan()
updateTask()
startCmd()
execTaskOut()
masscan()
socks()
backconnect()
runTaskWithHttp()
downloadAndExecute()
One of these interesting functions is startCmd() that allows for an arbitrary command to be executed on the victim's machine.
 Fig. 12) The doTask() function in a decompiled form is showing the RAT capabilities of the malware. Highlighted is the embedded startCmd() function which allows for an arbitrary command to be executed on the victim's machine.
Fig. 12) The doTask() function in a decompiled form is showing the RAT capabilities of the malware. Highlighted is the embedded startCmd() function which allows for an arbitrary command to be executed on the victim's machine.
Command & Control Communication
The malware communicates with the C2,185.154.53.140, over HTTP. It sends the C2 HTTP requests regularly, and receives instructions to be executed and provides simple health checks.
The infected machine sends the C2 information with every HTTP request about its current status and system resources, such as number of cores, memory, operating system, if root privileges were obtained or not, and more. All of these parameters are provided to the C2 server using custom HTTP headers.
 Fig. 13) A POST request made from an infected machine to the C2, which contains information about the victim’s system resources and obtained privileges
Fig. 13) A POST request made from an infected machine to the C2, which contains information about the victim’s system resources and obtained privileges
An endpoint that the infected machine constantly requests in order to receive instructions is /get. When an infected machine makes a GET request to the C2’s /get endpoint, the malware immediately attempts to download new additional malicious shell scripts from the original distribution IP 194.38.20.199.
 Fig. 14) The infected machine makes a GET request to the /get endpoint of the C2 and as a result fetches new shell scripts from the original distribution IP 194.38.20.199
Fig. 14) The infected machine makes a GET request to the /get endpoint of the C2 and as a result fetches new shell scripts from the original distribution IP 194.38.20.199
The bash scripts that are then downloaded from the original distribution IP 194.38.20.199 as a result of hitting the /get endpoint of the C2 are called ph.sh and spre.sh. These two files are different from the initial infecting bash script that we looked at before, they each have a different purpose and contain additional infection vectors.
We will first examine the ph.sh script, it downloads a rootkit called libsystem.so from the 194.38.20.199/libsystem.so endpoint in addition to the existing Kinsing malware on the victim’s machine. The ph.sh script then preloads this rootkit into /etc/ld.so.preload
 Fig. 15) A portion of the ph.sh bash script that preloads the fetched libsystem.so rootkit into /etc/ld.so.preload
Fig. 15) A portion of the ph.sh bash script that preloads the fetched libsystem.so rootkit into /etc/ld.so.preload
The ph.sh script also establishes a second persistence mechanism, in addition to the already existing cron jobs that were previously injected by the initial script. It does this by registering a system service that will periodically reinfect the host.
 Fig. 16) A portion of the ph.sh bash script that creates a system service to establish persistence and reinfects the host periodically.
Fig. 16) A portion of the ph.sh bash script that creates a system service to establish persistence and reinfects the host periodically.
If you would like to know more about the libsystem.so rootkit that the ph.sh script installs and its inner workings, Trend Micro wrote a fantastic blog about this specific rootkit that can be found here
The second interesting bash script file that gets fetched due to a /get response from the C2 endpoint is spre.sh. Its purpose is to spread the infection to additional hosts by finding ssh credentials for any hosts that the victim has access to by examining ~/.ssh/config , ~/.bash_history, and .ssh/known_hosts. The spre.sh script will then attempt to ssh into the discovered hosts using the obtained creds that were found and infect them as well.
 Fig. 17) The spre.sh bash script spreads the infection to additional hosts using ssh by finding ssh credentials in ~/.ssh/config ~/.bash_history and .ssh/known_hosts
Fig. 17) The spre.sh bash script spreads the infection to additional hosts using ssh by finding ssh credentials in ~/.ssh/config ~/.bash_history and .ssh/known_hosts
Another interesting C2 endpoint that the infected machine requests for instructions, is the /mg endpoint. When the infected machine makes a GET request to the /mg endpoint, the C2 responds with a few characters, then immediately the infected machine will start communicating with a third IP address, 95.181.179.88, which seems to be responsible for giving mining commands to the infected machine in the form of a JSON-RPC payload over HTTP.
 Fig. 18) The infected machine makes a GET request to the /mg endpoint of the C2
Fig. 18) The infected machine makes a GET request to the /mg endpoint of the C2
What to do
To mitigate these threats, the Akamai SIRT advises to monitor processes on your systems for abnormally high resource consumption and suspicious network activity. Abnormal high CPU usage for a given process may be an indicator of cryptomining activity.
The Akamai SIRT also recommends you frequently check the cron jobs that are registered under the crontabs on your systems to ensure that the cron jobs are not communicating to any unknown IP addresses, which is a common technique for Linux malware to establish persistence, and the discussed campaign is no exception.
On Windows systems the same should be done with PowerShell using the SchTasks.exe /Query to display any scheduled tasks that might have been created by this campaign. Also check the running processes on your Linux systems and ensure that processes with the name kinsing or kdevtmpfsi are not running and that a process called sysupdate is not running on your Windows systems.
Add strong authentication to your systems where possible, weak passwords can be easily brute forced. Also ensure services that are targeted by the discussed campaign which include Oracle WebLogic Server, Redis, Apache Solr, PHPUnit, and Supervisor XML-RPC are not internet facing if they don't need to be, which highly reduces the risk that these services will get infected. For example, if a Redis instance is only used by internal systems it does not need to be internet facing.
The Akamai SIRT also recommends checking your systems against the Indications of Compromise (IOC) provided in the IoCs section below to ensure that your systems are not already infected. In addition to that, patch your systems regularly and follow best practices.
Indications of compromise (IOC)
IPs
IP |
Description |
185.154.53.140 |
Command & Control |
194.38.20.199 |
Malware distribution |
95.181.179.88 |
Manages cryptomining operations |
195.3.146.118 |
Backup malware distribution |
Files
SHA-256 |
Name |
Description |
8ca0229fb64e3f1819375cf1daf32104c37c0d0923bdc35cb6bea655ecd1a6a4 |
s.sh |
194.38.20.199/s.sh, bash script that downloads Kinsing malware |
ede8fdb68d777efcc0538b465d640cbb2c061bd49461f76d65f68c135ff8bbb6 |
p.sh |
194.38.20.199/p.sh, bash script that downloads Kinsing malware |
0e79ec7b00c14a4c576803a1fd2e8dd3ea077e4e98dafa77d26c0f9d6f27f0c9 |
d.sh |
194.38.20.199/d.sh, bash script that downloads Kinsing malware |
6e35b5670953b6ab15e3eb062b8a594d58936dd93ca382bbb3ebdbf076a1f83b |
spr.sh |
194.38.20.199/spr.sh, bash script that downloads Kinsing malware |
818179ac928027a5c26c9b13d3d830b7331c3e4c46ba1e305867e3d4accaf3ef |
r.sh |
194.38.20.199/r.sh, bash script that downloads Kinsing malware |
56ac2321e481708ea72e2bf7710e66c3455afa729b24f6a6ba9065ae0cca8fb3 |
ex.sh |
194.38.20.199/ex.sh, bash script that downloads Kinsing malware |
05e5ad89443b58805ae2eb2628d3eef1d6cbcc338bced23f422abe5ce60ff82d |
tf.sh |
194.38.20.199/tf.sh, bash script that downloads Kinsing malware |
274b11542fcb30065c4cc0976ce33252ba2812756f7e22f6d80fae1acadf5c4c |
wb.sh |
194.38.20.199/wb.sh, bash script that downloads Kinsing malware |
6e25ad03103a1a972b78c642bac09060fa79c460011dc5748cbb433cc459938b |
kinsing |
194.38.20.199/kinsing, the Kinsing malware binary |
7d31843ce5231c95ce07a609cb4473fe53b95a8d0685df9d666de348d17c69ff |
config.json |
194.38.20.199/config.json, json config for XMRIG miner |
c38c21120d8c17688f9aeb2af5bdafb6b75e1d2673b025b720e50232f888808a |
libsystem.so |
194.38.20.199/libsystem.so, a rootkit binary |
5e5b5171a95955ecb0fa8f9f1ba66f313165044cc1978a447673c0ac17859170 |
xmrig.exe |
194.38.20.199/xmrig.exe, XMRIG miner for Windows |
49ff0329b9ad42c7fb17e6a2d80b316ed6b759ab5dfd04a5aba42b97225494cf |
wbw.xml |
194.38.20.199/wbw.xml, xml file that downloads a powershell script to infect Windows systems |
25b545dc3423d5c3c0181f559486643a7097b5fd87b32f0347ed667cbf3fb38e |
wb.xml |
194.38.20.199/wb.xml, xml file that downloads a bash script to infect Linux systems |
6b9e23cb675be370a18a0c4482dc566be28920d4f1cd8ba6b4527f80acf978d3 |
curl-amd64 |
194.38.20.199/curl-amd64 , curl binary |
fecd30cd7802f8ac4137a2d0659b3052411a99d809a5aefb48f8b821905100f3 |
al.sh |
194.38.20.199/al.sh, bash script that stops aegis service |
cb2ca16246a687b34fa1ba76015cb4aa3b50b4ecca4550478eb580c4725ab48f |
cron.sh |
194.38.20.199/cron.sh, bash script that updates the crontab |
d7cda9e427d0848352a1158c68a2577c1600965fb9dbb32bc1e10af1a442d284 |
ph.sh |
194.38.20.199/ph.sh, bash script that downloads the Kinsing malware and the libsystem.so rootkit |
f4c319e43296ab323615ac4bd4b7601991218ecb6d6043b1c040a96f1a33f14f |
spre.sh |
194.38.20.199/spre.sh, bash script that spreads the infection to other hosts via ssh |
dd603db3e2c0800d5eaa262b6b8553c68deaa486b545d4965df5dc43217cc839 |
kdevtmpfsi |
The Kinsing crypto miner process |



