Massive Campaign Targeting UK Banks Bypassing 2FA

On 14 July, 2020, Oliver Hough, a security researcher from Cyjax, published a report centered on a phishing campaign targeting banking customers in the United Kingdom, which evades two-factor authentication (2FA). On 16 December, 2020, researchers from the Global Threat Intelligence Team at WMC disclosed that they were tracking a threat actor who goes by the alias "Kr3pto".
This actor is a phishing kit developer who builds and sells unique kits targeting financial institutions and other brands. In some cases, these kits target financial firms in the United Kingdom, and they bypass 2FA. Akamai's research team was able to track some of the phishing campaign activity described in both publications. We were able to see the sheer magnitude of those attacks, dating back to May of 2020. Moreover, while the previously mentioned blogs noted that backend administrative panels used by the Kr3pto kits are different, our research shows that the core element in these attacks, the phishing kits themselves, are the same.
Admin panels are how criminals manage the various elements of a phishing kit, such as data collection, geo targeting, user prompts, and security. While most kits come with their own administrator control, that isn't always the case. Also, as kits are cracked and recirculated, those who repackage the kits (often referred to as rippers) will use their own admin panel as a form of branding.
Akamai tracked more than 7,600 domains being deployed with the Kr3pto kit, abusing 8 different banking brands, and using commercial web hosting to scale the various phishing campaigns in an effort to evade detection.
While these phishing campaigns are not new, details related to attacks like this can help us understand phishing market forces, and emphasize the scale and sophistication associated with such activities. The campaigns we observed also highlight the continued evolution of phishing threats targeting credentials. Once compromised, the targeted credentials can result in unauthorized access to secure networks or fraudulent activities, by introducing techniques that bypass 2FA solutions using One Time Password (OTP) tokens or Push Notification. Our research reveals that token-based 2FA solutions are far from bulletproof, requiring the adoption of stronger multi-factor protections.
The scam
Based on our research, and the research conducted by others watching the Kr3pto campaigns, distribution of the scam happens via SMS. The most common lure will indicate that a suspicious payee request was made on the account. The lure then asks the victim to take action if the payee addition was not initiated by them, by asking them to follow a link leading to the phishing kit's landing page.
Once on the landing page, the victim is prompted for credentials. If the victim shares their username and password, the scam moves forward and displays the text shown in Figure 1. The aim here is to make the victim believe that an allegedly fraudulent payee transaction was blocked, and a representative will reach out to them to discuss the matter.
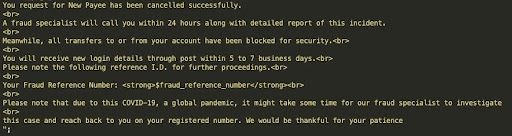 Figure 1: The message informing the victim that a so-called specialist will be calling them.
Figure 1: The message informing the victim that a so-called specialist will be calling them.
2FA bypass
Previous research on the Kr3pto kit campaign shows that the operation of the scam itself is customized to each bank's authentication workflow, and in some cases it will attempt to bypass the 2FA once that stage is reached. This happens manually.
The criminals will take the compromised username and password, and trigger a 2FA request, which generates an OTP that is then sent to the victim's device. From the victim's point of view, the generated OTP is requested by the phishing kit (Figure 2). Once the victim enters the OTP and submits the form, the criminals now have all they need to access the victim's account and take it over.
 Figure 2: Phishing website requesting 2FA token/OTP
Figure 2: Phishing website requesting 2FA token/OTP
COVID-19 is also being used as an attribute to the scam; the pandemic is used as a phony excuse for limited availability of anti-fraud specialists, giving the criminals time before phoning the victim in order to address the alleged fraudulent payee transaction. This way, if the victim doesn't immediately get a call, the criminal is counting on the COVID-19 notice to explain the slow response and prevent the victim from becoming suspicious.
In order to prevent the manual authentication request to the victim's account from being flagged as fraud or otherwise suspicious at the targeted bank, the criminals behind the phishing scam will leverage the collection of identifiers in the kit (Figure 3). Such identifiers can include the victim's User-Agent, operating system details, and IP address. Each of these things can be spoofed to a degree, which offers a slight edge to the criminals. It isn't a flawless evasion technique, but it does work.
 Figure 3: Code for exfiltration of victim’s User-Agent and IP address
Figure 3: Code for exfiltration of victim’s User-Agent and IP address
Phishing scams an industry of factories and economies
According to Akamai's research, more than 7,600 domains were deployed using the Kr3pto phishing kit, tracking back to May 2020. The most significant part of the campaign happened between October and December, 2020, with a peak of 800 domains in November 2020.
 Figure 4: Number of new phishing domains being deployed per week
Figure 4: Number of new phishing domains being deployed per week
Looking at the brands being abused by Kr3pto, Akamai is able to confirm that there are 8 banks in the United Kingdom being targeted. The use of rapidly changing domains is derived by the short lifespan of each domain before it is classified as malicious, and taken offline or blocked. Therefore, because the criminals continue to deploy new domains on a somewhat regular basis, the Kr3pto campaign has been able to maintain its efficiency.
In order to understand the connections across the domains used by the Kr3pto campaign, we turned to the Autonomous System Number (ASN) that hosts them. As Figure 5 shows, Akamai determined that there were more than 80 ASNs connected to domains hosting Kr3pto phishing kits. With this data, we assume that each ASN represents a different campaign running Kr3pto, on a different hosting service, and have labeled them as such.
The evidence supporting different campaigns using different hosting services is also explained by different threat actors pushing different scams using the same phishing kit. The assumption here is supported by evidence published by other researchers, indicating that variants of the Kr3pto kit are being sold on the darknet.
 Figure 5: Phishing campaigns associated with Autonomous System Number
Figure 5: Phishing campaigns associated with Autonomous System Number
The one campaign that stands out, as shown in Figure 5, is associated with "hoster_1". This campaign has over 6,000 domains being deployed under a hosting service provided by a well-known domain registrar.
Pivoting from hoster_1 to the phishing domains, and their associated targeted bank, Figure 6 shows us that there are 8 different UK bank brands being targeted. According to previously published reports, we were able to learn that the same administration panel can handle different targeted banks scams. This, combined with the usage of the same fully featured hosting provider, leads us to believe that the all activity associated with hoster_1 is using the same operational infrastructure.
 Figure 6: Here we see “hoster_1” pivot to targeted brand and the associated phishing websites
Figure 6: Here we see “hoster_1” pivot to targeted brand and the associated phishing websites
Attack campaigns that leverage hosting capabilities and associated features, such as domain registration, SSL certificates, and deployment and management tools, are not new to the threat landscape. Yet, the scale and usage of commercial hosting presented in this research is considered another indication of the evolution of the phishing landscape, as the criminals use and abuse commercial services enabling a scale to their operations that's rarely seen.
Summary
Based on our research, as well as the aforenoted research at WMC and Cyjax, the attack campaigns highlighted by this post are being propagated in the UK, primarily through mobile phones via SMS. In recent months we've seen an increase in the usage of SMS as a distribution channel for many phishing campaigns.
Indeed, we believe that the usage of SMS is driven by the reliability of this distribution channel and the lack of security controls on many mobile devices, therefore, leading to increase in attack efficiency.
The usage of phone numbers and association to the relevant bank is not clear. Yet, if such association exists, it could be the result of past data breaches or the outcome of preliminary phishing campaigns that target personal information.
As threat actors step up their game, it is clear that 2FA tokens are not enough to prevent phishing attacks. They offer some basic, low-level defense, but criminals are targeting them because they're a weak link in the authentication chain. Therefore, a more robust 2FA technology that is more resilient to phishing, such as the FIDO2 protocol, is needed. Protocols that cryptographically bind user credentials will make phishing harder and make tricks like the ones explored in this blog post near-impossible to pull off.
Defenders need to urge organizations to move away from SMS-based OTPs or 2 factor push notification, because it's clear that criminals are only going to get more creative in their efforts to subvert these mechanisms.



