Phishing Summary 2020—Trends and Highlights

2020 was a challenging year for many of us, as the COVID-19 pandemic disrupted life and introduced challenges in almost all elements of living. 2020 was also challenging from a cybersecurity point of view, as nearly the entire workforce moved to remote working and enterprise boundaries were never so vague, which introduced complexities on that end.
As this year comes to an end, it's time to look back and highlight some trends related to phishing attacks in general, including tracking across tens of thousands of domains and 200,000 potential victims, and how COVID-19 played a role in them.
Phishing kits recycling
As the phishing landscape becomes more mature and sophisticated, it's adopting other legitimate market behaviors, including the ecosystem of factories and economies. The factories are represented by cybercriminals who constantly manufacture new phishing toolkits, and economies being represented by the market of selling and trading those kits.
In order to indirectly evaluate the ecosystem of phishing factories and economies, we tracked the usage of over 500 phishing toolkits in the past year. We used two measurements. The first one evaluated the frequency of usage of each toolkit over the past year, where we were able to see at least one URL using the toolkit being deployed in the wild, as seen in figure 1.
The second measurement was to determine the scale and volume of recycled phishing toolkits in the wild. In order to do that, we counted the total number of URLs hosting one of the tracked 500 phishing toolkits as seen in the wild per day over the past year, figure 2.
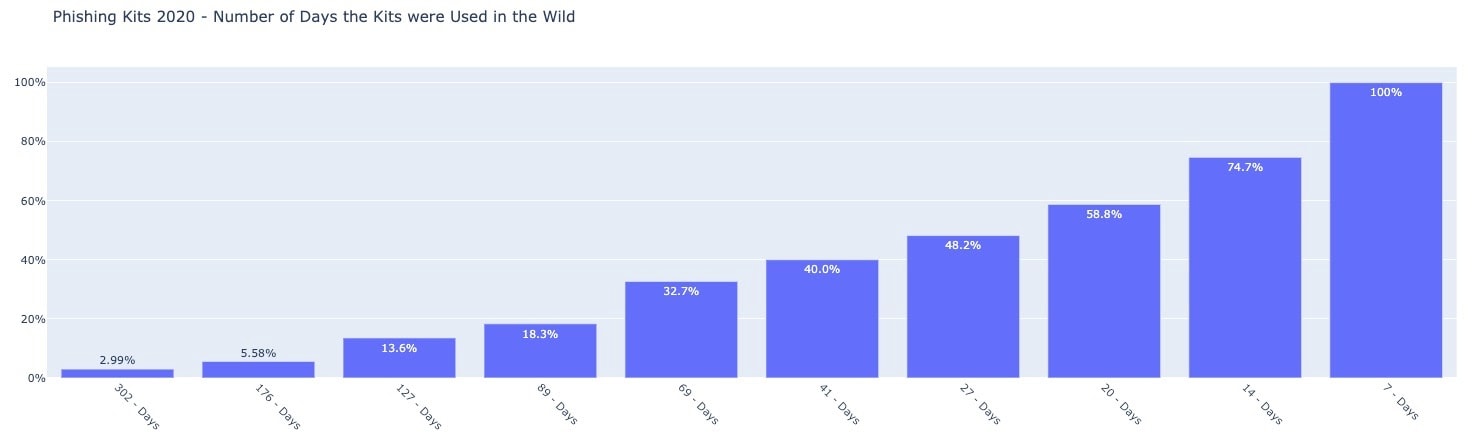 Fig. 1: Number of days on the past year each toolkit was used in the wild
Fig. 1: Number of days on the past year each toolkit was used in the wild
According to figure 1, we can see that over 13% of the toolkits were recycled on, at least, 127 different days during the year, 32% of toolkits on at least 69 different days and 74% on at least 14 different days. The frequency of the toolkit usage over the past year represents the phishing market forces that resell, recycle, and redeploy toolkits. These numbers help to explain the scale behind the ecosystem driving phishing factories and economies, and assist with understanding the ecosystem behind the overwhelming numbers of phishing threats emerging each day.
 Fig. 2: Number of URLs per week hosting one of the tracked 500 toolkits
Fig. 2: Number of URLs per week hosting one of the tracked 500 toolkits
According to figure 2, we see the number of URLs per week in the wild using one of the 500 toolkits we tracked, representing over 37,000 URLs. The numbers show the order of magnitude when it comes to phishing forces. On top of that, we also see a rapid increase in the number of phishing URLs using recycled toolkits starting May 2020. We believe this is a direct outcome of COVID-19, as cybercriminals launch more campaigns trying to engage more victims.
Earlier this year, we were able to track toolkits being recycled and reused in the context of COVID-19, linking toolkits used in the wild prior to the COVID-19 outbreak to those associated directly with COVID-19.
 Fig. 3: Phishing campaigns percentage increase consumers vs. enterprise user
Fig. 3: Phishing campaigns percentage increase consumers vs. enterprise user
We also analysed the recycled toolkit URLs by linking them to potential victims, as seen in figure 3. We can see that, over the measured year between November 2019 to October 2020, there is a 235% increase in attacks targeting enterprise users and a decrease of 6% in attacks targeting consumers. We believe the rapid increase in phishing attacks targeting enterprise users is a result of criminal motivations to leverage COVID-19 changes that took place during March 2020, which led to moving the majority of the workforce to their homes. By targeting remote workers who were unaccustomed to these environmental changes, criminals looked to gain an additional path into the network.
Victim's devices
As mobile became the primary device being used by internet users, we can see this being reflected in the number of phishing campaigns targeting said devices. For two months, we tracked over 200,000 potential victims visiting 500 different domains hosting phishing scams using the same toolkit.
 Fig. 4: Number of series of campaigns victims over the time frame of 2 months
Fig. 4: Number of series of campaigns victims over the time frame of 2 months
Looking at the number of victims over time in figure 4, we can see rapid growth towards early March of 2020, and we attribute that growth to more campaigns and higher engagement levels by victims as a direct outcome of COVID-19.
Looking more closely into the victims visiting the tracked campaigns, seen in figure 5, we observed that over 80% of them are using mobile devices, breaking evenly between iPhone and Android with nearly 40% each.
 Fig. 5: Number of victims by device type
Fig. 5: Number of victims by device type
As mentioned before, this data doesn't come as a surprise. Mobile devices have become the primary device for internet users. Moreover, some of the phishing campaigns we were able to track over the past year shows some that were explicitly targeting mobile devices. The likely reasoning behind such tracking is that those victims are considered in many cases to be the weakest link in the chain, due to lackluster defensive and security controls on their mobile devices.
Phishing from the CDN point of view
Earlier this year we published research showing how phishing-derived activities sometimes redirected to Akamai's CDN. In figure 6, we can see a yearly view of the number of phishing URLs we were able to track routing through Akamai's CDN.
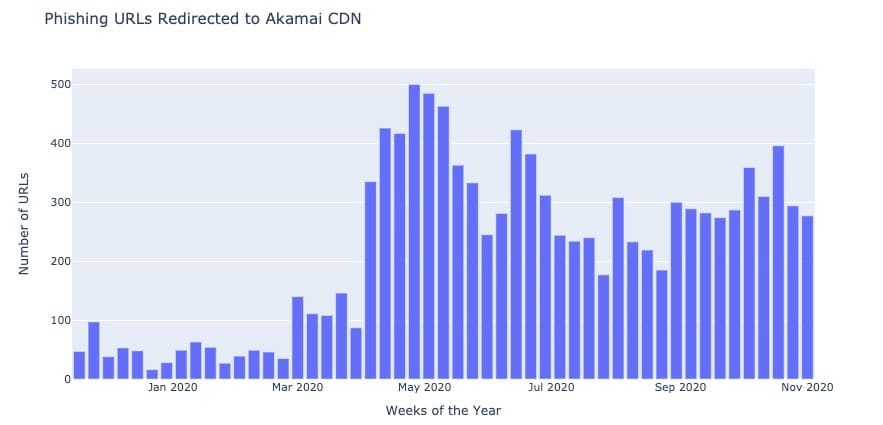 Fig. 6: Number of phishing URLs redirecting to Akamai's CDN
Fig. 6: Number of phishing URLs redirecting to Akamai's CDN
As figure 6 shows, we can see a similar trend to the one being observed on different data points in this blog, a rapid increase in the number of phishing URLs being detected starting in March 2020 and a further increase in May 2020. As mentioned before, according to our analysis, this is the direct outcome derived from COVID-19 pandemic, where cybercriminals are harnessing global concern and confusion to get more victims engaged with their campaigns.
Phishing Javascripts obfuscation
According to research done by Akamai earlier this year, we were able to see an increase in the usage of JavaScript obfuscation techniques by phishing websites. By using obfuscation techniques, cybercriminals can launch attack campaigns that can slip under the radar and make the scams much more effective and long-lived.
 Fig. 7: Number of phishing domains using obfuscation techniques
Fig. 7: Number of phishing domains using obfuscation techniques
As seen in figure 7, over the past 12 months we've seen an increase in the number of phishing URLs using JavaScript obfuscation techniques in the wild. There were more than 34,000 URLs observed over the past year. A noticeable increase in the number of phishing URLs was observed in May, and we suspect this is another point of evidence for the direct influence of COVID-19.
Ready, get set, 2021
Criminals will continue to hit us when we are most vulnerable; that is their nature after all. They'll do all they can to get us engaged in their scams by leveraging social engineering and harnessing the sentiments associated with seasonal events (holiday shopping for example) and, more importantly, global events. In this case, it's COVID-19.
As the data presented here shows, COVID-19 played a significant role in the phishing landscape this year, as criminals stepped up their efforts during the months of global lockdowns and infection surges. While organizations were struggling to deal with shifting their entire companies to remote work, criminals recycled their phishing kits and turned them to center on COVID-19 issues, including protective equipment, government assistance, and work-related problems, such as email access or service status.
Therefore, it is only natural to predict that, as we as a society move towards 2021 and the COVID-19 situation persists, the criminals are not going to stop. COVID-19 isn't going to go away, the stress and sense of concern isn't going to go away, and criminals will try to capitalize on that by continuing to focus their campaigns on whatever the latest COVID developments are.
One key element that is expected to grow during all of this is the shift towards attacking users on mobile devices. Victims there are some of the most vulnerable, and criminals will continue to target them, whether explicitly by executing targeted campaigns against mobile users, or implicitly as derived by the way we consume and use Internet services from those devices.
Moreover, the outcome of COVID-19 guidelines and movement of workforce to remote access will enable more work-related applications and services to be accessible from mobile devices, creating a sustained attack surface that criminals will be sure to abuse.



