Akamai’s Perspective on March’s Patch Tuesday 2024
Patching isn’t always as easy as pie, but let’s dig in anyway. As we do every month, the Akamai Security Intelligence Group set out to look at the more intriguing vulnerabilities that were patched. Of the 60 CVEs patched this month, only two were critical and both were in Windows Hyper-V. CVE-2024-21407 is a remote code execution (RCE) vulnerability with a CVSS score of 7.1 and CVE-2024-21408 is a denial-of-service (DoS) vulnerability with a score of 4.8.
In this blog post, we’ll assess how critical the vulnerabilities really are, and how commonplace the affected applications and services are, to provide you with a realistic perspective on the bugs that were fixed. Be on the lookout for these insights in the days after every Patch Tuesday.
This is an ongoing report and we’ll add more information to it as our research progresses — stay tuned!
This month, we’re focusing on the following areas in which bugs were patched:
Windows Hyper-V
Windows Hyper-V is the native hypervisor in Windows. It allows the hosting of virtual machines (guests) on a single host machine. Virtualization is very common in enterprise networks, as it saves hardware costs.
In our observations, 80% of environments had at least one machine with Hyper-V enabled (hosts), and an average of 35% of Windows machines had Hyper-V enabled. There were two vulnerabilities patched in Hyper-V this month, both of them critical.
CVE-2024-21407 is an RCE vulnerability that allows authenticated attackers with access to Hyper-V guest machines to execute code on the Hyper-V host by sending crafted file operations requests to the virtual machine’s hardware resources. This sounds like a local attack vector, but the MSRC actually says that the attack vector is the network. We hypothesize that this could be due to either (a) requiring the attacker to have remote access to the guest machine, or (b) some virtual network shenanigans with Hyper-V internal components.
CVE-2024-21408 is a DoS vulnerability with a CVSS score of 4.8. Unlike the other CVE, there aren’t any notes on this one, nor is there any explanation for why this is critical despite being scored so low. We believe that the criticality is due to Hyper-V’s extensive use and availability, while the low score is simply caused by CVSS calculation technicalities.
Detection
Although CVE-2024-21407 is categorized as a network attack vector, it is difficult to recommend network segmentation as a mitigation strategy (which is the common solution for network related attacks) since there is no information on how it is achieved.
Instead, we provide the following osquery, which customers can run in Akamai Guardicore Segmentation Insight, to detect machines running as Hyper-V hosts:
ELECT name, statename FROM windows_optional_features WHERE state=1 AND name LIKE 'Microsoft-Hyper-V%'
Open Management Infrastructure (OMI)
Microsoft OMI is an open-source project that implements the DMTF’s CIM and WBEM standards. You can think of it as Microsoft’s UNIX version of Windows Management Instrumentation (WMI). This month, there’s an RCE CVE (CVE-2024-21334) with the high score of 9.8, even though it is only given “important” severity. According to the FAQ under the patch notes, the vulnerability arises from a use-after-free primitive, which can be triggered by attackers from the internet.
Mitigation
Like its Windows counterpart, OMI agents listen on TCP ports 5985 and 5986 by default. If our attack vector is attacker access from the internet, then simply segmenting these ports from internet access should provide a temporary mitigation while you’re patching.
Detection
OMI is typically installed via the Microsoft Repo. Therefore, it should be possible to query for its installation:
SELECT * FROM deb_packages WHERE name == 'omi'
Alternatively, you can look for Linux machines that are listening on TCP ports 5985 or 5986 (Figure).
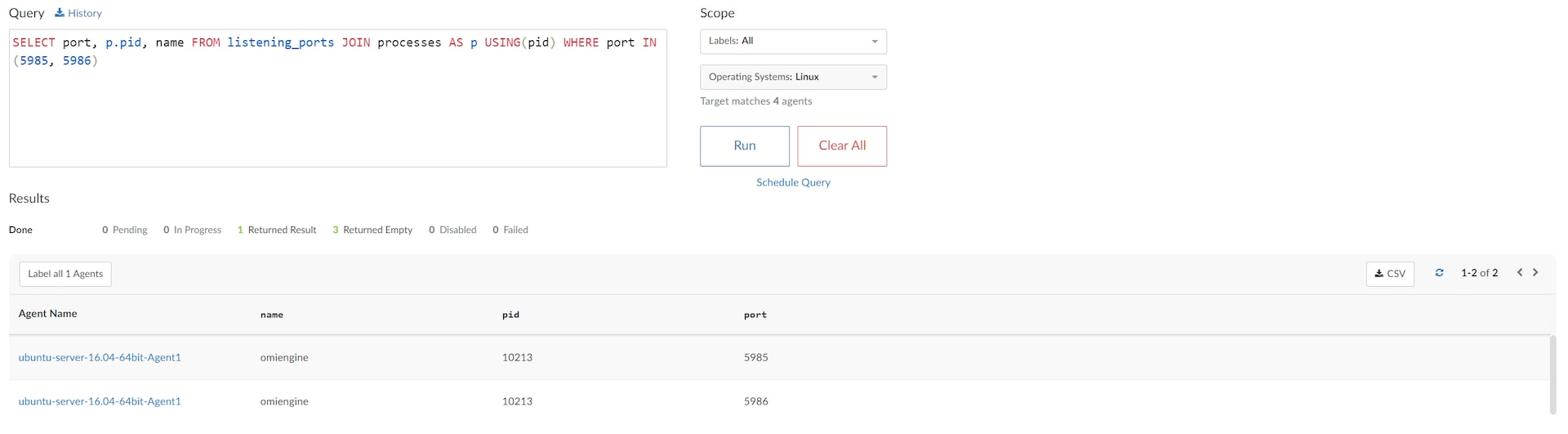 Querying for Linux machines that are listening on the default OMI ports
Querying for Linux machines that are listening on the default OMI ports
In our observations, 10% of environments had at least one machine with an OMI agent installed.
Windows Compressed Folder
The Windows Compressed Folder is the well-liked feature that lets users compress folders into zips, or view .ZIP files in Windows Explorer. Something must’ve changed in Windows 11 because the current CVE in Compressed Folder, CVE-2024-26185, is applicable only to Windows 11. It is a tampering vulnerability that requires victims to open a specifically crafted compressed folder to trigger the vulnerability.
Attackers need to convince users to download and open the compressed folder via some sort of phishing or social engineering scheme. It is unclear what effect the tampering has — but judging by the fact that it is file system–related, our educated (but ungrounded) guess would be something like file deletion or overwrite, or even extraction to unintended paths.
Previously covered services
Many CVEs in this month’s Patch Tuesday are for systems that we’ve already covered in the past. If you’re interested in our analysis of, or general recommendations for, those services, we encourage you to look at our previous perspectives on Patch Tuesday blog posts.
Service |
CVE number |
Effect |
Required access |
Remote code execution |
Network |
||
Remote code execution |
Network, requires user interaction |
||
Security feature bypass |
Network |
This summary provides an overview of our current understanding and our recommendations given the information available. Our review is ongoing and any information herein is subject to change. You can also visit us on X, formerly known as Twitter, for real-time updates.




