Threat Actors Recycling Phishing Kits in New Coronavirus (COVID-19) Campaigns

Recently, researchers at Akamai observed phishing attacks leveraging recycled kits in a series of campaigns taking advantage of the Coronavirus (COVID-19) health crisis. Phishing kits that have been previously deployed over the last several months are now being used again in order to reach a new pool of potential victims: those working from home due to self-isolation, mandated quarantine, or corporate policy during the pandemic.
 Figure 1: A phishing page targeting email accounts. Credit: Twitter/JCyberSec_
Figure 1: A phishing page targeting email accounts. Credit: Twitter/JCyberSec_
Leveraging the fear surrounding COVID-19, the recently-observed phishing attacks start with an SMS message or email that directs the victim to a domain seemingly related to COVID-19 news, governmental updates, or health-related products and services. Once the victim clicks the link, they’re directed to a domain and forwarded to another spoofing one of several well-known brands. Some of the brands being abused to target potential victims include Microsoft, Orange France, and eBay. In fact, Akamai researchers have seen recycled phishing kits - first seen in July of 2019 - being used in Corona-based phishing attacks as recently as last week.
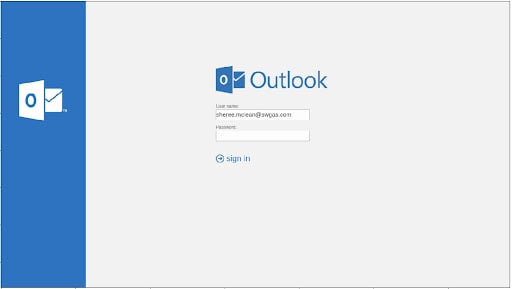
 Figure 2: One example has victims following COVID-19 related links, only to redirect them to phishing kits harvesting email credentials
Figure 2: One example has victims following COVID-19 related links, only to redirect them to phishing kits harvesting email credentials
Over the past few weeks, Akamai researchers have seen several examples of phishing URLs with corona, coronavirus, and the World Health Organization (WHO) in them. Most of these URLs are new. In all, there were several domains leveraged in this recent wave of phishing attacks, and dozens of new Coronavirus domains are being deployed each day – so we expect this trend to continue.
 Figure 3: Phishing kit recycling over time
Figure 3: Phishing kit recycling over time
Criminals will always leverage current events:
People are scared, and there is a fixation on information related to the pandemic. Fear is the key element for criminals running these scams, which are not limited to phishing alone.
Criminals have started spreading ransomware and other malware via email, SMS messages,and malicious apps. Others are running scam stores and offering to sell COVID-19 testing kits and related medical supplies. Phishing attacks are essentially a confidence scam.
By pretending to be an insurance company, bank, medical expert, or other trusted brand, criminals are convincing victims to trust them. Once trust is established, the criminal is betting on the victim doing as asked, by opening malicious attachments, following malicious links, and releasing sensitive personal information, in order to enable access to critical applications and services.
Criminals take advantage of recognizable top-level domains (TLDs) such as digital, zone, and healthcare in order to add legitimacy to their campaigns. What happens when the scam is successful will depend on the attack itself, but the overall goal is to obtain something - money or sensitive information.
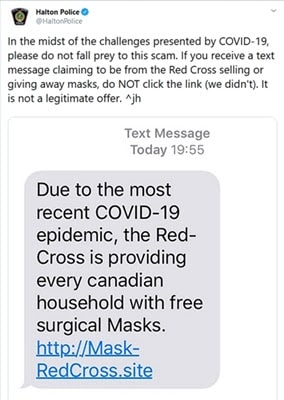
Figure 4: A SMS scam taking advantage of the COVID-19 pandemic. Credit: Twitter/HaltonPolice
The National Cyber Security Centre (NCSC) in the UK and WHO have issued notices to the public, warning about the surge in criminal activity surrounding the COVID-19 pandemic and urging a strong sense of caution. As people transition away from office life to a work-from-home program, criminals recognize that such situations create valuable attack surfaces and are working to take advantage.
Phishing isn't a new phenomenon, but it is a common attack vector that criminals will use in the worst of times, as they leverage fear in order to abuse a victim's state of mind. The recycling and repurposing of phishing kits themselves are indicative of the turnkey, industrial nature of the phishing industry.
The COVID-19 pandemic introduces unprecedented challenges for us all, and criminals are looking to take advantage, so everyone needs to remain more vigilant in the days to come.



